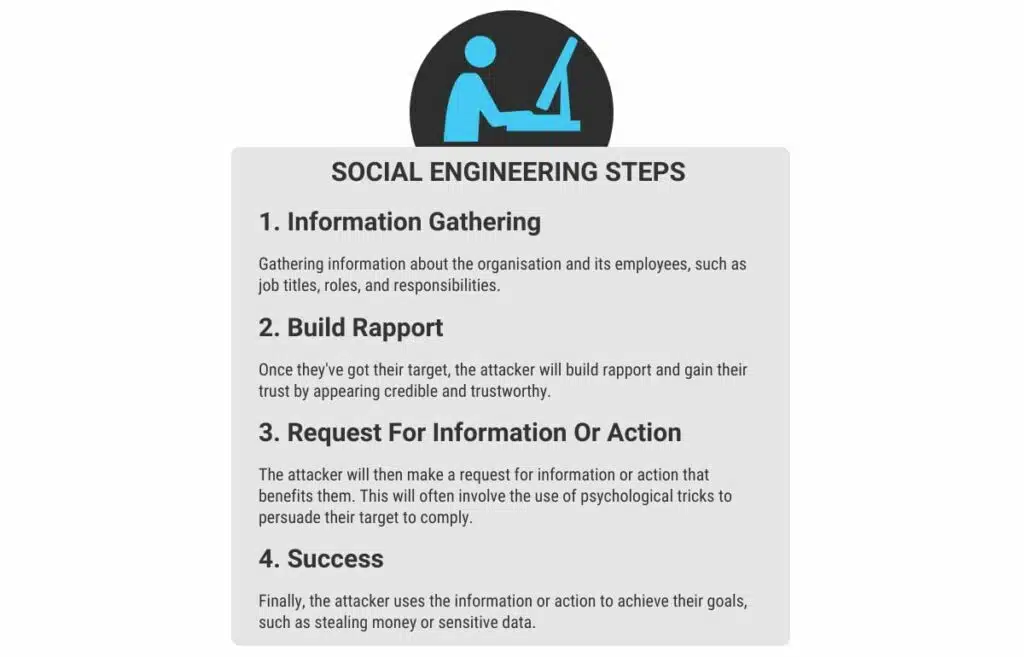
What if I told you that many cyber attacks were largely preventable? Social engineering is not a new phenomenon, yet people in a number of organisation’s continue to fall for them.
This is because they prey on the on the most vulnerable aspect of security – human error.
Social engineering attacks infiltrate the minds of unsuspecting victims, manipulating them into disclosing valuable information and personal data, or carrying out actions that can harm their organisation.
In this post, we’ll discuss the world of social engineering and examine real life examples. We’ll then offer 10 actionable steps you can take to fortify your business.
Key Takeaways
- Social engineering attacks exploit human error rather than technical vulnerabilities, manipulating emotions like trust, urgency, and authority to trick individuals into revealing sensitive information.
- Phishing and spear phishing are common tactics, with attackers using emails that appear legitimate to deceive victims into providing credentials or financial information, making it crucial to verify the sender’s authenticity.
- Cybersecurity policies and employee training are essential in protecting against social engineering attacks. Clear policies, regular security awareness training, and multi-factor authentication can help employees recognise and avoid such threats.
- Mobile device management (MDM) tools can limit the damage of social engineering attacks by controlling access to company data and restricting the sharing of sensitive information on both personal and corporate devices.
- Regular software updates, encryption, and role-based access controls provide additional layers of defense, ensuring that even if an attack occurs, your business is equipped to minimise the potential damage and protect critical information.
What is Social Engineering?
Social engineering is a fancy word for manipulation.
Social engineering attackers aim to take advantage of human nature in order to access private information.
What does this mean?
Social engineers want us to feel a certain way. They want to create a sense of:
- Trust
- Urgency
- Kinship
- Authority
- Disdain
- Power
- Stress
- Pity
And they’ll use various social engineering techniques like phishing, pretexting, and baiting to deceive their intended victim.
We all want to help those that we care about, and that’s exactly what attackers are hoping for.
