Hackers are increasingly throwing all they’ve got at cyber security in healthcare. Ransomware, phishing scams, malware, data leaks, identity theft, and constant social engineering. This leaves healthcare employees wondering if they should just go back to their pens and paper.
In 2015, an estimated 100 million healthcare records were compromised. This began to highlight the severity of the problem. The data was leaked from more than 8,000 devices across over 100 countries.
Of course, the problem didn’t go away.
In 2017, the WannaCry hack compromised the NHS, and the Petya attacks held more hospital records to ransom. The worst is not behind us. These attacks happen every day. And only the big ones make the news.
So what gives? Is the cyber security in healthcare so bad they’re practically giving away patient information?

Why Do Hackers Want Healthcare Data?
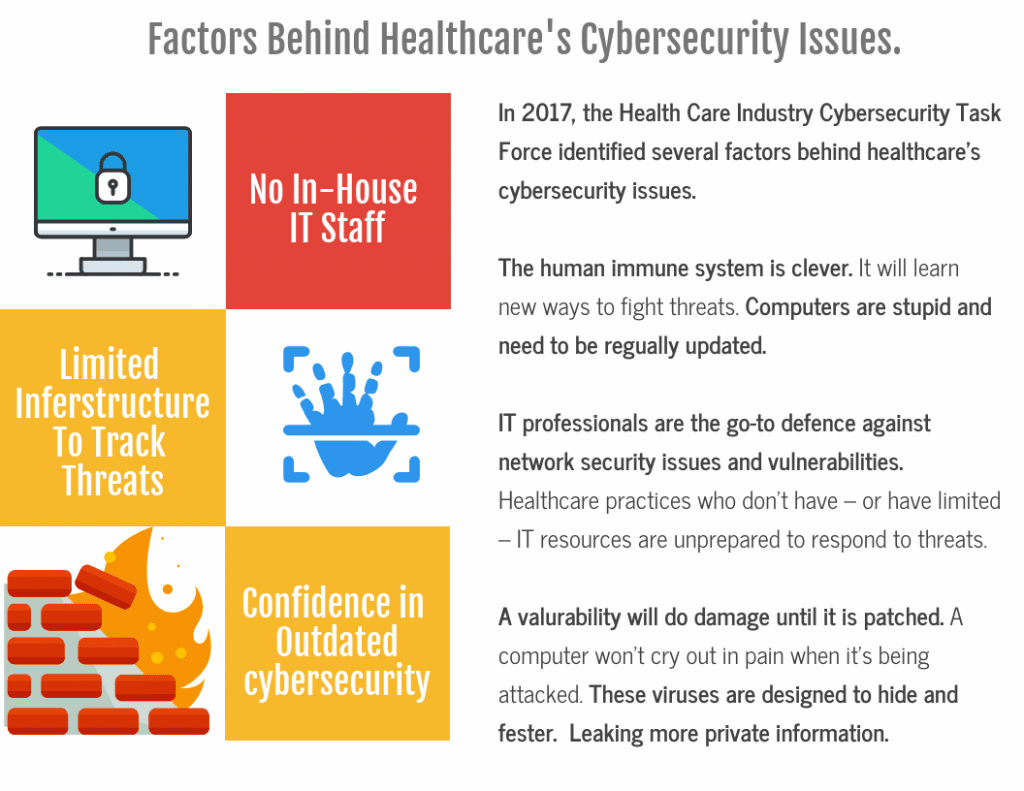
Healthcare data is valuable information to steal. In other words, it’s sensitive, personally identifiable, exploitable information. Knowing this, cyber security in healthcare should be solid, resilient and consistently excellent. However, in reality, these data stores are ripe for the picking.
In 2015, IBM conducted research into a Cyber Security Intelligence Index. They found that of all the industries they looked into, healthcare was the most frequently attacked by cyber-criminals. This is also consistent with the Notifiable Data Breaches Scheme quarterly report.
Millions of dollars worth of identity data are locked away in hospitals and when they are compromised it puts lives at risk.
Fraud is Out Of Control
In the future, this will be taught in schools. We live in an unprecedented age of digital fraud.
Just like shipping containers unloaded from a ship, digital identities are batched and unloaded onto the docks of the dark web. Modern fraud is a coordinated industry worth billions.
In short, fraudsters are anonymous skilled professionals competing with an ignorant general public. By comparison, their victims have an infant-level understanding of the computers and networks they use every day.
