Information security is a hot topic amongst all the IT experts these days, and they all tell you the same thing. Protect your information. Improve your information security. Prevent data breaches. Look both ways before crossing the street. Yawn… but seriously, it is super important.
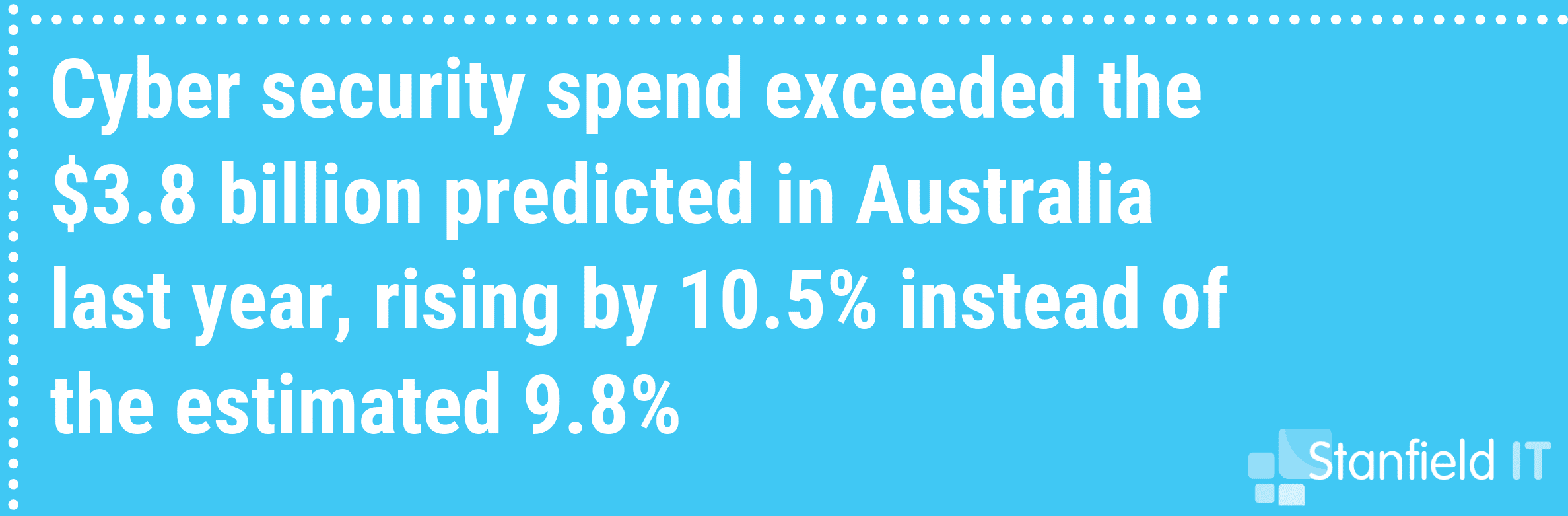
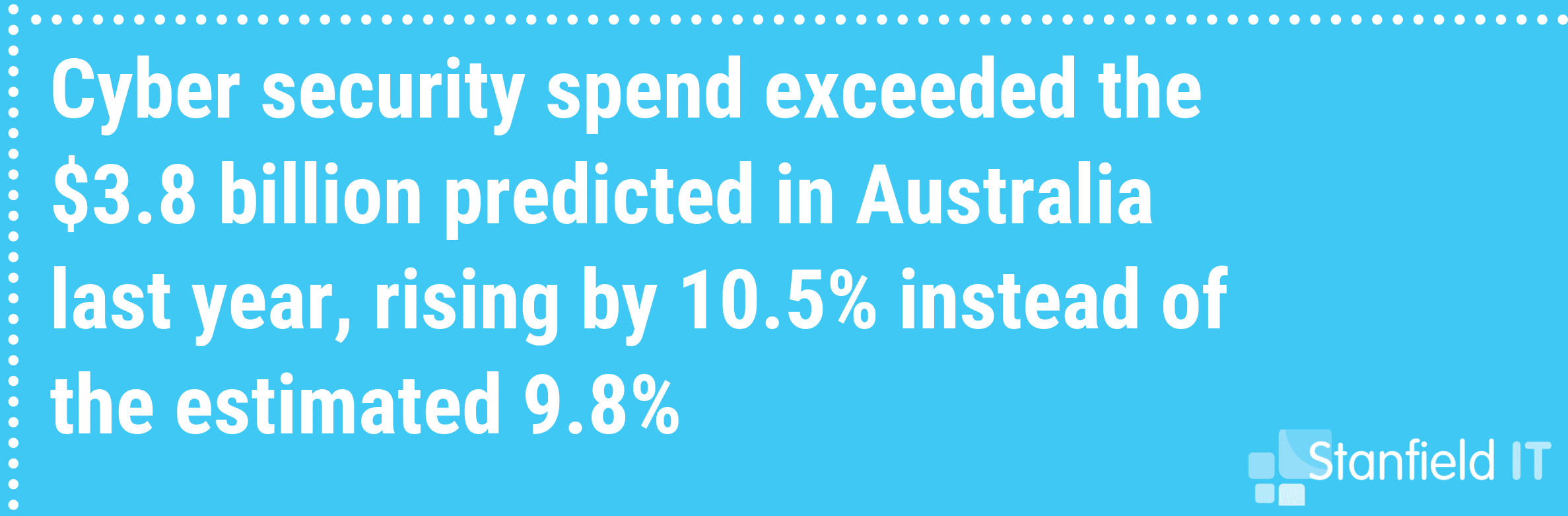
With over 500,000 Australian businesses falling victim to cyber attack last year, there is a great