Two-factor authentication (2FA): It’s a term that every internet user in the 21st century should be familiar with, and for good reason. Given the nature of threats to digital security, 2FA serves as a crucial additional check that ensures users are who they say they are.
When setting up or using 2FA, a user might have to provide a one-time passcode generated on their phone, or input an authentication code sent over text message. This extra step creates a separate proof of identity that potential hackers wouldn’t have access to, thereby increasing the security of your accounts.
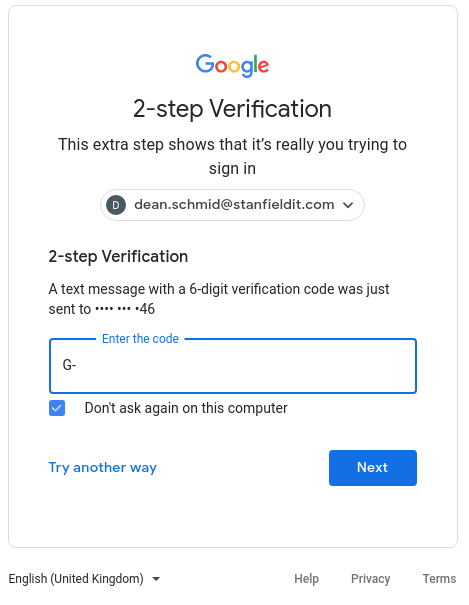
2FA has spread quickly over the year – a testament to its effectiveness. Popular platforms such as Gmail, WordPress, Amazon, Apple, eBay, and GitHub, among others embrace it. In fact, you’re unlikely to find a site today that doesn’t offer the option to enable two-factor authentication. There is also multifactor authentication (MFA), which adds even more layers of security. It isn’t a fleeting trend – it’s a necessary shift towards ensuring our digital profiles remain in the right hands: ours.
Why Businesses Need Two-Factor Authentication
Unfortunately, your accounts are valuable and hackers want to steal from you.
The cyber security landscape is rife with threats such as credential stuffing, where malicious bots use stolen or hacked passwords to gain unauthorized access.
They relentlessly attempt to log into accounts across various platforms using these credentials, hoping for a match. Essentially, your business’s passwords are only as secure as the weakest database they’re stored in.
In addition, most businesses rely on online platforms and data This makes the protection of sensitive information of huge importance. And this is where 2FA steps in as a crucial security measure, because the trusty username and password combination isn’t as secure as we would like.

Reduced Risk of Data Breaches
2FA adds an extra layer of security, making it harder for attackers to access company data. Even if a password is compromised, the additional authentication step ensures that your business’s sensitive data remains secure.
Regulatory Compliance
For businesses in sectors like healthcare and finance that handle sensitive customer or client data, adhering to regulatory standards is non-negotiable. In simple terms; you have a duty to protect the information you collect.

Boosted Customer Confidence
By implementing 2FA, you’re sending a strong message to your customers that you’re taking their data seriously. Remember, businesses thrive off trust. You don’t want to lose it by neglecting simple actions like implementing 2FA.
Protection Against Phishing
The average cost of a phishing attack for mid-size companies is
$1.6 million – dashlane
Phishing is an attack where a hacker sends a deceptive email that tricks employees into typing their password into a dummy form. The credentials they enter are then sent to the hacker. 2FA can help prevent against phishing attacks. Even if an employee unknowingly shares their login credentials via a phishing scam, the second authentication factor adds a protective layer to prevent unauthorised access.
Remote Work Protection
As remote work becomes the new norm, it’s critical to ensure secure access to company resources outside the office environment.
Understanding Two-Factor Authentication
To understand 2FA, think of it like a security checkpoint with two gates. To pass through, you’ll need to clear each gate using a different security key. These “keys” are the two separate factors used for verification.
- Something You Know: This is often a password or a PIN. It’s something you memorise and keep to yourself.
- Something You have: A possession factor could be your mobile device, hardware token, or a smart card. It’s something you physically possess.
How does it work?
Step 1: You enter your username and password (Something You Know) into the login page of an account.
Step 2: A prompt will then ask for a second form of authentication. This could involve entering a code sent to your mobile phone (Something You Have) or confirming the login attempt through an authentication app.
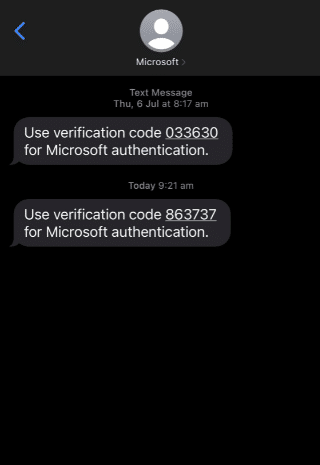
Step 3: Once you’ve successfully entered both authentication factors, you’ll gain access to the account.
