Another day, and another Australian business has suffered a data breach. The Latitude Financial cyber attack hack has once again put the spotlight on the importance of cyber security for businesses.
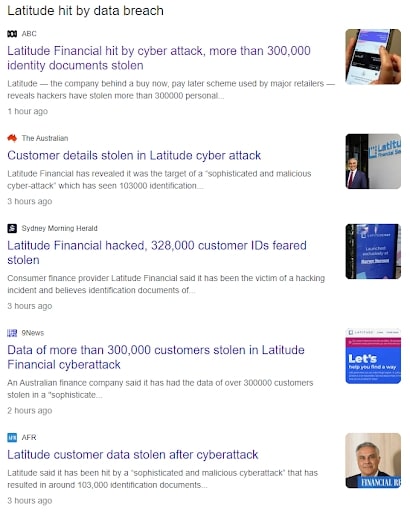
The recent attack also highlights the prominence of cybercrime in Australia.
With almost 8 million customers impacted and personal information stolen, the breach serves as a stark reminder; no organisation is immune to these threats.
In this article, we’ll go into details of the breach and explore the lessons businesses can learn. We’ll also outline strategies you can use to prevent similar attacks from happening to your business.
Background
This is never good.

Latitude Financial is a major Australian financial services company. They issue consumer loans and offer a buy now, pay later (BNPL) scheme used by major retailers.
On March 16 2023, Latitude revealed that it detected suspicious activity on its systems. This appeared to be a “sophisticated and malicious cyber-attack”.
How Was Latitude Financial Hacked?
Latitude claims that the cyber attack began with a major vendor the company uses. This is believed to be a back-end infrastructure provider.
The attacker eventually obtained the login details of a Latitude employee and stole personal information.
Latitude has confirmed that:
- Approximately 7.9 million Australian and New Zealand driver licence numbers were stolen.
- 53,000 passport numbers were stolen.
- Roughly 100 customers had a monthly financial statement stolen.
- A further 6.1 million records dating back to 2005 were stolen, of which 94% were provided before 2013.
That’s roughly 14 million records stolen.
Latitude Financial said it refused to pay a ransom to the hackers.
Why Was Latitude Hacked?
A company like Latitude could be targeted by a cyber attack for several reasons:
Valuable Data
Financial institutions possess a wealth of sensitive and valuable data. This includes personal information, credit card details, and transaction records. Cybercriminals love this kind of information. They can use it for identity theft, fraud, and other illicit activities.

However, financial institutions aren’t the only organisations that hold this type of data. Every business that stores sensitive customer information needs to be aware of the risks.
Financial Gains
This one is obvious. Cybercriminals target financial institutions to make direct financial gains through unauthorised transactions, stealing funds, or selling stolen data on the dark web. This is likely one of the motivating factors behind the Latitude hack.
Reputation Damage
Attacking a high-profile company like Latitude Financial can generate significant media attention and damage the company’s reputation.
This negative publicity may result in a loss of customers, reduced investor confidence, and potential legal repercussions.
Vulnerabilities in Third-Party Vendors
As the Latitude hack shows, cybercriminals can exploit vulnerabilities in third-party vendors that provide services to the company.
These vendors can inadvertently provide an entry point for attackers to access the company’s systems and data.
Demonstrating Their Capabilities
Cybercriminals or state-sponsored actors may target organisations like Latitude to demonstrate their skills or make a political statement.
Successfully breaching a well-known financial institution can serve as a warning to other organisations. Additionally, it can act as a showcase of the attacker’s capabilities.
Weaknesses in Security Measures
We hope that high-value targets like Latitude are continuously updating their security measures. However, cybercriminals are always looking for – and finding – gaps and vulnerabilities to exploit.
If a company has weaknesses in its cyber security infrastructure, it could become an attractive target for attackers.
Don’t miss out on our latest.
Join our subscribers and receive expert insights on cyber security and IT. Sign up now!
How To Prevent An Attack
No measures will guarantee you 100% security. However, there are some critical steps you can take to better protect your business.
Employee Awareness and Training
The Latitude hack involved the theft of employee login credentials. This highlights the need for continuous employee awareness and training.
Here are a few steps businesses should take.
