Imagine this: your business is thriving, taking advantage of all the opportunities in our increasingly connected world.
You’re reaching new customers, streamlining processes, and innovating like never before.
But wait, what’s that lurking in the shadows?
Cyber threats, ready to pounce at any moment and wreak havoc on everything you’ve built.
Scary right?
But don’t worry, we’ve got your back. We’ve put together the ultimate cyber security checklist, packed with 20 powerful strategies to keep your business safe.
Let’s dive in.
Do you still need a cyber security audit checklist even if you use an external IT team?
If you’re lucky enough to have an external IT team, you might think that’s enough to keep cyber threats at bay, right?
Not quite.
Yes, an IT security organisation is undoubtedly a crucial part of the process.
However, we can’t overstate the importance of every business leader having a solid understanding of information security in general. This includes cyber threats, vulnerabilities, and cyber security controls.
Equally important is educating your team. After all, data breach prevention often boils down to recognising the tell tale signs of an attack. This could be as simple as teaching employees how to identify suspicious emails or pop-ups and the importance of never clicking on dubious links.
Armed with the fundamental knowledge of cyber security essentials, you’re more likely to recognise potential threats or issues. By understanding what needs to be done before handing it off to the specialists, you’re already a step ahead in preventing attacks or system compromises.
Think of using a specialist as the next step after evaluating your current cyber security status.
We recommend going through our cyber security audit checklist to gain a basic understanding of your existing measures and identify areas for improvement. From there, you can start making plans for implementing a more robust cyber security framework, ensuring that your business remains a fortress in the face of ever-evolving cyber threats.

Our Cyber Security Audit Checklist Strategies
Securing your business’s cyber environment can feel overwhelming. So, our checklist is here to help you navigate the complexities of cyber security. Although we delve into greater detail in our Cyber Security Guide for small to medium businesses, this outline serves as the perfect first step to take before plunging into the vast sea of information available.
Our checklist is designed to highlight the key consideration you need to make regarding your business’s cyber security. As you work through it, you’ll gain clarity on which aspects require more attention and focus, allowing you to approach your research or the hiring of a cyber security support team with confidence and direction.
So, take a deep breath and dive in. With our checklist as your compass, you’ll soon find yourself charting a course to a more secure and resilient digital fortress for your business.
1. Develop a Comprehensive Cyber Security Policy
Roles and Responsibilities
Define the roles and responsibilities of all team members, from top management to entry-level employees.
Clarify who is accountable for ensuring cyber security measures are implemented, monitored, and maintained. By assigning specific roles and duties, you create a sense of ownership and shared responsibility within your company.
Risk Management
Adopt a proactive approach to risk management. Conduct a thorough risk assessment to identify potential vulnerabilities and assess the likelihood of threats materialising.
Stay ahead of the game by prioritising and mitigating risks based on their potential impact.
Regularly review and update your risk management strategy to ensure it remains relevant.
Incident Response Procedures
Even the most fortified organisations can fall victim to cyber attacks. Be prepared with a well-defined incident response plan that outlines the steps to be taken in the event of a breach.
This includes clear communication protocols, escalation procedures, and the swift mobilisation of a dedicated response team.
A timely and well-coordinated response can be the difference between a fast recovery and lasting damage.
We’ll go into a bit more detail about this later.
Examples of Policies
There are several cyber security policies and procedures that you can implement in your business. Here are a few:
- Turn on automatic updates
- Set mandatory password requirements, including length and difficulty
- Have lost and stolen device procedures and guidelines
Policies do not need to be overwhelming in length or complexity. Rather, they just need to effectively communicate key points to your team.
2. Regularly Update Software & Hardware
Staying ahead in cyber security is a constant battle. One of the most effective ways to maintain a strong defence is by regularly updating your software and hardware.
Outdated systems can serve as an open invitation for cyber criminals. S, it’s crucial to stay vigilant and proactive in this area.
To fortify your digital fortress, follow these rules:
- Monitor Updates: Keep a close eye on the latest security patches and firmware updates for your system, applications, and devices. Subscribe to vendor notifications and security bulletins to stay informed about the most recent developments and emerging threats.
- Establish a Schedule: Develop a consistent schedule for installing updates and performing system maintenance. This not only ensures your organisation is protected but also creates a culture of diligence and attentiveness towards cyber security.
- Automate When Possible: Utilise automated tools and software to streamline the update process. This can save time and reduce the risk of human error, making it easier to keep your systems up-to-date and secure.
