Introduction
Cybercrime in Australia is a hot topic, and for good reason. In 2022, two of Australia’s biggest businesses were victims of cyber-attacks.
Then, in 2023 we had the Latitude hack. And one thing is glaringly obvious; Australian businesses are not taking cyber security seriously.
This negligence is not just about major cyber-attacks but also extends to online fraud, which frequently targets smaller operations
Don’t be fooled by the big names in the headlines either. Cybercriminals will target small and medium businesses (SMBs) just as much as big companies.
Why?
Because often SMBs think they’re not big enough to be a target, they get complacent and invest too little in their cyber security. Sound familiar?
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
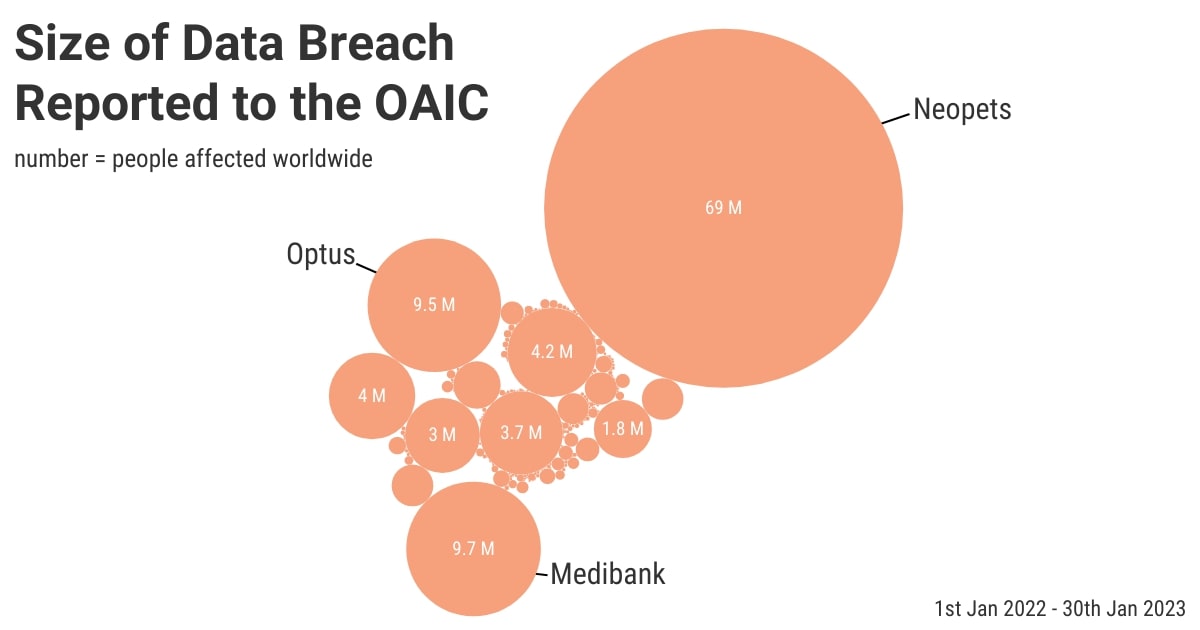
This belief that they’re not big enough to be a target is what gets many small businesses into trouble.
News stories about attacks on Optus and Medibank can lead many SMB owners to assume that all hackers are targeting big businesses. However, the same as how there are many different types and sizes of businesses, there are a massive amount of “bad actors” with varying capabilities. This leaves all businesses at risk of harm.
