If you’re a business owner or IT professional you’re probably familiar with the challenge of securing data and infrastructure.
One of the most effective frameworks designed to address these challenges is the Essential Eight Maturity Model. It comprises four distinct levels, from Maturity Level Zero to Level Three.
This model provided a structured approach to evaluating, implementing, and improving cyber security measures.
The objective of this guide is to demystify the Essential Eight Maturity Levels. We’ll take a look at what each level looks like, its benefits and challenges, and provide actionable insights on how you can progress through each level.
So, whether you’re a business owner hoping to improve your defences or an IT professional wanting a deeper understanding of this framework, this article has the answers you need.
Let’s get started.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
Section 1: What Are the Essential Eight Maturity Levels?
The Essential Eight Maturity Model (E8MM) is a benchmark for your organisation to gauge the effectiveness of its cyber security measures.
The model was first coined by the Australian Cyber Security Centre (ACSC). It outlines a hierarchy of security strategies designed to reduce the most widespread and damaging cyber threats.
The benefits of following this structured approach include the ability to:
-
- Defend against a wide range of attacks.
- Develop a roadmap for continual cyber security improvement.
Importance of Cyber Security
The E8MM is more than just a checklist; it’s a strategic guide to help you build stronger cyber security.
The framework emphasises essential controls that work in harmony to give you a multi-layered defence strategy.
By implementing these controls, you can help protect your business assets, maintain customer trust, and ensure your business operations remain uninterrupted.
Cyber threats are now a matter of “when”, not “if”. So, the importance of adhering to a well thought out model like the Essential Eight cannot be overstated.
The model is particularly beneficial for organisations that handle sensitive information, need to comply with industry regulations or aim to develop a proactive cyber security strategy.
By adhering to the framework, companies mitigate risks and lay the foundation for a resilient cyber posture that adapts to evolving threats.
For a full guide on the Essential Eight, check out our article here.
Section 2: Understanding the Maturity Levels
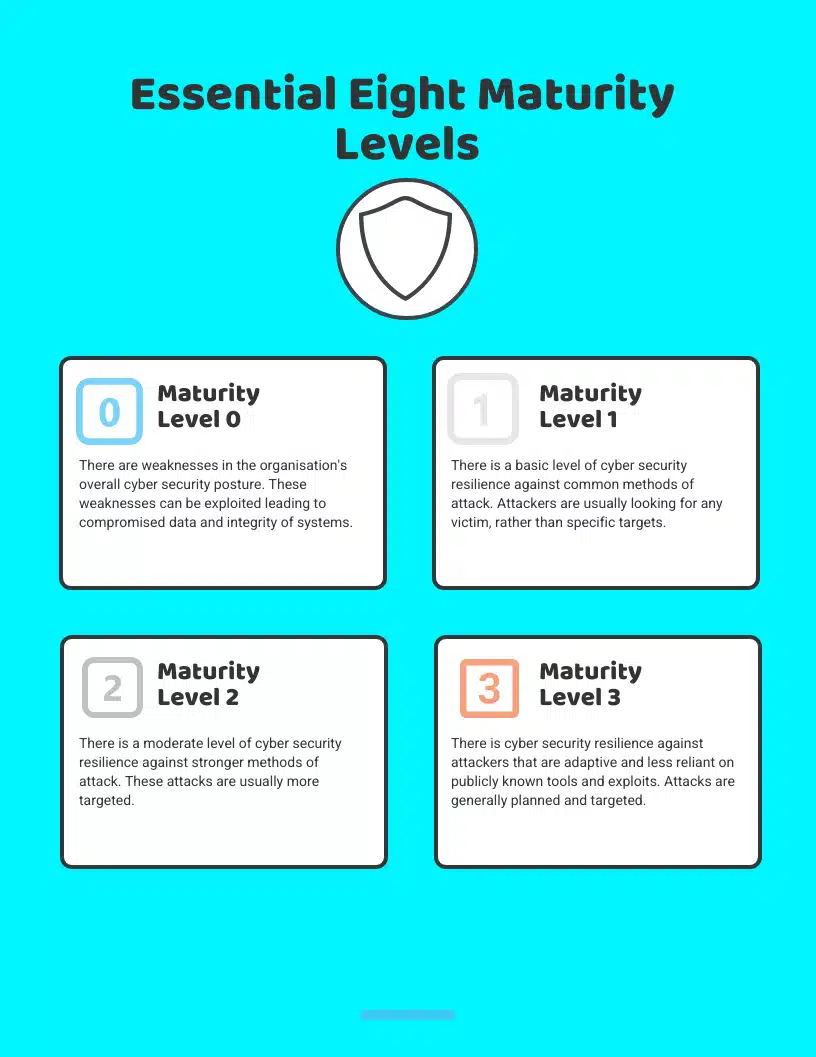
Maturity Level 0: Unmanaged
Put simply, the cyber security of an organisation at Maturity Level 0 is unmanaged, unplanned and informal.
