Malware is a problem for businesses of all sizes. It can be used to steal personal data, disrupt operations, and cost thousands or even millions of dollars in lost productivity and remediation expenses.
Every day, over 450,000 new malicious programs are registered.
Among these threats, ransomware is particularly damaging, with the average cost of recovering from a ransomware attack in 2023 being $1.82 million, contributing to a total global cost of ransomware attacks exceeding $30 billion.
All this is to say – as a business owner, it’s important to understand the various types of malware, how they work, and the steps you can take to protect your business.
In this blog post, we’ll discuss the different types of malware and how they can affect businesses. We’ll also provide tips and best practices to help you keep your business safe.
KEY TAKEAWAYS
- Malware is software used by cyber criminals to damage, disrupt, or gain unauthorised access to a computer system.
- It’s commonly spread through email attachments, text messages, infected websites, and removable media (USBs)
- Signs you have an infected computer include random pop-up windows or alerts, slow computer performance, unfamiliar programs or icons, and unexpected crashes.
- Prevent malware with regular system updates, antivirus & firewall software, strong passwords, and cyber security training.
- Attackers often use social engineering techniques to distribute malware.
What Is Malware?
Malware is a type of malicious computer program designed to disrupt, damage, or gain unauthorized access to a computer system.
Its roots can be traced back to the emergence of the first computer virus in the early 1980s, marking the birth of what we now know as malicious software or malware.
It is usually spread through internet functions like emails, websites, and removable media like USB drives. A threat actor will use malware to steal data, delete files, and infect other computers with malicious code. It can also install programs designed to exploit network security vulnerabilities.
Malware seriously threatens businesses because it can cause data loss, decreased productivity, and financial losses. Cybercriminals also use malware to launch cyber-attacks against companies, allowing attackers to access confidential data and cause reputational damage.
Attackers could target your business for any number of reasons. Commonly, malware attacks are for financial gain, disrupting a business, or even for political reasons. Some attacks may aim to steal identity theft information or disrupt services to cause chaos.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
How Does Malware Spread?
Malware spreads in various ways, including email attachments, infected websites, and removable media.
Email Attachments
Malware is commonly spread through a malicious email attachment. These attachments are usually disguised as legitimate files, such as PDF or Word documents. However, when opened the attachments contain malicious code that will infect the computer. It’s important for you and other users to be cautious about opening any emails or attachments that seem suspicious. That includes emails that appear to be from someone you know and trust.
Infected Websites
Malware is also spread through infected websites. Many websites have vulnerabilities that hackers can exploit to gain access to user data or install malicious code on their computers. It’s important for users to be aware of which sites they visit and to make sure they are using secure connections when accessing sensitive data.
Removable Media
Malware can also be spread through removable media such as USB drives, external hard drives, and CDs. These devices can contain malicious code that they transfer to a computer when inserted into a USB port or CD drive. To avoid this, users should only use removable media from trusted sources and scan all files with an up-to-date antivirus before opening them.
These are just some of the ways malware can spread to new devices. Businesses need to remain vigilant and take steps to protect their networks and data from malicious attackers. By installing security software, training employees, and backing up data regularly, businesses can stay ahead of potential threats and minimize the risk of a malware attack.
What is an Example of Malware?
Here are some of the most common types of malware threats that could affect your business.

Ransomware
Ransomware is a type of malware that infects a computer or network and holds files hostage until a ransom is paid.
The most common form of ransomware is cryptoviral extortion, which encrypts the victim’s files and then demands payment to decrypt them.
This is commonly delivered via phishing attacks and drive by downloads.
Once a ransomware attack infects a system, it will often display a message informing the user that their data has been encrypted and that they must pay a ransom to regain access to their files. Ransom payments are typically requested in a cryptocurrency such as Bitcoin, which makes it difficult for authorities to track the source of the money.