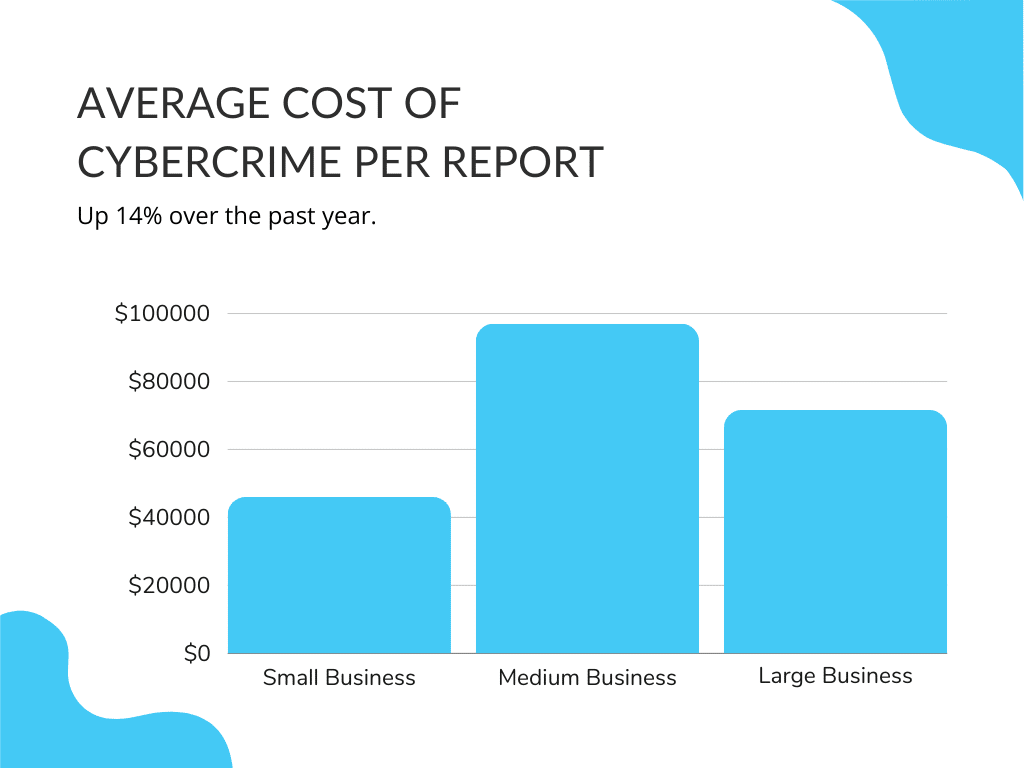
The recent surge in internet-connected devices and remote capabilities has created IT environments with multiple entry points. Of course, multiple entry points mean multiple areas for cybercriminals to exploit.
So, if you read nothing else in this article, remember; all businesses are susceptible. Always be prepared and have a plan.
Let’s take a look at current trends of cybercrime in Australia.
Cybercrime in Australia: 2024
According to the Australian Cyber Security Centre (ACSC’s) Annual Cyber Threat Report 2023 was a volatile year for cybercrime in Australia.
And 2024 is no different.
Criminal activities are creating more threats. And in many cases, threats are increasingly sophisticated and easier to replicate.
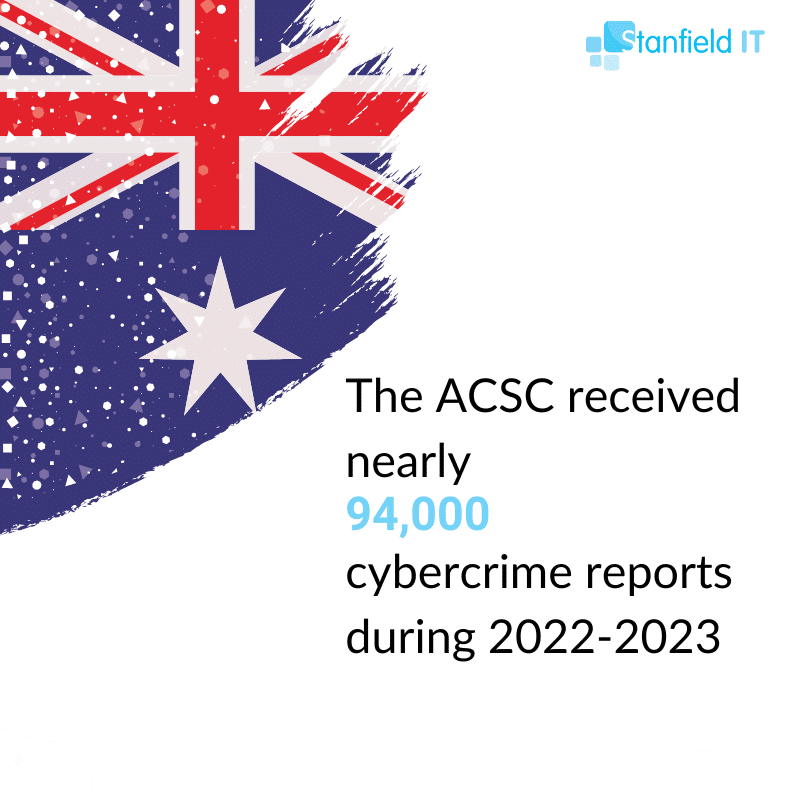
2023 saw a 23% increase in cybercrime reports, equivalent to one report every 6 minutes. It’s clear that Australia is becoming an increasingly attractive target for cybercrime.
