Phishing attacks are a dangerous threat to businesses of all sizes. For over 25 years cybercriminals have used deceptive tactics to trick employees into divulging sensitive information or downloading malicious software.
These attacks can result in financial losses, damage to the company’s reputation, and the compromise of sensitive data. Protecting your business from phishing attacks is critical for maintaining your customers’ and employees’ security and trust.
In this article, we’ll take a look at how you can prevent phishing attacks on your business. We’ll cover everything from the types of attacks you’re likely to encounter to practical steps you can take to safeguard your business against these threats.

What are Phishing Attacks?
Phishing attacks are a form of cyber attack. They use deceptive tactics to gain access to sensitive data such as usernames, passwords and credit card details. They attempt to acquire this information from unsuspecting victims by impersonating legitimate companies or individuals.
In many cases, these attacks are successful, resulting in financial losses, reputational damage, or other serious consequences. Therefore, it is essential for organisations to be aware of the threat posed by phishing and to take proactive steps to prevent it.
A Word On Social Engineering
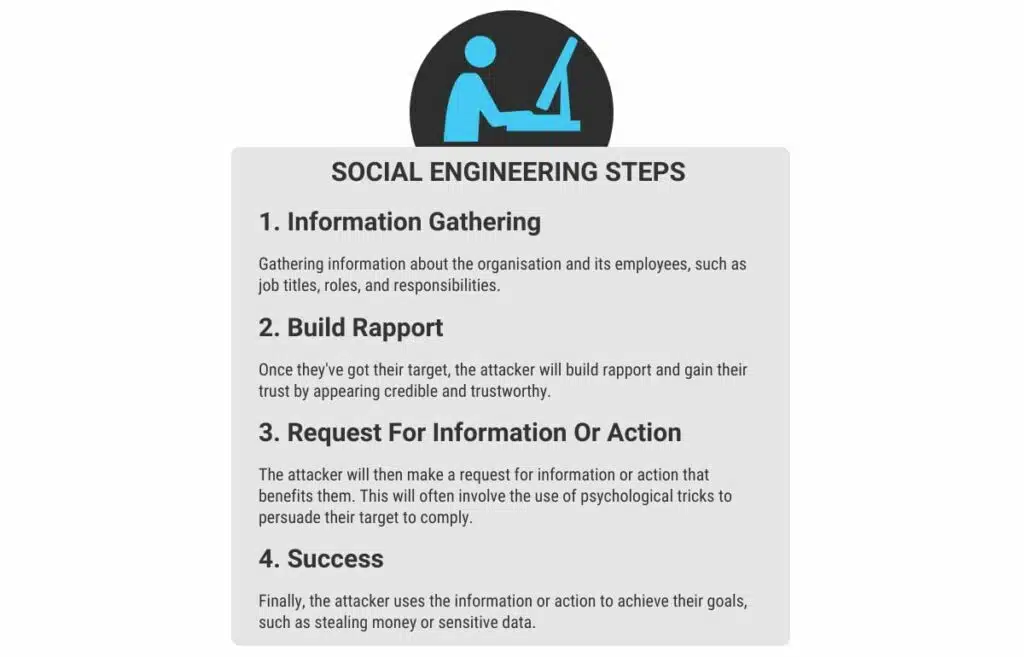
We’re going to mention social engineering a lot, so here’s a quick primer. Social engineering is a common tactic used by cybercriminals. It is used to manipulate and deceive individuals into revealing confidential information or performing actions that compromise their security.
The goal of social engineering is to exploit the human tendency to trust, be helpful, or act on emotions. Attackers will use psychological tricks to gain a victim’s confidence and make them act against their best interest. These methods include:
- Creating a sense of urgency
- Fear
- Authority
- Using familiarity to gain the victim’s confidence
By relying on human rather than technical vulnerabilities, social engineering remains sophisticated and difficult to detect.
Types of Phishing Attacks
Phishing attacks come in many shapes and sizes and can be difficult to spot without training. This next section will provide an overview of the types of phishing attacks businesses may encounter.
By understanding the different tactics attackers use, you can better prepare yourself and your employees for an attack.
