Introduction
If you haven’t implemented the ACSC’s Essential Eight, then it’s time to start paying attention.
That’s because the Essential Eight is one of the easiest ways you can protect your organisation from adversaries. And with the sharp rise in cybercrime affecting Australian organisations, who wouldn’t want more protection?
Of course, while no single measure alone will be enough to prevent a cyber attack, the Essential Eight offers a baseline strategy that will make your organisation’s network harder to hack. Implementing a robust cybersecurity framework is crucial in today’s digital landscape to protect against evolving threats and ensure the security of sensitive data.
Read on to better understand the Essential Eight and how its strategies, including essential mitigation strategies, can help protect your organisation from a cyber attack.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
What is the Essential Eight?
The Essential Eight is a series of mitigation strategies designed to protect Australian businesses from a range of cyber threats. Developed by the Australian Cyber Security Centre (ACSC) in 2017, the Essential Eight aim to protect Microsoft Windows-based internet networks in Australia.
Abiding by the Essential Eight can be a worthwhile investment. After all, implementing the Essential Eight can often be more cost-efficient than responding to a cyber security incident after it has occurred.
The strategies included in the Essential Eight are:
Application control is a security practice that restricts unauthorised applications from executing in ways that put data at risk. It involves the use of policies that allow only approved programs to run.
Example: A company using application control will have a whitelist of approved software. If an employee tries to install a non-approved application, the system will block it from running, preventing potential malware or security threats.
Patching applications refers to the process of updating software applications to fix security vulnerabilities. Keeping applications updated ensures they are protected against the latest known threats and ism.
Example: Regularly updating your email client or web browser to the latest version is a simple way to maintain security.
Configure Microsoft Office Macro Settings
This strategy involves disabling macros from Office files received from the internet. Macros can be used maliciously to install malware, so this step is essential in preventing such attacks.
Example: An organisation might set up its email system to disable macros in all incoming office files, protecting against phishing attacks.
This means configuring web browsers and other applications to block untrusted content like Flash, advertisements, and Java. This reduces the attack surface of the system.
Example: When Flash was still supported by Adobe, companies would often disable Flash in their web browsers, as Flash was often exploited by cybercriminals.
This strategy involves limiting administrative privileges to only those that truly need them. This minimises potential damage if an account is compromised.
Example: In a small business, only the owner and IT manager might have admin rights, while other employees have standard accounts.
Just like patching applications, this involves keeping your operating system updated to fix security issues and improve functionality.
