Are you concerned about the rising threat of cyber attacks on your business? Do you know how to respond in the event of a cyber security incident?
Having a well-planned incident response plan is crucial to minimise the impact of cyber threats on your business. Whether it’s data loss, financial damage, or reputational harm, the consequences of a cyber attack can be severe.
That’s why, in this blog post, we’re going to discuss the importance of having a cyber incident response plan in place. Not only will we break down the key components that your business should consider including in the plan, but I’ll also provide you with valuable tips on how to create an effective incident response plan.
From identifying key stakeholders and assets to establishing communication protocols and procedures, we’ll show you everything you need to know to respond to cyber security incidents quickly and effectively.
So, keep reading if you’re looking to protect your business from cyber threats and safeguard your reputation.

What is a Cyber Incident Response Plan?
Put simply, a cyber incident response plan is a documented set of procedures that a business follows during a cyber security incident. Its purpose is to enable the company to detect, contain, and recover from the incident as quickly and effectively as possible, minimising damage to assets, systems, and data.
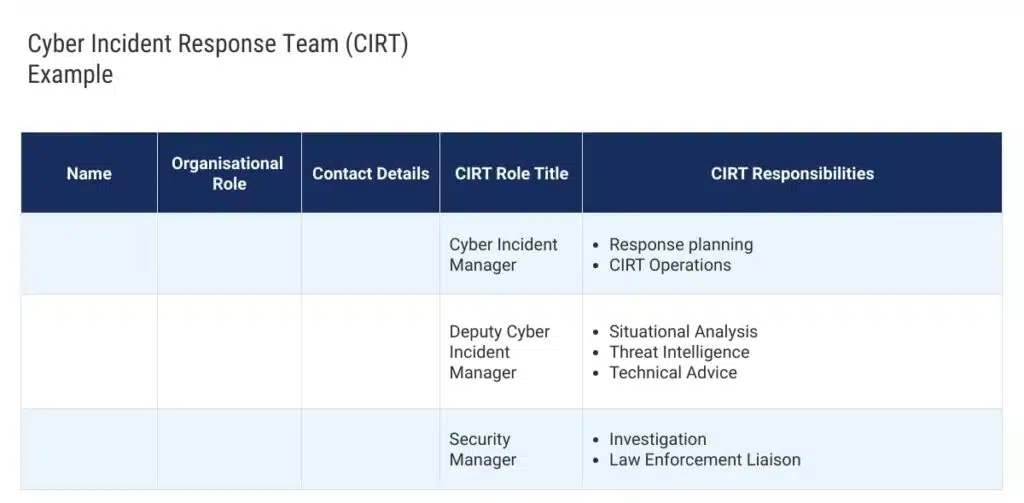
The incident response plan typically outlines the roles and responsibilities of individuals involved in the response effort. This normally includes IT staff, security personnel, and management.
It also specifies the procedures for identifying and analysing the incident. This includes assessing its impact, containing its spread, and restoring systems to normal operations.
An effective cyber incident response plan should be tailored to the specific needs and risks of the business. It should take into account:
- The types of cyber threats that are most likely to affect the organisation.
- The critical assets and systems that need to be protected.
- The regulatory and legal requirements that the business must comply with.
By having a well-designed cyber incident response plan in place, businesses can significantly reduce the damage caused by cyber attacks and minimise the disruption to their operations. They can also demonstrate to customers, partners, and regulators that they take cyber security seriously and are prepared to respond to incidents effectively.

Why It’s Important
A single cyber attack can cause data loss, financial damage, and reputational harm that can take years to recover from.
Without a cyber incident response plan, businesses may struggle to identify and contain cyber threats. This can lead to significant downtime, lost revenue, and damage to customer relationships. Additionally, businesses may face legal and regulatory penalties for failing to protect sensitive data.
Businesses with a well-designed cyber incident response plan in place are better equipped to handle cyber threats. Having established protocols and procedures allows you to act fast and effectively during an attack.
1. Identify Key Stakeholders
To effectively respond to a cyber security incident you need a clear understanding of the key stakeholders in your organisation.
These individuals or groups are responsible for making critical decisions and taking specific actions in response to an event.
Depending on the size of your business, examples of key stakeholders include:
- IT department: Responsible for managing and securing the organisation’s IT infrastructure and systems.
- Executive leadership: Responsible for making high-level decisions related to the organisation’s overall response strategy and resource allocation.
- Public relations/communications team: Responsible for managing the organisation’s reputation and communicating with external stakeholders (customers, partners, and media) in the event of a cyber security incident.
