Cyber security threats are a very real part of running a company, given just how much business is now conducted online. Cyber security can be a convoluted issue to deconstruct. Talk amongst businesses of cyber security threats as pressing issues can leave you overwhelmed and confused. Without knowing what actual cyber security threats are, it can feel like you’re floundering around in the dark. Cyber security threats include a whole range of vulnerabilities and cyber-attacks. Here, we’ll just cover some of the most common cyber security threats.
‘Cyber security threats’ isn’t some nebulous, new concept. It’s a trending term used as a catch-all to cover the various types of attacks and risks to networks, devices, and computers. Such threats have existed for as long as the internet itself. Just check out the Morris worm! The grouping of the words ‘cyber security threats’ helps to hammer home that these threats are very real. If your company is exposed to risk, it’s open to an attack by malware, phishing, data breaches, DDoS, ransomware and more.
For a deep dive on Cyber Security check out our Definitive Cyber Security Guide for Small to Medium Business.
The Most Common Cyber Security Threats
Malware
What is Malware?
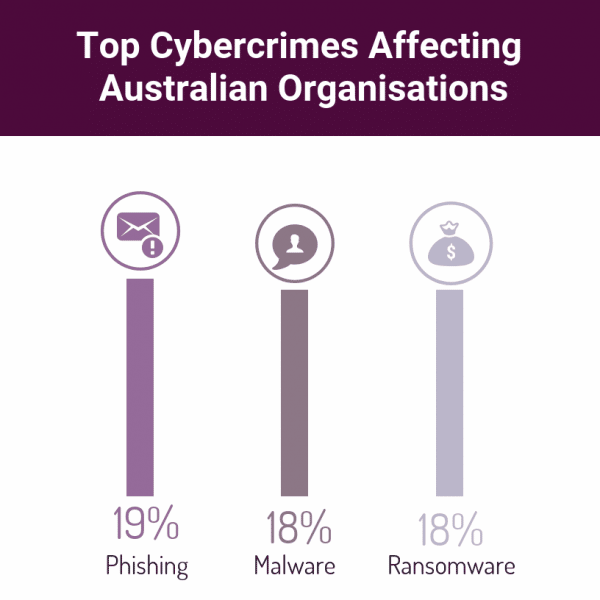
Malware makes up 18% of the top cybercrimes affecting Australian organisations. The term malware is a contraction of ‘malicious software.’ It’s a catch-all term for any number of malicious programs that infect your system with the intent to corrupt or steal your data. It could be a trojan, worm, virus, spyware. or ransomware. It’s almost always introduced to the system through an email attachment, or an unsafe download. This is often through a trusted site, in order to trick you into allowing it through your anti-virus software. Malware stands as one of the biggest and most prolific cyber security threats. When protecting your business from a malware attack, user vigilance is key.
So, who is behind the malware threatening your organisation? In most cases, Malware is created by a team of hackers, not a single person. The creation of malware is most often driven by money. However, it can be a tool for protest, a means to test security, or, in extreme cases, a government method of warfare. The creators of the malware will either use it themselves or sell it on the Dark Web.
Detecting Malware
Some strains of malware — like ransomware and adware — are known to you immediately, while others are harder to detect. Anti-malware software, like those offered by Stanfield IT, will ensure malware is detected before it infects your PC, Mac, or mobile device. Malware is a major threat to small and medium businesses. The damage it can cause is excessive. It can collect personal details, attack other computers and networks, delete files from your computer, or even corrupt your whole hard drive.
Avoiding a Malware Attack
Malware is all over the internet, but predominantly can’t infect your device unless you let it. For example, the Malware will prompt you to open an email or download a file. Employees being vigilant and informed when it comes to suspicious-looking attachments is vital. When it comes to cyber-security threats, education and awareness are key, making a big difference to the level of risk your company is under.

Phishing
What is Phishing?
Sitting high on our list of cyber security threats, phishing is primarily aimed at the less technologically savvy. Phishing makes up 19% of the top cybercrimes affecting Australian organisations.
Phishing attacks have been in operation for nearly 25 years and usually randomly target individuals. A phishing attack is when you receive an email appearing to be from an organisation or person that you trust. This could be your bank, for example. It will usually flag a vague ‘fraudulent activity as an urgent enticement for you to take action and click on the email link. The link will lead to a dummy site that looks like the real thing but is a trap to capture your login credentials.
Detecting Phishing
Phishing scams have become clever and very good at mimicking the real deal, such as emails from your bank. Just remember that your bank will never ask you to enter your password via an email link.