Multi-Factor Authentication (MFA) is a method of verifying a user’s identity by requiring two or more pieces of evidence (or factors). This adds an extra layer of security by making it harder for attackers to gain access.
Regular backups involve keeping copies of your data in a separate, secure location. This is crucial for recovering from issues like ransomware incidents or hardware failures.
Example: A business might back up its data nightly to both an external drive and a cloud-based backup service for redundancy.
By understanding and applying these strategies, businesses can significantly enhance their cyber resilience. We’ll explore each of these strategies in greater detail in the sections that follow, providing you with practical insights and a roadmap for implementation.
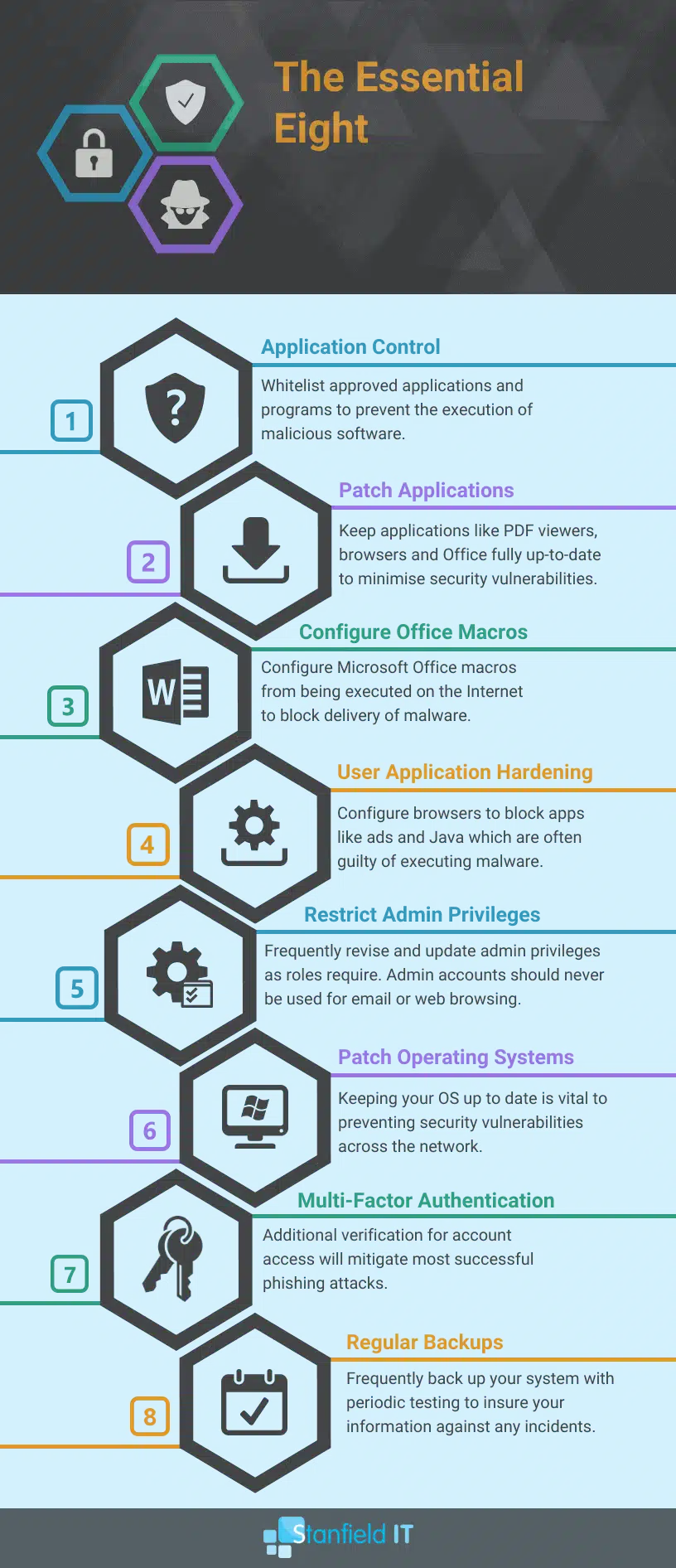
Objectives Of The Essential Eight
The Essential Eight strategies are then broken into three different objectives:
- Prevent Attacks
- Limit Attack Impact
- Recover Data & Data Availability
It looks a little something like this.
The Essential Eight Maturity Model
Finally, we have the Essential Eight Maturity Model (E8MM).
The maturity levels are target tiers for organisations to aim at for each strategy. They range from Maturity Level 0 to Maturity Level 4.
The idea behind these four levels is that as an organisation grows, its defences will improve. However, the capabilities, methods, and technologies of criminals trying to hack their data will also improve. So, each level escalates protections to appropriately handle the growing threats.
You can find a more in-depth article on the E8MM here.
Maturity Level 0
This is the weakest maturity level of the Essential Eight and indicates that the organisation’s cyber security posture is poor. If an attack was to occur, then it is likely that security vulnerabilities would be easily exploited. Consequently, this could result in a significant data breach.
Maturity Level 1: Basic Security Controls
This maturity level focuses on preventing attacks from cyber criminals who use simple technologies to try and gain access and/or control of your system. At this level, cyber criminals will tend to exploit publicly known vulnerabilities that have not yet received a patch. Alternatively, they will simply access a system using stolen or guessed information.
In these cases, most criminals are looking to exploit any organisation with vulnerabilities, rather than a specific target.
Maturity Level 2: Advanced Security Controls
Maturity Level 2 of the Essential Eight sees a significant increase in a hacker’s capabilities. At this level, we start to see planned and targeted attacks.
Criminals will use well-known technologies and methods to bypass security controls. This can include techniques such as phishing and social engineering. While these attacks are more targeted, criminals are unlikely to invest a lot of time trying to access a system. Instead, they will attempt to target users with special privileges in order to get the most bang for their buck.
Maturity Level 3: Expert-Level Security Controls
Lastly, Maturity Level 3 focuses on defending against highly skilled hackers who are less dependent on open-source technologies and methods. Instead, they are capable of exploiting gaps in their target’s cyber security posture, such as those created by outdated software.
In most cases, hackers tend to be more narrowly focused on specific targets. They are also willing to invest significant time and effort to get around their target organisation’s specific policies and security controls.