It’s important to note that these attacks are constantly evolving. Attackers are always looking for new ways to bypass security measures and trick victims.
Email Phishing
This is the most common type of phishing attack. Attackers will send fake emails designed to look like they come from a legitimate source, such as a colleague. The goal is to trick users into clicking on a link or downloading an attachment that contains malware or entering sensitive information.
Email phishing typically starts with a mass email campaign. Attackers will send out thousands of emails to potential victims.
The emails are designed to look like they’re legitimate and from a trusted source. They could appear to be from a bank, e-commerce site, or social media businesses. They’ll often include logos, graphics, and other elements that make them look convincing.
The email may contain a request to click on a link or download an attachment. They often also present a sense of urgency, such as warning victims that an account is compromised, or a bill is overdue.
Spear Phishing
This is a more targeted form of phishing. Attackers will research their victims in advance and use personal information to create a highly compelling message. This means they’ll comb social media profiles and research where the victim works and who they interact with. In doing so, they’re able to build a complete profile of the victim. This background makes spear phishes more personalised, convincing, and harder to detect.

A spear-phishing email will often include a sense of urgency or importance. They want you to act quickly, without taking time to verify the email legitimacy.
The email may contain a request to click on a link or download an attachment. Bad idea. Like email phishing, this can result in the installation of malicious software or the theft of sensitive information.
Whaling
This attack targets the big players. High-level executives or other high-profile individuals in the business. Attackers are “hunting” for the “big fish”. The “whales”.
Whaling attacks are personalised, sophisticated, and often rely on extensive research on their target. Like spear phishing, this can include research into social media, job titles, and relationships with colleagues and business partners.
The attacker can then carefully craft an email that appears to be from a trusted source. This might be a senior executive within the company, a business partner, or a government official.
The email may request sensitive information or access to sensitive accounts. These attacks rely on social engineering techniques to trick a target into taking action. After all, not many people want to ignore an email from their boss or an executive colleague.
Whaling attacks can have serious consequences for businesses. Targeting high-profile workers mean that a successful attack can result in the theft of sensitive information, financial loss, and damage to the company’s reputation.
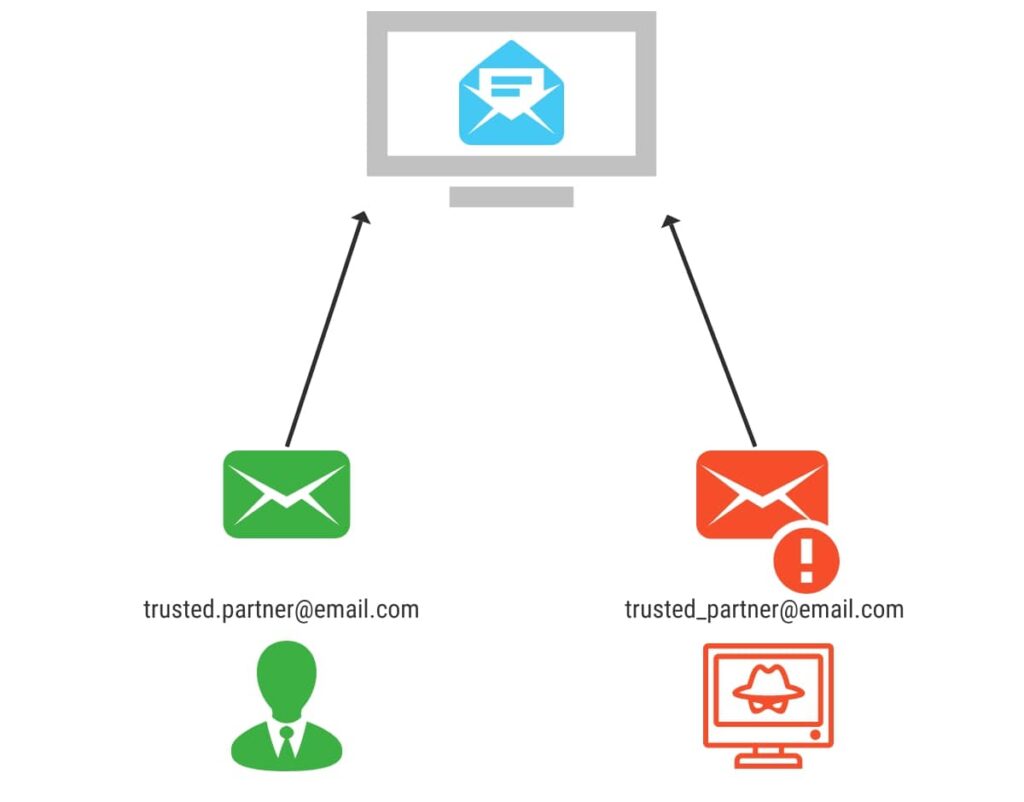
Clone Phishing
Clone phishing is a type of attack where the attacker creates a nearly identical copy of a legitimate email or website. They’ll then replace certain elements with malicious content.
