Cyber Security Services
Grow your business, win bigger deals, and build customer trust with our cyber expertise.
Trusted by Australian businesses like you







Nothing is ever an issue, all the staff are so helpful and knowledgeable. They have gone above and beyond for us and have been extremely customer focused.
Become. Architecture

All the staff are very professional and efficient. Follow up when needed. I feel they always put the customers first. Very happy with their service.
Women’s Legal Service NSW

They are responsive, they do what they say they are going to do and they are always able to assist us with any IT issue we may have.
Family Aged Care Advocates
Our Cyber Security Services
Cyber Strategy
Cyber Protection
Incident Response
Cyber Resilience
Auditing & Reporting
Reduce Your Risk
Lower your security risks quickly with our effective cyber security solutions.
Accelerate Growth
Get protected, compliant, and competitive, faster.
Build Trust
Show that you’re security conscious to win more contracts, speed up sales, and build stronger client relationships.
Cyber Strategy
Each business is unique, with its own set of challenges and risks.
That’s why our approach to cyber security isn’t one-size-fits-all.
Using best practices, we’ll create custom strategies that integrate with your business and help protect your digital assets
As the threat landscape changes, our services will guard you from today’s threats and future challenges, preventing reputational damage and maintaining your business integrity.
Risk Assessment
Identify & manage potential cyber risks.
Regulatory Compliance
Expert guidance on compliance requirements
Custom Security Consulting
Cyber security planning that aligns with your business.
Cyber Protection
Cyber threats are evolving, but so are our defences.
These services are your shield against potential threats – protecting your sensitive data, your systems, and giving you greater peace of mind.
With a range of proactive cyber security services, we can strengthen your network, ensuring your business stays secure and ahead of the risks.
Cyber Security Strategy Implementation
Implementing cyber security measures tailored to your business.
Device & Application Management
Keep your devices and applications secure, compliant, and optimised.
End User Training
Help your team recognise & prevent security threats.
Data Loss Prevention
Prevent data breaches & protect sensitive information.
Cloud Platform Management
Management of platforms like Microsoft, Google, and AWS.
System & Application Support
Support for your systems and applications.
Control & Governance
Helping you maintain higher security standards.
Deployment & Migration Services
Secure and smooth transition services for Microsoft 365 and Google Workspaces.
Networks & Connectivity
Secure network infrastructure for safe and reliable connectivity.
Compliance Documentation
Guidance on ISMS, SOE, and ISO 27001.
Disaster Recovery
Planning for quick recovery & minimal business impact.
Framework Management
Managing frameworks including The Essential 8, NIST, and ISO 27001.
Vendor & Asset Lifecycle Management
Management of vendor relations and asset lifecycle.
Infrastructure Management
Protect your physical and cloud infrastructure.
Communication System Security
Keeping your business communications private.
Password Management
Simple access management – easy to share.
Initial Response
Ensure immediate containment and minimise the impact of a breach.
Forensic Analysis
Detailed investigation to uncover the cause and extent of the breach.
Contingencies
Pre-planned contingencies to address and reduce the effects of cyber threats.
Recovery & Planning
Restore operations post-incident while proactively planning for future threats.
Incident Response
Respond and recover with confidence.
Even the best defences will face incidents. If they do occur, a swift and effective response plan is critical to minimise impact.
Our response services give you the ability to recover. They’ll ensure business continuity and help protect your reputation.
Cyber Resilience
Empower your organisation with our Cyber Resilience services, designed to not only withstand cyber threats but to thrive amidst them.
Our comprehensive approach encompasses rigorous defence and penetration tests and continuous strategy refinement, ensuring your defences are always at their strongest.
Defence Testing
Regularly test and strengthen your defences so you’re always ready.
Penetration Testing
Identify vulnerabilities before attackers do.
Attack Simulations
Prepare your team with realistic attack simulations.
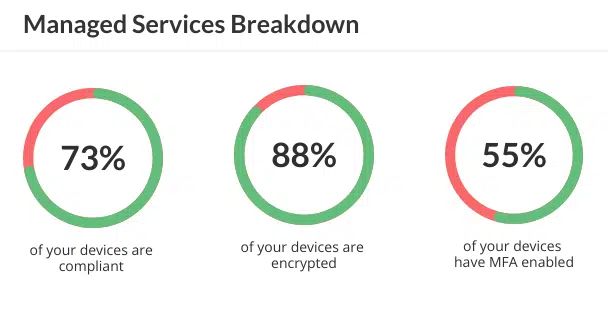
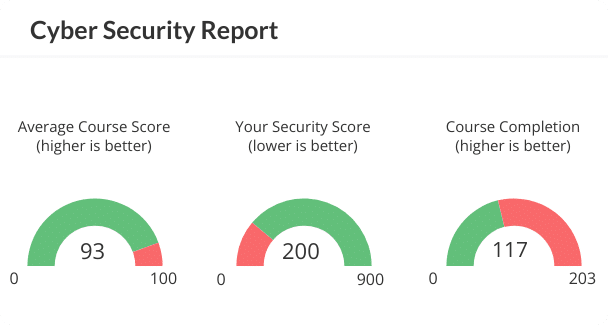
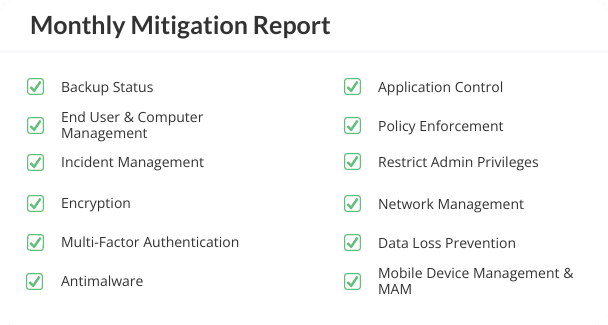
Auditing & Reporting
Stay informed, stay in control.
We provide a range of reporting options, from daily security updates to comprehensive annual overviews, all focused on your information security needs and criteria.
Our reports help you make decisions about your cyber security posture. Coupled with regular audits, they ensure regular oversight and adaptability.
Cyber Security Services Keep Your Business Secure
We have a dedicated team of service providers with the expertise to identify every potential weakness in your IT infrastructure and the knowledge to strengthen it, day in and day out.
See how your business can reach new heights in security using our awareness programs and security strategies. Let’s create a secure and resilient digital environment for your business and stakeholders.

