The Definitive Cyber Security Guide for Small-to-Medium Businesses
Cyber security should be a familiar term, especially if you’re responsible for running a business or have any involvement in handling information within a business. That covers everyone from the CEO to the customer service agent that needs to access and distribute account information. It’s so important now to realise that cyber security is no longer just the province of IT nerds, but the responsibility of the whole workplace.
Cyber security incidents are directly costing Australian businesses $29 billion per year. Just in case you thought that the importance of cyber security was being overrated. Spoiler alert: It’s not. The dictionary definition of cyber security is pretty vague:
Cyber Security: The practice of building, and maintaining the protection of your networks, devices, or data from cyber attack.
It doesn’t even come close to encompassing the full breadth of what cyber security truly entails. Cyber security covers a range of security factors from information management, to network architecture, to identity management, multi-factor authentication, scheduled backups, firewalls and mobile device management. And that’s just the tip of the proverbial iceberg.
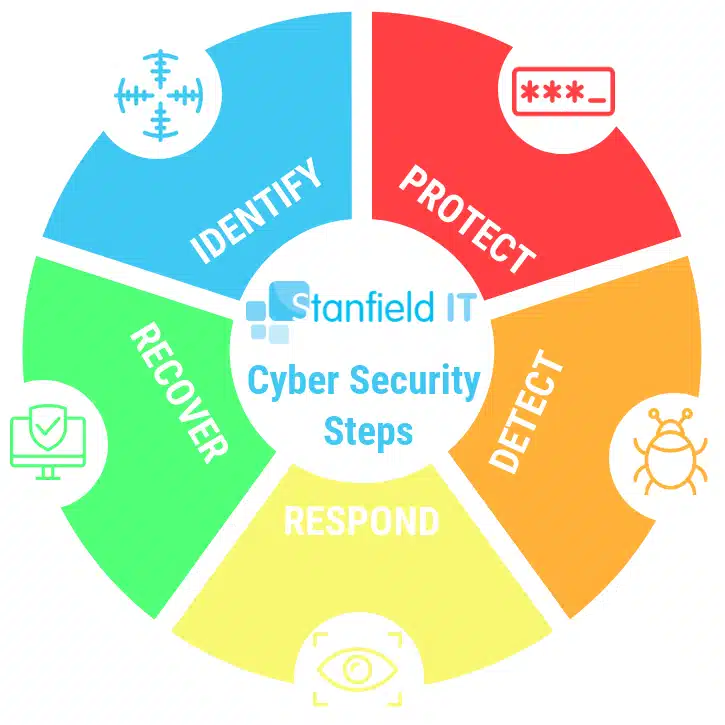
The Cyber Security Race
The biggest challenge in cyber security is that new risks and methods of attack arise literally all the time. How can you defend your system and information from brand new attacks that evolve overnight?
So, it becomes a bit of a race. A security patch for every new vulnerability, evolving firewall technology, AI-driven anti-malware software. Due to the constant evolution of attacks and risks, cyber security simply can’t be a matter of set and forget. It requires constant maintenance, consistent updating, and growth. It all sounds a little bit daunting, that’s for sure.
Overall, cyber security means you can’t just rely on Windows Defender to catch everything for you. It means controlling physical access to hardware and systems, not just network access. It’s understanding the nature of attacks, and implementing a security framework. Furthermore, it can come down to the smallest thing, such as remembering to lock your desktop when stepping away, or double-checking who the sensitive files are being sent to. As a result, cyber security falls into the hands of everyone within an organisation.
Why Does Cyber Security Matter?
Cyber security has existed in some form or another as long as computers, networks, and the Internet have been around. We’ve always recognised the need to protect our data, much in the same way attackers have recognised opportunities to steal data. In this advancing technological age, cyber security is increasingly critical and relevant. We have smart devices galore, and cloud services holding all of our data.
The Internet of Things has our fridges talking to our cars and our phones talking to our TVs. Without cyber security, we subject ourselves to attack. This compromises critical information or crashes critical systems.
Many businesses are now conducted entirely in the digital sphere. This means financial transactions, identity management, and life-saving data are all subject to attack. Our society has more or less progressed to managing our entire lives online in some form or another. Consequently, the need for high level cyber security is greater than ever.
It Could Happen to You!
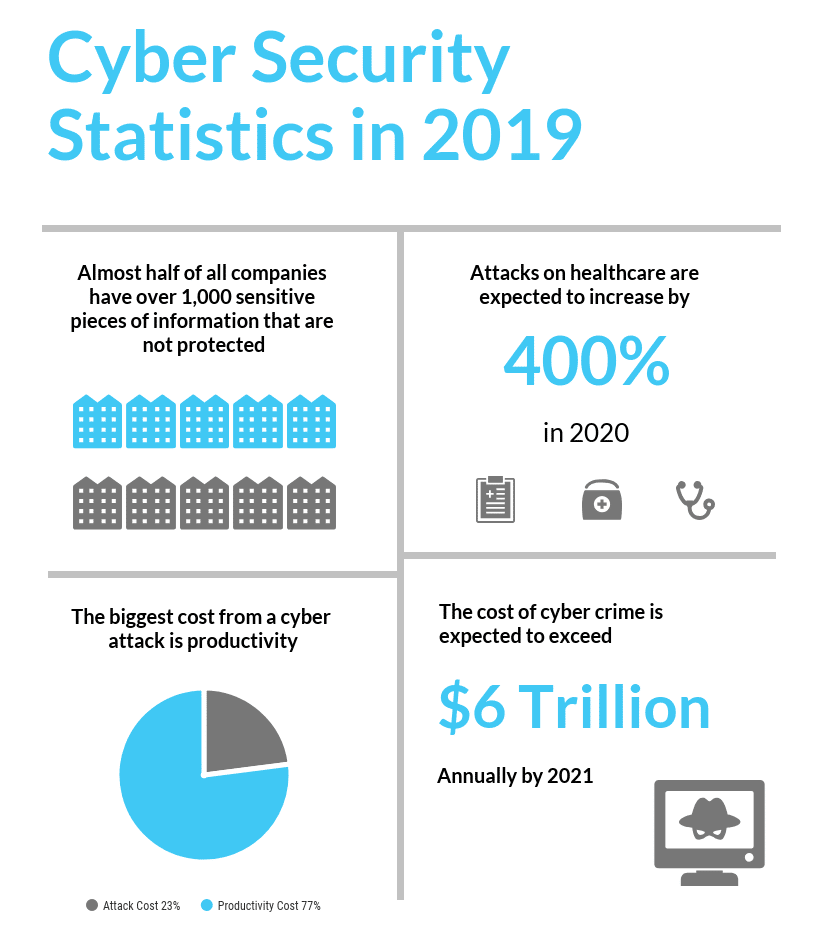
With smart devices in every home and office, and many of those devices being used in BYOD work policies (Bring Your Own Device), the risk of cyber attack or incident is higher than ever. Statistics show the increase in cyber attacks, and Australian businesses are taking the fall for not being prepared.