They’ll appeal to the target’s natural tendency to help a friend or family member in need. They want to elicit an emotional reaction.
They want to put the victim in a position where they think now and act later.
After that, they can abuse that position to trick their victim into opening an email, clicking a link, or accepting a download. This download infects the computer with malicious software.
It’s often easier to exploit our instinct to trust than it is for attackers to try and hack into a system.
If they can fool you into giving away your credentials it’s an easy pay day for them. So, you can see the appeal.
A regular hacker will often look for software vulnerability and cyber security gaps. A social engineer, on the other hand, uses deceit to get an employee to divulge login credentials.
Social engineering itself is not necessarily a new concept. But social engineering scams have become more sophisticated and personalised.
They’re also becoming more common for small-to-medium businesses to encounter. We’ve all received a dodgy email from a known contact but they’ve always been easy to identify. You don’t expect to receive “CLICK HERE FOR XXX” from grandma Jean in your inbox, right? So the attacks were easy to avoid.
But, they’re less obvious now and use psychological manipulation to target unexpecting victims.
How so? Read on…
What are some Social Engineering tactics?
Let’s take a look at some social engineering tactics. Understanding what social engineering attacks may look like will help you to recognise and identify such attacks. As a result, you’re less likely to fall victim to an attack.
Phishing
Imagine receiving an email that looks exactly like it’s from your bank, asking you to confirm your account details.
It seems urgent and official, but it’s actually a phishing attempt.
Phishing attacks use emails that mimic legitimate organisation’s to trick you into providing sensitive information (passwords or credit card numbers).
Attackers often use search engines to gather information about their targets, making their phishing attempts more convincing.
It’s a reminder to always verify the sender’s authenticity before clicking on links or sharing any personal information.
We dive deeper into phishing in our article that you can read here.
Quick tip: if you’re not sure if the email is legitimate, take a closer look at the sender’s address.
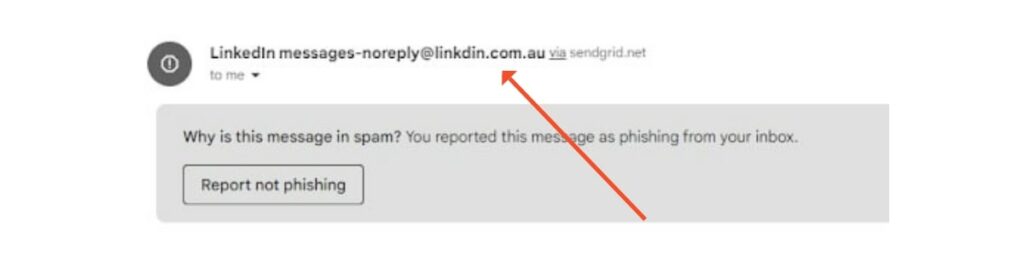
Spear Phishing
Now, picture this: you get an email addressed to you personally, referring specific details about your work or personal life.
This is a spear phishing attack, a more targeted form of phishing.
Attackers gather information about you from various sources, even ones as simple as Google search results, to make their message seem trustworthy.
Because the email feels personalised, it’s easier to fall for the scam.
Always be sceptical of unsolicited requests for sensitive information or personal details, even if they seem tailored to you.
Pretexting
Pretexting is like a con artist’s best trick.
An attacker creates a believable story or pretext to obtain your personal information.
For example, someone might call you pretending to be from IT support, claiming they need your login credentials to fix an issue.
They rely on your trust and the pressure of the situation to get what they want. It’s crucial to verify the identity of anyone requesting sensitive information, especially if it’s over the phone.
Quid Pro Quo
Something for something.
Have you ever been offered something in exchange for information?
That’s the essence of quid pro quo attacks.
An attacker might pretend to be a tech support agent offering to help with a problem you didn’t even know you had, in exchange for you login details.
It’s an appealing offer, but one that can lead to a serious data breach.
Always be way of unsolicited offers, especially if they involve sharing personal information.
Impersonation
Impersonation attacks take advantage of established trust.
An attacker poses as someone you already know, like a company executive or familiar colleague.
They might request sensitive information or access to systems, counting on you to comply without question.