- Legal department: Responsible for understanding and complying with relevant laws and regulations relating to data privacy and security.
How to identify key stakeholders
To identify key stakeholders, consider mapping out your incident response team. You can then document the roles and responsibilities of each member. This will help ensure that everyone knows their role and is prepared to act if an event occurs.
Additionally, it’s important to ensure that key stakeholders receive training and awareness regarding their roles and responsibilities. This includes reviewing the incident response plan as a whole. With regular training and testing, you can ensure that everyone is prepared and able to respond to an event.
2. Identify Assets
This is a crucial step in creating a strong cyber incident response plan. Assets may include anything from hardware and software to data and intellectual property.
It’s important to understand which assets are most critical to your business. You’ll want to ensure these are properly protected in the event of a cyber attack.
To identify assets, start by conducting a thorough inventory of all technology and data your business uses.
This could include:
- Servers
- Computers
- Mobile devices
- Cloud services
- Databases
You should also consider the physical security of your assets. This includes the location of servers and access control measures in place.
Once you’ve identified your assets, categorise them based on their importance to your business.
For example, customer data and financial records may be more critical than marketing materials or employee files. Doing so will help you prioritise your response efforts and better allocate resources.
Remember to regularly review and update your asset inventory. This will change as your business evolves and implements new technologies.
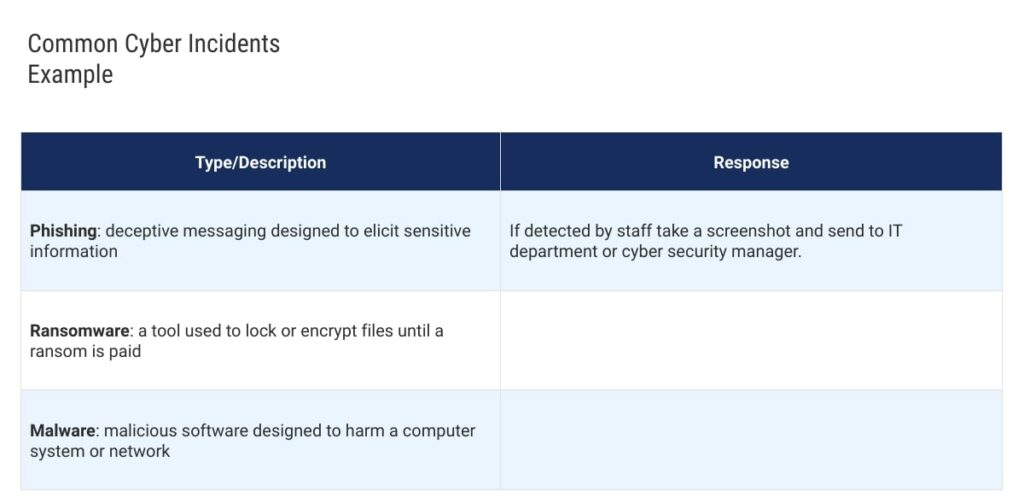
3. Identify Potential Threats
The next step in creating a comprehensive cyber incident response plan is to identify potential threats.
In order to effectively respond to an incident, you need to understand the types of threats that your business may face.
To start, conduct a thorough risk assessment to identify potential vulnerabilities in your system and processes. This will help you determine the likelihood of a cyber attack and the potential impact on your business.
Next, consider the different types of cyber threats that your business could face. These can include malware, phishing attacks, ransomware, and denial of service (DoS) attacks. Each type of threat requires a different response. So, it’s important to understand their unique characteristics and how to mitigate them.
Finally, consider how insider threats might impact your business. These are threats that come from within your own organisation. Intentional or accidental.
They can include employees, contractors, or even third-party contractors that have access to your systems and data.
By identifying these potential threats, you can be better prepared to respond quickly and effectively to any security threats.
4. Establish Communication Protocols
Clear communication protocols are crucial in incident response. It’s essential to have a plan in place for the sharing of information throughout the process.
Naturally, this includes communication with the incident response team and other employees. However, it also includes external stakeholders such as customers, partners, and authorities.
To establish clear communication protocols:
- Designate a point of contact: Assign a primary and secondary point of contact to coordinate communications between the incident response team and other stakeholders.
- Determine communication channels: establish clear channels of communication for each stage of the incident response process. This could include email, phone, instant messaging, or video conferencing.
- Develop messaging templates: Develop pre-approved templates for communication with stakeholders to ensure that messaging is consistent, accurate, and timely.
- Define escalation procedures: Establish escalation procedures to ensure critical information is communicated to the appropriate parties in a timely manner.