Provide regular cyber security training
You must equip every employee with the necessary knowledge and skills to identify, prevent, and respond to potential cyber threats.
- Develop a comprehensive training program: Create a cyber security program that covers essential topics. Update the program periodically to address evolving threats and include emerging best practices.
- Conduct frequent training sessions: Offer regular training sessions to ensure employees stay up to date with the latest cyber security information. Continuously remind employees of the importance of practising safe online habits. Training can be in the form of workshops, webinars, or an online course. Remember to tailor training to the needs and skill level of each employee.
- Include real life examples and scenarios: Real life examples will help your employees understand the implications of cyber threats. This approach can make training more engaging.
- Test employee knowledge: Use assessments and quizzes in your training program. In doing so, you can gauge individual employees’ understanding of cyber security topics. See the example below from usecure.
- Promote a culture of cyber security awareness: Encourage a culture of cyber security awareness in your organisation. This means promoting open communication about cyber threats, sharing security updates and news, and recognising employees who demonstrate good cyber security practices.
- Provide ongoing support and resources: Offer continuous support and resources for your employees. This way, they can reference relevant materials when they encounter cyber security concerns or have questions.
Educate employees on phishing attacks
The Latitude breach highlights the importance of educating employees about cyber security in general. However, it’s worth stressing the importance of educating your team about phishing attacks in particular.
These attacks often involve fraudulent emails, messages or websites designed to trick people into revealing sensitive information.
We’ve got a comprehensive guide on phishing here.
However, some quick steps you can take include:
- Teaching employees to recognise phishing emails
- Highlighting the risks of phishing on social media and messaging platforms
- Discussing the dangers of clicking on unknown links or downloading attachments
- Providing guidance on reporting phishing attempts
- Conducting phishing simulations
Implement Strong Password Policies and Password Managers
Strong password policies and password managers. Two tactics that play a crucial role in protecting sensitive information and preventing unauthorised access to systems and accounts.
Implementing strong password practices alone can significantly reduce the risk of cyber attacks.
Define password complexity requirements
Set clear guidelines for password creation. This includes requirements for:
- Minimum length
- A mix of upper and lower case letters
- Numbers
- Special characters
This will help ensure your employees create strong and secure passwords that are difficult to crack.
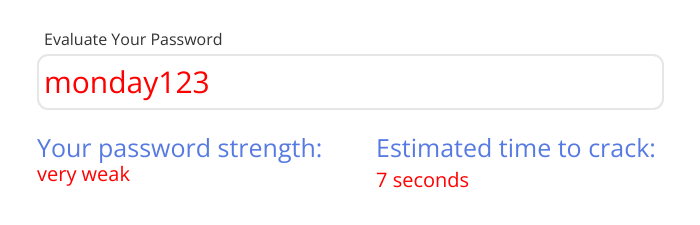
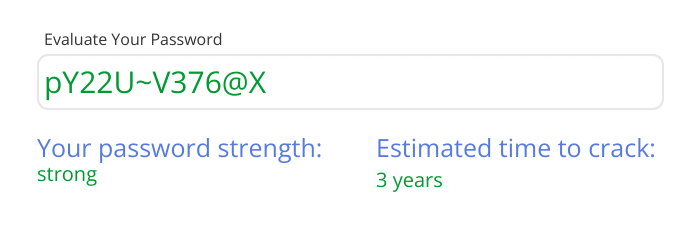
Enforce password expiration & reuse policies
Require your employees to change their passwords periodically. This could be every 60 to 90 days.
Make sure you prohibit the use of old passwords. These are easy targets.
Promote the use of password managers
We know. There’s a lot in the news about the security of password managers right now. However, they still remain a safer option than writing passwords on a piece of paper.
Password managers can help your employees store, generate, and manage their passwords. Password managers can also create complex passwords. Ones that are unique to each account.
This instantly reduces the risk of employees using weak or reused passwords.
Monitor & audit password compliance
Be sure to regularly audit employee accounts to ensure compliance. To some, this might feel a bit like spying. However, at the end of the day, you are simply trying to protect your business, including your employees.
Check for the use of default or easily guessed passwords. Additionally, you’ll want to assess the overall strength of employee passwords.