One key factor in this rise was the number of exploitable software vulnerabilities. Bad actors routinely scan for networks that are not up-to-date. They can then use these as entry points into systems.
Healthcare was once again one of the most targeted sectors in Australia. This is consistent with previous years, as healthcare typically has a greater attack surface than other industries. Not to mention the huge amount of sensitive data and personal information shared in the system.
Why is healthcare such a high-value target?
- Healthcare data is more profitable than credit card and banking details. If your credit or banking accounts are accessed, you can quickly change them. However, you can’t change years of unique healthcare data.
- Cyberattacks might delay and disrupt critical hospital operations, putting lives in danger. As a result, hospitals may feel they have no alternative but to pay the ransom.
- Many healthcare providers use outdated technology because of the perception that upgrading will cause a major disruption of service.
What’s Driving Cybercrime in Australia?
Cybercrime-as-a-Service
A notable evolution of cybercrime in Australia is the increasing use of Cybercrime-as-a-Service (CaaS). We know what you’re thinking, what isn’t a service these days?
Basically, just as you might engage a business for marketing, financial or IT services, so too will hackers sell their capabilities using a pay-per-use service model. In many cases, the packaging and selling of tools used to commit crimes hold less risk and higher rewards than actually undertaking an attack.
Using CaaS an attacker could:
- Launch a ransomware attack.
- Send phishing emails.
- Sell access to compromised data.
- Launder stolen money.
And much more.
So what does this mean for business owners? Unfortunately, it’s not good news. Because of CaaS, the barrier to entry into the world of cybercrime is lower than ever. These tools are readily available, and as a result, cybercriminals don’t need to be experts in every part of their operation to achieve their desired results.
Using CaaS, cybercriminals can monetise their expertise, making them more specialised and harder to defeat. And as long as it pays, the CaaS marketplace will keep growing.
Business Email Compromise
Business email compromise (BEC) is a form of phishing that targets businesses in an attempt to scam them out of money or goods, pretend to be business representatives, or trick employees into revealing confidential business information.
Using BEC, criminals will send an email that, by all appearances, looks like it’s from a legitimate contact. These emails might appear to be from:
- A known vendor your company works with regularly – with a fake invoice attached.
- The CEO of a company requesting an assistant to purchase gift cards for employees.
You can probably see how such requests often go unnoticed. A slight variation in email can make all the difference. For example, john.doe@fakecompany.com vs. john.d0e@fakecompany.com could easily catch someone off guard.