The goal is to trick the recipient into believing the email or website is legitimate. From there, they’ll attempt to persuade the recipient to take action that may result in malicious behaviour.
To carry out the attack, the attacker may first gain access to a legitimate email or website. They’ll then use that information to create a copy. The clone will look almost identical, including logos, graphics, and other notable design elements. It may even come from a legitimate email or URL.
Sounds pretty convincing doesn’t it?
However, the attacker will typically have made subtle changes to the clone email or webpage. For example, replacing a legitimate link with a harmful one, or requesting sensitive information where it otherwise wouldn’t have.
Similar to other types of phishing, the email or website may include a sense of urgency to get you to take action.
Business Email Compromise
Business Email Compromise (BEC) is a form of attack that targets businesses and organisations. The goal of this type of attack is usually to trick employees into transferring funds or sharing sensitive information. BEC attacks are often extremely sophisticated, requiring a lot of research into the target organisation.
In a typical BEC attack, the attacker will first gain access to an employee’s email account. This is done either through a phishing email or by exploiting a vulnerability in the organisation’s network.
Now comes the waiting part. The attacker will monitor the employee’s email activity. They’re looking for opportunities to impersonate the employee or other high-level executives within the organisation.
Once they’ve established a level of trust with their victim, they may ask that the victim transfer funds to a fraudulent account, or provide sensitive information such as login credentials or customer data. The attacker will use similar social engineering techniques as other phishing attacks. They may create a sense of urgency in their request. Or even simply rely on the fact that the proposal appears to be coming from a trusted source.

Phishing attacks are a serious threat to businesses of all sizes. Understanding the different types of attacks can help your employees prepare themselves to identify and avoid potential attacks.
It’s important to remember that phishing attacks are constantly evolving. Stay vigilant and up-to-date.
Common Targets
Attackers don’t discriminate when orchestrating an attack. Phishing attacks can target anyone with an email address and an internet connection. However, attackers are more likely to target some individuals and organisations. In this section, we will look at some of the most common targets of an attack.
Employees
Unsurprisingly, employees are a common target of phishing attacks. This is because they often have access to sensitive information and insufficient training. Alternatively, employees are a good stepping stone to gain access to higher-level targets.
Attackers may also use social engineering techniques to exploit employees’ trust in their coworkers or superiors.
Attackers will target employees using a variety of methods, including:
- Social Media
- Phone Calls
Naturally, it’s important to provide regular training and education to employees on how to identify and respond to phishing attacks.
Executives
Executives are high-profile targets for cybercriminals. The “whales” we mentioned earlier. This is due to their access to sensitive information and ability to make critical organisational decisions.
Cybercriminals may try to steal their credentials, compromise their devices, or use social engineering techniques to access sensitive data.
Customers
Cybercriminals will also target your customers. They can do this by creating a fraudulent website or phishing emails that look like they’re from your company. In doing so, they aim to trick customers into providing sensitive information. This could be:
- Credit card information
- Login credentials
- Personal information
In other cases, a criminal might pose as a customer service representative and convince customers to provide their details.
Additionally, cybercriminals may target customers indirectly by compromising the company’s systems and stealing customer data.