Unlike pretexting, where a story is created, impersonation leverages your trust in the person they are pretending to be.
In 2016, an employee in Snapchat’s payroll department fell for exactly this scam with an HR employee handing over payroll information to an attacker impersonating the CEO.
Always double check the identity of anyone making unexpected requests, even if they seem to be someone you know well.
Vishing (Voice Phishing)
Vishing, or voice phishing, involves scammers using phone calls to trick you into revealing sensitive information.
You might receive a phone call from someone claiming to be from the bank, urgently asking for your business account details to resolve a supposed issue.
These calls can be very convincing, but remember that legitimate organisation’s rarely ask for sensitive information over the phone.
When in doubt, hang up and call the organisation back using a verified number.
Business Email Compromise
Business Email Compromise (BEC) is a sophisticated scam targeting businesses that conduct wire transfers and have suppliers abroad.
Attackers gain access to a business email account through phishing, social engineering, or other means.
Once inside, they use the compromised email account to trick employees or partners into transferring funds to fraudulent accounts.
For example, an attacker might pose as a company executive or trusted vendor, instructing an employee to make an urgent payment to a specific account.
The email appears legitimate, which makes it difficult to detect fraud until it’s too late.
The Influence of AI
AI will shake up cyber security. There’s no doubt about it.
Research from Darktrace indicates that there has been a 135% increase in new social engineering attacks in 2023.
This suggests that hackers are using generative AI tools like ChatGPT to construct targeted attacks at scale. This will likely make it more difficult to spot red flags in phishing emails.
For example, if a lot of your writing is online, attackers can feed examples of it into an AI system. The AI can then produce convincing emails written in your style.
It’s a developing area of cyber security that we all need to keep an eye on.
Examples of Social Engineering Attacks
Facebook and Google Scam
A notable example of a successful social engineering attack was against Facebook and Google.
The attacker, a Lithuanian man, impersonated a Taiwanese electronics manufacturer. He registered a company in the same name and sent fraudulent emails requesting payment for goods that the legitimate company had provided.
Thinking nothing of it, finance at Google and Facebook paid the fraudster a combined $100 million.
Toyota
In 2019 a supplier of Toyota parts was hit by an email scam, costing them $37 Million.
The attackers convinced a financial executive to change account information for an upcoming electronic transfer.
Merseyrail
A British railway company suffered a rather embarrassing social engineering attack.
Journalists received an email that appeared to come from the company’s director. The email revealed that Merseyrail had been hacked, however it tried to downplay the attack.
The attack appeared to have originated via a successful compromise of a privileged Microsoft 365 account. It was likely the result of a spear-phishing campaign.
In addition to sending the email to journalists, many employees received an email about the attack. This is known as a double extortion technique, as it puts pressure on the company to pay up via a public shaming campaign.
Protect Your Business From Social Engineering Attacks
A lot of cyber-attack prevention boils down to many of the same tools and steps. It’s about reducing your exposure, being aware of vulnerabilities, and utilising tools to increase your protection.
Having said that, social engineering attacks can be a little different, as they play on human emotion. Ultimately, there’s not much that an anti-malware program or firewall can do to stop a person from giving away the goods.
Keep in mind that many examples of social engineering will try to bypass your security system completely. But there’s a number of steps you can implement within your business to reduce your risk of social engineering attacks. We’ll run through them with you to ensure your business is on the right path.