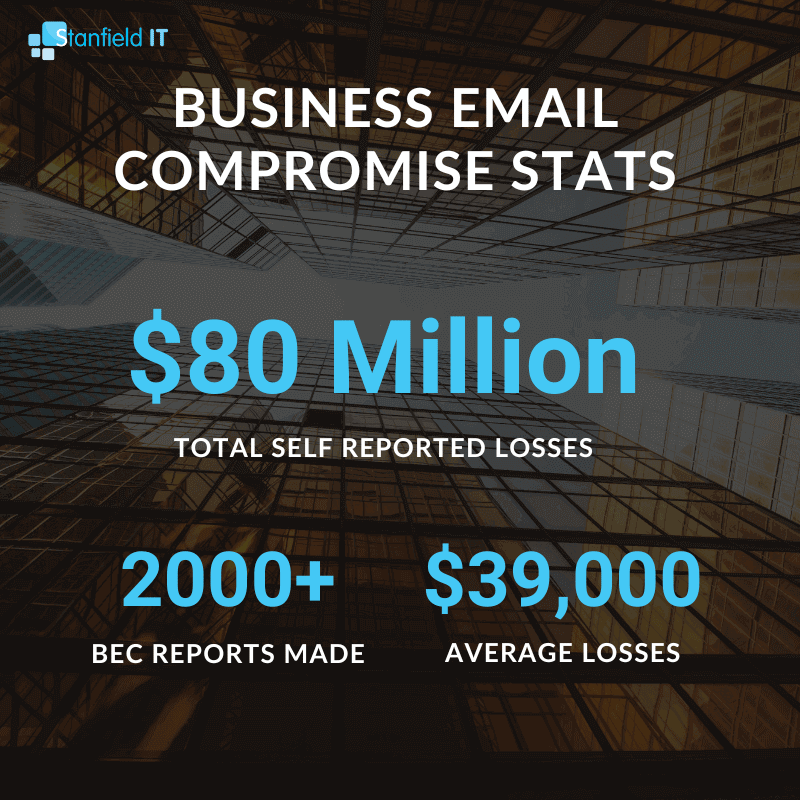
Nationally, the average loss due to BEC was just over $39,000, which is lower than previous years. However, only a small percentage of BEC financial losses are successfully recovered.
Cybercriminals Are Specialising
The threat of cybercrime has become more complex and specialised. The range of malicious actors is growing, as is their focus on Australian businesses. As digital threats have evolved, so have the tactics used by cybercriminals to target organisations across all industries.
Organised crime groups are at the forefront of many cyber attacks on Australian businesses. These groups of malicious actors include state-sponsored hackers, sophisticated organised crime syndicates, hacktivists and individual hackers looking for financial gain or recognition. Criminal groups are driven by a range of factors, from financial reward to notoriety, making them increasingly dangerous and capable of damaging Australian businesses.
Specialisation means that businesses can’t always rely on their traditional anti-malware defences either. Modern-day threats require additional levels of security including application security monitoring and access controls designed to detect suspicious behaviour early enough before significant damage is done to corporate systems or reputation. Cybercriminals now also use new technologies such as AI to analyse networks more effectively – allowing them to automate processes and identify vulnerabilities much faster than ever before.
Australian businesses must be aware of the threat posed by specialised cybercriminals, who employ unique tactics in order to achieve their goals more easily. As organisations look for ways to protect themselves from cybercrime groups, it’s important for business leaders to understand that vigilance must remain a top priority when dealing with any form of digital security threat.
Secure Your Business Today with Our Expert Cyber Security Solutions
Cyber Security Assessment – Schedule a call to identify vulnerabilities and protect your business from cyber threats.
Custom Security Strategy – Our team will develop a tailored plan to safeguard your digital assets and ensure business continuity.
Proactive Monitoring & Incident Response – Benefit from ongoing protection and rapid response to any security incidents.
Ransomware
The list of the types of cyber-attack that you could face in the business world is always increasing. However, ransomware attacks on Australian businesses recently made headlines, so we’ll focus on them.
What is Ransomware?
Ransomware is a form of malware designed to deny business users access to company files. Once these files are encrypted, the attacker will demand a payment to restore access to the files.
There are a few common steps seen in ransomware attacks.
1. Infection
Ransomware can infect a computer using a number of methods. However, one method is to gain access to computers through phishing campaigns – dodgy email attachments that look safe. These attachments are downloaded, opened, and then easily spread through the victim’s computer.
2. Encryption
After successful implementation, the malware searches for and encrypts valuable files including:
- Documents
- Pictures
- Videos
In some instances, the ransomware will block basic computer functions, in others, it won’t. It depends on the type of ransomware that has been deployed.
Some forms of ransomware will also attempt to delete backups and other copies of files to make recovery without the decryption key harder.
3. Ransom Demand
In the end, the goal of all ransomware is the same; to demand payment for the decryption of files.
