The number of cyber incidents caused by human error varies depending on which report you read.
But they all have one thing in common.
It’s high.
A study by IBM estimates that human error is the driving factor in 95% of cyber security breaches.
But how can that be?
Anybody with internet access knows the risks. Cyber attacks frequently populate the news. And spam messages appear on our devices ad nauseam.
To add to that – most businesses have basic security controls like multi-factor authentication (MFA) in place.
But maybe that’s part of the problem.
Despite widespread awareness of cyber risks and the use of basic security controls, humans remain the weakest link in cyber security.
This article will explore two key reasons for this:
- Users’ willingness to engage in risky online behaviour; and
- The dangerous overconfidence in technical controls like MFA.
In the following sections, we’ll dive deeper into convenience at the cost of safety and the MFA fallacy.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
Convenience At The Cost of Safety
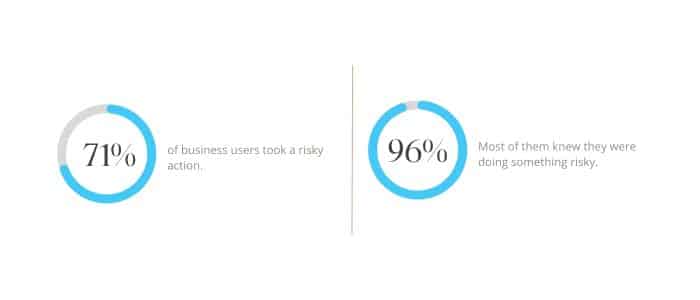
71% of business users took a risky action on their devices. 96% of them knew that they were doing something risky.
That’s according to a new report by Proofpoint, where they surveyed 7,500 users and 1,050 security professionals across 15 countries.
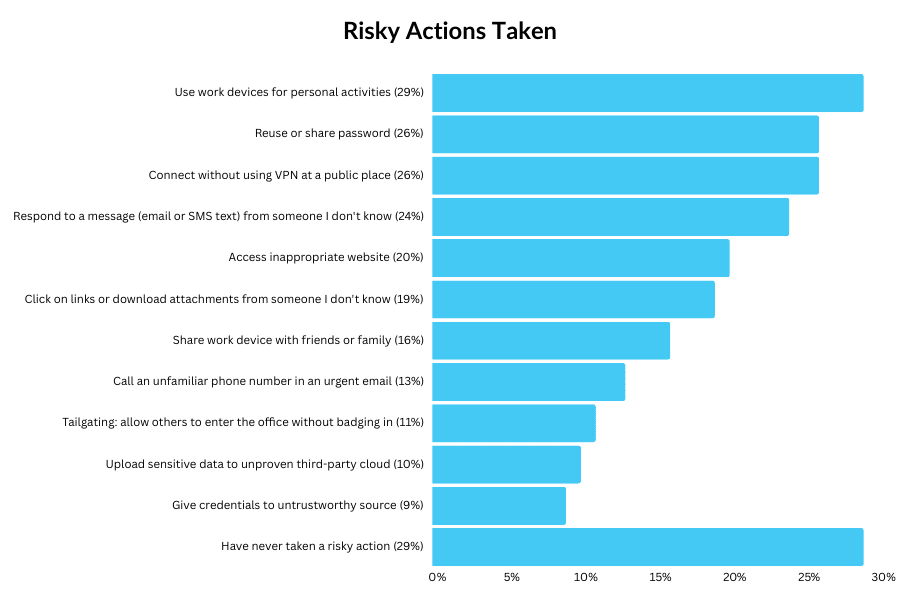
These behaviours included things like:
-
- Reusing passwords;
- Clicking on links from unknown senders;
- Giving credentials to unknown sources; and
- Using work devices for personal activities.
Those are startling findings for anyone working in cyber security.
So, why are end users knowingly taking risky actions?
Why Are End Users Knowingly Taking Risks?
No surprise here – it’s convenient.