To summarise, 2FA provides an extra layer of security by requiring two different authentication methods. If one factor is compromised, the second layer still stands. This makes it more challenging for an attacker to access your account.
How Do Hackers Steal Passwords?
A password is a shared secret between you and the systems you interact with. When you create an account on a website or an application, your credentials are stored in their data base. This allows the system to verify your identity for future logins.
But this poses a significant risk. Every account you create, every service you sign up for, has a copy of your credentials. This means an ever growing number of systems hold your password. And you’re trusting each one of them to keep your credentials safe.
Moreover, we tend to reuse passwords across multiple accounts for convenience. This dramatically increases the risk of a security breach, as one compromised account can lead to the compromission of others.
So, how do these breaches happen?
Hackers have a lot of tricks up their sleeves. Aside from phishing, they can perform brute force attacks, systematically trying all possible password combinations until they find the right one.
Or, they can exploit existing security vulnerabilities in software to gain unauthorised access to databases, stealing the stored credentials.
When you add up all these factors, it’s easy to see how password security alone isn’t enough. For each individual in an organisation, multiply the risk by the number of accounts they have, and you’ll quickly understand the magnitude of the potential problem.
Benefits of Two-Factor Authentication
Integrating two-factor authentication can feel like a significant change, but the benefits it brings are substantial. Here’s how it can make a difference in your organisation:
1. User Convenience
Once set up, 2FA often just take an extra few seconds of your time but provides significant better protection.
2. Avoid Data Breaches
Data breaches are causing significant financial and reputational damage to organisations all over the world. With 2FA, you’re significantly reducing the chances of unauthorised access, even if the first factor (usually a password) is compromised.
This makes it a powerful tool in your cyber security arsenal.
3. Lower Maintenance Costs
Data breaches are expensive. And while setting up 2FA requires an initial time investment, it can save your IT team from the aftermath of a security breach in the long run. Fewer breaches mean less time and resources spend on recovery, incident response, and damage control.
4. Ease of Implementation and User Familiarity
Two-factor authentication is an increasingly common security measure, understood by most. As such, the learning curve for employees is minimal, making it quicker and more painless to implement. Smartphones serve as readily available security tokens, capable of generating one-time passwords or receiving secret codes via SMS.
Furthermore, plenty of modern devices are equipped with biometric features like fingerprint and facial scanners for a more user friendly 2FA process.
Various software offerings facilitate 2FA. However, before considering additional investments in security, check existing solutions: Microsoft Azure Active Directory Premium, Microsoft 365, and Google Workspace all offer two-factor authentication capabilities.
5. Increased Protection Against Dark Web Activities
The dark web has increased the potential damage of compromised passwords. Today, stolen credentials are commodities traded in bulk, enabling a symbiotic relationship between different types of cyber criminals: some focus on stealing passwords, others specialise in turning these stolen credentials into profit.
In this context, it’s wise to operate under the assumption that passwords can and will be compromised – if not from your database, then potentially from other sources. It’s a harsh reality of today’s digital world.
However, there’s no need to panic. This is precisely why measures like 2FA exist. Even if passwords are compromised, the second user authentication factor isn’t.
6. Alerts to Potential Compromises
2FA also serves as an early warning system.
If an employee suddenly starts receiving security codes for uninitiated login attempts, it’s a strong indication that their password might have been compromised. This can prompt a review of your cyber security practices and an immediate password change.

Ideally, your endpoint management system software should track login events to facilitate further investigation into any suspicious activities. It’s also advisable to have a strategy in place that outlines steps to identify the source of a potential leak following such an alert.
One recommended measure is to generate a strong password on behalf of the employee, which they can securely note down until it’s memorised. This adds an extra layer of security by not allowing a predictable or weak password to be chosen.
Step-by-Step Guide to Introducing Two-Factor Authentication
Starting is always the hardest part. But you can successfully accomplish a successful 2FA implementation with some careful planning and execution. Here’s a roadmap you can follow:
1. Choose the Right 2FA Method
There are several 2FA methods out there. These include, SMS codes, authenticator apps, biometrics, and hardware tokens. Each has its pros and cons, so it’s essential to select one that suits your organisation’s needs and capabilities.