Cyber crime has grown at an enormously fast rate in the last few years and continues to grow. This is partly due to the difficulty in policing cyber criminals and the enticing financial gain to be had. The Australian Cyber Security Centre (ACSC) stated in their Threat Report that they had identified 47,000 cyber incidents over the previous financial year, marking a significant increase in cyber crime in one year alone.
Most importantly, 56% of all reported cyber incidents in the private sector were due to a compromised system. When we think of cyber security and data breaches, we think of some basement-dwelling troll hacking into our system, but lets acknowledge the biggest cause of data breaches shall we? Human error. Whether its a trusted insider, a third-party contractor, or vendor, there are always additional users with access to your data. These people are not infallible and need to understand the seriousness of following cyber security protocol.
Read Here for The Top Ways to Become a Cyber Resilient Business.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
Aftermath of a Cyber Attack
Getting hit by a cyber attack is a big blow to any business, but moreso for small-to-medium-sized organisations. Dealing with any cyber incident (be it accidental data breach or malicious attack) will mean several things. There will be a real financial cost in the wake of the incident, and it’s likely your reputation will also take a hit once word gets out about the attack. The following days and weeks will see continuity and productivity grind to a halt as you try to navigate your recovery. Let’s break down the different ways in which your business is impacted by a cyber attack.
Financial Loss
Unfortunately, virtual data breaches come with real-world financial costs. Don’t fall into the trap of assuming there is no actual monetary consequence to such an intangible event. Following an attack, you’ll likely see the following events:
- Instigate an investigation to locate the source and scope of the breach.
- Employ an IT security consultant to perform a security audit (in order to identify vulnerabilities).
- Associated PR and legal costs in order to manage company image, and time lost to notifying authorities and clients.
- Staff are taken away from their regular duties in order to handle inquiries and ongoing management of the breach.
- Employ an IT services team to reinforce your security perimeter, and implement solutions to address any vulnerabilities.
- Loss of clients and associated revenue due to breach of trust.
All of these steps ultimately incur a significant financial penalty that are all a direct result of the data breach.
Reputation Damage
With any system breach, you risk breaking your carefully crafted public image. You have to send that sheepish email notifying your client base that their private data has been stolen. Their private, financial, personally identifying information that is. They trusted you! And now their information is compromised.
You can take every step at that point to turn your system into Fort Knox, but the damage has been done. The trust is broken, and it doesn’t really matter if you couldn’t prevent it. You’ll need to pour a significant amount of time and money into this disaster in order to recover your reputation. You should think of your data as a shoe box full of embarrassing photos and love notes from your teenage years. Protect it at all costs, and never let its contents see the light of day.
74% of consumers said they would switch providers in the event of a breach.
Productivity
An obvious impact to take into account with any cyber attack is the loss of productivity. You will experience a significant drop in productivity due to heavy disruptions in normal business activity.
In order to determine the extent of the breach, you’re looking at halting sales, shipments, and performing ongoing investigations. Because of this time taken away from the business, you now have a significant loss in productivity and momentum. Not to mention lost profits during this time as well. Once you factor in the ramp up back to optimal productivity, you’re looking at a critical impact on your business.
Common Types of Cyber Vulnerabilities
There are a number of ways in which a business can be vulnerable to cyber attack. This is a little technical, but it can definitely be beneficial to understand the ways in which data can be exposed. A fuller understanding of the cyber security environment gives you a better ability to manage risks.
A cyber vulnerability is where you have the intersection of three factors.
- A weakness in the system.
- The attacker’s access to said weakness.
- The attacker’s ability to exploit it.
If we were to translate that into a layman’s analogy we could say that:
(1) the weakness is a security gate with a hole in it.
(2) is a burglar’s physical access to that gate.
(3) the attacker being physically able to squeeze through that hole and consequently break into the building.
There are so many ways in which your system could be vulnerable, and we could populate an article on that alone. For the sake of being succinct, however, we’ll just look at the five most common weaknesses:
Injection Flaws
An injection vulnerability can occur in any application that allows a query input that communicates with a back-end database. SQL is probably the most common example of this. This essentially allows the attacker to bypass the intended function of the application, and execute a malicious query. Using the SQL example, the attacker can input a malicious command that alters the path of execution. This can cause the program to retrieve and dump sensitive data into unauthorised hands.
Buffer Overflows
A buffer overflow vulnerability is a common weakness that is frequently present in operating system code. While buffer space and memory layout is generally well-defined, sometimes anomalies occur where you have too much data input. This causes the buffer space to ‘overflow’. It is in this overflow space that an attacker can enter malicious executable code and potentially gain access.
Sensitive Data Exposure
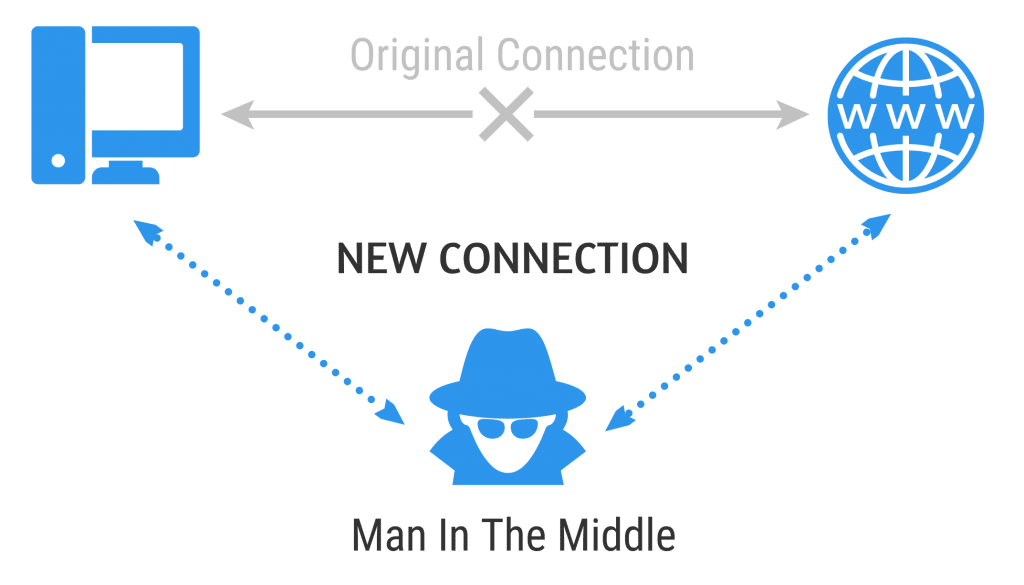
This one is a little more self-explanatory. Sensitive Data Exposure occurs when an application does not sufficiently protect sensitive information from being disclosed to attackers. The attacker could, for example, intercept the data between a server and a browser. This is creatively known as a Man-In-The-Middle attack. The biggest cause of this weakness is a lack of encryption, weak key generation, and algorithms.