- Test communication protocols: Test your communication protocols to ensure that they work effectively and identify any areas that need improvement.
Clear communication protocols help you ensure that everyone is on the same page and that information is shared quickly and accurately.
5. Develop Containment, Eradication & Recovery Procedures
These procedures help ensure that the impact of an attack is minimal.
Containment procedures involve isolating the affected system or network to prevent the spread of an attack. This may involve disabling network connections, shutting down affected systems, or taking other steps to prevent the attacker from continuing with malicious activities.
Eradication procedures involve removing the attacker’s presence from the network or systems. This can involve removing malware, closing vulnerabilities, and ensuring the system is secure before returning online.
Recovery procedures involve restoring normal operations after an incident is contained and eradicated. This might involve restoring data from backups, verifying systems are operating normally, and conducting post-incident reviews.
Effective containment, eradication and recovery procedures require careful planning and coordination. It’s important to identify the specific procedures for different scenarios. Additionally, ensure that each stakeholder is aware of their responsibilities.
6. Implement Incident Analysis and Investigation Protocols
Incident analysis and investigation are critical components of an effective incident response plan.
The purpose of incident analysis and investigation is to:
- Understand the root cause of the incident.
- The extent of the damage.
- The effectiveness of the response procedures.
By conducting a detailed analysis, you can identify areas of improvement in your response plan. This can prevent similar incidents from occurring in the future.
There are several steps involved in incident analysis and investigation.
- Gather evidence: Collect all relevant information about the incident, including logs, system configurations, and any other relevant data.
- Analyse the evidence: Use the evidence gathered to identify the root cause of the incident, determine the scope of the damage, and understand how the incident occurred.
- Report findings: Document the findings of the investigation and share them with key stakeholders. This will help to inform future incident response plans and improve overall security posture.
- Take corrective action: Based on the findings of the investigation, take corrective action to address any vulnerabilities or weaknesses in your systems and processes.

It’s important to note that you should undertake incident analysis and investigation in a timely manner. This ensures lessons learned are applied to future incidents.
7. Test & Refine The Plan
Once you’ve developed your incident response plan, it’s essential to test and refine it regularly. This helps ensure its effectiveness. Testing the plan allows you to identify any gaps or weaknesses in the plan and adjust it accordingly.
Here are steps to refine your plan:
Conduct tabletop exercises
Tabletop exercises are a simulation of a cyber attack where you test your plan and effectiveness.
During a tabletop exercise, the incident response team encounters a hypothetical scenario, such as a ransomware attack. They must then respond according to the plan.
Evaluate results and identify gaps
After the tabletop exercise, it’s essential to evaluate the results thoroughly to identify gaps in the plan.
This evaluation should focus on key areas, such as response time, communication effectiveness, and decision-making processes.
Gather feedback from all stakeholders involved. Analyse this feedback and look for areas where the incident response plan can be improved.
Common gaps include:
- Inadequate documentation
- Lack of clarity around roles and responsibilities
- Insufficient training or resources
Make sure you address any gaps promptly to ensure the plan is effective as possible.
Update the plan
Based on the results of the tabletop exercise and analysis, update the plan to address any identified gaps or weaknesses. Revise the procedures and processes to ensure they are effective and efficient.
Retest the plan
Once you’ve updated the plan, test it again to ensure that it’s effective in addressing identified gaps or weaknesses. Repeat this process regularly to keep the plan up-to-date and effective.
By testing and refining your incident response plan regularly, you can ensure that it remains effective in protecting your business from cyber attacks. Keep in mind that cyber threats are constantly evolving, so your plan should be flexible enough to adapt to changing circumstances.
Conclusion
Cyber attacks are a constant and growing threat to businesses of all sizes. The potential consequences of a cyber attack can be severe, including data loss, financial damage, and reputational harm. That’s why having a well-planned incident response plan is essential for any business that wants to protect itself from cyber threats.
In this article, we’ve outlined the key components of a cyber incident response plan. We’ve also provided valuable tips on how to create an effective plan specific to the needs and risks of your business.
By implementing a robust incident response plan, businesses can not only mitigate the damage caused by cyber attacks but also demonstrate their commitment to cybersecurity to their customers, partners, and regulators.
It’s essential to understand that the threat of cyber attacks will continue to evolve. As such, your incident response plan must evolve with it. Regularly reviewing and updating your plan is crucial to ensure that you stay ahead of the ever-changing cybersecurity landscape.
Don’t wait until it’s too late to start planning for a cyber attack. With the insights and strategies outlined in this article, you can take proactive steps to protect your business and safeguard your reputation.