In 2018, the number one disguise for distributing malware in phishing attacks were fake invoices, followed by email delivery failure notices. You’ll often see phishing emails disguised as Apple, with the sender appearing to be ‘Apple Payment.’ It’s important to not only educate your staff around phishing, but your clients or customers, too.
There are 1.5 million new phishing sites created every month and can result in customer accounts being jeopardised. Make it known how to identify emails or pop-ups that may look like they’re from your company but are, in fact, phishing.
Avoiding a Phishing Attack
Strategies like implementing two-factor authentication can greatly decrease cyber security threats. Even if they succeed in capturing your password in a phishing attack, it will not be enough to access your information if you have two-factor authentication.
Other security measures include always keeping your browser updated, using anti-virus software, and not clicking on popups. Making sure staff are aware of these simple measures will help secure them — and your business — from a phishing attack. Also ensure your staff are across the signs of phishing emails. Bad grammar and spelling, strange greetings, a misleading URL, urgent or threatening language, and requests for personal information are common indicators.

Data Breaches
What is a Data Breach?
Data breaches represent some big bucks for hackers and cyber criminals. Malware program can easily hold your information hostage until you cough up the asking price. Ransomware, in particular, has seen a huge surge as one of the more common cyber security threats. Victims will often pay the price to recover their data that hasn’t been backed up.
Who is at Risk of a Data Breach
It’s important to note that smaller businesses are often targeted more due to the relative ease of infiltration. Bigger companies, like Amazon and Google, will have world-class digital security protecting them from such cyber security threats.
Data breaches aren’t only a threat for small companies, and often target organisations with extremely sensitive and confidential information, like in healthcare. It’s not only the security and information of your company a data breach can jeopardise. Individuals within (employees or investors) or external to (clients or customers) the company are affected, too. This could include an individual’s medical information, account details, financial information, passwords, or contact details being taken.
Dealing with a Data Breach
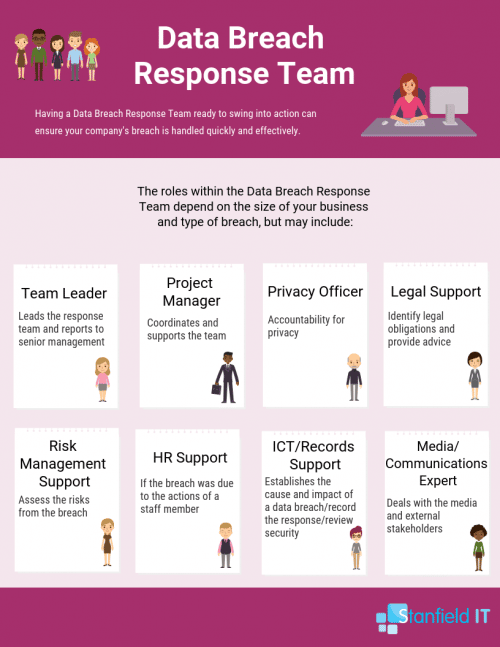
Of course, prevention is always better than cure. Having appropriate, up-to-date security programs and software across your business will reduce the risk of being targeted. However, it’s also important to have a data breach response strategy in place. Establishing a data breach response team is an important way to be prepared in case of a breach and minimalise damage. This team will help your company quickly and effectively manage a data breach by providing the strategy for containing, assessing, and managing the incident from start to finish.
Data breaches are one of the most serious forms of cyber security attacks. 64% of reported data breaches by December 2018 were due to malicious or criminal attacks. The other breaches came down to human error. Having a data breach response team at the ready can reduce any harm suffered by affected individuals and preserve and build public trust.
DDoS Attack and Botnets
What are DDoS Attacks and Botnets?