- Assess Hardware Lifecycles: Be mindful of the lifecycle of your hardware devices. Outdated equipment may no longer receive security updates and support. This can leave your organisation exposed to vulnerabilities. Regularly evaluate the need to replace or upgrade your hardware to stay protected.
3. Implement Strong Access Controls
Controlling who has access to your business’s sensitive information systems is extremely important. A strong access control strategy helps prevent unauthorised access, data breaches, and insider threats.
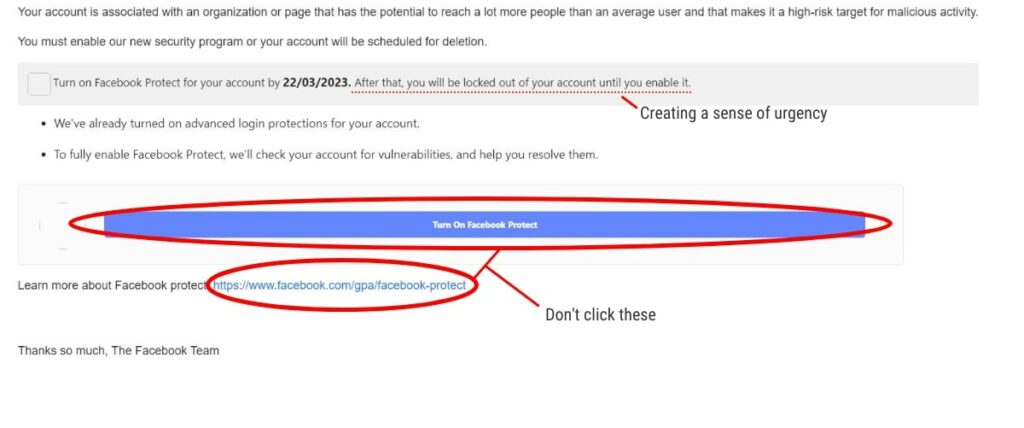
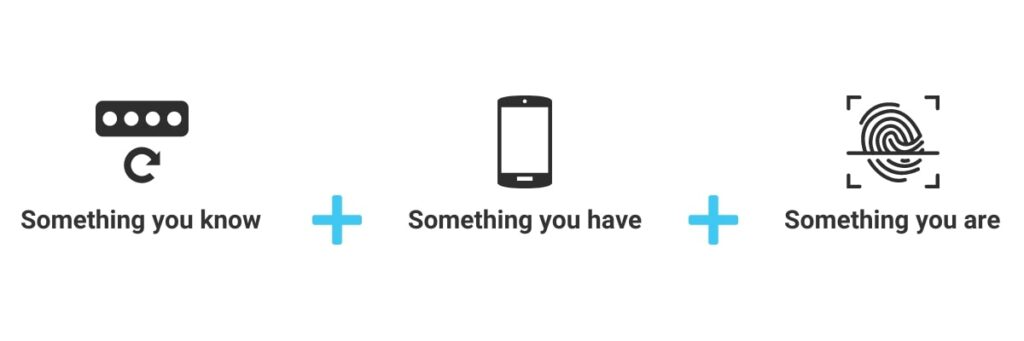
To safeguard against unauthorised access, employ secure authentication methods like multi-factor authentication (MFA). MFA combines two or more verification methods, such as a password, a token, or biometric data. In doing so, it provides an extra layer of protection and makes it more challenging for cybercriminals to gain entry.
You can also limit user access to sensitive information by strictly adhering to the principle of least privilege. Grant employees only the permissions they require to carry out their responsibilities. This will minimise the potential for unauthorised access and data breaches.
Finally, you can also conduct periodic audits of user access rights to ensure they align with employees’ current roles and responsibilities. When an employee changes positions or leaves your organisation, revoke permissions immediately.
4. Encrypt Sensitive Data
Sensitive data is the lifeblood of your business. Protecting it from unauthorised access is critical to maintaining trust and ensuring business success. Especially if your business collects and stores personally identifiable information (PII).

One of the most effective ways to achieve this is by employing encryption, a powerful tool that transforms your data into an unreadable format, safeguarding it both in transit and at rest.
Let’s explore how encryption can fortify your business’s security posture and keep your valuable data under lock and key.
Understanding Data Encryption
At its core, encryption is a process that uses algorithms to convert readable data (plain text) into an unintelligible format (ciphertext), that can only be deciphered using a secret key.