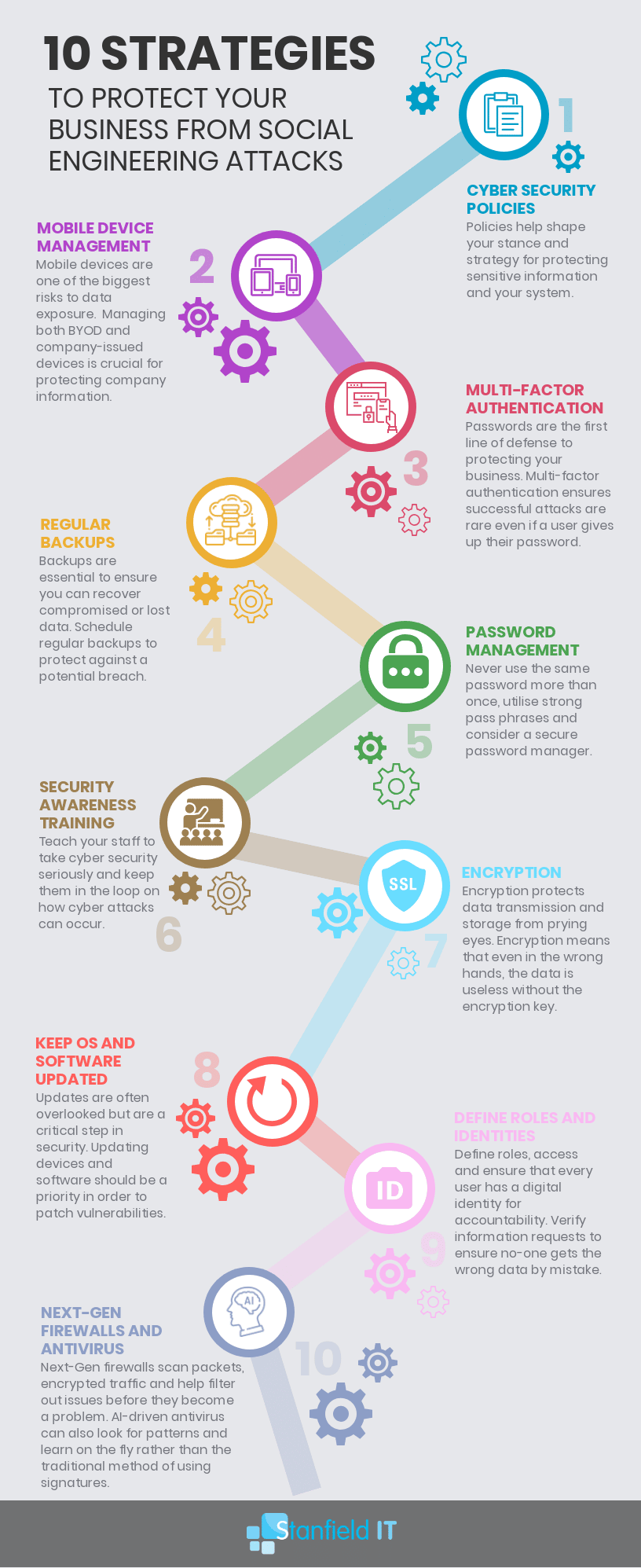
1. Cyber Security Policies
Cyber security policies may sound incredibly boring and tedious. However, they are crucial to protecting your business and employees from social engineering attacks.
Although it’s not enough to just create the policies. They need to be well understood and enforced. Don’t stick it in the back of the employee manual that no one ever reads. Keep the policy clear, visible, and regularly reinforced with your staff to ensure the recommendations becomes habit.
Having a solid cyber security policy will do a few things to help prevent social engineering attacks:
- Individuals are less likely to click on phishing links or give out credentials online.
- It reduces the chance of accidently downloading malicious files onto the system.
- Having high-level email spam rules and policies can filter out many social engineering attacks from the get-go as they fail to pass filters.
2. Mobile Device Management
Mobile device management is protection for your business and for employees using a mobile device. This is especially relevant when they are using a personal device for work, instead of a company-issued device.
Mobile-device-management tools enable you to implement policies that control company data, passwords, sharing restrictions, and more.
Even if an employee falls victim to a social engineering attack, you can control what data attackers can access and share.
Let’s say you suffer a pretexting attack. Now Janet in accounts thinks she needs to send a copy of payroll information to Bob the CEO. Mobile device management ensures that Janet isn’t able to share those documents, or even copy the information within, based on your restrictive rules designed for just this purpose.