It’s important to remind your customers to remain vigilant and cautious when interacting online. You might consider providing information to protect your customers from an attack. This should include ways customers can verify the authenticity of your websites and emails.
Financial Institutions
Financial institutions, such as banks, are common targets for cybercriminals because of the valuable financial information they hold. Hackers may attempt to gain access to customer accounts, steal personal information, or initiate fraudulent transactions. They may also attempt to compromise the institution’s internal systems, such as payment processing or account management.
If your business is in the financial sector, it’s important to remind customers to take steps to protect themselves. You should remind customers that:
- They should never share their account credentials or personal information with anyone.
- They should regularly monitor their account activity for any unauthorised transactions or charges.
- They should always use secure, trusted networks when accessing financial accounts.
Government Agencies
Government agencies are also a common target for phishing attacks, as they often handle sensitive information related to national security and public safety. These attacks can take various forms, such as fake emails from officials, fake job offers, or fake requests for information.
In many cases, phishing attacks on government agencies are part of a larger campaign. These campaigns often aim to compromise critical infrastructure or gain access to classified information.
Alternatively, government agencies may be targeted for politically motivated reasons. In such cases, the attack may be more sophisticated and targeted.
Given the severe consequences of a successful phishing attack on a government agency, it is critical that government employees receive adequate training.
Healthcare Organisations
Healthcare organisations are frequently targeted by cybercriminals due to the sensitive nature of the information they hold.
Attackers can use stolen healthcare data to commit identity theft, insurance fraud, or even to create counterfeit prescriptions. The impact of a successful attack on a healthcare organisation can be severe, potentially resulting in damage to reputation, financial loss, and even patient harm.
Phishing attacks on healthcare organisations can take various forms. For example, attackers might send emails that appear to be from a trusted source, such as a government agency or a medical supplier, requesting sensitive information or directing the recipient to a fake login page. Alternatively, attackers may use social engineering techniques to trick employees into revealing login credentials or installing malicious software.
Educational Institutions
Finally, educational institutions such as universities or schools are common targets for phishing attacks. Cybercriminals may target students, faculty, or staff members to access sensitive information or launch a larger attack.
In 2020, a successful phishing attack on a Texan school resulted in a loss of $2.3 million. The scam involved fraudulent emails sent to the organisation in November 2019, leading to three separate transactions.
In other cases, attackers can target educational institutions to steal research data or intellectual property. Attackers can then sell this data on the dark web, or use it to gain a competitive advantage in the market.
Impact of Phishing Attacks
Phishing can have a huge impact on businesses, both large and small. In this section, we’ll explore the various ways that phishing attacks can impact businesses.
Financial Loss
One of the most significant impacts of a phishing attack on a business is financial loss. This can result from a variety of factors, including theft of sensitive financial information, fraudulent wire transfers, and unauthorised purchases.
Cost of Mitigation
After an attack, businesses are often forced to invest significant resources in mitigating the damage caused by the attack. This can include the cost of hiring IT experts to identify and remediate the cause of the attack. As well as the cost of implementing new security measures to prevent future attacks.
Compliance Violations
Phishing attacks can also result in compliance violations for businesses. For example, if an attack results in the loss or theft of sensitive customer data, the business may be in violation of industry regulations or data protection laws. This can result in significant fines and legal fees.
Reputational Damage
Reputational damage is another significant impact of phishing. When a business falls victim to a scam, it can lead to irreparable harm to its reputation. This can lead to a complete loss of customer trust and revenue.
If an attack results in a data breach it can damage the company’s reputation even further. Naturally, customers may be hesitant to do business with an organisation that has experienced a security incident.
Phishing can even cause reputational damage if the organisation is not directly affected. For example, let’s say a victim falls for a malicious email appearing to come from an organisation. In future, they may associate the negative experience with the business rather than the attacker.
Rebuilding a damaged reputation is a costly and time-consuming process. It can involve heavily investing in public relation campaign, improving cyber security measures, and offering compensation. Failure to address reputational damage caused by phishing attacks can have long-lasting consequences for businesses.
Productivity Loss
Phishing attacks don’t just cause financial and reputation damage to businesses. When your business suffers an attack, it can lead to system downtime, decreased efficiency, and lost productivity.