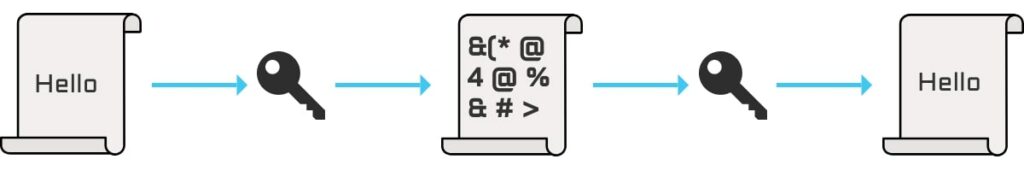
By encryption sensitive data, you ensure that even if it falls into the wrong hands, it remains unreadable. I.e, useless to cybercriminals.
Protect Data in Transit
Data in transit refers to information that’s being transmitted across networks, such as emails, file transfers, or online transactions.
To secure data in transit, deploy end-to-end encryption methods, such as Transport Layer Security (TLS) or Secure Socket Layer (SSL), which encrypt data before it leaves your device and decrypt it upon reaching its intended recipient.
Safeguard Data at Rest
Data at rest is any data that’s stored on physical devices or within cloud storage. Protecting this data is equally important as security data in transit.
Utilise encryption tools, such as disc encryption or file-level encryption, to keep your stored data safe.
Use the Right Encryption Tools
When choosing encryption tools, consider factors like:
- Ease of use
- Compatibility with your system
- Level of security they offer
Opt for industry-standard encryption algorithms, such as Advanced Encryption Standard (AES). This will ensure your data receives the highest level of protection.
Manage Encryption Keys Carefully
The effectiveness of encryption relies on proper key management. Store your encryption keys securely, restrict access to them, and regularly rotate and update keys to minimise the risk of unauthorised access.
5. Conduct Regular Vulnerability Assessments
Proactive security management is the cornerstone of an effective cyber security strategy. By conducting regular vulnerability assessments, you can identify and remediate security weaknesses before they are exploited.
A vulnerability assessment is a systematic process that scans your network and systems to identify potential security weaknesses. By conducting these assessments, you gain valuable insight into your organisation’s security posture. You can then prioritise remediation efforts based on the severity of discovered vulnerabilities.
Various assessment tools are available to help you conduct vulnerability assessments. These range from automated scanners to manual testing techniques.
You’ll want to select tools that align with your organisation’s needs and provide comprehensive coverage of your network and systems.
Vulnerability assessments need to be consistent. So, consider developing a schedule that balances the need for security with the resources available for conducting assessments.
Depending on the size and complexity of your organisation, you may perform assessments monthly, quarterly or annually.
Remember – the value of vulnerability assessments lies in the actions taken following their completion. Ensure you do the following:
- Plan to address identified vulnerabilities
- Prioritise high-risk issues
- Prepare to allocate resources and personnel to remediate vulnerabilities quickly
Finally, regularly review and update your vulnerability assessment process. Don’t skip this part. It ensures that your processes remain effective in the face of emerging threats.
Keep in mind industry best practices and incorporate them into your assessment strategy.
6. Monitor and Log Network Activity
Network monitoring tools enable you to track user activity and identify anomalies that may signal a security breach. By continuously monitoring your network, you can detect and respond to threats in real time. This minimises potential damage and protects your digital assets.
Implement a Robust Logging Strategy
Logging network activity is essential for post-incident analysis and compliance with industry regulations.
A comprehensive logging strategy will capture relevant data, including user actions, access attempts, and network events.
Ensure that you store log data securely and retain it for an appropriate duration to support future analysis and reporting requirements.
7. Implement Intrusion Detection and Prevention Systems
Intrusion Detection Systems (IDS) monitor network traffic for signs of potential security breaches.
Intrusion Prevention Systems (IPS), on the other hand, actively block malicious traffic before it can cause harm.
By implementing both systems, you’re setting up a powerful one-two punch against cybercriminals.
Choosing the right IDS/IPS configuration solution is crucial to effectively protect your network. Consider factors such as compatibility with your existing infrastructure, ease of integration, scalability, and the vendor’s reputation for providing timely updates and support.
IDS/IPS solutions work best when integrated with other cyber security measures. These include firewalls, endpoint protection, and network segmentation. By building a multi-layered security approach, you can create a strong defence against a variety of attacks.
