Data breaches should be near the top of the list of concerns for any small business in Australia. Every small business is at risk of a data breach, and probably more so if you think you’re beyond that risk; because it means you haven’t taken adequate measures to protect yourself.
Data breaches sound kind of dull and vague, but a data breach can and does have serious repercussions for businesses; even big businesses are not immune to the consequences. PageUp, a key provider of HR tools for Australia’s Fortune 500 lost some major clients due to a data breach. Even though there was no tangible loss or effect on those clients. Just the loss of trust and reliability due to the breach was enough to lose those businesses.
Let’s consider data breaches from a purely selfish point of view (ie the financial loss and reputation damage). That should be enough to make any small business sit up and take notice. Let alone the potential damage to your clients, their privacy and security. Which small business owners (should and do) care about.
Defining Data Breaches
What makes a data breach, well, a data breach? It can be something of a vague catch-all term. Is it a data breach if the office cleaner looks over your shoulder while you’re accessing sensitive information? Or is it just if someone hacks into the database and steals confidential data?
A data breach is an incident in which sensitive or otherwise protected information is accessed without authorisation.
So this would cover information like:
- Financial details (credit card numbers, bank details, salary information)
- Healthcare information (patient histories, diagnoses, etc)
- Corporate information and processes that are protected from outside company eyes.
And that does mean that yes, if any unauthorised person happens to lay eyes on information they should not have access to, then that’s a data breach. So it could be something as accidental as the wrong eyes coming across a file, or it could be a more sinister event wherein someone breaks into an account in order to forcibly access information.
The State of Data Breaches in Australia
Unfortunately for Australian businesses, we are just at risk of a data breach here as anywhere else. The latest OAIC statistics report (Q4 2018) shows an increase in reported breaches compared to the previous quarter. A new report will be due at the end of March and while it will be interesting to see any changes, it’s clear already that there is an increasing pattern of breaches and attacks.
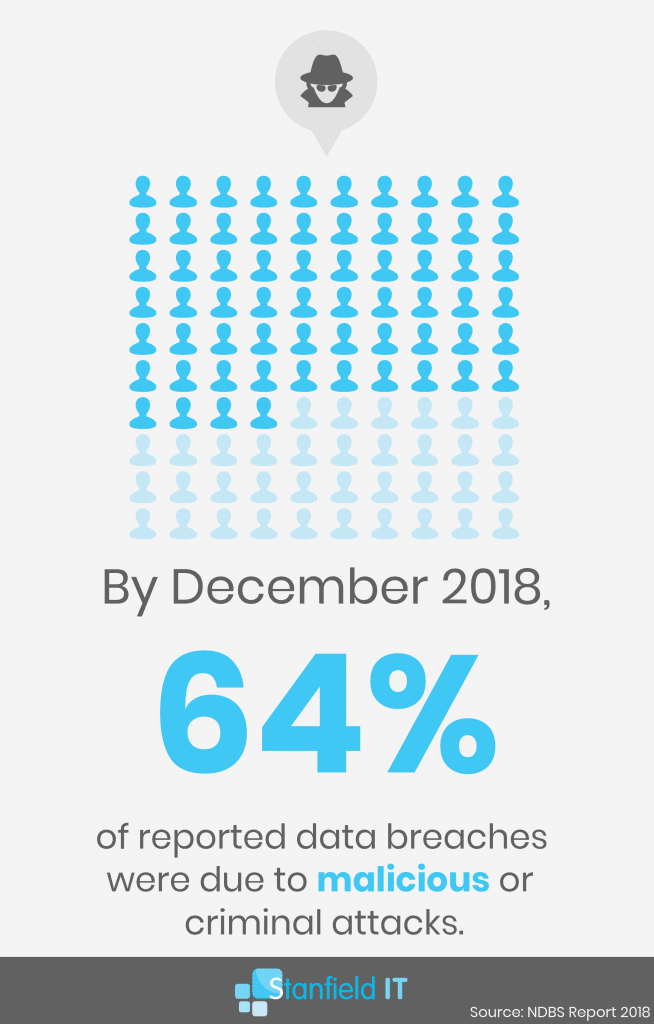
64% of breaches can be attributed to a malicious attack, which is an alarming rate. But 33% of breaches coming down to human error is still a huge number. With the right training and ongoing cyber security awareness, that could be significantly lower.