Additionally, businesses may have to spend time and resources investigating the attack, identifying affected systems and users, and implementing remediation measures. As a result, employees may be diverted from their typical duties, and projects may be delayed.
Moreover, phishing attacks can cause emotional stress and anxiety for employees that were targeted or impacted by the attack. This can lead to a decrease in morale and motivation, further impacting your business’s productivity.
Legal Issues
Finally, phishing attacks also have legal consequences. Cybercriminals accessing sensitive customer and employee data could lead to lawsuits and regulatory fines.
These penalties can vary depending on the types of data involved and the severity of the breach.
If your business is involved in a data breach the cost of legal fees and regulatory fines can be significant. In some cases, a single phishing attack could result in years of legal battles and financial strain.
How To Spot Phishing
Phishing tactics are constantly evolving, and it’s becoming increasingly difficult to identify an attack. However, it’s crucial that you and your team can identify potential phishing attempts. Here are some common signs to look out for.
1. Be wary of unexpected or unsolicited emails
If you weren’t expecting an email from the sender, exercise caution. Look out for if they ask you to click on a link, download an attachment, or provide personal information.
2. Check the email address
Look for any suspicious elements. This could be incorrect spelling or strange domain names.
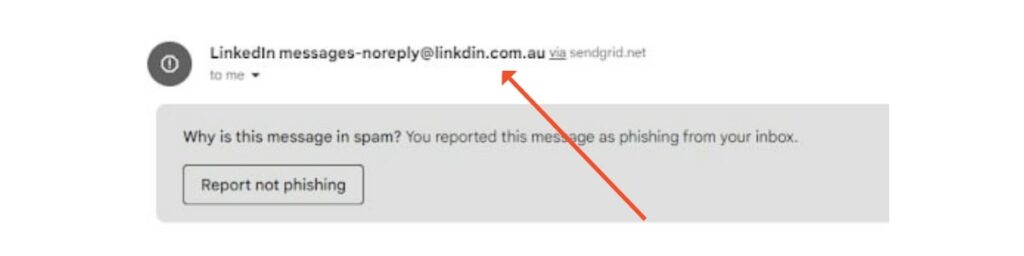
3. Hover over the link
When you hover over a link (don’t click it) you can see the URL and verify its legitimacy. However, some phishing emails may use convincing domain names or URLs.
4. Watch out for urgency
Many phishing emails will use urgent or threatening language. This is a high-pressure tactic that encourages you to take action immediately. For example, emails may threaten to close your account or offer you a time-limited deal.
5. Spelling and grammar mistakes
Legitimate emails from brands are usually well-crafted and edited. Scan the email carefully, noting any spelling or grammatical errors.
Why do scam emails make these mistakes?
Because if you notice them – it’s not for you.
They’re not interested in people who are skeptical and read carefully.
They’re interested in people who will overlook mistakes and fall for the scam.
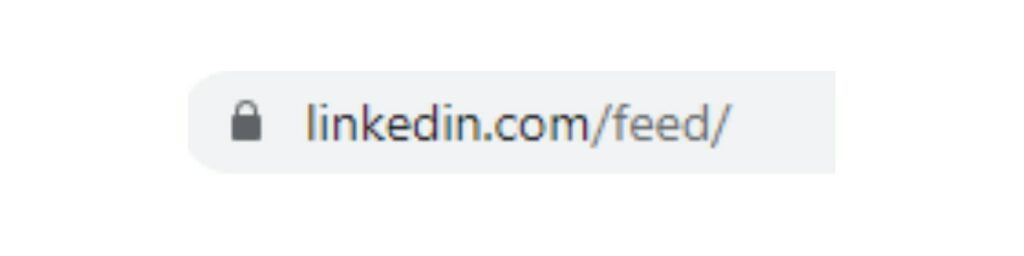
6. Look for the lock
Don’t trust any site that doesn’t have verified security. This means the URL will begin with HTTPS, not HTTP. Any sites with HTTPS will have a padlock on the address bar, so you know it’s safe. If you end up on a site that is not secure, do not enter any information.