Furthermore, in the wrong hands, credential information can be used to open bank accounts and take out loans. These fraudsters run up as much debt as possible, then when the hammer comes down, they are nowhere to be found. The tools to anonymise internet users have overtaken the tools to track them.
Therefore, by exploiting broken authentication fraudsters are able to send credit card transactions, buy Amazon gift cards, or authorise Western Union transfers. Australian victims reported $340 million lost to fraud schemes in 2017. Identity theft happens every single day.
Ransomware Attacks Targeting Cyber Security in Healthcare
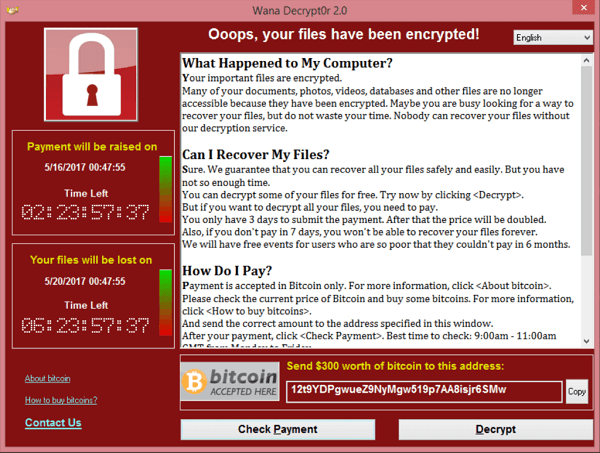
The Melbourne Heart Group faced a difficult decision in February when 15,000 medical files were encrypted and held ransom.
To sum up, encryption hide files in plain sight. You can see the files, but you can’t read them. In order to decrypt the files, the criminals demand a ransom (usually as cryptocurrency).
In recent years, this type of attack has plagued hospitals and healthcare practices. It was ransomware that infected The Melbourne Heart Group.
Ransomware frequently targets healthcare practices. Stanfield IT has helped practices bounce back from ransomware attacks, so we can talk first hand about the dangers it presents.
Ransomware Targeting Healthcare Cyber Security Hides in Emailed Word Documents: Don’t Enable Macros
Ransomware commonly infiltrates networks through a technique called phishing. Phishing is where a hacker sends an official-looking email either to a random recipient or targeting an employee. Subsequently, the employee opens the email, which will attempt to deceive the employee into downloading a malicious email attachment.
Microsoft Word documents transport ransomware via macros.
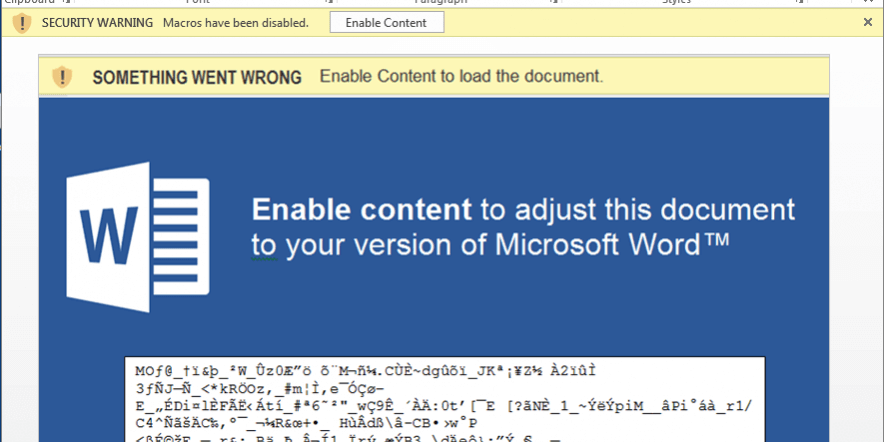
No-one suspects a Word document, which is exactly why this attack works so well. Once the attachment is open, the Word document will appear corrupted, and a pop up will appear asking if the user would like to activate the macro.
Macro is similar to a programming language, and malicious Macro can run or install applications, and change system settings or configurations. Macros attacks have existed since the 90s. Again, thanks to general computer illiteracy, somehow this isn’t common knowledge. This type of attack is the key reason for step three of the Essential Eight.
Cyber Security in Healthcare Lags Behind Other Industries
Certainly, in most corporate environments, only a select few admins will have the authorisation to enable macros and perform other actions that could put their organisation at such risk. However, in antiquated or independent healthcare systems, no such provisions exist.