We Only Work With Industry Leaders
Staying ahead requires the right tools. We believe in bringing you the best of both worlds.
Our proactive approach blends custom cyber security strategies with best-in-class tools and technology from industry-leading vendors.
This allows us to deliver strong, scalable and future ready security solutions that fit your needs and exceed your expectations.
About Us
We’re a team of in-house cyber security and IT experts. Nothing is outsourced.
We’re committed to providing cutting-edge cyber security solutions. Our mission is simple: to safeguard your digital assets and empower your business with strong cyber security.
Local Expertise
Our fully Australian-based team ensures reliable, locally informed services without the risks associated with offshore staffing.

Security Verified Team
Every new team member undergoes a rigorous security check by Equifax, ensuring a team that’s skilled and trustworthy.
Personalised Security & Client Management
With dedicated security consultants and account management, we offer personalised attention to each of our clients’ needs.
Is investing in cyber security expensive?
While there is an upfront cost associated with investing in cyber security, the potential financial damage from a data breach or cyber attack is far greater. Our services are designed to provide cost-effective protection for your business.
I don't have a technical background. Will I understand what's happening?
Absolutely. We make cyber security simple and accessible. We explain everything in clear language and ensure you’re fully informed about the measures we’re implementing.
Will implementing cyber security measures disrupt my business operations?
Our team is experienced in implementing cyber security measures with minimal disruption. We’ll work around your business operations and ensure a seamless integration process.
Will your services fit my specific business needs and industry?
Definitely. We understand that every business is unique, which is why we provide customised solutions tailored to each client’s individual needs and industry requirements.
What happens after the initial setup? Do you provide ongoing support?
Yes, we do. Cyber security is an ongoing process, not a one time event. We provide continuous monitoring, regular updates, and round-the-clock support to ensure your business remains intact.
Can your services help me meet regulatory compliance?
Absolutely. We understand the complexities of industry-specific regulations and standards, and our services are designed to help you remain compliant. We’ll work with you to understand your specific compliance requirements and ensure our solutions meet those needs.
Create a cyber resilient business
Grow your business and win more clients with our cyber security consultants by your side. We’ll help keep your customer data safe with a secure digital environment. You can rely on our IT security services to protect your business from online threats, offering you and your clients greater peace of mind.