Prevention Measures
Obviously, preventing a phishing attack is more desirable than dealing with one after the fact. In this section we’ll go through some preventive measures you can implement in your business.
Employee Training
One of the most effective ways to prevent a phishing attack on your business is to implement employee training. Employees need to be educated on the dangers of phishing, and how to identify and avoid suspicious emails, links, and attachments.
You can even copy the list above into an educational email for starters.
The training should cover common phishing tactics such as social engineering, email spoofing, and baiting.
Furthermore, encourage employees to quickly report any suspicious activity to the IT department or their manager. This can help the IT team to investigate and take action before the attack causes harm.
Conduct regular training sessions to keep employees updated on the latest threats and prevention measures. Training can also include simulated phishing attacks to test employees’ knowledge and awareness. This can help identify areas that need improvement and reinforce good practices.
Investing in employee training can not only prevent phishing attacks but also increase cyber security awareness and promote a culture of security in the workplace.
Strong Password Policies
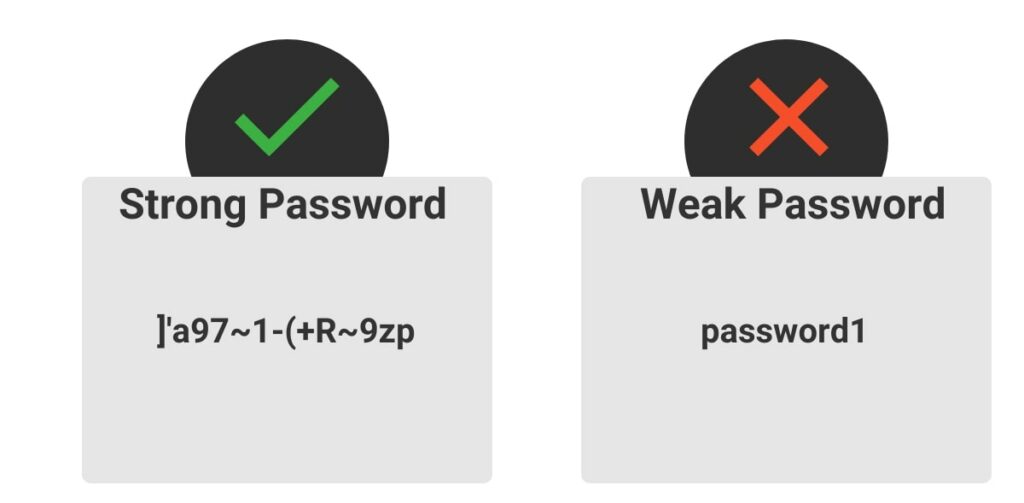
Another easy way to prevent an attack is to implement strong password policies in your business. A strong password policy will require employees to create passwords that are difficult to guess or crack. Here are some tips for creating a strong password policy.
- Length: Passwords should be at least 12 characters long, the longer the better.
- Complexity: Passwords should be complex, and use a combination of upper and lower case letters, numbers, and special characters.
- Frequency: Change passwords frequently, such as every 90 days.
- Prohibition: Prohibit employees from using personal information or commonly used passwords.
By implementing these policies, you can significantly reduce your risk of an attack. Regularly reminding employees to update their passwords and conducting periodic password audits can also help ensure that the password policy is being followed.
Multi-Factor Authentication
Multi-factor authentication (MFA) is a security process that requires users to provide two or more forms of authentication before being granted access to an account or system. This process helps prevent unauthorised access to sensitive information by adding an extra layer of security.
MFA typically combines:
- Something the user knows (like a password or PIN).
- Something they have (like a security token or smart card).
- Or, something they are (like a biometric identifier such as a fingerprint or facial recognition).
Implementing MFA can significantly reduce the risk of phishing attacks. Even if an attacker obtains a user’s login credentials, they won’t be able to access the account without the additional form of authentication.
Many online services and platforms now offer MFA as an option. It’s recommended that you encourage employees to enable MFA on all accounts where it is available. Additionally, you can implement MFA as a mandatory security measure for accessing company systems and networks.