Verizon’s annual Data Breach Report for 2018 estimates that ransomware is included in 85 percent of the successful malware attacks against hospitals. Cyber security researchers at Cylance estimated that the number of ransomware attacks tripled in 2017.
Once a device is infected… well, it’s called a virus for a reason. It spreads across all the connected devices until it has brought down the whole network.
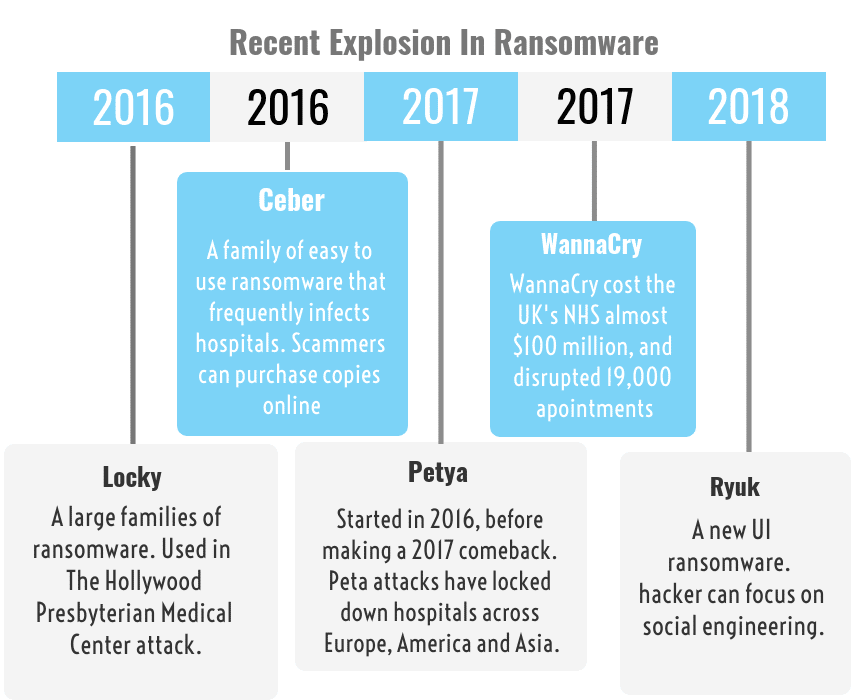
The WannaCry attacks in 2017 infected more than 300,000 companies around the world. The malware locked-up devices and files and demanded payment in Bitcoins to regain access.
This attack devastated the NHS in the UK. Hospital staff had to revert to pen and paper, and used their mobile phones to do what little they could. In subsequent investigations, it was revealed that parts of the NHS were still running Windows XP. In other words, an outdated, unsupported, vulnerable system. It’s fair to say, that this attack really shone the light on the poor state of cyber security in healthcare
Healthcare Employee Negligence a Leading Cause of Data Loss

More than half of recent data leaks in the healthcare industry are due to internal cyber security issues. Not a result of hackers or external parties. There is a good reason why human error is a significant cause of data breaches.
Up until now, we have only focused on hackers and external forces stealing data. However, the evidence suggests that poorly trained staff, who don’t understand cyber security, are more likely to be the culprit when data breaches occur.
For example: an employee forwards a sensitive work email to a personal account or device. Unbeknownst to the employee, malware has infected their device. Now the customer’s data is compromised.
The hospital’s network was secure, but the employee’s behaviour still compromised the data.
More impressive cases of negligence, common in hospitals and clinics, include, sending an email to the wrong person filled with unencrypted information. Furthermore, a quarter of all breaches were a result of unauthorised access.
Disruption Of Treatment

Ransomware targets hospitals because patient data is important enough to force the practice’s hand. While a company may be able to afford to spend weeks trying to beat the hackers and recover their data, patient data’s restoration is time-sensitive.
Hospitals will fold and pay. It’s not just data that hackers hold to ransom, but all the patients in the hospital by delaying treatment.
The WannaCry hack cancelled 19,000 appointments. The NotPetya malware attack affected Nuance medical supply chains holding up potentially life-saving treatment.
Attacks are only going to get more advanced. For example, using big data algorithms, a study from Israel tested the vulnerability of an operating hospital. They found that the results of a CT scan searching for lung cancer could be altered 98% of the time.