Commonly, your device will display a ransom note in the background. Alternatively, the note will appear when you try to access the encrypted files.
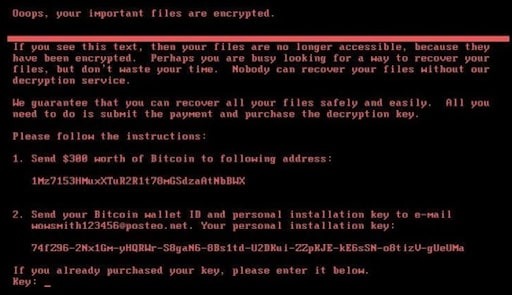
A typical ransom note will demand a cryptocurrency payment in order to reaccess the encrypted files. Once payment is made, the attacker will run a decrypter program to reverse the encryption and restore access to the business’s files.
It’s worth noting that only 4% of companies that pay ransoms get all of their data back.
Ransomware Attack: What To Do
Ransomware can be one of the most expensive types of cybercrime in Australia to resolve. Financial impacts will vary depending on each business, but will often include:
- Loss of productivity due to downtime
- Time and money spent rebuilding systems
- Costs linked to reputational damage
Because of this, it can be tempting to simply pay the ransom, recover your data, and continue business as usual. Unfortunately, it’s not that straightforward.
Important
The ACSC advises against paying a ransom. Payment does not guarantee all of your will be restored or kept private. Paying a ransom will only increase the likelihood that further ransomware attacks will occur, putting other Australian businesses at risk.
The ACSC has a helpful guide on what to do if you’re held ransom. But we’ll summarise the first few steps below.
Step 1: Record All Important Details
Anything and everything you record during a ransomware attack could be valuable. Important details you should try and take note of include:
- If the affected files have a new extension
- The name of any new extensions you see
- The ransom note
- Any changes that occur during the attack
Try to take photos of everything you can as it may be of use later on.
Step 2: Turn Off The Infected Devices
Turn off the infected device once you’ve recorded details about the attack. Hold down the power button, or unplug the device from the wall socket. Don’t skip this step, as it might stop the ransomware from spreading to other devices.
Step 3: Disconnect Any Other Devices
Don’t let ransomware spread throughout your network. Turn off all devices, starting with those that are most important.
Step 4: Change Your Important Passwords
It’s difficult to know what information ransomware has accessed, and which it hasn’t. Because of this, you should change your passwords as a precaution, starting with those that are most important.
Remember to use a strong password. You may also want to consider using a password manager.
Finally, you can report the incident at ReportCyber.
Case Study: Medibank
One of the most prominent examples of cybercrime in Australia is the Medibank data breach.
Medibank is one of the leading private health insurers in Australia.
In October 2022, Medibank detected unusual activity on its network. Early reports indicated that the company had successfully contained the event and that no sensitive data had been accessed.
Medibank later announced that hackers had made contact with the company. They claimed to have stolen 200 gigabytes of customer data and provided samples of customer details as evidence, including:
- Names
- Addresses
- Dates of birth
- Phone numbers
- Medical claims regarding personal diagnosis and procedures
Eventually, it became clear that the attacker had access to all Medibank customer’s personal data and significant amounts of health claims data.
This included the name, date of birth, address, phone number and email address of approximately 9.7 million current and former Medibank customers.
For some customers, the attacker also gained access to:
- Medicare numbers
- Passport numbers
- Health claims data
Medibank ultimately declared that it will not pay the ransom for the return of its customer data.
As a result, the attacker followed through on threats to publish some of the data on the dark web.
At the time of publishing this article, it’s not entirely clear how the hackers initially gained access to Medibank’s system. However, it appears that they used compromised login credentials.
How To Protect Your Business From Cybercrime
Protecting your business from cybercrime in Australia is no different to any other part of the world. Australian businesses are just as exposed to an attack as global corporations and must take the same preventive measures.
Training and Awareness
Humans are often considered to be the weakest link in a business’s cybersecurity. So, business owners need to take this into account and take action to raise cyber security awareness and implement routine cyber security training.