8. Establish a Robust Firewall Configuration
Imagine you have a castle. And you want to protect it from intruders. A firewall serves as the digital drawbridge and moat that surround your business’s virtual castle. It ensures that only authorised traffic can enter or exit.
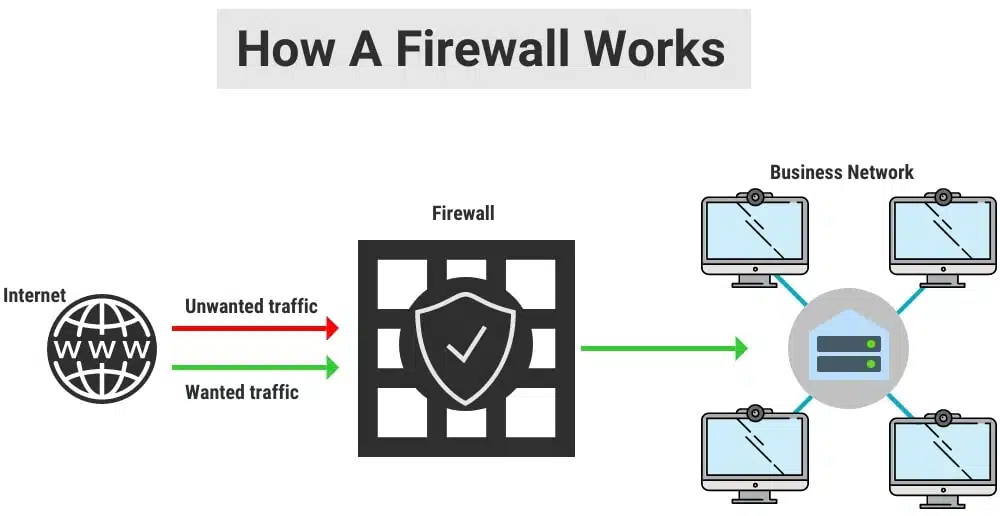
There are various types of firewalls, including hardware firewalls, software firewalls, and cloud-based firewalls.
Hardware firewalls are physical devices installed between your network and the internet.
Software firewalls, alternatively, are installed on individual devices, like your computer or smartphone.
Finally, cloud-based firewalls are hosted remotely and protect your network via the internet.
However, they all intend to do the same thing. It’s important to note that the right type of firewall depends on your business’s specific needs and infrastructure.
Setting up a strong firewall configuration is essential for optimal network security. This involves defining clear rules and policies that determine which traffic is allowed and which is blocked. And, of course, you need to regularly review and update these rules to ensure your firewall stays effective.
9. Implement Secure Remote Access
The modern workforce is mobile. Remote work and the ability to access your organisation’s network from anywhere are now essential components of business life.
With this new flexibility comes the challenge of ensuring that remote connections remain secure.
The Need for Secure Remote Access
Whether you and your team are working from home or a coffee shop, accessing your network from an unsecured connection can expose sensitive data. Implementing secure remote access solutions ensures that employees can access company resources and maintain the integrity of your network.
Virtual Private Networks (VPNs)
A VPN is a secure, encrypted connection between a user’s device and your organisation’s network.
It creates a private tunnel through the public internet. This allows remote workers to securely access company resources as if they are connected to the office network.
VPNs help protect your data from eavesdropping and other cyber threats, ensuring that remote connections remain secure and confidential.
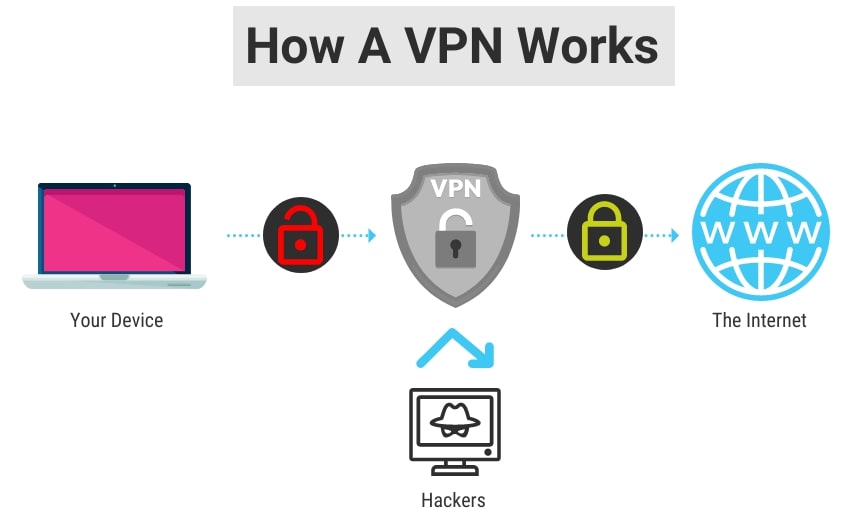
VPN Best Practices
To maximise the benefits of VPNs, follow these best practices:
- Choose a reputable VPN service provider with strong encryption protocols and a no-logs policy.