Broken Authentication & Session Management
This type of flaw is difficult to eliminate due to the variety and number of authentication methods. Each user can employ different methods, and there are multiple ways an attacker can bypass these mechanisms. They could for example, use the aforementioned injection attack to retrieve a session identifier, or reuse an old session token. With that, they could access your online banking, because they’ve tricked the server into thinking you never logged out. Yikes.
Security Misconfiguration
This type of flaw is possibly the most common and dangerous of all. Some examples include: running outdated software, applications running in debug mode, running unnecessary services on the system, not changing factory settings (e.g default passwords), and incorrect exception management that allows system information to be disclosed to attackers. Thanks to some ethically-dubious products on the market, an attacker is easily able to identify systems that are not properly configured.
How To Identify Cyber Vulnerabilities
Now that we’ve covered the common type of cyber vulnerabilities, the next issue is, how do you identify them? How do you assess if you are exposed in this way? Luckily, there are software tools created for exactly this purpose (thank you Symantec, Trend Micro, and NetIQ, amongst others).
But bear in mind that it’s unwise to simply rely on a piece of software to handle all your risk assessment for you. A truly thorough risk assessment should involve a comprehensive protocol alongside specialised software. This software doesn’t just identify, but also analyses, evaluates, and manages all vulnerabilities in a structured manner.
Easy Guide To Understanding Your System
The best thing you can always do for yourself and your business is to be involved, regardless of your current cyber security status. You need to learn about and understand the current state of security. Take part in actively screening potential vendors or third-parties, and be engaged with the whole process of protecting your business.
We’ve put together a simple step-by-step process you can follow to identify and understand your security status and where your vulnerabilities lie. Follow these simple steps to get a good understanding on your organisation’s cyber security.

Types of Cyber Attacks
What type of threats should you anticipate with regards to these weaknesses? Attacks can come in several different forms and this information can be overwhelming. However, as long as you address your vulnerable points, you’ve already done the important part.
Another part of taking a proactive role in the security of your business means understanding the types of attacks you could be subject to. Arming yourself with this information means you’ll be more likely to recognise things like phishing scams or the signs of malware in your system. The following types of cyber attacks are among the most common.
Malware
Malware is somewhat of an umbrella term that includes trojans, worms, spyware, ransomware and viruses. Its basically defined as a malicious code or software with the intent to corrupt or steal something on your system.
Malware usually gets introduced to the system through an email attachment or an unsafe download. Sometimes its attached to a frequently used and trusted website so you’ll allow the malware through your anti-virus software.
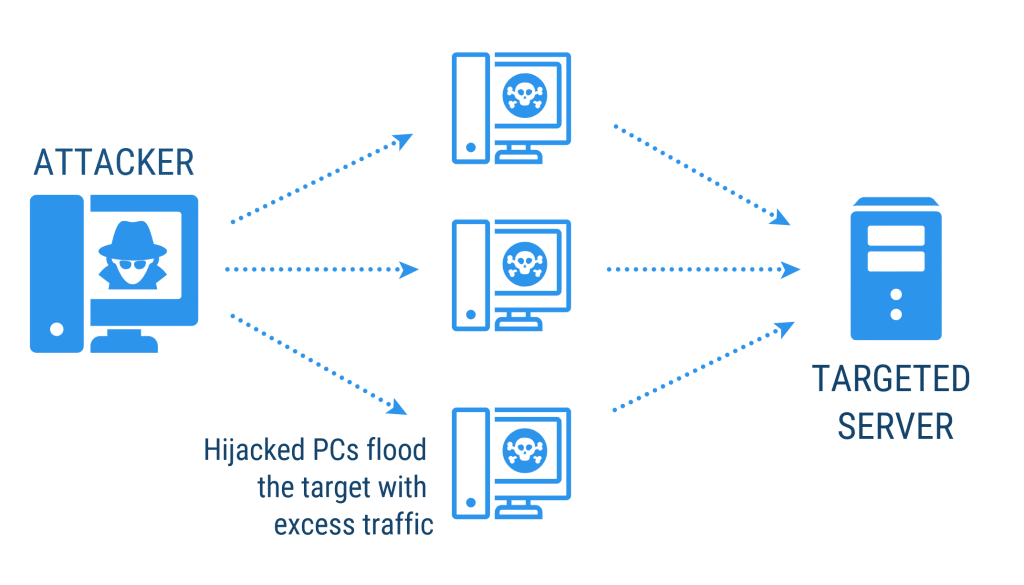
Distributed Denial of Service (DDoS)
DDoS is an attack that focuses on disrupting service to your network. Attackers send high volumes of traffic through the network until it becomes too congested and can no longer function. Attackers often use multiple computers to send the traffic or data; hence distributed.
Users often won’t even realise that their computer has been hijacked to participate in a DDoS attack. These attacks primarily target huge companies, often in protest towards governments or individuals.
Phishing
Phishing attacks are almost always sent by email. They’ll appear to be a trusted source that will ask you to click a link and enter personal information. They could be posing as your bank, and asking you to ‘verify’ your password by clicking on a link. These are usually pretty easy to spot, but they’ve definitely grown more sophisticated in recent years. They can closely resemble official emails from parties like Apple or PayPal.
A tried-and-trusted method for avoiding these traps is to remember that your bank or any other trusted site will never make such requests via email.
Read Here For Clear Ways To Identify Phishing Attacks.
Ransomware
This type of malware is self-explanatory—it’s as its name suggests. Ransomware is a type of malicious software that will effectively hold the victim’s data hostage in exchange for a ransom. Your data becomes encrypted and completely inaccessible without the decryption key. The attacker will usually threaten to completely destroy the data if their ransom demands are not met.
Most perpetrators are not prosecuted, since ransoms are almost always paid in cryptocurrency (which is nearly impossible to trace). Ransomware attacks are typically carried out by exploiting a vulnerability with a trojan.
Brute Force Attack
The brute force attack can also be called a password attack. The brute force attack is fairly self-explanatory in nature. Previous methods attempt to trick the user into allowing the malware through, or find a backdoor into the system. However, the brute force method employs an algorithm or software that will literally try to deduce the password.
The algorithm will run thousands of word and number combinations, sometimes even comparing against a dictionary for potential words. Hence, it’s so important to create a strong password, including upper and lower-case letters, numbers, and symbols, as well as change it on a regular basis.
Rogue Software
Rogue software is another type of malware, but has a key difference that is important to note. It will disguise itself as critical security software that will keep your system safe. They create legitimate looking pop-ups and alerts, often masquerading as updates to existing security software, or terms of service agreements. Through these pop-ups users are tricked into allowing the software to access their system.
Man in the Middle
We briefly mentioned this one earlier when discussing Sensitive Data Exposure. The way this works is by impersonating the endpoints in an online data exchange. From your computer to your online banking website, for example. The ‘man in the middle’ impersonates the bank to communicate with you, while also impersonating you to communicate with the bank.
Therefore, they receive all the information traveling between the two and gain access to sensitive information. Use an encrypted wireless access point, and always look for a HTTPS connection. Take these simple precautions, and you are less likely to be targeted by this attack.