This proactive approach to password security will help safeguard your organisation against potential cyber threats such as the Latitude hack. Additionally, it will ensure a safer working environment for all employees.
Data Minimisation and Privacy by Design
It’s also important to adopt proactive strategies like data minimisation and privacy by design. These are focused on preventing threats rather than responding to them.
What is Data Minimisation?
The core idea here is simple: the less data you have, the less data you have to lose.
Data minimisation is about collecting only what you need, storing it only as long as necessary, and then securely disposing of it. It can drastically reduce your risk footprint.
If you recall from above, Latitude Financial had data dating back as far as 2005.
Had they disposed of this data appropriately, they’d have saved millions of pieces of data from the breach.
Key Steps:
- Assess Your Data Needs: Review the data you’re collecting at scheduled intervals. Ask yourself, “Do we really need this?” If the answer is no, don’t collect it.
- Limit Access and Storage: Just as you minimise what you collect, minimise who has access and how long you keep it. Think of data as perishable goods.
- Regular Audits: Implement routine checks to ensure unneeded data isn’t lingering in your systems.
What is Privacy by Design?
This is all about integrating privacy into your business’s DNA. From the first line of code to the final product, every step should consider the privacy of user data.
This is a proactive stance – not waiting for a problem to arise, but preventing it in the first place.
Key Steps:
- Proactive Measures: Anticipate privacy issues before they arise. Be ahead of the game.
- Default Privacy: Make sure that user privacy isn’t an option – it’s a given.
- Integrated Privacy: Privacy shouldn’t be an add-on. it should be an integral part of your product or service.
- End-to-End Security: Secure data throughout its entire lifecycle, from collection to deletion.
- Transparency: Be open about your data practices. Transparency creates trust.
Implementing these Principles
- Privacy Impact Assessment (PIAs): Regularly conduct PIAs for new projects.
- Training and Awareness: Update your team on best practices in data privacy, especially with the surge in AI usage.
- Collaboration: Work with privacy experts to align with the latest standards and regulations.
Embedding these frameworks into your organisation can help you protect data and build trust.
Use Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is a vital security measure that adds an extra layer of security to your accounts and systems.
By requiring at least two separate forms of verification, MFA makes it more difficult for attackers to access sensitive data. Even if they have obtained the user’s password.
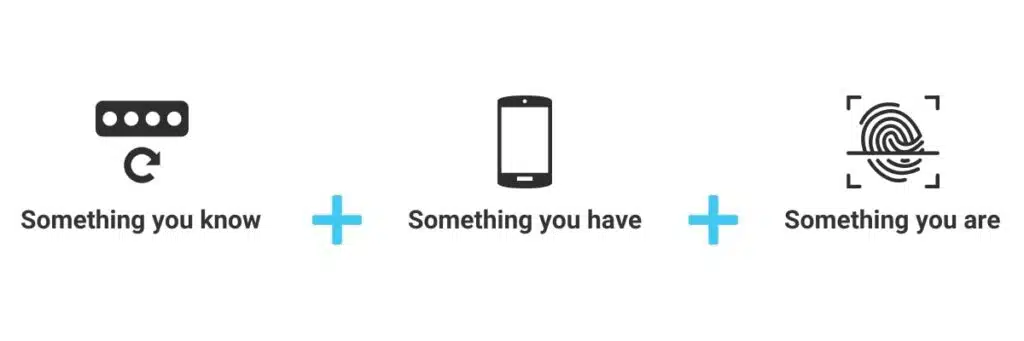
MFA typically involves a combination of at least two of the following factors:
- Something you know (e.g., a password)
- Something you have (e.g., a smartphone)
- Something you are (e.g., fingerprint or facial recognition)
Prioritise the use of MFA for systems and accounts that store sensitive information or control critical infrastructure. This could include email accounts, financial systems, customer databases, and admin accounts.
Make sure you implement a user friendly MFA solution. This will make it easy for employees to use and minimise disruption to their workflow. In doing so, you will encourage user adoption.
Good options include hardware tokens, biometric authentication, or mobile apps like Google Authenticator.
Regular Security Assessments & Penetration Testing
Regular security assessments and penetration testing are proactive measures that will help you identify vulnerabilities in your systems and networks.