- Regularly update VPN client software to ensure the latest security features are in place.
- Educate your employees on the importance of using VPNs and how to connect securely.
- Establish clear guidelines for remote access and enforce the use of VPNs for all remote connections.
Additional Secure Remote Access Solutions
Aside from VPNs, other secure remote access solutions include remote desktop services, multi-factor authentication (MFA), and zero-trust security models. These tools can further enhance the security of remote connections to your network.
10. Develop an Incident Response Plan
An incident response plan (IRP) is a critical component of your cyber security strategy. Here’s a brief outline of the key elements of developing a cyber incident response plan:
- Preparation: Establish a dedicated incident response team consisting of individuals from various departments. Provide team members with regular training on incident response best practices and have the necessary tools and resources.
- Identification: Define the criteria for classifying an event as a cyber security incident and outline the process for reporting suspected incidents. Implement monitoring and detection tools to identify potential security breaches quickly.
- Containment: Develop procedures for containing a security incident once it’s identified. This may include isolating affected systems, blocking malicious IP addresses, or disabling compromised accounts.
- Eradication: Outline the steps to remove any threats from your network and systems, such as cleaning up malware, applying patches, or rebuilding compromised systems
- Recovery: Establish a process for restoring affected systems and resuming normal operations. Ensure that all security measures are up and running before bringing the system back online.
- Lessons Learned: After an incident, conduct a thorough review to identify the root cause, assess the effectiveness of your response, and determine if you can make any improvements. Update the plan as needed.
For more detailed information on developing an IRP tailored to your business, be sure to check out the article here.
11. Perform Regular Backup and Recovery Tests
Regular backups ensure that you can restore your data in the event of a cyber security incident, system failure, or other disruptive events. However, simply performing backups isn’t enough; it’s equally important to test your backup and recovery process. This ensures that they are effective and reliable.
Regularly testing your backups confirms that the data stored is complete, accurate, and free of corruption. This ensures that you can successfully recover essential data when needed, reducing downtime and potential losses.
One of the key benefits of backup and recovery tests is that they can reveal problems. A backup and recovery test might tell you that there is inadequate storage capacity, hardware failures, or software bugs. Identifying these issues early allows you to address them proactively, ensuring seamless data recovery after an incident.
Additionally, many industries have regulatory requirements regarding data retention and recovery. Regular backup and recovery tests help demonstrate compliance, and reduce the likelihood of fines or penalties.
12. Conduct Employee Awareness Training
A well-informed workforce is often your first line of defence. Regular cyber security training will help employees recognise risks, respond appropriately to incidents, and contribute to a culture of security awareness.
Employee awareness training is essential to:
- Reduce human error
- Promote a security-conscious culture
- Comply with regulations
- Improve incident response
We only touch on the importance of employee awareness training here. We encourage you to explore our in-depth article for more information here. The article has actionable tips on how to develop an effective training program for your organisation.
13. Review Third-Party Vendor Security
Third-party vendors are often vital to your operations, however, they can introduce risks. A great example of this is the Latitude hack.
It’s crucial to review the security practices of these external entities and ensure they align with your standards.
Here’s an overview of why third-party vendor security is important, and how to approach it.
Identify Potential Weak Links
Vendors and partners can often access your business’s sensitive data and systems. If their security measures are inadequate, they can become an entry point for your network.
You want to review their security practices and ensure that potential weak links are addressed. Before they become a problem.
Establish Clear Expectations
Communicate your security expectations to third-party vendors and partners. By outlining your requirements and expectations, you can create a mutual understanding of the importance of cyber security.
Conduct Regular Assessments
Don’t review vendor security practices once; make it an ongoing process. Regular assessments can help you monitor changes in their security posture and ensure they continue to meet your expectations.