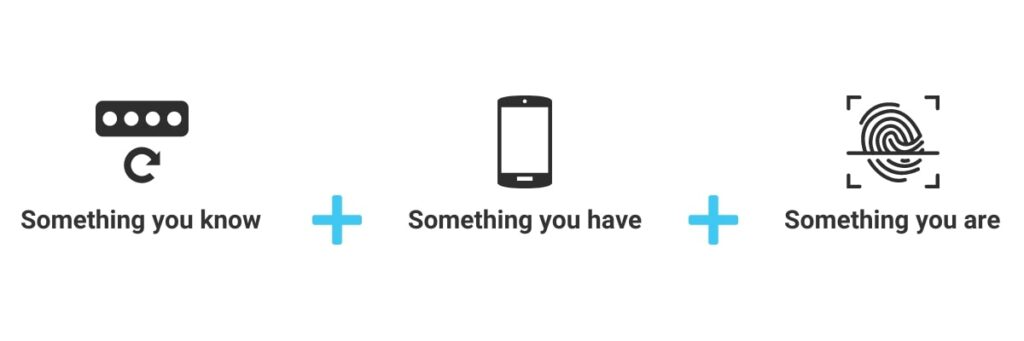
3. Multi-Factor Authentication
We always come back to this one. Multi-factor authentication ensures that account security is not defined by just one factor (the password).
Passwords are important, sure, but as we’ve come to realise, they are insufficient on their own. Why? It’s far too easy for someone else to get access to your password, and therefore access to your accounts.
Whether that password is accessed via social engineering, or because Janet wrote it on a post-it next to her computer, the result is the same: unauthorised access.
Multi-factor authentication ensures that the password is not the master key to any given account. An additional verification will be required which could be anything from a security question, to a one-time generated code, or even biometrics such as fingerprints or facial recognition.
4. Regular Backups
Time to rag on Janet a little more.
She defied all policies and logic, and failed to engage the slightest bit of suspicion or common sense.
She clicked the link that Bob The Fake CEO sent her and now the company has been infected with a virus hell bent on destroying everything.
But… thank goodness you followed sensible protection policies and scheduled regular backups for your data. You’re able to revert the system back to its original state, change all passwords and update policies as required. And give Janet a stern talking to. If any Janet is reading this, we’re so sorry.
5. Password Management
This should be integrated into your cyber security policies, but it’s worth covering as a separate point.
Good password management is incredibly important to prevent social engineering attacks. I know we just said that passwords are not the be all end all, but that doesn’t mean you can get away with password1234 on all your accounts. And yes, people still use that password.
Good password management means doing a few things:
- Creating a strong password (random, multiple cases, characters, and passphrases are all excellent).
- Never using the same password more than once.
- Using a secure password manager to keep track of all your logins, and changing passwords at scheduled intervals (for example every 3-6 months).
6. Security Awareness Training For Employees
As mentioned above, it’s not enough to just stick a cyber security policy in the back of the manual and call it a day. Employees need to be able to take charge of cyber security. They must understand where attacks can come from and what they can do to avoid an attack. This means that your employees beed cyber security awareness training.
Essentially, you want these procedures and protocols to become second nature to your employees. If they feel that they have ownership of cyber security and attack prevention, they are far more likely to follow cyber security protocols and your risk of social engineering attacks will be reduced.
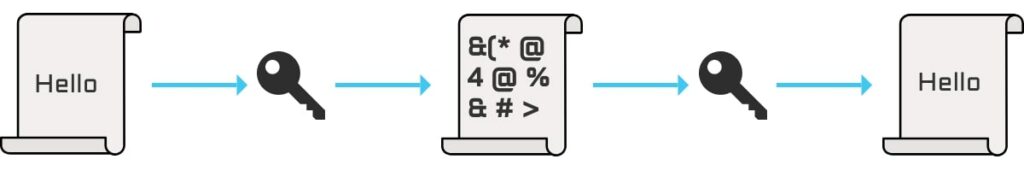
7. Encrypting Emails and Data
Ensuring that all your emails, data, and communication are encrypted ensures that, even if an attacker intercepts your data in transit, they aren’t able to view or access the included information. Their ‘payload’ is useless, as they can’t use any of the information contained within. You can achieve this by utilising a VPN within your business, which will encrypt data transmitted between you and any websites, protecting you from prying eyes.
8. Keep Software/OS Up to Date
This is a simple, yet critical, step that shouldn’t be overlooked.