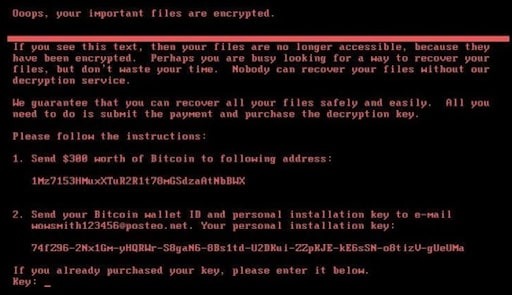
Businesses are particularly vulnerable to ransomware attacks because they have more valuable data for which criminals can demand money. If a business’s data is held hostage, it can result in financial losses, decreased productivity, and reputation damage. In some cases, businesses may choose to pay the ransom if they cannot recover their data through backups or other methods.
However, current advice is that victims of ransomware do not pay the ransom.
Trojan Horse
A trojan horse is a malicious program that acts as legitimate software or document. Once installed on the victim’s device, it can perform a variety of functions without the user’s knowledge or consent. It can log keystrokes, send out spam emails, steal data and more.
Because they are difficult to detect and identify, Trojans are one of the most dangerous types of malware. Hackers use Trojans for espionage, fraud, cyber-terrorism, and other malicious activities.
Banking Trojans
Banking Trojans steal financial information from businesses and their customers.
The primary purpose of banking Trojans is to gain access to online banking credentials used on online banking systems. These include:
- Usernames
- Passwords
- Credit card numbers
Hackers also use bank Trojans to take control of a user’s computer or device, allowing the attacker to access confidential files and other data.
Like other malware, banking Trojans are spread through phishing emails and downloads from unsafe websites.
Once installed, banking Trojans can monitor web traffic and harvest financial information. They can also assist with launching a DDoS attack on websites and networks.
Banking Trojans can devastate businesses, leading to data loss, decreased productivity, and financial losses. Because banking Trojans often target businesses that use online banking systems, a successful attack could also lead to significant reputational damage.
Protect your business from cyber attacks. Safeguard customers and end-users, and create a clear picture of your cyber security landscape.
Worms
Worms are a type of malware that can replicate and spread across networks, infecting other computers.
Worms can be hard to detect, as they operate quietly in the background. They are especially dangerous because they can spread quickly, causing widespread damage to businesses.
Like other malware, worms can steal data and access passwords. They can also send out spam emails and download malicious content onto other systems. In addition, worms can replicate themselves in order to avoid detection. This means that, once a worm has been released it can spread rapidly without any intervention from the user.
A famous example of a worm known as Conficker targeted the Microsoft Windows OS. Using advanced malware techniques, the worm spread to millions of government agencies, businesses, and home computers in over 190 countries, making it one of the largest known worm computer infection events ever seen. Surprisingly, the worm is not thought to have done much damage, is it was never used for any specific purpose.
Spyware
Spyware is a type of malware installed on business devices that then tracks and monitors user activity, all without the user’s knowledge.
Sounds pretty sneaky right?
Hackers will use spyware for various purposes, including monitoring online activities, stealing business data, or tracking browsing habits.
Spyware is particularly dangerous for businesses when used to track employee activity, steal data, or gain access to confidential information. Cybercriminals may use spyware to monitor emails and other data, eavesdrop on conversations, capture confidential files, monitor keystrokes, and gain access to accounts and networks.
As well as being a serious threat to a business’s security, it can also lead to lost productivity and financial losses if confidential information is stolen or leaked, as well as reputational damage.
Adware
You’re probably already familiar with adware.
Adware targets computer users in order to display advertisements. It’s often installed on a computer system without the user’s knowledge, typically by downloading a free application, template, or software.
Companies will use adware to generate revenue from displaying ads, and often includes features such as tracking a user’s browsing habits and collecting data for targeted advertising.
Adware can range from relatively benign programs that show ads in an annoying way to malicious programs that can track a user’s personal information and transmit it to third parties without the user’s permission.
We most commonly see adware distributed through pop-up ads, banners, and search engine redirects.
Additionally, some forms of adware install automatically after clicking on a link in an email or even through drive-by downloads which occur when users visit an infected website.