Increasing cyber security awareness allows your team to identify and understand the many types of cyber threats your business faces. Doing so could mean the difference between quickly shutting down your systems after identifying unusual activity or letting an attack proceed unnoticed.

Developing cyber security awareness allows you to assess and identify employee gaps in knowledge. From there, you’re able to offer effective training that targets areas of weakness that need to be addressed.
Effective cyber security training is:
- Relevant
- Regular
- Positive
While promoting cyber security awareness and training is not going to guarantee a stronger cyber security environment, it’s far better than not doing it. By offering frequent, relevant and effective training you’re putting your business in a stronger position to defend against cybercrime.
Implement the Essential Eight
The Essential Eight is one of the easiest and most cost-effective ways to protect your business from cybercrime. The Essential Eight are mitigation strategies developed by the ACSC with the objective of:
- Preventing attacks
- Limiting the impact of attacks
- Recovering data following an attack
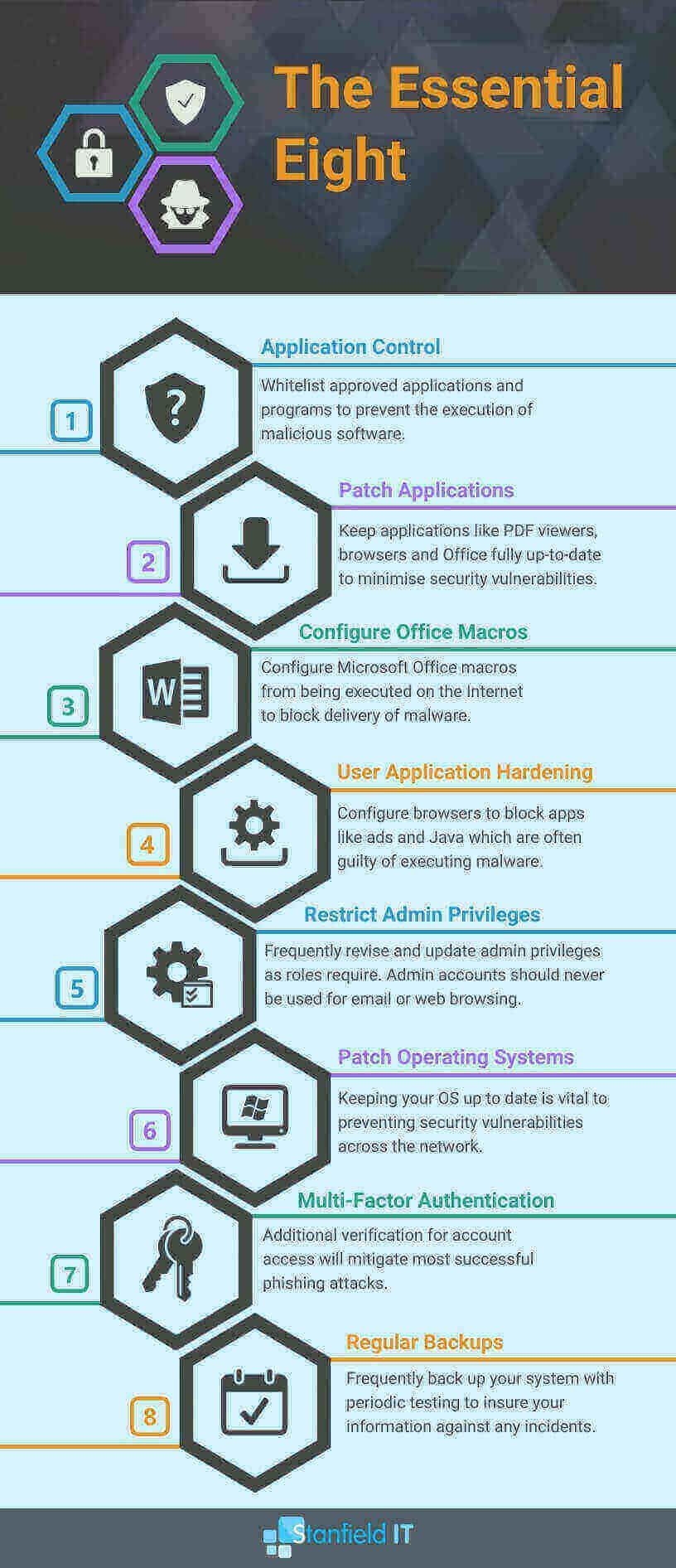
You should consider these strategies as the minimum defence measures your business uses to protect against cybercrime.