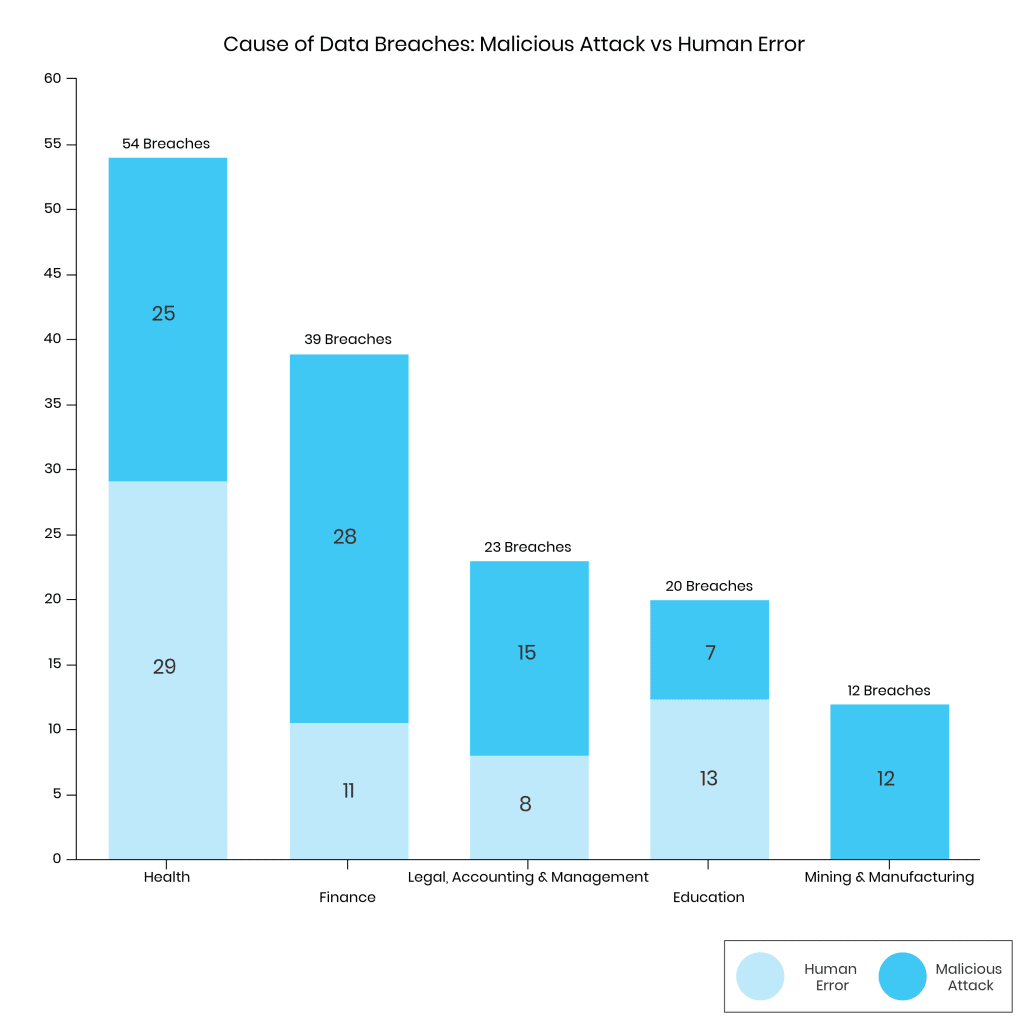
In terms of industries being hit, health service providers continue to be the most consistently affected by data breaches. Finance follows close behind. These industries rely on handling highly sensitive and confidential data. As a result, they need to take according action to protect them to the best of their abilities.