At this level, there is usually no structured approach to cyber security. This often results in vulnerabilities that are easily exploited by attackers.
Explanation
In this stage, cyber security measures are usually implemented on an ad-hoc basis with little to no documentation. There may be some basic security tools in place. Antivirus and software, for example. However, these are not part of an organised strategy.
The takeaway here is that without a formal framework, the organisation is at high risk for cyber incidents, data breaches, and other security compromises.
Benefits
Truthfully, there are limited benefits to being at Maturity Level Zero. However, smaller businesses and startups often find themselves here due to limited resources or a lack of awareness.
For us, the only “benefit” of this maturity level is that it serves as a starting point from which to improve.
Challenges
There are a number of challenges at this level.
Organisations face a heightened risk of cyber attacks, data loss, and compliance violations. The absence of a formal process means there is no effective way to assess or improve the security posture.
So, you end up with a reactive approach. This is not only risky but can also result in higher costs in the long term due to potential breaches and legal repercussions.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
Maturity Level 1: Ad hoc
Maturity Level One represents a basic level of cyber security. While there are some measures in place, they are sporadic and not systematically managed.
Explanation
At this level, organisations have taken some vital initial steps towards cyber security. There are basic tools in use, such as firewalls and antivirus, and there might be the occasional security audits.
However, these activities are not consistently executed nor well-documented. The focus is often on quick fixes rather than long-term solutions.
Benefits
The main advantage of being at Level 1 is the presence of some cyber security measures, which is better than none. These initial steps can offer a basic level of protection against low-level threats and may satisfy minimal compliance requirements.
Challenges
Despite the basic safeguards, organisations at this level are still significantly exposed to cyber risks. The lack of a formal strategy makes it difficult to prioritise security efforts effectively.
Furthermore, sporadic and uncoordinated actions can create gaps in the posture, making the organisation susceptible to more sophisticated attacks.
Maturity Level 2: Partial
Maturity Level Two signifies that an organisation has progressed from ad-hoc cyber security measures and started implementing a more structured approach, albeit partially.
Explanation
In this stage, the organisation has identified key assets and risks and has taken steps to address them systematically. Security measures like multi-factor authentication, regular patching, and some levels of monitoring are generally in place.
However, these practices are not yet fully integrated or consistently managed across the organisation.
Benefits
The primary benefit at this level is the enhanced security posture.
Typically the business will have a more organised approach and can better defend against moderate-level cyber threats. Additionally, they are usually better prepared for compliance audits.
Another benefit at this level is that there tends to be a greater awareness of cyber security within the organisation, which contributes to a culture of security.
Challenges
While improvements have been made, there are still gaps and inconsistencies in your cyber security framework.
The partial implementation means some assets or departments might be better protected than others, leading to potential vulnerabilities. Additionally, without comprehensive monitoring and regular updates, the organisation is still at risk of falling behind in addressing evolving cyber threats.
Don't miss out on our latest.
Join our subscribers and receive expert insights on cyber security and IT. Sign up now!
Maturity Level 3: Mostly
Reaching Maturity Level Three indicates that an organisation has a well-structured and mostly consistent cyber security framework in place.
Explanation
At this level, cyber security practices are integrated into the organisation’s daily operations.
Advanced tools for threat detection, incident response plans, and regular training sessions are standard practice. Policies are documented, and compliance is actively managed. While not perfect, the cyber security measures are mostly comprehensive.
Benefits
The advantages of being at Level 3 are substantial.
For a start, the organisation can effectively defend itself against a range of cyber threats.
Compliance with industry regulations is more straightforward, and the company is likely to gain trust from clients and partners due to its strong security posture.
Challenges
Despite the well-implemented strategies, there is always room for improvement. Cyber security is an ever-evolving field, and organisations at this level must continue to adapt.
The challenge lies in staying ahead of new threats and continually refining and updating the cyber security framework. Monitoring and periodic reassessment are crucial for maintaining a strong security posture.
Section 3: How to Progress Through Each Level
Moving up the maturity ladder involves a combination of planning, implementation and ongoing assessment. Below are the general steps to help your organisation advance through the Essential Eight Maturity Levels.
Identify Your Current Status
Firstly, assess where your organisation currently stands. Use self-assessments, third-party audits, or internal reviews to gauge your maturity level.
Understanding your starting point is crucial for setting achievable goals.
Create a Roadmap
Based on your assessment, create a cyber security roadmap. Identify the controls you need to implement or improve. Then, prioritise them based on risk and business impact.
Secure Leadership Buy-In
Cyber security is not just an IT issue, it’s an organisational one. Security support and resources from leadership is crucial for effective implementation.
Implement Controls
Begin the implementation of planned controls. Whether it’s enhancing your incident response plan or setting up multi-factor authentication, each control puts you one step closer to a higher maturity level.