chance your business could be one of those statistics for 2019. So we’re here to provide you with a whole lot of excellent strategies you can implement to increase your information security, and protect your business.
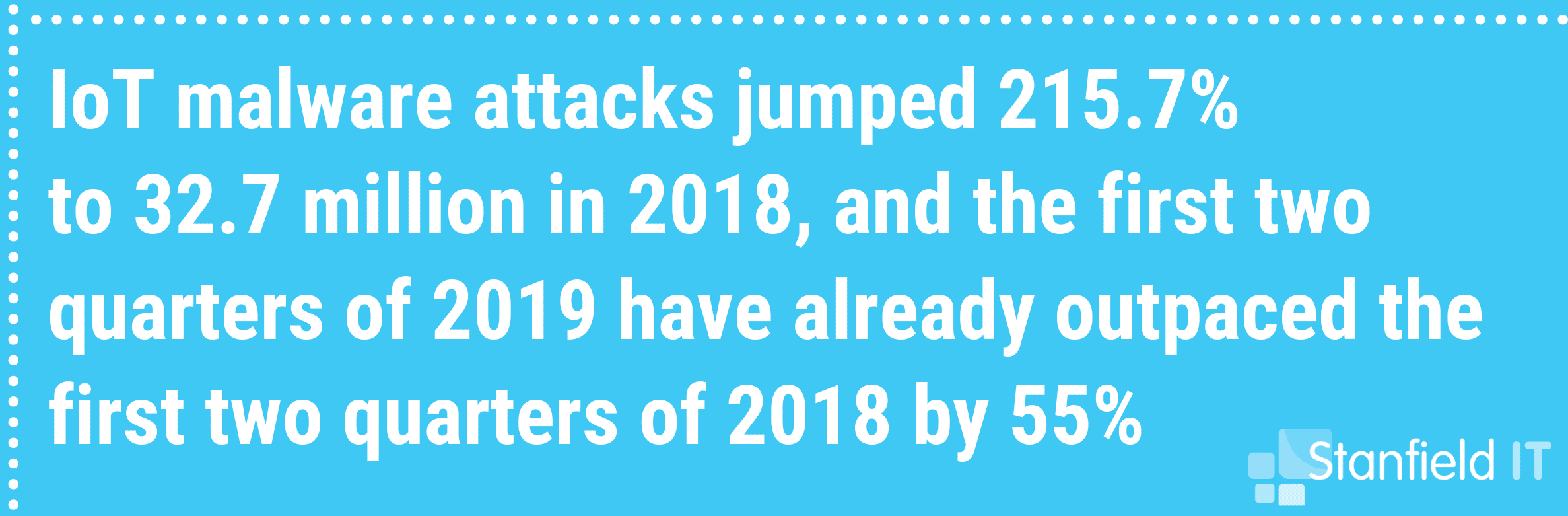
This year the Internet of Things (IoT) has exploded. Old devices are becoming smart, everything is talking to something, devices and software are turning up in places we never thought possible in recent years.