How Cyber Prepared Are We?
Across the Asia-Pacific region, Australia ranks with the lowest percentage of cyber awareness and preparedness. Only 36% of businesses in Australia have an overall information security strategy!
Chinese companies are working much harder to comply with new cyber security laws both domestically and internationally (e.g. General Data Protection Regulation in the EU). Compared to our neighbours, it seems that Australian businesses are not putting in enough effort and awareness to comply with cyber security regulations and minimise risk of cyber attacks.
With Australian regulations such as the Privacy Act, and the Notifiable Data Breaches Scheme; it’s curious to see how few businesses are aware and in compliance. Especially considering the heavy consequences for violation.
Individuals can be fined up to a maximum of $420,000 for violating the Privacy Act and companies can be looking at fines of up to $2.1 million for failing to comply with the Act or the Notifiable Data Breaches Scheme.
10 Steps To Take in the Event of a Data Breach
If your business has been hit with a data breach, be it malicious or unintentional, there are several steps you need to immediately take and some further follow up we recommend in order to prevent another occurrence.
While every data breach is different, we believe that these steps can be applied in any similar incident. Though of course, each case may incur additional steps depending the nature of the breach. Every breach should be given the same weight when first identifying and assessing. A breach may seem insignificant at first, but the full implications may not be clear until further down the line. If evaluation concludes that there was no damage from the breach, then at the very least, you refined and enforced your data breach protocol.
1. Identify the Source
Once you’ve identified that there is a data breach, you’ll need to identify the source. Was it due to human error/maliciousness or has there been a cyber attack? Examples of a breach source include:
- Unauthorised verbal disclosure
- Failure to use BCC when sending email
- Loss of paperwork or data storage device
- Sensitive information sent to the wrong recipient
- Social engineering or impersonation
- Rogue employee/insider threat
- Phishing
- Brute-force attack
- Ransomware
- Malware
2. Begin Containment Procedure
Control access to all affected accounts and systems immediately:
- Change associated passwords
- Check that recovery information is still correct (ie recovery phone numbers or email accounts haven’t been tampered with)
- Review all systems that could have been affected by the breach: any accounts that could accessed by the user (e.g. devices, information or data systems, financial software or accounts etc)
- In the case of a malware attack (e.g. ransomware), disconnect the affected device or server from the network as soon as possible.
3. Assess the Data Breach
At this point, it’s time to identify the extent of the breach and what data has been affected. Was any compromising information accessed? Take the time to evaluate if customer information has been affected, particularly anything personally identifiable.
4. Identify if Eligible Under NDBS
Any breach that results in the compromise of personal information that is likely to cause serious harm becomes eligible under the Notifiable Data Breaches Scheme. Serious harm could be considered any of the following:
- Physical harm
- Financial/economic harm (e.g. credit card details compromised)
- Emotional harm (e.g. embarrassment, humiliation)
- Psychological harm (e.g. marginalisation, bullying)
- Reputation harm
5. Notify Affected Parties
It’s important to notify the affected parties following the breach, giving them an opportunity to further secure their accounts as necessary. They may wish to change account passwords, or freeze credit card accounts.
If the breach falls under the authority of the Notifiable Data Breaches Scheme, then you need to submit a report to the OAIC using their report form.