Train Employees
Cyber security is a collective responsibility. Regular training programs can enhance employee awareness and ensure all staff are aligned with your cyber security goals.
Monitor and Adjust
Implementation is not the end. Continuously monitor the effectiveness of your controls and be prepared to adjust your strategy based on performance metrics or evolving threats.
Regular Audits
Conduct regular internal and external audits to ensure compliance and to identify areas for improvement. These audits serve as both a checkpoint and a source for actionable insights.
Section 4: Tools for Assessment & Monitoring
Understanding and progressing through the E8MM is only part of the journey.
Implementing the right tools for assessment and monitoring is equally crucial for a well-rounded security posture. Knowing these tools is beneficial for several reasons.
Firstly, it provides practical guidance, enabling you to convert theoretical knowledge into actionable steps.
Secondly, these tools help you allocate resources effectively, whether it’s for vulnerability scanning or employee training.
Lastly, many of these tools are designed to automate complex tasks, offering real-time insights into your cyber security state. This reduces manual effort and lowers the risk of human error.
By arming yourself with the right set of tools you not only improve your security measures but also streamline processes. This will make it easier to climb the maturity ladder.
Vulnerability Scanners
These tools scan your systems to identify weaknesses that attackers could exploit, helping you take preventative action.
Security Information and Event Management (SIEM)
SIEM solutions help in with real-time analysis of security alerts generated by your IT infrastructure, allowing you to respond to threats faster.
Intrusion Detection Systems (IDS)
IDS tools monitor network traffic to identify suspicious activities, providing an extra layer of security by helping you spot potential threats early.
Compliance Management Tools
These platforms ensure that your cyber security controls meet industry regulations and standards, which is essential for avoiding fines and maintaining client trust.
Endpoint Security Software
These solutions offer comprehensive protection for all endpoints in your network, including antivirus, firewall, and more.
Employee Training Platforms
Such platforms educate your staff on cyber security best practices, aiming to reduce the risk posed by human error.
Patch Management Tools
These tools automate the process of updating software and fixing security vulnerabilities, keeping your systems up-to-date and secure.
Performance Metrics Dashboards
These dashboards help you visualise key performance metrics related to your business’s cyber security posture. This allows for better decision-making.
Section 5: FAQs
What Are the Essential Eight Maturity Levels?
The Essential Eight Maturity Levels are a framework designed to help organisations assess and improve their cyber security status. They provide a roadmap to follow for implementing key security controls effectively.
Why Are Maturity Levels Important?
The maturity levels serve as a benchmark for cyber security readiness. They guide organisations in identifying gaps in their security. They also help prioritise the implementation of controls.
How Do I Assess My Organisation’s Maturity Level?
Assessment can be done through internal reviews, self-assessments, or third-party audits. Tools for assessment and monitoring can also be useful in this process.
What If I’m Stuck on a Lower Maturity Level?
Being at a lower maturity level is not a failure – it’s a starting point. Identifying your level helps you understand what steps to take next. A well-thought-out plan and consistent efforts can help you move up the maturity ladder.
Is Reaching the Highest Maturity Level the End Goal?
While reaching the highest maturity level is commendable, cyber security is an ongoing process. Regular audits, monitoring, and updates are essential to maintain a strong cyber security posture.
Can Small Businesses Benefit from Understanding Maturity Levels?
Absolutely. The E8MM is scalable and can be adapted to organisations of any size. Even small businesses can find value in assessing and improving their cyber security measures.
Conclusion
Understanding and progressing through the Essential Eight Maturity Model is an invaluable exercise for any organisation concerned about cyber security.
From identifying your current status to equipping yourself with the right tools and knowledge, each step is a move toward a more secure environment.
If you found this article helpful and want to dive deeper into the topic, we invite you to check out our Free Essential Eight Cyber Security Report. This comprehensive report will provide you with additional insights, expert analysis, and practical steps to bolster your cyber security measures effectively.
Don’t leave your organisation’s safety to chance. Take control of your cybersecurity today.
More Like This
How Risky Behaviour and MFA Myths are Undermining Cyber Security
The number of cyber incidents caused by human error varies depending on which report you read. But they all have one thing in common. It’s high. A study by IBM estimates that human error is the driving factor in 95% of cyber security breaches. But how can that be?...
Latitude Hack: How To Stop It Happening To Your Business (Updated 2024)
Another day, and another Australian business has suffered a data breach. The Latitude Financial cyber attack hack has once again put the spotlight on the importance of cyber security for businesses. The recent attack also highlights the prominence of cybercrime in...
The Top 22 Cyber Security Audit Checklist Strategies in 2024
Imagine this: your business is thriving, taking advantage of all the opportunities in our increasingly connected world. You're reaching new customers, streamlining processes, and innovating like never before. But wait, what's that lurking in the shadows? Cyber...