Watering Hole Attack
This is a strategy for delivering malware in which the victim is a particular group (like an organisation or an industry). Watering Hole attacks happen when the attacker targets a website or websites that are frequently used by members of the group. They infect these websites with malware as a trap.
Eventually, a member of the group will fall prey to the malware and from there gain access to the whole network. Given the large number or users exposed to the infected site, this type of attack is extremely difficult to trace.
Social Media Threats
Not even our beloved Facebook is safe from cyber crime. Now social media platforms like Facebook, Twitter, or LinkedIn are being used to deliver cyber attacks. They often achieve this by exploiting broken authentication and stealing login credentials, or through phishing attacks.
Once logged into Facebook, you could receive a download link, or a rogue friend request and you should absolutely be wary. Users must take extra caution due to the fact that Facebook is integrated so thoroughly into all aspects of online life. It’s incredibly common to use your Facebook login for an infinite number of sites and apps, so giving up your social media security could mean so much more than just access to your friends’ list.
Unpatched Software
Unpatched applications and programs present a real vulnerability that can be exploited for attack. Consider browser add ons and programs like Adobe Reader or Flash. You frequently use these to make your online experience smoother, without so much as a second thought. These programs often have regular updates, so it’s important to ensure you apply them to reduce your risk of attack.
Simple Steps To Increase Your Cyber Security
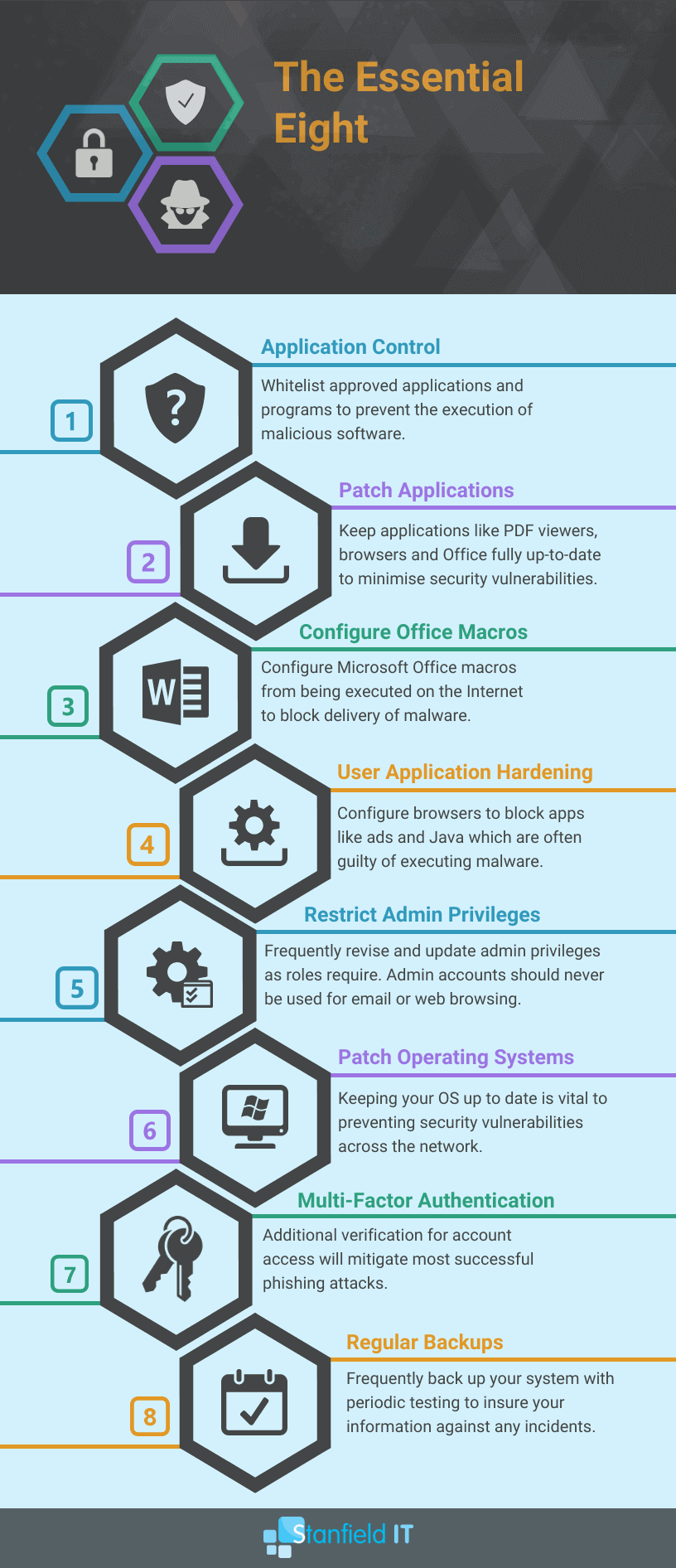
So far we’ve covered ways to identify key vulnerabilities, and ways in which you may be targeted for attack. However, there are a few key practices you should be employing to proactively minimise your risk of an attack. The Australian Signals Directorate has published a list of strategies to follow that will help mitigate any chance of an incident. They call these the Essential Eight.
20 Additional Tips For Securing Your System
1. Use a Password Manager
The downside of having multiple passwords that fit the requirement of being long, complex and random is that it becomes incredibly difficult to remember them all. Enter: the password manager! A password manager stores your passwords securely by encrypting them and offers the ability to share them safely. When you want to disable their access, you can do so without needing to change the password. Have a look at password tools like LastPass or Dashlane.
2. Use a Next-Gen Firewall
A next-gen firewall is part of the third generation of firewall technology, meaning it combines traditional firewall with more sophisticated functionalities for detecting and preventing intrusion. They generally include anti-malware and anti-virus that are continually upgraded as new threats are discovered. FortiNet and Cisco are both among the top NGFW tools on the market.
3. Restrict Access To Data
Regularly evaluate your system and ensure that your staff only have access to the data and networks that they actually require to perform their job. The less people you have exposed to sensitive data, the less likely that such data is going to be compromised (either intentionally or accidentally).
4. Use AI-Driven Anti-Malware
These malware detection programs use clever algorithms to immediately detect and contain any malware, often detecting intrusions before they take effect. There is some debate on whether it’s really AI, or just advanced machine learning, but the end result is the same—an anti-malware program that handles threats before you’re even aware of them. Just avoid the one called Skynet. Check out tools like BitDefender and Cylance.
5. Conduct a Vulnerability Scan
Performing a vulnerability scan of your entire infrastructure will help to highlight any security weaknesses in your system. You can do it yourself as an individual using an entry-level scanner tool, or employ an IT expert who can use a more sophisticated enterprise-level product. We discussed this briefly above in more detail, but if you want to review some scanning tools, check out Detectify and Nessus.
6. Cyber Security Audit
A cyber security audit should give you a clear idea of your problem areas and what issues you need to deal with regarding your information security. There are audit questionnaires you can use yourself to get an idea of where you stand. Or, you can opt to take your business to an IT company that specialises in cyber security and ask them to take your security to the next level. We’ll review this further below.