Implement Contractual Obligations
Incorporate security requirements into your contracts. This can create a legally binding obligation for vendors to maintain a certain level of security. It also provides you with recourse if they fail to meet those standards.
Coordinate Incident Response
Finally, work with third-party vendors and partners to develop a coordinated incident response plan. This ensures both parties know how to react in the event of a security breach.
14. Test Your Security Controls
Ok, so you’ve implemented a range of security controls. You think you’re safe, but are you? The truth is, without testing these controls, you’re playing a game of chance.
Regular testing isn’t just about finding vulnerabilities – it’s about staying at least one step ahead, adapting to an ever-changing digital landscape, and keeping your organisation safe from the unknown.
Penetration testing, or ethical hacking, turns vulnerability into an opportunity. By simulating real-world cyber attacks, you identify weaknesses, learn from them, and emerge stronger and more prepared than ever before.
Additionally, regular vulnerability assessments put you in the driver’s seat. Scanning your network and systems for security gaps is like taking a proactive approach to your organisation’s health. You can address vulnerabilities before they become catastrophic.
In the end, you want your organisation’s cyber security to transform from a passive one to an active, dynamic strategy.
15. Conduct Regular Cyber Security Audits
There’s great power in insight. Regular cyber security audits give you a bird’s-eye view of your security posture. They’ll shed light on your business’s strengths, weaknesses, and opportunities for growth.
By scheduling these periodic evaluations, you ensure that your security program remains effective and up-to-date. Moreover, the audit process can help you maintain compliance with industry standards and regulations.
During a cyber security audit, you’ll assess various aspects of your organisation’s security measures, identify weaknesses, and develop action plans to address them.
Remember, cyber security is a team effort. By making regular audits an integral part of your security strategy, you’ll empower your team to take ownership of your business’s digital safety.
16. Implement a Mobile Device Management Policy
Mobile devices are indispensable. Be it personal or company-owned devices, employees rely heavily on them to stay connected.
But, with this convenience comes new security challenges.
By establishing a Mobile Device Management (MDM) policy, you can strike the perfect balance between productivity and security.
Set Clear Rules
An effective MDM policy starts with setting clear rules for the use of personal and company-owned mobile devices.
Define acceptable usage, device access permissions, and data handling protocols. Ensure that employees understand their responsibilities when it comes to protecting sensitive data.
Remote Management
To bolster your mobile security even further, deploy an MDM solution that allows you to secure, manage, and monitor devices remotely. This way, you can enforce security policies, track device usage, and even wipe data from lost or stolen devices. Additionally, make sure to keep the devices updated with the latest security patches and applications.
17. Secure Wireless Networks
Wireless networks offer convenience and seamless connectivity. But, as with any technology, they can also introduce security risks. To protect your organisation’s valuable data, it’s essential to secure your wireless networks with encryption and authentication protocols.
Start by choosing a strong encryption standard, such as WPA3, to safeguard your wireless communications.
This ensures data transmitted over your network remains encrypted and protected from prying eyes. Avoid using outdated encryption methods like WEP, which are easily cracked and offer minimal security.
Next, implement authentication protocols to control access to your wireless networks. Consider using MFA, which requires users to provide additional proof of identity.
Segmentation is another crucial element of securing your wireless networks. By separating them from your internal network, you minimise the potential damages in case of a breach.
Implement separate networks for different purposes, such as guest access, IoT devices, and business operations. This way, you can apply specific security policies and controls for each segment, tailored to their unique needs.
18. Develop a Data Classification System
Understanding the value of your data is vital. By developing a data classification system, you can prioritise and protect sensitive information based on its level of importance. Here’s a quick guide to help you build a tailored classification system.
- Identify Data Categories: Start by dividing your data into distinct categories. These may include public, internal, confidential, and highly confidential information.
- Establish Criteria: For each category, determine clear criteria that outline the characteristics of the data it contains. For example, public information might be available to anyone, while highly confidential data may include trade secrets or financial records.
- Assign Ownership: Designate data owners who are responsible for classifying and managing data within their purview. This not only ensures accurate classification but also encourages accountability.
- Develop Guidelines: Create a set of guidelines outlining the handling, storage, and sharing practices for each data category. This may include access controls, encryption requirements, and retention policies.
- Implement Security Controls: Based on the classification, apply appropriate security controls to protect each data category. For example, highly confidential data may require stronger encryption or stricter access controls.
- Train Your Team: Educate employees about the data classification system and their role in maintaining it.