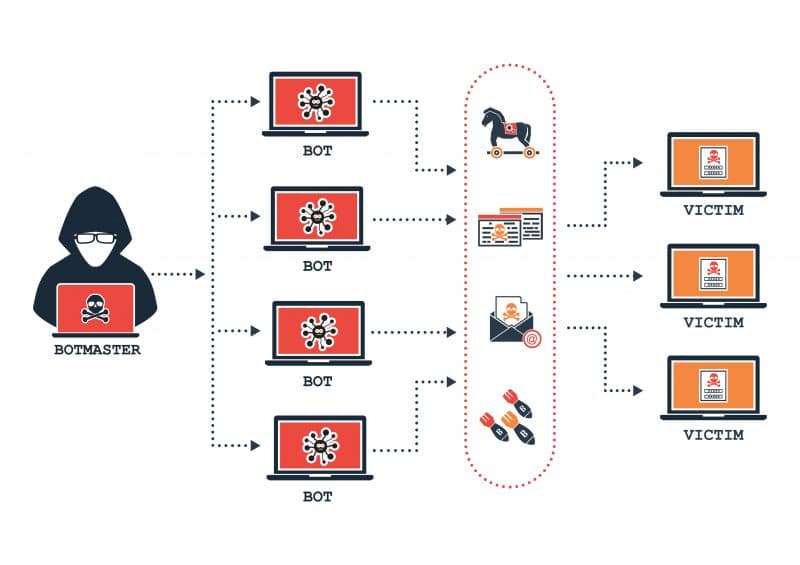
DDoS (Distributed Denial of Service) and botnets often go hand in hand as double-whammy cyber security threats. A botnet is a network of bots across ‘infected’ computers that can be remotely controlled at the source. A botnet could be used in a DDoS attack where the network of computers all apply pressure to a targeted website or server until it eventually crashes. The hacker behind such an attack could easily be using your computer in this attack without your knowledge.
Detecting a DDoS or Botnet Attack
There are two types of DDoS attacks — application layer attacks and network layer attacks. The former include HTTP floods, slow attacks, zero-day assaults, as well as attacks that target vulnerabilities in operation systems, web applications, and communication protocols.
The goal of these attacks is to overwhelm a target application with requests that seem innocent and legitimate. The result? High CPU and memory use that may hang or crash the application. Network layer attacks include UDP and SYN floods; NTP, DNS, and SSDP amplification; and IP fragmentation. These attacks are nearly always done by botnets who try to consume the target’s upstream bandwidth and thus saturate the network.
Avoiding a DDoS or Botnet Attack
Both DDoS and botnet attacks can be controlled through the correct protection service, such as Fortinet Enterprise Subscription. Many of these services can work through the Cloud to limit cyber security threats. Setting up all employees with two-factor authentication can help mitigate botnet attacks in your company. Botnets give a hacker unlimited attempts at guessing a password. With two-factor authentication, they will not be able to access your account from their device without your authorisation. This is true even if they eventually guess the password correctly.
Ransomware
What is Ransomware?
Briefly addressed above, ransomware deserves a mention of its own as it poses a high risk to small businesses. Ransomware is a type of malware and makes up 18% of the top cybercrimes affecting Australian organisations. Ransomware, as its name suggests, stops access to systems or personal files unless a ransom payment is made. This is done by first fully encrypting your information. It’s then locked away and rendered completely inaccessible without a specific decryption key.
The attackers may threaten to completely destroy the data if their demands are not met. These payments are to be sent via cryptocurrency or credit card. Cryptocurrency is a popular method as it’s incredibly difficult to trace, meaning most perpetrators are not prosecuted. Ransomware, however, has existed since the late 1980s, where payments were demanded to be sent via snail mail!
Detecting a Ransonware Threat
So, how does ransomware infect a device in your business in the first place? The most commonly used method today is through malicious spam (malspam). Malspam refers to emails that may contain attachments or links to websites that, once open or clicked, will affect your computer. Like malware, the email will try to appear legitimate, but you can flag them by poor or strange use of language. Scare tactics may be used — like saying account information has been breached or posing as a figure of authority. A newer form of ransomware cyber security threats, which was rife in 2016, is malvertising (malicious advertising). Malvertisng distributes malware without needing the user to do anything. In this scenario, users can be redirected to criminal servers without even clicking on an ad.
Avoiding a Ransomware Attack
The best way to avoid ransomware threats is to set up proper cyber-security measures in your business. This will ensure these emails or ads don’t pop up on employee computers and mobile devices in the first place. Educating the team about the signs of ransomware is also an easy, effective way of making sure these sorts or links and attachments are not clicked on.

The above points cover some common and often avoidable threats that you’re able to protect yourself and your employees from. They are, though, just the tip of the iceberg when it comes to cyber security threats. If you want delve further into cyber security, we explore the wonderful world of cyber security here.
Education is key and common-sense cyber security protocols will deter any successful phishing attempts and block most malware downloads. The Ponemon Institute, 2018, released the findings that an incident response plan, extensive use of encryption, and employee training are the top three cost-reducing factors when it comes to cybersecurity.
Cybercrime is costing the Australian economy up to 1 billion dollars annually in direct costs alone. Don’t let your business be another statistic. Stanfield IT specialise in cyber security, and we were named one of the Top 10 Cyber Security Providers for 2019.
Contact us today and learn about making your business as secure as possible from the threats of malware, phishing, data breaches, DDoS attack and botnets, and ransomware.