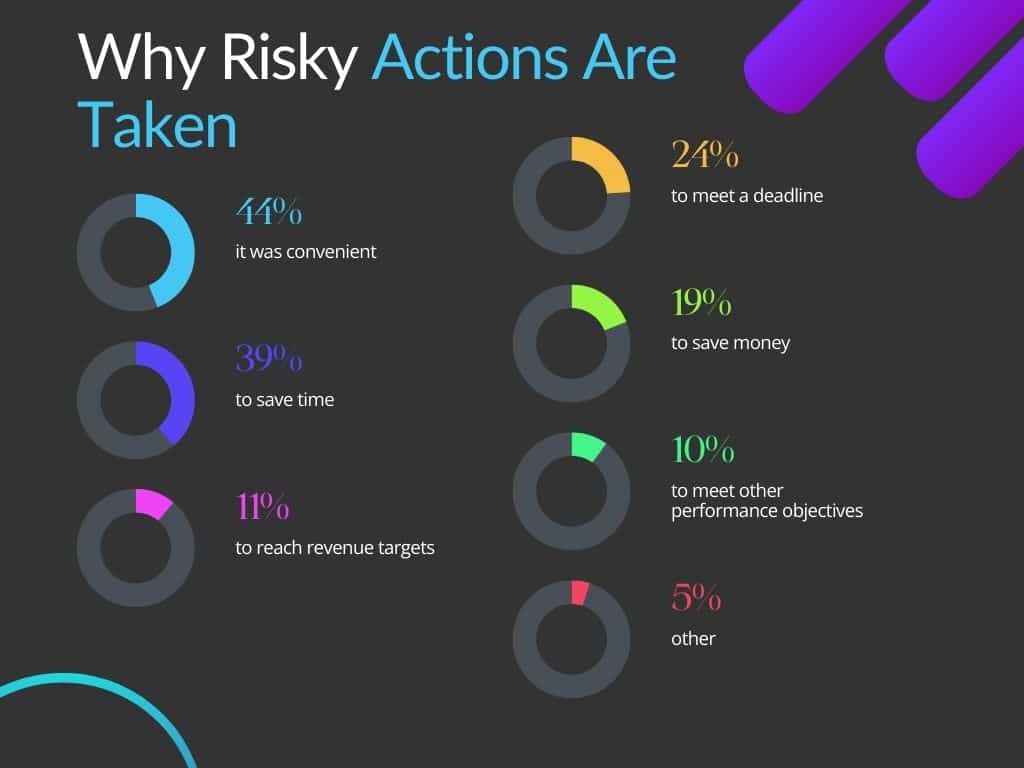
That’s right, 44% of respondents said they took risky actions because it made their life easier.
For example, memorising passwords is hard and annoying. Especially if it’s a complex password.
Meanwhile, reusing the same simple password you’ve been using for every account you’ve ever had (personally and professionally) is easy.
There’s just one problem with that…
When faced with a choice between security and expediency, many users opt for the path of least resistance.
The other Top 3 reasons for taking risky action are saving time (39%), and meeting urgent deadlines (24%).
We’re constantly bombarded with tasks and deadlines, so the temptation to cut corners is strong.
Reusing the same password across multiple accounts might save a few minutes here and there. Clicking on a link without verifying the sender might seem like a harmless shortcut. But these seemingly minor risks can add up to serious consequences.
If We Know, Hackers Know
The problem is that cybercriminals are all too aware of this human tendency to convenience.
They specifically craft their attacks to exploit our desire for expediency, using social engineering tactics designed to pressure, deceive, or manipulate users into making risky decisions.
In fact, Proofpoint’s research reveals that 58% of users who took risky action engaged in behaviour that would make them prime targets for social engineering attacks.
-
- This could include:
Replying to phishing emails; - Providing personal information or critical business data to unverified sources; or
- Allowing a stranger to remotely access their device.
- This could include:
And we’ve all seen the consequences of falling for one of these attacks. They can be severe, and even cripple businesses, leading to data breaches, financial losses, and reputational damage.
The best defences mean nothing if users aren’t doing the right thing.
In the next section, we’ll explore another factor contributing to the human risk in cyber security: overconfidence in technical controls like MFA.
The MFA Myth
To be clear, we don’t think MFA is a myth. And we do believe it is effective.
However, MFA has long been viewed as a cyber security silver bullet.
And there is solid reasoning behind this. MFA requires users to provide an additional form of verification beyond a password. So it adds an extra layer of protection.
That being said, the industry’s confidence in MFA may be misplaced.
While MFA certainly is a valuable tool, it’s not infallible.
Cybercriminals are increasingly finding ways to bypass MFA, rendering this supposed fortress of security more of a paper tiger.
A striking example of this is the prevalence of MFA-bypass attacks using frameworks like EvilProxy.
Proofpoint data shows that around 1 million such attacks are launched every month. These attacks use reverse proxy servers to intercept and manipulate traffic between a user and a target website, allowing attackers to capture and replay MFA tokens.
Despite this, 89% of security professionals believe MFA provides complete protection against account takeover.
There is danger in this overconfidence.
When security teams believe they have strong controls in place, they may be less vigilant in monitoring for other types of attacks.
Users, too, may let their guard down, assuming MFA will protect them even if they engage in risky behaviours.
Hackers Are Bypassing MFA
How are they doing it?
One method is what is known as an MFA Fatigue attack.
This is where attackers repeatedly send second-factor authentication requests to a person’s device. Said person, wanting to make the notifications stop or even thinking it’s a glitch, eventually approves one.
This approval lets the hacker bypass the MFA security and receive access to the victim’s account.
This is how the 2022 Uber hack unfolded.
The point here isn’t to suggest that MFA is redundant. Far from it.
However, because MFA has become a standard security control, attackers are finding standard ways to circumvent it.
By recognising the limits of MFA and adopting more comprehensive security controls, your organisation can be better prepared for the changing nature of cyber attacks.
Don't miss out on our latest.
Join our subscribers and receive expert insights on cyber security and IT. Sign up now!
The Common Denominator
At first glance, it might seem that users taking risky actions and MFA are separate issues.
One is about user behaviour, the other about technical controls. But there’s a common thread that ties them together: the human factor.