- Review and Update: Regularly review and update your data classification system to ensure it remains relevant and effective in the face of evolving threats and changing business needs.
19. Deploy Email Security Measures
Your business’s email system is a prime target for cybercriminals. Consider these essential email security measures to ensure its security and protect against spam, phishing, and other email-based threats.
Email Filtering
Implement advanced email filtering solutions to identify and block malicious emails for they reach your team’s inbox.
Email Encryption
Encrypt emails to protect sensitive information from unauthorised access. By using encryption, even if an email is intercepted, the content will remain unreadable to anyone without the decryption key.
Email Authentication
Authenticate email domains using protocols such as SPF, DKIM, DMARC, and BIMI. This helps verify the legitimacy of emails sent from your domain and prevents cybercriminals from sending spoof emails
20. Maintain a Comprehensive Asset Inventory
Finally, the foundation of a strong cyber security posture lies in knowing what to protect. A comprehensive asset inventory is a critical component of any effective security strategy.
Here are some important tips to remember.
- Know Your Assets: Identifying every asset within your organisation helps you gain a clear picture of the potential risks and vulnerabilities. After all; you can’t protect what you don’t know exists.
- Categorise and Prioritise: Classify your assets based on their value, sensitivity, and criticality. This enables you to prioritise your security efforts and allocate resources effectively.
- Stay Current: Continuously update your inventory as new assets are added, modified, or decommissioned.
- Monitor and Manage: Implement tools that automatically discover, track, and monitor your assets. This helps you detect unauthorised devices, software installations, and data access.
- Map Security Controls: Identify and document the security controls applied to each asset. In doing so, you will confirm that proper protective measures are in place and identify potential gaps.
- Compliance and Reporting: An Accurate asset inventory is essential for demonstrating compliance with various industry standards and regulations. It also simplifies reporting and auditing processes.
21. Develop a Business Continuity and Disaster Recovery Plan
Cyber attacks and other disasters can cause significant disruptions to your business operations. To minimise the impact and ensure quick recovery, it’s crucial to have a comprehensive Business Continuity and Disaster Recovery (BCDR) plan.
A well-crafted plan outlines clear steps for responses and recovery in various scenarios, from natural disasters to cyber incidents.
Key components of a BCDR plan include:
- Data Backup and Recovery: Regularly back up critical data and systems, and store backups securely off-site. Establish procedures for restoring data and systems in the event of a disaster.
- Alternative Communications Channels: Identify backup communication methods to ensure team coordination during a crisis.
- Designated Roles and Responsibilities: Define roles and responsibilities of each team member, including key decision-makers and specific tasks.
- Business Impact Analysis: Assess the potential impact of disruptions on your business operations to prioritise critical functions and allocate resources effectively.
- Step-By-Step Response Plan: Develop a detailed plan for responding to different incidents, including immediate actions, communication protocols, and procedures for transitioning into backup systems.
Regularly test and update your BCDR plan to identify gaps and areas for improvement. As your business evolves and new threats emerge, review and revise your plan accordingly.
A comprehensive BCDR plan minimises downtime, financial losses, and reputational damage. By investing in a strong plan and regularly testing its effectiveness, you demonstrate your commitment to resilience and ensure your business is prepared for any disruption.
22. Secure Device Charging Practices
To protect your devices and the sensitive data they contain, it’s crucial to adopt secure charging practices.
Use trusted charging cables. Cheap, off-brand cables may damage your device or be used to inject malware or intercept data. Always use genuine cables from reputable manufacturers or trusted third-party brands.
Avoid public USB power outlets, such as those found in airports, cafes, or conference centres. These outlets can be compromised by attackers to install malware on your device or steal your data while it’s charging.
Charge your devices using your own AC adapter plugged into a standard electrical outlet. If you must use a public USB power outlet, consider using a USB data blocker, which prevents data transfer while allowing your device to charge.
Conclusion
The digital landscape is constantly changing. But, armed with the right tools, knowledge, and strategies, you can confidently navigate the associated challenges and ensure the security of your assets.
By following the steps above, you’ll not only enhance your understanding of cyber risks but also empower your team to work collectively in safeguarding your business.
Remember, cyber security is an ongoing process. Be proactive in tackling vulnerabilities, innovative in leveraging new technologies, and relentless in refining your protocols.
The road may be challenging, but the rewards of protecting your business and its reputation are well worth the effort.