Now let’s look at a few of the most effective cyber security solutions from the Essential Eight that you can implement today to protect your business.
Patch Management
Patch management incorporates operating systems and applications. Simply put, it’s the process of applying updates to the software in your system.
As software ages, it’s not uncommon for security flaws to become apparent. Cybercriminals love to exploit these vulnerabilities, using them to access your system.
To counter this, software developers release patch updates that essentially “patch up” known security flaws.
Sounds simple enough.
But there is a problem. One we see far too often. People don’t apply patches when prompted.
That’s a real spanner in the works for patch management. The simple fact is that a patch cannot resolve security vulnerabilities if you don’t install the update containing the patch.
Until you do, that flaw remains wide open and exploitable.
Now let’s say you haven’t installed an update in the past year. There’s a security flaw exposed for every patch you miss. That’s potentially dozens of security flaws making your systems and applications vulnerable to a cyber attack. By neglecting patches you create ample opportunity for cybercriminals to take advantage of your understrength network.
So remember, install patches to your applications and operating systems whenever they become available. In doing so, you’ll create an IT environment with stronger security, better efficiency, and with reduced vulnerabilities.
Multi-Factor Authentication
Multi-Factor Authentication (MFA) requires two or more methods of identification to give you access.
When you sign into an account you go through an authentication process in order to prove you are who you claim to be. The typical authentication process we’re all used to is typing in a username and a password. However, these days that’s not considered to be very safe. Emails, one of the most common usernames, are easy to find. And often passwords are weak, can be guessed, or are used for multiple accounts.
MFA is a better alternative and one we recommend you implement today.
MFA still uses usernames and passwords during the authentication process. However, at least one other method of authentication, or “factor”, is required.
Typically the factors included are:
- Something you know – e.g. password or PIN.
- Something you have – e.g. mobile phone or keyfob.
- Something you are – e.g. fingerprint or facial recognition.
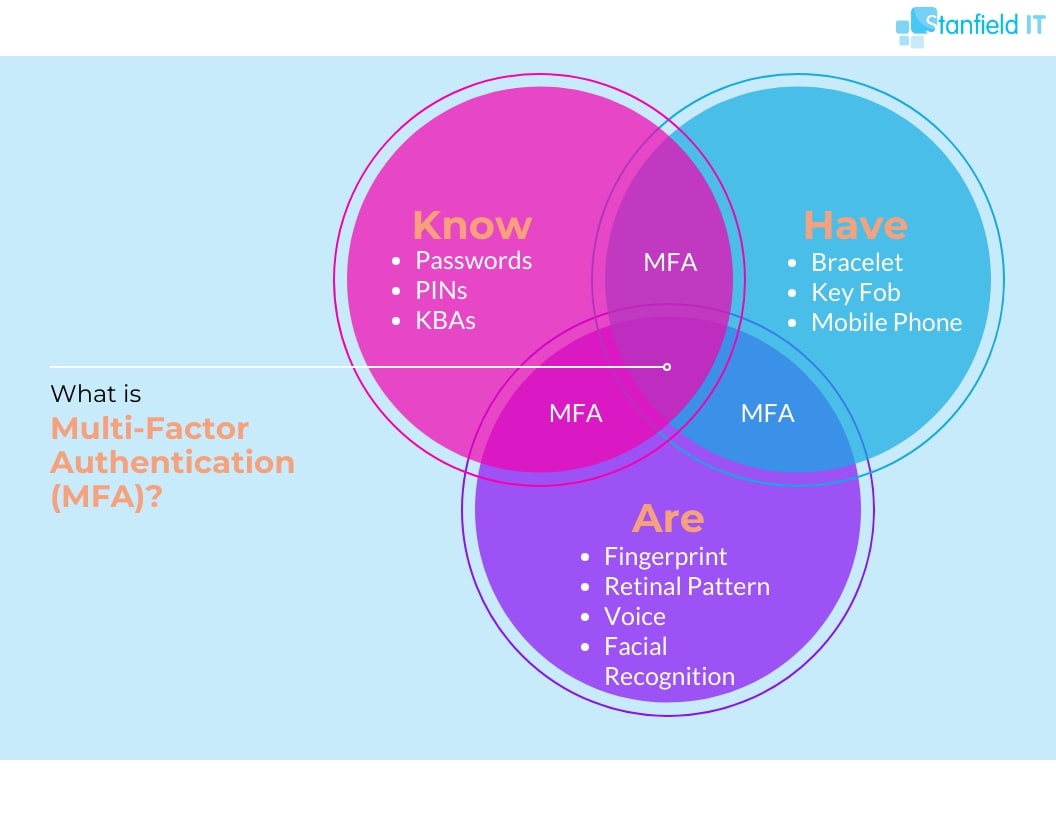
Enabling MFA for your work accounts is a quick and easy way to keep your business data safe. Let’s say a hacker has acquired your username and password. However, you’re using the Google Authenticator app as your second factor. If they don’t have access to your mobile phone, they’re unable to enter the 6-digit code, and your account is kept safe.
While some people worry that MFA is an inconvenience in our time-optimised society, it adds an extra layer of security that makes it hard to ignore.
Looking Ahead: The 2023-2030 Australian Cyber Security Strategy