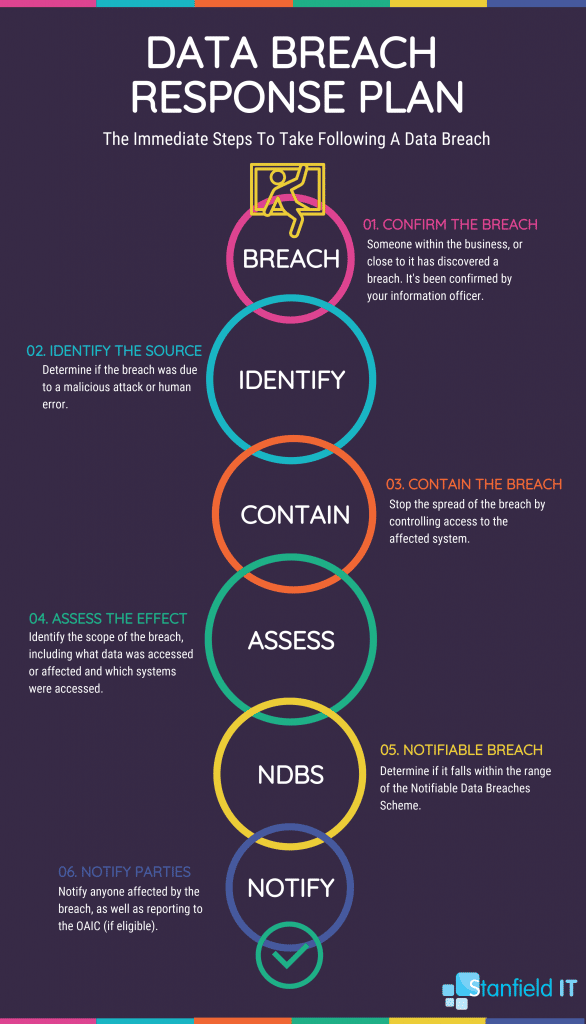
6. Follow Up: Audit Cyber Security
Once you have dealt with the immediate fallout of the breach; that is, identifying, securing and containing it. It’s time to conduct a review of your cyber security environment.
You can begin the audit process yourself by following the steps we’ve described here. This primarily comes down to learning the information processes within your business and reviewing existing security measures. Conduct further evaluation using our cyber security questionnaire and then employing specialised IT support to follow up.
7. Follow Up: Implement Additional Security Measures and Changes
In the wake of your auditing and review, it will be time to implement some changes and security measures within your business. Utilise the ASD’s ‘Essential Eight‘ as your primary security measures to start with. Beyond implementing the essential eight, some other security features you can choose are:
- Use a password manager
- Managed IT services for network monitoring
- Upgrade your anti-malware and firewalls
- Enforce strict data access policies
- Mobile device management
- Device encryption
8. Follow Up: Review Response Plan
After utilising your incident response plan (which you should have done following any incident), it can be a good idea to go back and review the plan. Revise it as necessary using your recent experience as feedback.
What worked from the plan? What didn’t? Was there anything missing that you should have included? Are there any redundant steps that are possibly outdated? As cyber security and technology evolves, it’s wise to periodically review and update your response plans accordingly.
9. Follow Up: Review Prevention Measures
Now you must review and test your prevention measures to ensure that the risk of another breach is significantly minimised. From your firewalls and anti-malware, to multi-factor authentication and administrative access.
Test the prevention measures, test your backups (you do have backups, right?) and ensure that your cyber security environment is healthy and working as required. The last thing you need is a missed vulnerability, due to something incredibly simple like a missed patch or update.
10. Follow Up: Revise and Refresh Staff Training
Last, but absolutely not least, staff involvement is key. Keep your team informed of any breaches or attacks, so they act with further caution and safety. But more importantly: educate your team!
As we saw above, human error plays a huge role in the rate of data breaches in businesses. The only way to combat that effectively, is to drill home the importance of cyber security awareness. Run cyber drills, or team sessions to review security issues. Enforce cyber awareness from day one and offer incentive for your team members to execute excellent cyber security etiquette. More staff awareness = less human error.
To Conclude
As we’ve emphasised above, no business is exempt from the risk of a data breach, but there is so much in your hands to change and reduce your risk. Don’t let cyber security be a taboo topic in your office but keep it alive amongst the team.
If you need more information on the best way to handle a data breach, or you suspect your business has experienced one, then our experienced team at Stanfield IT will be happy to answer your questions and get your business back on track.