Once they’ve accessed the system, hackers will attempt to access privileged credentials and passwords before moving on to other areas of the network and covering their tracks.
Note
The Essential Eight strategies support one another and provide cover for a range of cyber threats. Therefore, we recommend that your organisation focuses on achieving the same maturity level for each strategy before targeting higher levels. I.e. Don’t focus on getting strategies to Level 3 one at a time. Instead, increase maturity levels at the same time.
The Essential Eight Strategies
Application Control
There are new malicious files created every day, and older methods of protection no longer provide adequate protection by themselves.
Enter the first Essential Eight control – application control. Application control is a security method designed to prevent malware from entering a computer network. It works by restricting which applications users can access in the first place. Application control technology will recognise files considered to be safe (whitelisted) and allow them to pass through your network. It’s as simple as that. Subsequently, you select which applications you trust and grant them access. As a result, it will prevent everything else from accessing your network.
In the past, blacklisting has been the primary method of application control. This is where files considered to be suspicious are blocked. However, the default of blacklisting is to allow access unless told otherwise, which is now considered to create a less secure network.
Whitelisting, on the other hand, will always deny access unless told otherwise. So, it’s pretty clear which is the safer of the two.
Benefits of Application Control
- Automatically identify trusted software that has been authorised to access your network.
- Identify and control which applications are active in your network.
- Prevent unauthorised applications from activating – regardless of if they are malicious, suspicious or unwanted.
How to Implement Application Control
You can implement application control by taking the following steps:
- Identify any approved applications.
- Create application control regulations so that only approved applications can run.
- Maintain application control rules by using a change management program.
- Assess application control rules at least once per year.
Patch Applications
Applying patches to applications is a critical Essential Eight strategy.
Whenever you don’t update old applications, you create vulnerabilities in your network. These vulnerabilities expose you to dangerous files which can lead to a data leak. This is because hackers thrive off known vulnerabilities. They are essentially weak spots in your cyber security network that, when discovered, create easy opportunities for hacking.
This is why patching applications is so important. So, we encourage you to install a new patch as soon as it’s released. No more clicking “Remind Me Later”.
Benefits of Patching Applications
- Stronger security: Fix vulnerabilities in your network leading to better overall security.
- Better efficiency: Applications and operating systems will run more smoothly when up to date.
- Minimise vulnerability: Up-to-date applications and operating systems will decrease the amount of time you are exposed.
Recommendations For Patching Applications
Here are a few recommendations from the ACSC regarding patching applications.
- For basic cyber threats:
- Internet-facing services: Within two weeks; or 48 hours if an exploit exists.
- Commonly-targeted apps: Within one month.
- For moderate cyber threats:
- Internet-facing services: Within two weeks; or within 48 hours if an exploit exists.
- Commonly-targeted apps: Within two weeks.
- Other apps: Within one month.
- For advanced cyber threats:
- Internet-facing services: Within two weeks; or within 48 hours if an exploit exists.
- Commonly-targeted apps: Within two weeks; or within 48 hours if an exploit exists.
- Other apps: Within one month.
Configure Microsoft Office Macro Settings
Microsoft Office macros are time savers and can help you automate certain tasks in the Microsoft Suite. Unfortunately, they can also contain dangerous codes that give hackers access to an organisation’s sensitive information. That’s why configuring macros is such an important part of the essential eight.
How? Macros are written in a programming language called VBA (Visual Basic for Applications). Hackers are able to embed malicious scripts into the macros, which can harm your system. Macros are often used in programs such as Excel and Word. Because of this, they can spread quickly, as these documents are shared throughout an organisation.
Recommendations For Protecting Your Organisation From Macros
Below are some recommendations for securing macros in your organisation.
- Disable macros for users that don’t need them. If users don’t need macros to perform their work tasks, then macros should be disabled.
- Only use macros from trusted locations. If your organisation needs to use macros, you should only allow macros from trusted locations. Trusted locations are a feature of Microsoft Office where files from certain folders are assumed to be safe. Furthermore, only specific applications that are required to use macros should have them enabled. All other applications should have macro support disabled.
- Only use macros from trusted publishers. If your organisation needs to use macros, you should only allow macros signed by trusted publishers. As above, you should only enable macros specifically for applications that require them.
- Delete emails from unknown people, or with suspicious content. Never open a suspicious email or an email from someone you do not recognise. If you’ve accidentally opened a suspicious email DO NOT click on any attachments and promptly delete the email.