7. Educate Your Team
This is one strategy that doesn’t require any big spending, and we will always advocate for this. Ensure that your team understands the risks and gravity of information security—they will be your biggest defenders if they’re alert and aware. Teach your team to identify cyber risk so they make safe online choices. Suggestions to engage your team are to:
- Run a ‘lunch and learn’ session where you review the latest security vulnerabilities and issues.
- Perform a ‘cyber drill’ so staff experience a simulated attack, or phishing attempt.
- Start cyber awareness from day one of hiring to enforce a security mentality.
- Offer incentives for executing excellent cyber security awareness and management.
8. Mobile Device Management
Implement a mobile-device-management solution within your business. There are numerous MDM tools you can use, and many have their pros and cons. Ultimately, they work to secure your company data and your employee’s personal information. A good MDM tool allows you to provide your staff with access to business apps and data on mobile devices without requiring individual device enrollment.
Compare the MDM Tools on the market HERE.
9. Encrypt All Devices
All your devices should be encrypted—this means computers, mobile devices, hard drives, and storage. Encrypting the devices means that your data is incomprehensible without a key. Basically, if someone gets access to your laptop or mobile, they can easily access files and data without encryption. If encrypted, your files are still protected in such an instance.
- Device Encryption for Windows
- Data Encryption for Mac OS
- Encrypt your Android device
- Encrypt iPhone backups
10. Enforce Strong Password Policies
Passwords are the key to your accounts, so why make it easy for others to guess or hack? Create a policy of strong passwords in your work place and enforce it. Ensure your staff create complex, random passwords to boost security and change them periodically. Tips for creating strong passwords:
- Use passphrases made up of at least four words that you can remember
- Don’t include any personal information or meaningful dates
- Practice Password Etiquette
11. VLANs
A VLAN is a group of devices that appear to be on the same local network despite their physical distribution. Hence the name “virtual local area network.” This drastically improves the security of such a network. VLANs also allow you to virtually segment devices or departments on different networks to improve security—you may have heard it referred to as ‘network segmentation’. As long as you have a VLAN-capable switch, you can do this.
12. Regularly Evaluate Permissions
Make sure to conduct regular evaluations of who has permission to different systems in your network. This includes systems that have been opened with APIs. Due to staff turnover or evolving roles, permissions should be periodically updated and reviewed.
13. Control Removable Storage
Control removable storage media and connected devices, which can easily carry or transmit malware to an unsuspecting or unprepared computer. Don’t allow anyone to just bring in their thumb drives willy-nilly! You can even disable drives so employees aren’t able to put information on removable media.
14. Web Content Filtering
Use your firewall to set up web content filtering. The filter works by identifying the origin or content of a web page based on rules you have defined. This can help you avoid visiting malicious pages. Content Filtering will significantly improve your security by blocking access to malicious or risky websites, utilise your policy-based controls and prevents malware download.
15. Guest WiFi
Set up a WiFi specifically for guests that is separate from the one you use for work. The guest WiFi should have no access to your internal networks. This way, your guests have internet access but not access to your data.
16. VPN
Using a VPN is a simple but thoroughly reliable security measure. It protects your network from being exposed to the network, or other unsafe networks, by encrypting your information and providing a secure network of communication. You can set up a VPN software on Windows or your Mac OS. Alternatively, you can use your existing security solution, such as FortiGate.
17. Identity Management
Identity management is all about defining and managing the roles and privileges of your individual users on the network. How do you define who can access what? Have you separated customer identities from employee identities. Each individual should have one identity. This way, you can monitor activity and immediately identify who performed what action.
18. Incident Response Plan
An incident response plan gives your team a set of steps to follow to manage and mitigate any data breaches or other incidents. Tailor the response plan for data breaches and information security. If you’ve got a framework implemented, then it should also provide an incident response plan for you to follow.
19. Network Monitoring
With a cyber security monitoring system implemented, you’ll be able to consistently monitor critical systems and data. With this you’ll be able to know straight away if there’s any suspicious activity or data breach.
20. Physically Protect Equipment
Seems simple enough, but it’s also important to physically protect and restrict access to your critical equipment as much as you need to restrict virtual access. Data can be accessed or compromised through physical access, too! Some tips for creating a physically secure environment are:
- If you have a dedicated server room, ensure it’s locked whenever not in use, and clear policy about who has access to the key or code.
- Set up surveillance in the event of unauthorised access.
- Use rack mount servers as they are easier to secure.
- Any portable or vulnerable devices should be locked away.
- Shred or destroy unwanted printed documents that may contain sensitive information.
Check our expanded list on security strategies here.

Cyber Security Framework & Guidelines
Don’t stress if the wording gets a bit technical here. We’ll try not to bog you down with too much jargon. There are set frameworks and guidelines in place you can follow to maintain cyber security compliance, like a checklist for hitting all the right steps to secure your network.
The Australian Cyber Security Centre (ACSC) is a fairly new collaborative organisation the Australian Government has pieced together from existing federal agencies with the sole aim of bolstering the security of Australian networks. The ACSC has put out multiple documents outlining important cyber strategies and threats to watch out for, though their Cyber Strategy document refers to the overall government strategy and action plan for strengthening Australian cyber security in general.
What is a Cyber Security Framework?
A Cyber Security Framework is a set of documented processes that are used to define policies and procedures around the implementation and ongoing management of information security.
Think of it as a template for your organisation’s cyber security. Many organisations publish and maintain different frameworks for general use, though when you first start digging, you’ll mostly find US-based guidelines that aren’t recognised in Australia. Not so helpful, but we’ll steer you in the direction of some more useful framework resources. Here are a few resources and guidelines out there for Australian businesses and individuals to refer to:
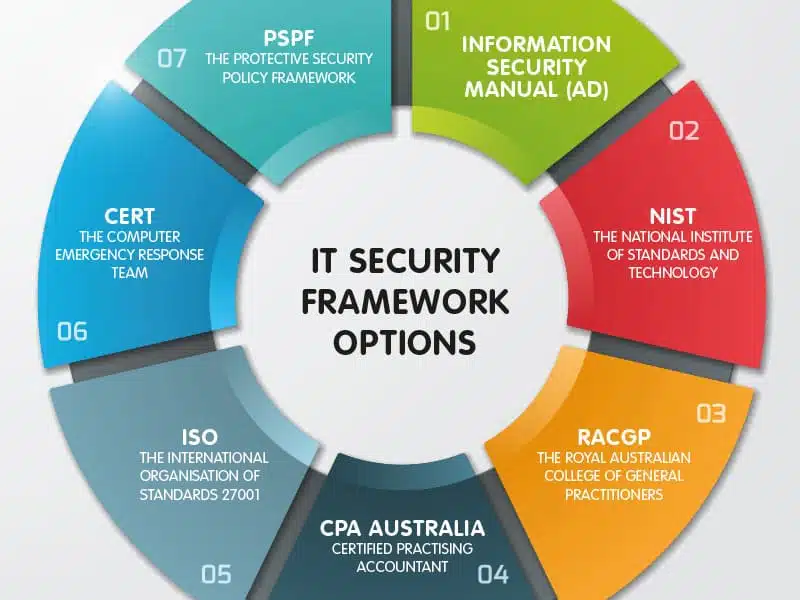
Information Security Manual by ASD
This manual is divided into multiple parts, but most of the relevant information for businesses is in Principles and Controls. This set of guidelines describes the compliance standards expected of Australian government agencies, but much of it is non-specific in its approach. Therefore, you can apply these guidelines to your private business or website as well.