2. Educate Your Team
Before you start rolling out 2FA, educate your team about what it is and why it’s important. You can even copy some of the earlier sections of this article.
Clear communication will ensure that everyone is on board and understand their role in protecting the organisation’s digital assets.
3. Plan Your Rollout
Don’t rush the rollout process. Depending on the size of your organisation, you might consider implementing 2FA in phases, starting with your IT team or a small group of users. This allows you to acknowledge and address any issues before a company-wide implementation.
4. Implement 2FA
Begin the rollout process as per your plan. Depending on the method you’ve chosen, this might involve setting up an authenticator app on user’s mobile devices or distributing hardware tokens.
5. Provide Support
Ensure that you have a robust support system in place to help your team during the transition. This could be a dedicated IT support team or a designated point person in each department that has 2FA training.
6. Review and Refine
After the rollout, gather feedback from your team. Did they face any challenges? Is there anything you can improve? Use this information to refine your 2FA process and make it more effective and user-friendly.
Overcoming Resistance
Transitioning to 2FA isn’t always as easy as flipping a switch. It’s a people-centric change, and some of your team might have some reservations. So, how can you help guide them through this process smoothly?
Begin with an open forum. The change may seem significant, or even pointless for those that are less tech savvy. It’s natural for your team to have queries or concerns.
Holding a Q&A session and encouraging everyone to participate can dispel many anxieties. This session provided a platform to openly discuss how 2FA works, why it’s necessary, and what it means for everyone in the organisation.
Highlight Their Responsibility
One vital point to underline during this discussion is the importance of everyone’s role in securing the organisation. Highlight that 2FA is a team effort, not an isolated IT project. Everyone contributes to the protection of sensitive information and the overall security posture of the organisation.
Simplify The Process
When it comes to implementation, clear and straightforward instructions are crucial. Guide them through the process with simple, easy-to-follow instructions. Demystify any technological complexities and reassure them that adopting 2FA isn’t as daunting as it may seem.
However, you need to do more than just show them how it works. Demonstrate your commitment to supporting them through this change. Have a mechanism in place to offer help when needed. Knowing they have someone to run to for assistance can ease the transition.
Encourage a Culture of Awareness
Finally, foster a culture of security within the organisation. This is a shift in mindset where everyone understands the importance of security and their role in it. The introduction of 2FA is a perfect opportunity to do this.
Commend early adopters, share their success stories, and motivate others to follow suit.
Addressing Common Misconceptions
While 2FA adds a higher level of security to your accounts, some employees may have concerns or misconceptions about its use. Let’s debunk some of the common ones:
- It’s time-consuming: Yes, 2FA adds an extra step to your login process, but it’s usually a matter of seconds. The slight delay is a small price to pay for the significant increase in account security.
- It’s complex: 2FA might seem complicated, but in reality, it’s quite straightforward. Most of the time, it’s as simple as entering a verification code that’s sent to your phone or email. The process is user friendly and easily incorporated into your daily login routine.
- It’s not necessary: Some might think their accounts aren’t at risk or that a strong password is enough. However, no one is immune to cyberattacks, and even strong passwords can be hacked.
- It invades privacy: 2FA does require some personal information, like a trusted phone number or email address. However, this information is sued solely for verifications purposes and not for tracking or marketing. Remind employees of your company’s commitment to privacy and secure handling of personal data.
Using Two-Factor Authentication for High-Risk Activities
Beyond the login process, 2FA is crucial for high-risk activities within your business. These include actions such as:
- Sending funds
- Accessing sensitive resources
- Changing passwords
- Linking new accounts
- Installing software
By requiring 2FA for these activities, your business can enhance its security measures and guard against both external threats and internal risks.
Think about it: Have you ever logged in from a new device and had to enter a 2FA code? While it might be annoying, it also underscores the effectiveness of 2FA in tracking and authentication user behaviour.
In this way, two-factor authentication not only protects your business from external threats but also helps prevent opportunistic crimes and potential issues caused by disgruntled employees. It’s a multi-faceted tool for securing your business.
Conclusion
Implementing two-factor authentication doesn’t have to be a complicated process. With the right preparation, communication, and ongoing support, you can overcome resistance and foster a culture of cyber security awareness.
2FA strengthens your security and brings peace of mind to your team, clients, and partners. This level of trust is a cornerstone for any successful business. While the path to full adoption may have some challenges, the payoff in protection and peace of mind is well worth it.
Remember, cyber security is a team sport. Your dedication to implementing 2FA effectively can significantly decrease the risk of cyber threats, ensuring a safe and secure digital environment for your organisation.