While not flawless, these measures will allow you to address potential security weaknesses before they are exploited as seen in the Latitude hack.
What’s the difference?
Security assessments involve a comprehensive evaluation of your security posture. This includes policies, procedures, and technical controls.
Penetration testing, on the other hand, is a targeted attempt to exploit existing vulnerabilities in your systems and applications. It essentially simulates the actions of a malicious attacker. Without the subsequent extortion attempts, of course.
How often should I do them?
The frequency of security assessments and penetration tests will depend on your company’s risk profile. For most organisations, yearly assessments are a good starting point.
Use professionals
Be sure to engage qualified cyber security professionals to conduct these tests. Of course, this comes at a cost. However, professionals with relevant certifications and experience will provide you with more valuable information than if you tried to go it alone.
A certified professional will:
- Define the scope of testing: With a clear outline of the systems, applications, and networks that will need testing. This will ensure coverage of all critical components of your business.
- Document and remediate findings: They will document and prioritise vulnerabilities, with a focus on addressing high risk issues as quickly as possible.
- Monitor progress and update your security posture: Ensuring your testing and assessment schedule is adjusted as needed to address emerging threats.
This approach, combined with employee education and the implementation of robust security controls, will help create a more secure working environment and protect your organisation’s sensitive data and assets.
Data Encryption & Secure Storage
Data encryption and secure storage are essential components of a solid cyber security strategy.
They help protect sensitive data from unauthorised access and potential misuse. Thus, reducing your risk of a data breach or other cyber security incidents like the Latitude hack.
What is encryption?
Encryption is the process of converting data into a secure format. It does so by “scrambling” plain text into obscure cipher text. This data is then only accessible by users with the correct decryption key.
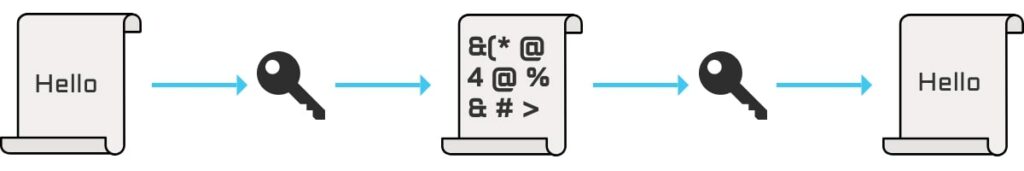
Note: when an organisation is the victim of a ransomware attack, its data is encrypted by the attacker. The “ransom” is requested to decrypt the data.
However, when your organisation uses encryption it’ll hopefully be for non-malicious reasons.
Before you encrypt anything, you need to first identify the types of sensitive information your organisation handles. This will help you determine which data requires encryption.
Choose the right encryption method
Different types of encryption will be suitable for your organisation’s needs. You’ll need to take into account the sensitivity of data, performance of your systems, and any regulatory requirements. Common encryption methods include symmetric encryption, asymmetric encryption, and hashing algorithms.
Remember that for trivia night.
You’ll want to ensure that sensitive data is encrypted both at rest (when stored on discs and databases) and in transit (when transmitting over networks or between systems). This will help protect your data during all stages of its lifecycle.
Storage
In addition to encryption, consider implementing secure storage practices to further protect sensitive data.
This might include segregating sensitive data from less important data, implementing access controls to restrict access to authorised users, and regularly backing up data to ensure its availability in the event of a breach or system failure.
Create A Cyber Incident Response Plan
Make sure your organisation has a cyber incident response plan.
A cyber incident response plan will help protect your organisation from cyber attacks and mitigate damage in the case of a security breach.
An incident response plan outlines the steps your business will take to identify, contain, eradicate, and recover from a cyber incident.
To create a cyber incident response plan, you’ll need to:
- Establish an incident response team: Identify key personnel responsible for managing and responding to cyber security incidents. Your response team should include members from various departments including IT, legal, HR, and public relations. Assign clear roles and responsibilities to each team member to ensure an effective response.