User Application Hardening
Application hardening determines what applications are able to do when they are running. In this sense, it is similar to application control. However, the focus is on the actions applications can take, rather than whether or not they are able to run.
For example, application hardening will restrict Java from running on its own accord and thus making your system more vulnerable.
Application hardening will reduce the attack surface of your system, giving hackers fewer opportunities to deploy malicious software onto user workstations.
Recommendations For User Application Hardening
- Configure web browser to block ads and java on the internet.
- Disable Microsoft Office features that aren’t used.
- Disable web browsers and PDF viewers.
In doing so, you are helping prevent malware from being downloaded and introduced to your system. Additionally, you are reducing the software attackers can utilise to attack your network.
Restrict Admin Privileges
Restricting admin privileges is one of the most effective ways to limit the impact of a cyber event. Because of this, restricting admin privileges is one of the most important Essential Eight strategies.
What are admin privileges?
Administrators are users authorised to access system and security functions that normal users are unable to use. Someone logged into an account with admin privileges can do a lot of things on a computer. Administrators can:
- View any file on the system.
- Undertake account maintenance.
- Change system-wide settings.
- Install new programs.
- Change the username and password of other users.
- Bypass security settings.
- Access sensitive information.
As you can see, accounts with admin privileges have a lot of power.
Why should you restrict admin privileges?
Admin accounts are able to make significant changes to operating systems and applications. Because of this, hackers often attempt to use malware to exploit admin privileges.
By restricting admin privileges you are minimizing the impact a hacker may have if they successfully access an admin account. Restricted admin privileges make it harder for a hacker to:
- Hide their existence.
- Spread to other hosts.
- Elevate their privileges (once in the system).
- Obtain sensitive information.
Restricting admin privileges can create a safer and more stable network.
How to restrict admin privileges?
Here’s a rundown on how to restrict admin privileges:
- Identify tasks using admin privileges that are essential to your organisation’s operation.
- Confirm who in your team has authorisation and a requirement to perform those tasks.
- Create separate admin accounts for each team member. Ensure that each account has the minimum privileges required in order for that team member to successfully perform their tasks.
- Re-evaluate who has admin privileges frequently, including when team members change duties or leave their role.
Patch Operating Systems
Keeping your operating system up to date is a vital Essential Eight control to prevent security vulnerabilities in your network.
If you have an outdated operating system, then you are at risk of being exploited by hackers. How? Similar to applications, operating systems will often have known vulnerabilities. And it doesn’t take long for hackers to take advantage of these vulnerabilities. So, similar to patching applications, you are limiting the number of vulnerabilities that hackers can exploit by patching operating systems.
Patching operating systems is one of the easiest security measures you can take. When a new patch is ready, you will usually receive a notification to install it. Our advice: install patches early, and install them often.
Benefits of Patching Operating Systems
- Fix security vulnerabilities
- Address bugs and flaws
- Improve operating system stability
Recommendations For Patching Operating Systems
- For basic cyber threats:
- Internet-facing services: Within two weeks, or within 48 hours if an exploit exists.
- Workstations, servers, network devices and other network-connected devices: Within one month.
- For moderate cyber threats:
- Internet-facing services: Within two weeks, or within 48 hours if an exploit exists.
- Workstations, servers, network devices and other network-connected devices: within two weeks.
- For advanced cyber threats:
- Internet-facing services: within two weeks, or within 48 hours if an exploit exists.
- Workstations, servers, network devices and other network-connected devices: within two weeks, or within 48 hours if an exploit exists.