Email Filters
Email filters are a critical prevention measure to prevent an attack. Filters will scan incoming emails and block messages that contain suspicious links, attachments, or other indicators of phishing emails.
Nowadays, most email services, such as Gmail and Outlook, have built-in filters that use machine learning algorithms to detect phishing attempts. These filters analyse the content and sender of the incoming messages and assign a score based on how likely they are to be malicious.
You can customise email filters to your company’s specific needs. For example, setting filters to block emails that contain certain keywords or come from unverified senders. You can also set them to quarantine suspicious emails for review, rather than immediately block them.
However, email filters are not foolproof. Sophisticated attackers can bypass email filters. Therefore, it is important to combine email filters with other prevention measures.
Update Software
Another crucial prevention measure is keeping software up-to-date. Cybercriminals love to take advantage of vulnerabilities in outdated software.
To prevent this, It’s important that businesses implement a regular software update schedule. This should include operating systems, apps, and security software. These updates often include security patches that address known vulnerabilities.
It’s recommended that businesses consider using automatic software updating tools. These will automatically download and install software updates as soon as they’re available.
Finally, regular security audits are an essential part of your business’s efforts to prevent phishing attacks. These audits involve an in-depth examination of your IT infrastructure, systems, and processes to identify vulnerabilities and exploitable points.
A comprehensive security audit will include several components, including:
- Penetration testing: Simulating real-world attacks to identify weaknesses in an organisation’s defences.
- Vulnerability scanning: Searching for vulnerabilities in an organisation’s systems and applications.
- Risk assessments: Help organisations identify and prioritise potential security risks based on their likelihood of potential impact.
Regular security audits can help you proactively identify and address security concerns before they are exploited by an attacker. By conducting audits on a regular basis, your business can stay ahead of emerging threats.
Note, security audits are not a one-time event. Cyber threats are constantly evolving, and security measures that worked in the past may not work today. As such, regular audits are required to ensure your business remains protected.
Incident Response
Having an incident response plan in place is crucial for any business to respond to a phishing attack effectively. An incident response plan outlines the steps and actions your business needs to take in the event of a security incident. This allows for a fast and organised response to mitigate the damage caused by the attack.
An incident response plan should include the following steps:
- Identification: Identify the source and nature of the incident, determine the scope and severity of the attack.
- Containment: isolate the affected system or network to prevent further damage or spread.
- Investigation: Collect and analyse data to determine the root cause of the incident and assess the extent of the damage.
- Eradication: Remove any malicious software or access points from the affected systems.
- Recovery: Restore the system, network and data to their pre-attack state.
- Learning: Conduct a post-incident review, identify weaknesses in the incident response plan and make necessary improvements to prevent similar incidents in the future.
A well-defined incident response plan can significantly reduce the impact of a phishing attack on your business. Remember to regularly review and update the plan to ensure it’s relevant and effective.
Case Study
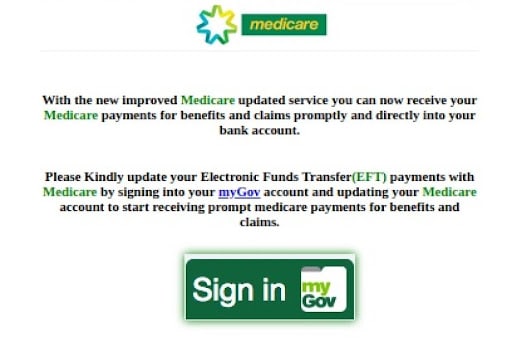
As previously mentioned, phishing attacks are constantly evolving. As people are more aware of the obvious red flags such as spelling mistakes, attackers have refined their attempts. Let’s take a look at an attack that hit many Australians in 2019.
Victims received an email, appearing to be from Medicare, prompting them to log in to myGov and update information. The email looked convincing. It even duplicated logos from Medicare and myGov websites.