Information Security Manual – Australian Government
FIRST
FIRST (Forum of Incident Response and Security Teams) is a collective organisation of response teams that handle computer security incidents and promote incident prevention programs. They have their own publication of standards, and a Best Practice Guide that details all the steps recommended to best protect your website from any incidents. FIRST contributes to external standards bodies like ISO, which lends a great deal of credibility to their organisation. They have a clear layout of their own created standards that are easy to find and follow.
NIST
NIST (National Institute of Standards and Technology) is a U.S. agency established to provide industry standardisation and measurement solutions. Their cyber security framework also adopts a risk-management approach, comprised of three parts. Between them all, these parts cover industry standards, guidelines, and cyber security activities. While this is a U.S. based framework, there is no reason the steps and guidelines in it cannot be useful to an Australian-based business.
RACGP
It’s no surprise that RACGP stands for none other than the Royal Australian College of General Practitioners. They have published a set of standards that are applicable to all general practices, and other office-based practices. This set of standards doesn’t only focus on risk assessment, but also managing availability of information. Furthermore, it covers backup processes, business continuity and recovery planning, and access management.
The 5 Healthcare IT Services Your Business Needs
CPA Australia
CPA have published an array of articles and webinars focusing on the best ways to secure your information. Their document IT Checklist covers the whole range of topics on IT system management and cyber security. They focus on a similar approach to the ACSC’s Essential Eight steps for security management.
ISO
The International Organisation of Standards does seem to be the place to go when looking for cyber security standards. ISO 27001 focuses mainly on information security management systems. It’s an extremely detailed document covering all aspects of information security from establishing a management system, through implementation, maintenance, and improvement.
CERT Australia
CERT Australia is the national computer emergency response team. They primarily provide advice and support on cyber threats and vulnerabilities. They also offer guidelines and advice on how to mitigate cyber threats, as well as monitoring cyber incidents. CERT has developed several useful framework documents that can benefit your security.
– Remote access protocol that can be implemented into your cyber security framework.
Protective Security Policy Framework
This framework is a dedicated set of policies and protocols that provide guidance for protecting assets and information. This covers all types of security protocol, but they do have a dedicated document for information security management. This set of protocols was developed by the Australian government for governmental agencies but again, can provide the tools and guidelines that can be used by a private organisation. Review this framework here.
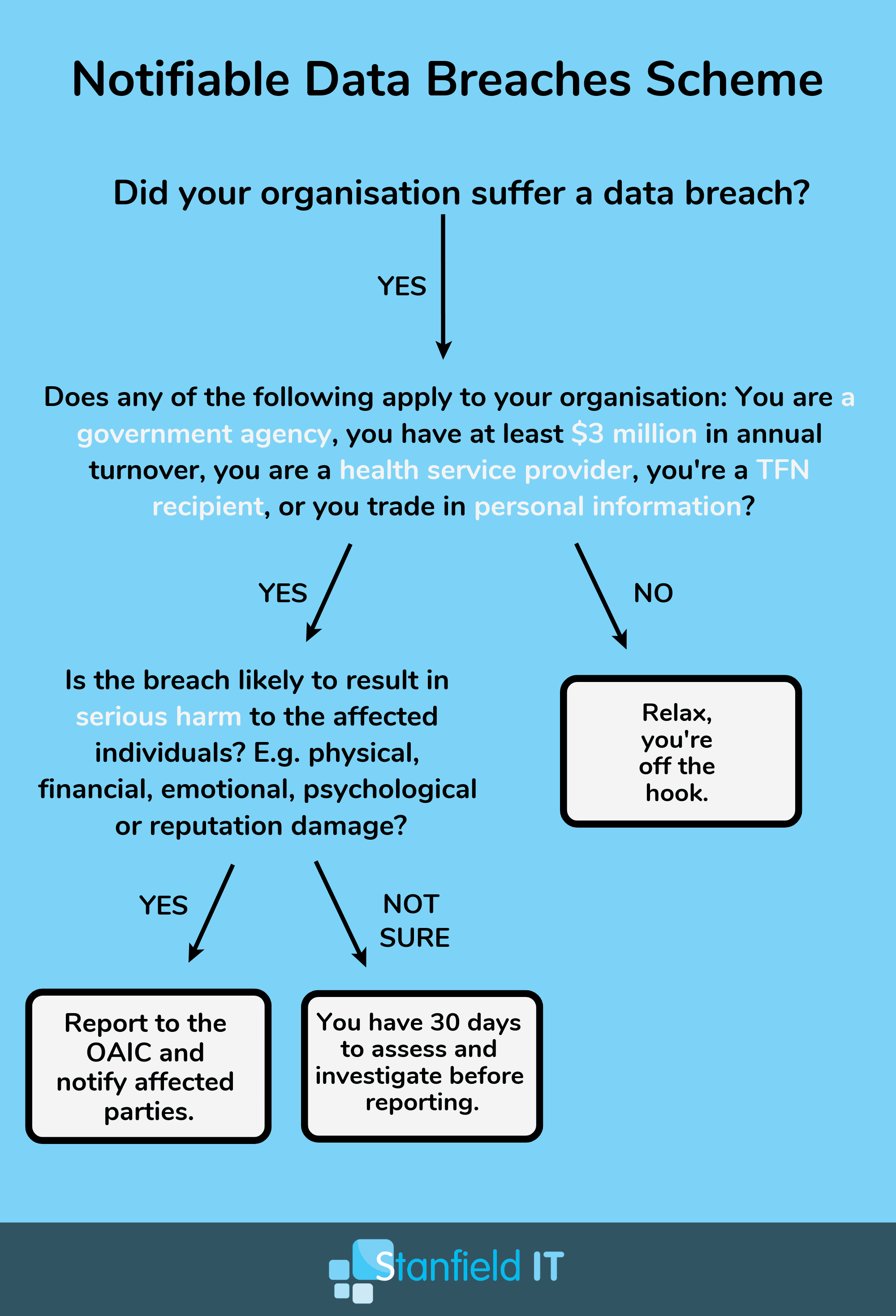
Notifiable Data Breaches Scheme
The Notifiable Data Breaches Scheme is a governmental legislation that only just came into effect on February 22, 2018. This scheme creates an obligation to notify individuals whose personal information is involved in a data breach that is likely to result in serious harm. This notification must also include recommendations about the steps individuals should take in response to the breach. The Australian Information Commissioner must also be notified of eligible data breaches.