It’s so easy to put off those updates, as they always seem due at the most inconvenient times. These updates, however, reduce vulnerabilities and keep your system secure.
Rolling out patches across a large network can be time-consuming, but knowing which software has critical vulnerabilities and the updates that are more urgent can help you to prioritise and manage the task at hand. Of course, employing an external team to manage your IT services will be a big boon in this instance, so it’s not something you need to fret about.
9. Define Roles and Verify Identities
If you have a workplace where everyone does a bit of this and a bit of that, it’s hard to know where to draw the line in terms of who can access what.
Defining roles within the business means that everyone has a clear cut understanding of what they can and should access at any given time. This cuts down on successful social engineering attacks as individuals know that George (let’s give Janet a break) isn’t permitted access to the employee database he’s suddenly requesting, immediately raising a red flag.
Furthermore, having a system of identity verification internally will help to reduce this risk as well. It may be that any time certain requests are made, or certain information is being accessed, employees are required to answer a security question or provide a pre-determined passphrase. Social engineers often do their research on their targets and can be very convincing in their assumed identities, so having a method of verification provides that extra security.
10. Utilise Next-Gen Firewall and Anti-Virus
You are probably already using a firewall and anti-virus software within your business, but next-gen firewall technology (NGFW) is designed to provide maximum security in ways that previous versions didn’t.
Traditional anti-virus and firewall software doesn’t have the sophisticated techniques and knowledge required to truly protect your system against modern attacks. Although social engineering attacks rely on human mistakes, a good NGFW will alert you to any attempted malware installations, preventing any potential infiltration.
Quick Tips
Let’s finish with some tips from expert Pierluigi Paganini, as published in Digital Guardian, who is a security researcher for the InfoSec Institute and boasts 20+ years of experience.
- Stay vigilant of spam, flag emails that request personal or financial information; call for quick action by threatening the user with frightening information; or are sent by unknown senders.
- Regularly monitor online accounts to make sure no unauthorised transactions have been made.
- Never give personal information via the phone or malicious websites.
- Don’t click on links, download files, or open email attachments if you don’t know the sender and recognise the email address.
- Only complete online transactions on websites that use the ‘https’ protocol. Also look for a sign that indicates that the site is secure, such as a padlock on the address bar.
- Beware of phone phishing and never provide personal information over the phone. Also, beware of emails that ask the user to contact a specific phone number to update their information.
- Never give personal or financial information via email.
- Beware of links to web forms that request personal information, even if the email appears to come from a legitimate source. Phishing websites often disguise themselves as exact replicas of legitimate websites.
- Beware of pop-ups; never enter personal information in a pop-up screen or click on it.
- Adopt proper defense systems, such as spam filters, anti-virus software, and a firewall, and keep all systems updated.
- Social network users should trust no one and reveal only a limited amount of information. They should never post personal information on the social networking site. This includes vacation schedule and home photos, click on links and videos from unknown origin, or download uncertified applications.

Conclusion
Reviewing the examples of social engineering above, it’s clear that social engineering targets a huge part of human nature. It plays on our curiosity and desire to help. It’s human nature to be curious; we want to know everything! A Google study showed that 48% of individuals who picked up a random stray USB drive then plugged it into their computers. This is beyond risky.
Moreso, we want to help our fellow humans, especially those close to us or in our everyday lives. Social engineering attacks exploit this. This is why so many cases of social engineering involve a request for assistance from either coworkers, or friends―these are people we tend to trust. And the ones we’re willing to help.
Social engineering has been around ‘forever’, of course―it’s not a new technique. However, social engineering attacks have grown more sophisticated in recent years. With social media now so mainstream, it’s easier than ever for these attackers to collate relevant information in order to present a convincing identity. According to a study by KnowBe4, a whopping 98% of hackers target users via social engineering rather than through a technical flaw.
Overall, these steps won’t prevent social engineering attempts on your business―the hackers will just keep on trying. Keep the examples of social engineering in mind and learn to recognise them so that if such an attempt comes your way. This way, you’re already on the defence and less likely to fall victim to social engineering attacks.