The 2023-2030 Australian Cyber Security Strategy is a framework for businesses aiming to enhance their cyber security.
Key Takeaways for Business Owners
- Empowerment and Responsibility: Businesses are encouraged to proactively strengthen their cyber defences and cultivate a cyber-aware culture among employees and customers.
- Investment in Safe Technology: The Strategy urges businesses to invest in secure technologies, safeguarding their digital assets.
- Collaboration for Threat Intelligence: It emphasizes collaboration between industries and the government for sharing real-time threat information, vital for timely and effective responses to cyber threats.
- Focus on Critical Infrastructure: Businesses in critical infrastructure sectors are given specific guidelines to enhance their cyber resilience.
- Development of Local Cyber Solutions: The Strategy supports the development of Australian cyber security solutions, reducing reliance on foreign technology and bolstering local capabilities.
- Engagement in Legislative Reforms: Businesses are invited to contribute to cyber security legislative reforms, acknowledging their role in shaping the nation’s cyber security landscape.
Australia’s Cyber Security Strategy is not just an Australian government initiative but a call to action for businesses to actively participate in and contribute to Australia’s cyber security. It’s an opportunity for business owners to align with national efforts and elevate their cyber security measures, playing a critical role in securing Australia’s digital future.
Conclusion
Australian business owners must stay informed about current cybercrime trends in Australia.
Businesses are becoming more appealing targets for cyber criminals and cybercriminal groups due to extensive connectivity and prosperity.
Maintaining an up-to-date understanding of these trends and implementing a robust cyber security strategy, including the recommended security measures, will enhance the cyber security posture of your business.
Developing and regularly updating a comprehensive cyber security strategy is key to safeguarding against evolving threats.
More Security Insights
Windows 10 End of Life (EOL) and What it Means
Microsoft has announced that October 14, 2025, will be the End of Life (EOL) date for Windows 10. Windows 10 EOL is set to affect all versions of Windows 10, including Home, Pro, Education, and Enterprise. Research from Lansweeper indicates that only 23.1% of...
ISO 27001 Certification in Australia: A Comprehensive Guide
Business data is like a treasure for cyber criminals. In fact, buried in almost every organisation's information assets are details worthy of holding ransom. So, how do you protect it? With ISO 27001 certification. ISO 270001 is more than just a standard industry...
Cyber Hygiene For Business: What You Need To Know
Implementing cyber hygiene practices is one of the most effective ways to protect your business from cybersecurity risks. As a business owner, the security of your company's data is paramount. With the prevalence of cyber-attacks in the modern world, it’s increasingly...