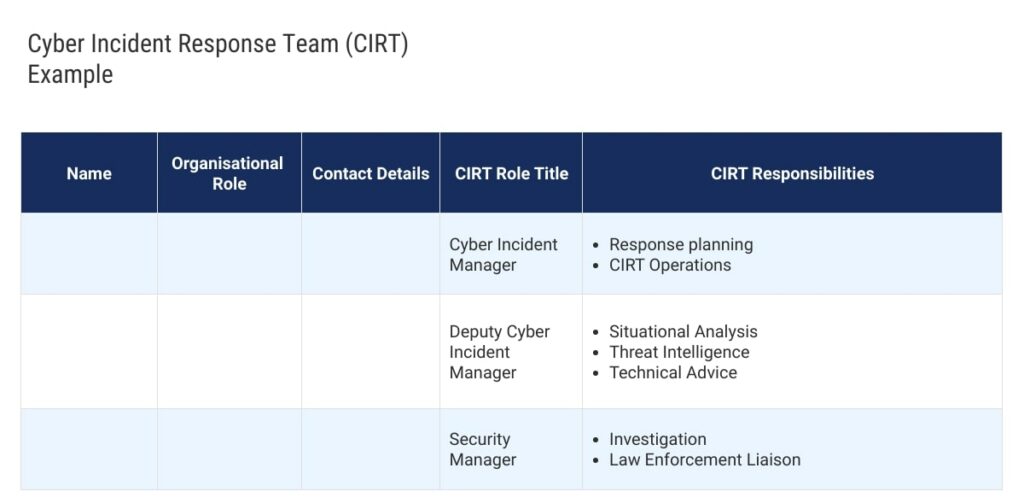
- Develop response procedures: Outline the steps your business will take to address the cyber security incident. This should cover initial detection and full recovery.
- Create communication protocols: Develop clear communication protocols for reporting and escalating incidents. Both internally and externally. This includes guidelines for notifying affected customers and clients, law enforcement, and regulators.
- Establish a notification and escalation process: Clearly define the criteria for escalating the incident to higher levels of management or external authorities.
- Integrate with business continuity and disaster recovery plans: This will help ensure your business has minimal downtime and reduce the overall impact on your organisation.
- Conduct regular training and simulations: Conduct simulated exercises to test and refine your response capabilities. If you identify gaps in your plan, address them immediately.
- Review and update your plan: Incorporate lessons learned from previous incidents and adapt to changes in your business’s risk profile. There will always be new threats or vulnerabilities that you need to address.
By creating a robust incident response plan, you will be better prepared to handle cyber security incidents.
Collaborate With Cyber Security Experts
Finally, one of the best ways to prevent an attack like the Latitude hack on your business is by collaborating with cyber security experts.
Partnering with external experts allows your organisation to benefit from their specialised knowledge, experience, and resources. In doing so, you’ll stay ahead of the constantly evolving threat landscape.
Here are some tips to consider when collaborating with cyber security experts.
Assess your needs
It’s important to evaluate your specific cyber security needs and challenges. This will help you determine the type of expertise and services required. This could include penetration tests, threat intelligence, or incident response support.
Select the right partner
When selecting a cyber security partner, consider their industry reputation, experience, range of services, and customer references.
You’ll want to ensure that the partner you choose has the necessary expertise and resources to effectively address your needs.
Foster open communication
Establish open lines of communication with your cyber security partner to facilitate the sharing of information and insights.
This will allow both parties to work effectively as a unit. Additionally, you’ll be in a better position to adapt to any changes in the threat landscape or your company’s risk profile.
Leverage external expertise for employee training
You’ve got a relationship with the professionals. Why not utilise their expertise to provide training and awareness programs for your employees?
In doing so, you can enhance your internal cyber security capabilities and build a security conscious culture.
Stay informed
Work closely with your cyber security partner to stay informed about emerging threats, vulnerabilities, and trends in your industry.
This will help your organisation stay on the front foot in its approach to cyber security.
Conclusion
Cyber attacks like the Latitude hack serve as important reminders. Each new attack is more sophisticated than the last.
As such, it’s important to invest in robust cyber security measures to protect your assets, sensitive data, and customer trust.
By incorporating the strategies above you can bolster your defences against potential threats.
Take these steps to demonstrate your commitment to the security and privacy of your customers, partners, and employees.