What’s next? Hackers crashing stock prices, and disrupting governments, by tricking CEOs, and world leaders, into thinking that they have only months to live.
It sounds like sci-fi but isn’t that far-fetched.
How the Notifiable Data Breach Scheme Affects Healthcare Providers

The NDBS applies to all health service providers.
Regarding any breach of personal data, the law mandates a healthcare provider notify affected parties within 30 days. However, it’s not always feasible to notify affected parties individually. In such cases, the practice must post a notice online and leave it up for 6 months.
Obviously, this is terrible for a practice’s reputation. Medical data is something people want confidential. A big “Oops, We Lost Your Data” banner on your GP’s website is hardly reassuring. Medical practices owe it to their patients to improve their cyber security.
If you somehow fail to notify affected individuals (intentional or not), the penalties run up to $1.8 million for organisations and $360,000 for individuals.
If you fail to report the leaks, affected individuals can lodge a complaint against an organisation. This could lead to the Information Commissioner to instigate an investigation into your organisation. And a victim of fraud would be perfectly justified for doing so.
The Essential 8 Strategies to Mitigate Cyber Security Risks
The Australian Government’s recommends these 8 strategies as baseline cyber security:
- Application whitelisting
- Configure Microsoft Office macro settings
- Restrict administrative privileges
- Multi-factor authentication
- Daily backups
- Patch applications
- User application hardening
- Patch operating systems
It’s a good list. Proper implementation of these 8 strategies, would have stopped every single ransomware attack we have covered in this post.
If you want to learn more about the essential eight, Stanfield IT has covered these strategies at length. We go through the specifics of application whitelisting, MFA, and general cyber security best practice in our many blog posts.
No one wants a data breach. It’s bad for your practices’ reputation. Now the NDB is in effect, there are monetary consequences for unaddressed data breaches and the possibility of further inquiry and legal action.
How Can A Healthcare Provider Improve Its Cyber Security

Training & General Awareness
Every report, article and evaluation of cyber security in healthcare arrives at the same conclusion; healthcare staff underestimate, overlook, and don’t understand cyber security risks.
The intention of this post was to really drive this point home. Phishing and human error are almost always how malware gets into a network. Address this with training and general awareness, and your practice is already safer.
If you work in a hospital or clinic and are trying to draw attention to the need for better cyber security in healthcare, use all the hacks that have occurred recently to make your point. You can share this article. We don’t mind.
Cyber Security Management Software
The same problems affecting healthcare, also affect every other industry which stores valuable customer private data. An unfortunate truth is that businesses with a handful of employees do a better job of mitigating these security risks than 1000-bed hospitals.
By adopting and updating corporate security tools and investing in skilled IT professionals, businesses can create secure and partitioned working environments. Secure environments that are rich with access management and endpoint protection software.
If you restrict an employee’s admin privileges, you reduce the opportunity for a hacker to manipulate and socially engineer a ransomware installation. Because ultimately, human error causes most breaches. Most cyber security software will restrict human access to limit the potential for error.
Every day, people bring malware to work on their phones, download files they shouldn’t and send sensitive data unencrypted. Prevention is always better than a cure.
MDM software, for example, will manage an employee’s phone and control user privileges while in the workplace. Data Loss Prevention tools will scan employee emails for personal customer data and prohibit employees from sending emails until they remove or encrypt the data.
Seek Out a Cyber Security Audit
The luxury of in-house IT staff is reserved for a select few practices. For this reason, a cyber security audit makes logistical sense. Ideally, someone comes in to give the network a once over and advise if it has a clean bill of health. If not, the sooner you find a vulnerability the better.
A good audit will analyse how employees use the network and identify weaknesses at the behavioural and a systems level. Identifying risks is step one. Step two is determining a clear path towards better cyber security in your healthcare practice.
Final Thoughts On Cyber security in Healthcare

Healthcare’s cyber security problems aren’t difficult to solve. The problem is that practices aren’t taking them seriously enough. As a result, they are not being addressed properly.
We get it. We do. The bureaucracy in a large practice or hospital moves slowly. We all know how people can be; rather than accept they don’t understand something, people will protest they don’t need it. Long term staff want to stick with what they know. This attitude isn’t good enough, and we encourage you to reject it whenever it rears its ugly head.
When it comes to healthcare, lives and personal data are on the line. If things keep on like this, there will be a disaster. It’s only a matter of time. Do something about your cyber security today.