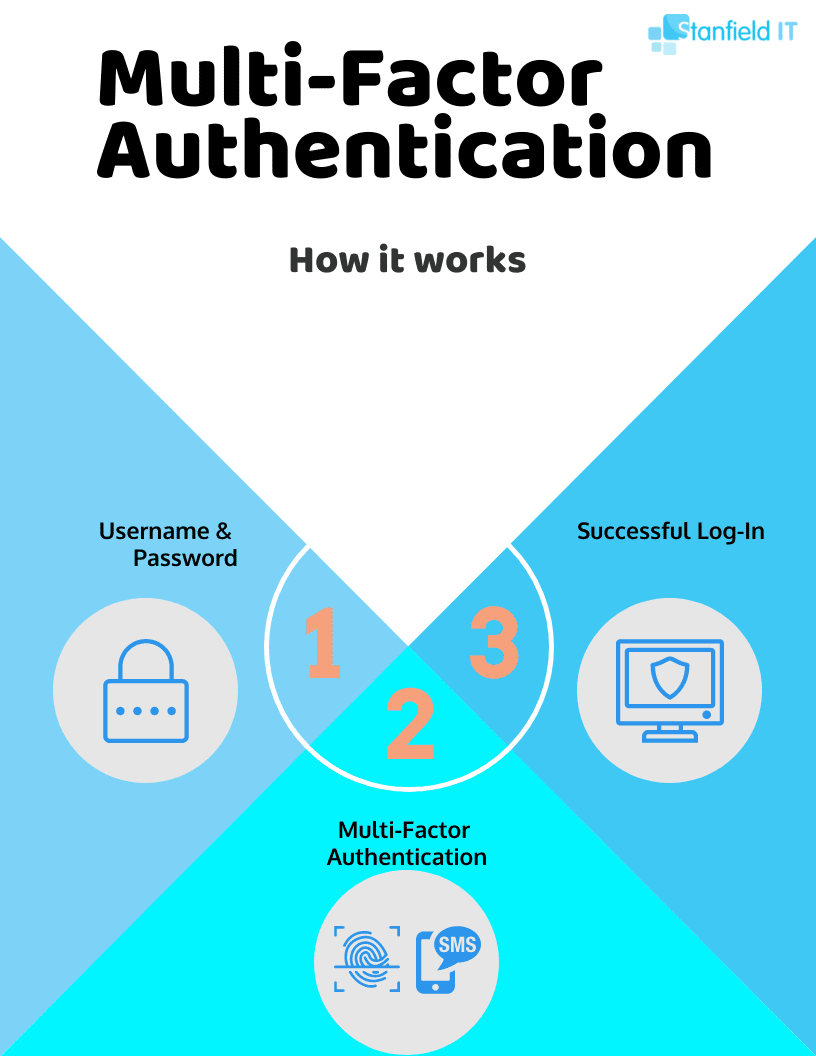
Multi-Factor Authentication
Multi-Factor Authentication (MFA) is a security measure that requires users to provide two or more means of verification in order to access a system or application. Where traditional access requirements included simply a username and password, MFA requires at least one more verification item, decreasing the risk of a cyber attack.
One of the most common MFA requirements is a one-time password. These can generate via SMS or with apps such as Google Authenticator. Each password will generate for a short period of time, making it harder for hackers to guess passwords.
MFA technology will usually require credentials including:
- Something you know: Such as a password or PIN.
- Something you have: Such as a one-time password.
- Something you are: Such as a fingerprint.
In doing so, MFA creates an added layer of security, which makes it harder for hackers to log in pretending to be you.
Benefits of Multi-Factor Authentication
- Added layer of security: MFA creates an extra layer of security for your systems, devices and applications.
- Easy implementation: MFA is generally easy to set up and can be ready to use in minutes.
- Protect remote workers: Finally, MFA can help protect remote workers that are increasingly becoming cyber security targets.
Regular Backups
Lastly, we have regular backups. Conducting regular backups is one of the best ways to protect your organisation if a cyber attack occurs. Regular backups sit under the ‘data recovery and data availability’ objective of the Essential Eight.
You can lose critical data in a number of ways:
- Server crashes
- Lost devices
- File deletion
Similarly, cyber attacks such as ransomware attacks often result in the loss of critical business data. Because of this, it’s extremely important that you back up your organisation’s data.
What is a backup?
A backup is a digital copy of your organisation’s most important data. This includes files such as:
- Organisation personnel records: This can include tax and payroll records.
- Admin documents: Such as sales and marketing information, business plans, and insurance policies.
- Financial data: Revenue records, inventory lists, and bank statements.
- Sensitive information: This is can include credit card information and personally identifiable information.
Having a backup of this information means you can restore important files if something was to go wrong.
Here’s a handy guide on how to set up automatic backups.
Conclusion
The world of cyber security is getting more and more challenging. In order to protect your organisation, you may want to consider implementing the Essential Eight. While no strategy will guarantee that a cyber attack will not occur, we believe that the Essential Eight is a great way to cover your bases.
By following best practices such as the Essential Eight, you can decrease the chances of your organisation being harmed by a cyber security attack.
If your organisation hasn’t implemented the Essential Eight then contact us for a free 30-minute consultation.