The NDB scheme applies to agencies and organisations that the Privacy Act requires to take steps to secure certain categories of personal information. Therefore this includes Australian Government agencies, businesses, and not-for-profit organisations with an annual turnover of $3 million or more, credit reporting bodies, health service providers, and TFN recipients. Check if your organisation falls under this scheme.
The NDB scheme only applies to data breaches involving personal information that are likely to result in serious harm to any individual affected.
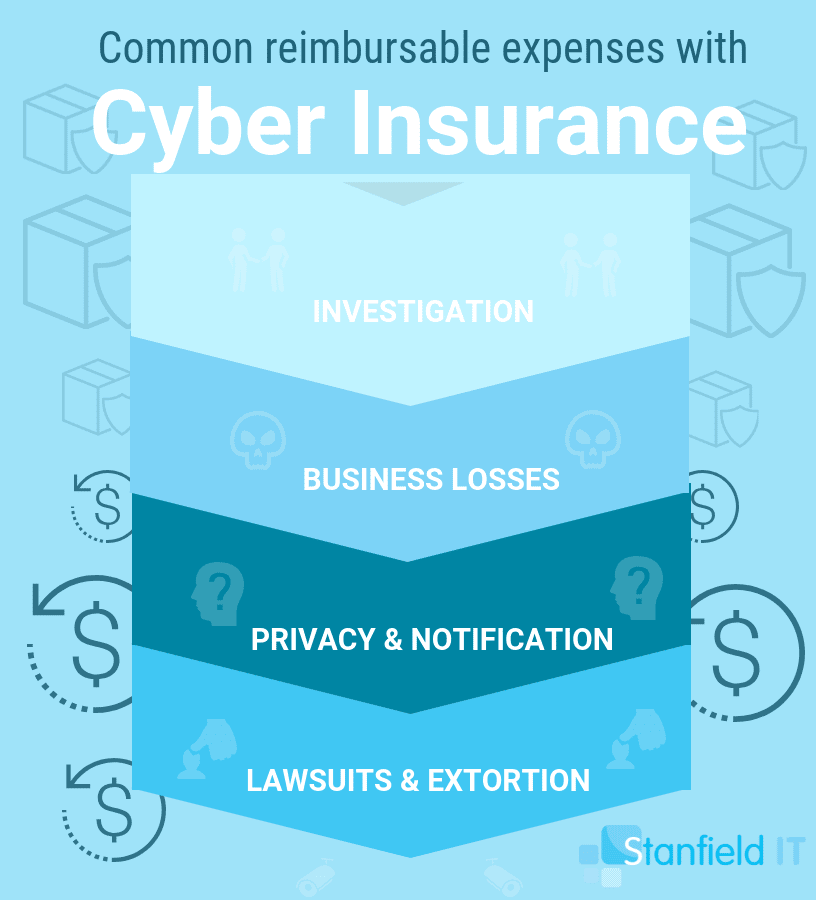
There’s Always Cyber Insurance
So, let’s say the worst comes to pass, and, despite all your best efforts to secure your information and networks, some malicious troll compromises your data. Enter: Cyber insurance. Cyber insurance can provide your business with an added layer of assurance in the case of a cyber incident.
It can’t protect you from a cyber attack, but the insurance can cover many of the associated costs. Investigations, customer notification, credit monitoring, public relations, legal costs, compensation, loss of revenue, and more.
In order to find a fit for you and your organisation, investigate what risks are covered by the policy. One thing cyber insurance cannot do, though, is recover the loss of intellectual property or prevent any reputation damage incurred as a result of a data breach.
Cyber insurance is still a pretty new type of policy, so coverage and premiums may not be flexible or diverse. Your best bet is still to minimise the risk of any incidents from the inside and hope you never actually need to use the insurance.
Case Study: PageUp
PageUp is a medium-sized Australian company that provides a cloud-based HR management software. It currently serves clients all over the world. Recently they suffered a security breach and we have been able to watch this play out in almost real-time due to PageUp’s transparency and responsiveness.
What Happened?
On May 23, PageUp detected unusual, unauthorised activity on their IT infrastructure, and immediately took the initiative to launch a forensic investigation. Their initial investigation revealed that a malicious code was executed within PageUp’s systems.
First Response
PageUp’s response was to launch an investigation immediately with the assistance of a third-party cyber security organisation, as well as advise Australian regulatory bodies in keeping with the Notifiable Data Breaches Scheme. By May 28, they located indications that client data had been compromised. On June 5, the CEO released an announcement advising of the potential breach and ensuing investigation. PageUp was very proactive and forthcoming with information with all regulatory bodies, but most importantly, with their clients.
Ongoing Communication
PageUp continued to keep their clients and public informed with progress updates. On June 12, the CEO posted another update confirming that they had contained the breach and secured their site. The organisation advised that their site had no further threats and was safe to continue using. They also made sure to announce that some types of personal data had been accessed and listed specifically what information had been potentially compromised.
Further Action
Aside from launching a forensic investigation, PageUp contacted the Australian Cyber Security Centre (ACSC), the Australian Federal Police, and Australia’s Computer Emergency Response Team (CERT) to advise them of the incident and draw support.
On June 17, they posted another update advising they have liaised with the Office of the Australian Information Commissioner (OAIC). PageUp offers steps and suggestions on what the individual can do from home to further insulate themselves from cyber risk, namely changing passwords, implementing multi-factor authentication, etc.
Impact To The Business
This breach had a significant impact on PageUp. Many customers lost faith in the platform, and opted to cancel their contracts following the breach. Australia Post was one of the big-name clients who chose to sever their connection with PageUp and moved elsewhere for their recruitment solutions. PageUp was also forced to delay their ASX listing, which was due to commence in 2018.
There was also discussion of a class action lawsuit being launched against PageUp due to the breach.Overall they suffered real brand and reputation damage which translates into financial loss for their business.
Resolution
As of July 2018, the investigation is ongoing to determine the extent of the breach and which records were affected. On June 19, they shared another update; the ACSC, the Office of the Australian Information Commissioner and IDCare released a joint statement on the issue.
On 21st November, their forensic expert confirmed there was no conclusive evidence to suggest data was taken in the incident.
Conclusion
As a business with many high profile clients, including most of the ASX200 companies, it’s highly likely that PageUp already had a business continuity plan in place. They promptly sprung into action and opted for a route of transparency with their clients, as well as the public.
However, it goes to show that, despite the best laid plans, an unforeseen security incident such as this (i.e. an attacker installed tools to steal data), clients still lost faith and some chose to take their business elsewhere. The damage to both their reputation and finances was severe.
Overall, this incident demonstrates the need for a well-established response plan and the need to have extensive preventative measures in place. Prove that you are committed to protecting your client information through transparency and communication (people love integrity). It shows that you are serious about cyber security and understand the negative impact that a data breach can have.
Current Cyber Security Trends
Now that you’ve learnt the ins and outs of cyber security in Australia, let’s take a look at what the cyber security trends look like now, at the start of 2020.
LoT-based Attacks
The time for IoT (Internet of Things) devices is now, with people utilising the Internet of things in both their personal and work lives. There is a whole new market for smart speakers (like Google Home, Alexa, and HomePod), as well as smart lights, plugs, and whitegoods. Public transport, urban spaces, and workplaces around the globe are installing IP-connected devices.