Adware can be especially dangerous when it has the capability to track a user’s browsing activity and collect data that can be used for targeted advertising. This type of adware can track a user’s IP address, the pages they visit, the links they click, and even the searches they enter into search engines. In some cases, this data can be sold or shared with third parties without the user’s consent.
Furthermore, adware often forms part of a cybercriminals strategy to gain access to business data such as financial details and sensitive information. Cybercriminals can use such data for various fraudulent activities.
It is important for businesses to be aware of the dangers associated with adware and take steps to protect their systems.
Fileless Malware
While many types of malware rely on planting malicious files into a system’s storage to carry out their operations, fileless malware takes a stealthier approach.
As the names suggest, fileless malware doesn’t use files as part of its operations. Instead, it leverages legitimate system tools and runs malicious scripts directly from a system’s memory.
This type of malware is particularly sneaky because it leaves no traceable artifacts. This makes it incredibly difficult for traditional antivirus software to detect. It often exploits applications that are trusted by system security measures, like PowerShell or Windows Management Instrumentation.
The sophistication of fileless malware makes it crucial for businesses to implement advanced threat detection and response strategies capable of identifying and eliminating malware infection.
How Do You Tell If You Have Malware?
There are several signs that your business devices are infected by malware:
- Strange pop-up windows or alerts: Malware may display unwanted pop-up windows or alerts on your computer.
- Slow computer performance.
- Changes to your homepage or search engine: Malware may change your homepage or search engine without your permission.
- Unfamiliar programs or icons on your desktop.
- Unexpected or frequent system crashes.
- Issues shutting down or starting up your computer.
If any of these issues are present on your business’s devices, it’s possible they are infected with malware.
It’s important to take action immediately to prevent further damage. You should run a malware scan, remove any detected threats, and consider installing anti-malware software to protect against future infections.
How To Protect Your Business From Malware
There are several steps your business can take to prevent malware infection:
- Install and maintain firewall and anti virus software: Virus protection software can help protect your computer and network from malware by blocking known threats and alerting you to suspicious activity. Additionally, integrating anti malware software provides a more comprehensive security shield, capable of detecting and combating a wider range of malicious threats.
- Keep all software up to date: Make sure to keep all software on your devices, including the operating system, web browsers, and any other programs, up to date. Software updates often include security patches that can help protect against malware. Uninstall unwanted software.
- Use caution when opening email attachments and links: Be wary of opening email attachments. Don’t click on links from unknown sources.
- Implement strong passwords and use two-factor authentication: Use strong, unique passwords for all accounts and enable two-factor authentication whenever possible. This adds an extra layer of protection by requiring you to enter a code sent to your phone or email in addition to your password when logging in.
- Educate employees about cyber threats: Make sure your employees are aware of the importance of cyber security and how to recognize and avoid potential threats.
Malware protection is relatively straightforward. And using these simple measures you can better protect your business.
Conclusion
Malware is a serious threat to businesses of all sizes. It’s important to be aware of the different types, as well as the various ways it can be transmitted.
Taking steps to protect your business from malware can help to minimise the potential damage it can cause. Utilise strong security measures to protect your business from malicious actors.
Additionally, staying up-to-date on the latest cyber security news and trends can help to keep your business secure.
Taking action now can help to ensure your business is safe and secure.
More Like This
Windows 10 End of Life (EOL) and What it Means
Microsoft has announced that October 14, 2025, will be the End of Life (EOL) date for Windows 10. Windows 10 EOL is set to affect all versions of Windows 10, including Home, Pro, Education, and Enterprise. Research from Lansweeper indicates that only 23.1% of...
ISO 27001 Certification in Australia: A Comprehensive Guide
Business data is like a treasure for cyber criminals. In fact, buried in almost every organisation's information assets are details worthy of holding ransom. So, how do you protect it? With ISO 27001 certification. ISO 270001 is more than just a standard industry...
Cyber Hygiene For Business: What You Need To Know
Implementing cyber hygiene practices is one of the most effective ways to protect your business from cybersecurity risks. As a business owner, the security of your company's data is paramount. With the prevalence of cyber-attacks in the modern world, it’s increasingly...