In both cases, human attitudes and behaviours are undermining cyber security efforts.
When users prioritise convenience over caution, they create vulnerabilities that no technical control can fully mitigate.
And when security professionals place too much faith in controls like MFA, they risk overlooking the critical role of user awareness and behaviour.
Whose Responsibility Is Cyber Security?
Proofpoint’s survey reveals a worrying lack of clarity around cyber security responsibility among users. Only 41% of users acknowledged that they bear personal responsibility for cyber security while at work. A majority (52%) were unsure, while 7% believed they had no responsibility at all.
Meanwhile, 85% of security professionals say that most employees know they are responsible for security.
What is going on here?
The ambiguity is a major problem. When users don’t see cyber security as their responsibility they’re less likely to prioritise it in their daily actions. Also, they may be more likely to engage in risky behaviour, believing technical controls will protect them, or that security is not their concern.
And if cyber security professionals fail to communicate the collective responsibility the issue will only compound.
The reality is that cyber security is everyone’s responsibility. No matter how strong your technical defences are, they can be undermined by a single careless click or compromised credentials.
Every user, from the entry-level new starter to the C-suite executive, plays a crucial role in maintaining the security of an organisation.
The Importance of User Behaviour
This is why focusing on user behaviour is so critical. Technical controls are important, but they’re not enough on their own. To truly strengthen your organisation’s cyber security posture, you need to create a culture of security awareness and responsibility.
This means regular, engaging security awareness training that goes beyond just telling users what not to do.
It means fostering a sense of shared ownership for cyber security, where everyone understands their role and the responsibility to make safe choices.
It means leading by example, with senior management demonstrating their commitment to cyber security through their actions.
Changing user behaviour isn’t easy. It takes constant effort, clear communication, and a willingness to challenge entrenched attitudes and habits.
But it’s an effort worth making.
In the next section, we’ll explore some strategies for effecting behavioural change.
Shifting the Paradigm
Addressing the human factor in cyber security requires a paradigm shift. Instead of viewing users as the weakest link, we need to empower them to be our strongest line of defence. Here are three strategies for making this shift.
1. Make Security Convenient and User Friendly
As highlighted earlier, one of the main reasons users engage in risky behaviours is that secure practices are often seen as inconvenient or cumbersome.
To counter this, organisations need to prioritise user experience in their cyber security strategy.
This could involve the use of single sign-on (SSO) solutions to reduce password fatigue, providing secure and easy tools for remote work, or streamlining security processes to reduce friction.
The goal is to make the secure way the easy way, so users are less tempted to find risky workarounds.
2. Build a Culture of Security Responsibility
As we’ve seen, many users are unsure about their role in cyber security. To address this, organisations need to build a culture where security is seen as everyone’s responsibility.
This starts with clear, consistent communication from leadership. Senior management should regularly emphasise the importance of cyber security and model good behaviours.
Also, security teams should work to build relationships with other departments, acting like partners rather than policemen.
Regular security awareness training is also crucial. But training should go beyond just compliance. It should be engaging, relevant to users’ daily work, and focused on fostering a sense of shared responsibility.
By helping users understand the “why” behind security policies, we can motivate them to become active participants in the security process.
3. Positively Reinforce Good Behaviours
Too often, we frame cyber security in negative terms – don’t click this, don’t download that. While these messages have their place, they can also create a sense of fear and resentment around security.
To counter this, your business should focus on positively reinforcing good security practices.
This might involve recognising and rewarding employees who report phishing attempts, offering incentives for completing security training or celebrating departments with the best security track records.
Making cyber security a positive part of your business’s culture may encourage users to view it as a shared goal that everyone should contribute to.
This change won’t happen overnight. But it can help you turn vulnerabilities into assets.
Conclusion
Here’s the bottom line: humans are the weakest link in cyber security.
Whether it’s risky actions taken in the name of convenience or blind faith in MFA, user behaviour and attitudes are leaving organisations vulnerable.
Changing this won’t be easy. It means rethinking our approach to security, making it more user-friendly, and fostering a culture of shared responsibility.
But the cost of inaction? It’s far higher.
In the end, cyber security comes down to people. People are our greatest asset, but also our biggest risk.
By putting people at the centre of our security strategies, we can turn that risk into our greatest strength.
More Like This
Windows 10 End of Life (EOL) and What it Means
Microsoft has announced that October 14, 2025, will be the End of Life (EOL) date for Windows 10. Windows 10 EOL is set to affect all versions of Windows 10, including Home, Pro, Education, and Enterprise. Research from Lansweeper indicates that only 23.1% of...
ISO 27001 Certification in Australia: A Comprehensive Guide
Business data is like a treasure for cyber criminals. In fact, buried in almost every organisation's information assets are details worthy of holding ransom. So, how do you protect it? With ISO 27001 certification. ISO 270001 is more than just a standard industry...
Cyber Hygiene For Business: What You Need To Know
Implementing cyber hygiene practices is one of the most effective ways to protect your business from cybersecurity risks. As a business owner, the security of your company's data is paramount. With the prevalence of cyber-attacks in the modern world, it’s increasingly...