With every exciting, technological advances comes heightened cyber security risk With these new devices and technologies surrounding us, people aren’t considering how their data could be compromised in new, sneaky ways. IoT attacks are a true threat for businesses, and even countries (essential infrastructure, like utilities, can be targeted).
Thanks to the IoT boom, we’re seeing increasing attacks on devices that have little or no inbuilt security, as people are connecting them to the Internet. Many of these devices are in our small-to-medium businesses, connecting to corporate IT systems and putting personal and company data at risk.
More Supply-chain Attacks
Supply-chain attacks are a leading security threat that business owners and IT managers need to face. A supply chain causes strong potential cyber security risks, as stakeholders may have access to business systems, but lower information and information-security standards. This can also come about from business partners not exhibiting the same level of training that exists in your business.
It’s important to note that, when it comes to playing it safe with cyber security, a contract is not enough. Although, legally, the responsibility for the breach lies with the supply chain, there’s no guarantee an SME within the supply chain will effectively flag cyber security risks and manage this appropriately.
Zero-trust to Digital-trust
The zero-trust model won’t automatically trust any user, system, or service operating from within a business’s security perimeter. It tries to verify everyone who is trying to access the network. Historically, the zero-trust model was viewed as overkill. But, today, it’s standard in enterprises and making its way into smaller business models, too.
As noted by Matthew Gyde, Group Executive—Cybersecurity at Dimension Data, the zero-trust model has the downside of, in some cases, decreasing productivity. This can make it difficult to implement as a cyber security measure—though, if it prevents a breach, it is worth its setbacks.
Moving forward, the trend looks like ‘zero trust’ will evolve into ‘digital trust,’ which will see threat-intelligence tools being combined with internal authentication. This is the process of automated threat seekers looking for fraudulent or compromised credentials on the dark web. They then alert the organisation to this, flagging that this user as untrustworthy. The next step is that the compromised account is reset by internet-security teams and an accurate version of the user’s digital footprint is reinstated.
Insurers Become Strict on Non-compliance
Since 2018, Australian businesses have been having a real focus on data privacy regulation. We have taken Europe’s GDPR (general data protection regulation) on board and have also implemented our own NDB (notifiable data breaches) scheme.
2019 saw these regulations being a given and the number of insurers asking businesses to provide proof of compliance has risen. The big-name are very on top if the financial risks that insurers are exposed to when they agree to cover non-compliant businesses. The result? Unfortunately, Australian businesses are left with no choice but to lower their premiums.
Some organisations are even being made to hand over full-penetration test reports—certified by an external party—of their applications and networks. Many businesses are also now finding themselves in the market for extra premiums for cyber insurance, where their insurer has to rate them with a score that shows how likely a breach would be and charging them in accordance to this. This means that the more effort a company invests into their cyber security, the less their premium will be.
Implementing Cyber Security from the Get Go
Today, businesses are realising that they need to be secure by design. This means implementing security measures throughout the process of designing and adopting technologies, not after as it has been done in the past. Cyber security has to align with the business goals and objectives, too, for it to be truly effective. On the back of this, businesses today are realising that they need to identify if any sensitive information has been compromised by conducting regular data-risk assessments.
BYOD Increases in Popularity, as Does its Policing
The significant rise in BYOD (bring your own device) to the workplace has resulted in new, sometimes simple and easy, ways or hackers to access corporate data. MDM (mobile device measurement) or MAM (mobile application management) need to be applied to try and mitigate this increased cyber security risk that BYOD allows.
MFA (multi-factor authentication) is also a no-brainer when it comes to BYOD in workplaces. Requiring staff to verify their identity on multiple devices upon sign-in is a simple, easy way to eradicate a huge portion of the cyber security risks BYOD brings.
Sharing Data Within the Business
While data is born in silos, it’s most valuable when it’s accessible across different departments in your business. This is especially relevant to information-centric industries like financial services, retail, tourism, and fast-moving consumer goods. In such industries, competitive advantage is gained via data, making the quickly, daily sharing of data within these organisations a critical ingredient to their success.
Unfortunately for the cyber security side of their organisations, these consumer-centric industries also keep large amounts of PII (personally identifiable information) about people on file. This data is then rapidly shared among departments, third parties, and business partners. This results in one thing: an increased risk of a data breach.

Review Your Cyber Security Status
In addition to the simple evaluation guide published above, we have here a questionnaire you can apply to your business to further assess your current cyber security status. This is not an exhaustive list, but it’s an excellent starting point:
- Does your organisation have cyber security policies and procedures in place?
- Does your organisation protect all sensitive information transmissions (ie with encryption, SSL)?
- Are all devices protected from the Internet by a firewall?
- Does your organisation have designated cyber security personnel and/or a cyber incident response team?
- Does your organisation have a cyber security user education and awareness program?
- Do you perform cyber security audits annually?
- Are all users with access to devices containing or processing sensitive information required to use a unique username and complex password to access these systems?
- Do all devices with access to sensitive information have access control configured? (ie users can only access the data they require)
- Do all devices with access to sensitive information get scanned for vulnerabilities on a regular basis?
- Are said vulnerabilities being treated in a risk-based priority? (ie more urgent vulnerabilities treated first)
- Are all laptop and mobile devices encrypted and password protected?
- Do all mobile devices with access to sensitive information have mobile device management with the ability to remotely wipe the device?
- Does your organisation require two-factor authentication for remote access?
- Does your organisation have a Business Continuity Plan, and if so, does it include back up and recovery procedures for all virtual systems?
- Are all administrative accounts only permitted to perform administrator activity, with no access to internet or external email?
Cover these steps, and you’ve covered the essentials. Of course, this is not all you need to protect your business. Make time in your schedule to further analyse and audit your systems regularly, and follow the investigative steps we listed earlier to make sure you’ve got all your bases covered.
Other Cyber Security Resources
Australian Cybercrime Online Reporting Network
Visit: https://www.acorn.gov.au/
ACORN is a national policing initiative of the Commonwealth, State and Territory governments. It is a national online system that allows the public to securely report instances of cybercrime.
National Identity & Cyber Support
Visit: https://www.idcare.org.au/
IDCare is a not-for-profit Australian charity that addresses a critical support gap for individuals confronting identity and cyber security concerns.
Australian Cyber Security Centre
Visit: https://www.acsc.gov.au/
An important Australian Government initiative to ensure that Australian networks are amongst the hardest in the world to compromise.
Cyber.gov.au
Visit: https://cyber.gov.au/business/
A new service that combines ASD and CERT services, all being delivered by the ACSC. This consolidated site will eventually supercede ACSC and ASD related pages.
Australian Signals Directorate
Visit: https://www.asd.gov.au/
An intelligence agency in the Australian Government Department of Defence with a focus on information security.
Computer Emergency Response Team
CERT is the primary government contact point for major Australian businesses to receive and respond to cyber security incident reports.