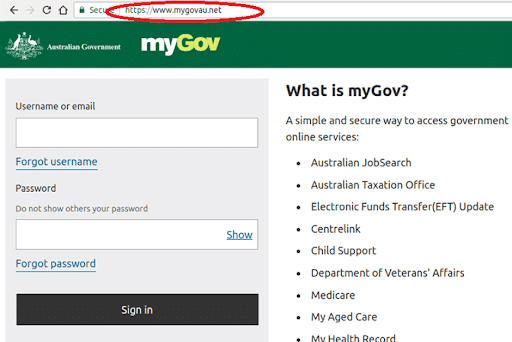
The “sign-in” link took victims to a clone myGov website, identical to the original. At a glance, the site looked authentic, it even had the lock to indicate it was a secure site. The only giveaway was the URL.
The real myGov URL is my.gov.au – as opposed to the phishing site, mygovau.net.
Needless to say, the scam worked on a number of people. A scam this convincing is difficult to detect. This is why knowing the signs to look out for is so important.
Future Trends
As phishing attacks continue to evolve, it’s important to stay up-to-date with the latest trends to protect your business.
AI-powered attacks
The world has become extremely interested in AI.
As AI technology advances, cybercriminals are expected to rely heavily on AI to create more sophisticated and targeted attacks. Criminals can use AI to automate and personalise attacks based on data gathered online. This can make attacks harder to detect and difficult to protect against.
For example, criminals can use AI to craft fake emails and websites that appear legitimate, making it easier to trick victims.
AI can also quickly adapt attack strategies based on the victim’s behaviour and response to previous attacks.
To stay ahead of such attacks, businesses will need to continue to invest heavily in advanced security solutions and training programs to help employees recognise and respond to AI-powered attacks.
Mobile Phishing
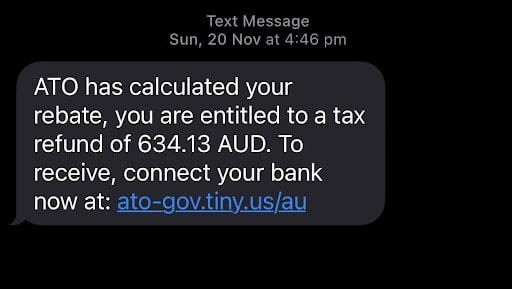
Mobile phishing, also known as “smishing” (SMS phishing) or “vishing” (voice phishing), is becoming increasingly common. Attackers will use mobile devices such as smartphones and tablets to deliver malicious content. With the rise of mobile banking and payment systems, cybercriminals are looking for ways to exploit vulnerabilities in these devices.
Mobile phishing attacks typically involve sending a fraudulent text, voicemail, or phone call. These will appear to be from a legitimate source such as a bank or government agency. The message may ask you to click on a link or provide personal information.
One common tactic used in mobile phishing attacks is to create a fake mobile app that appears legitimate. These are often banking or shopping apps. These apps will look and feel like the real thing. However, they’re designed to steal the user’s information.
Much like other methods of phishing, it’s important to be careful when clicking on SMS links or providing personal information on your mobile device. Keep business devices up-to-date and use anti-malware software to detect and remove potential threats.
Ransomware
If you’ve been paying attention to cybercrime in Australia, you’ll know ransomware is on the rise.
Ransomware is a type of malware that encrypts the victim’s files and demands payment in exchange for the decryption key.
Ransomware is commonly delivered through phishing emails delivering malicious links or attachments. When clicked, the link downloads the ransomware onto the victim’s device.
Once ransomware infects the device it can quickly spread throughout the network. It encrypts files, rendering them inaccessible. This can lead to significant downtime, loss of productivity, as well as potential data losses.
Paying the ransom is not recommended. You may not receive the decryption key. You may not recover all of your files. And by paying you are funding and encouraging the activity.
Instead, there needs to be a focus on prevention and comprehensive incident response.
Conclusion
Phishing attacks continue to pose a significant threat to businesses of all sizes and across all industries. It’s essential that you take proactive steps to prevent attacks from happening.
Ultimately, the key to preventing phishing attacks is to remain vigilant. Stay informed about the latest trends and tactics attackers use. Implement strong security measures. And protect your business and your customers.
By taking these steps, you can reduce the risk of falling victim to an attack and safeguard your reputation, financial stability, and customer trust.