The latest Australian Notifiable Data Breaches scheme and the European GDPR now both at play businesses need to implement mitigation strategies more than ever.
What is Information Security?
Information security is a part of cyber security, but the two are not interchangeable. It refers more specifically to the actual processes and tools that focus on preventing sensitive information from falling into the wrong hands. This means that information security is ultimately about risk management.
What are the areas of risk?
- Protecting confidential and personal information
- Protecting company Intellectual Property
- Ensuring high-value systems are not breached, such as computers, servers, email platforms and networks — interruptions to these can bring the whole business to a grinding, expensive halt.
Let’s quickly look at the ways in which your information security is likely to be compromised:
7 Common Information Security Threats
1. Ransomware
Ransomware takes your data hostage in exchange for a ransom payment (usually demanded in cryptocurrency for anonymity). Without the decryption key, your information is completely inaccessible. The attacker will threaten to destroy or expose the data if their ransom demand is not met.
2. Phishing
Phishing attacks are the culprit for so many malware attacks. Malicious attacks disguised as trustworthy emails and links that entice you to enter your personal information. Voila, the dummy site now has your username and password — and you might not even realise.
3. Distribution and Denial of Service
A Distributed Denial of Service (otherwise known as DDoS) is an attack that essential floods your network with traffic until it can’t function. Your computer can be hijacked to participate in one of these attacks, and you wouldn’t even know it.
4. Scams
These refer to any type of fraud scheme that uses email, web sites, chat rooms or forums to present fraudulent solicitations to prospective victims. They are not always obvious and can range from dating scams to fake shopping websites and get-rich-quick offers.
5. Confidential Personally Identifiable Data Theft
A malware program that catches your data presents a huge risk to your information security. These are almost always introduced to the system through an email attachment or an unsafe download. Once installed, these programs comb your system and steal critical data that can leave you personally exposed.
6. Unauthorised Crypto-Mining
Similar to how the DDoS attack hijacks your system to provide computing power, attackers are utilising crypto-mining malware to exploit remote computers. They use your system’s processing power to mine cryptocurrency, which cripples your system and puts your information at risk.
7. Financial Theft
Whether through malware, or phishing, on your phone or computer — internet banking fraud can lead to having your money illegally withdrawn from your account to someone else. Despite the convenience and ease of mobile banking, attackers still focus on tricking victims directly to reveal confidential information.

50 Tips To Increase Your Information Security
We’ve put together 50 tips to increase your information security in your small-to-medium business, based on our own hands-on experience in our own business and that of our clients:
- Implement Multi-Factor Authentication
- Restrict Administrative Privileges
- Patch All Operating Systems
- Whitelist Your Trusted Applications
- Patch All Whitelisted Software
- Application Hardening
- Configure Microsoft Office Macro Settings
- Daily Backups
- Use a Password Manager
- Use a Next-Gen Firewall
- Restrict Access to Data
- Use AI Anti-Malware
- Conduct a Vulnerability Scan
- Cyber Security Audit
- Educate Your Team
- Implement a Framework
- Mobile Device Management
- Mobile Application Management
- Encrypt All Devices
- Enforce Strong Passwords
- Email Security
- VLANs
- ICT Policy
- Financial Transaction Protocols
- Physically Protect Equipment
- Scanning Email and Web Content
- Web Content Filtering
- Control Removable Storage
- Set up TLS Encryption
- Disable Local Admin Passwords
- Penetration Testing
- Block Access to Unnecessary Cloud Services
- Business Continuity Plan
- Server Snapshots
- Regularly Evaluate Permissions
- Avoid Public WiFi
- Guest WiFi
- Use Your Email Security Features
- Industry Guidelines
- Cyber Security Monitoring
- Incident Response Plan
- Keep Abreast Of Vulnerabilities
- VPN
- Use An Expert
- Hardware Security
- Network Segmentation
- Understand and Assess Risk
- Protect Your WiFi
- Secure your CMS
- Always Assume There is A Vulnerability
The first eights points are recommended by the Australian governments Cyber Security Center as essential to any business or organisation and should not be overlooked. These are called The Essential Eight.
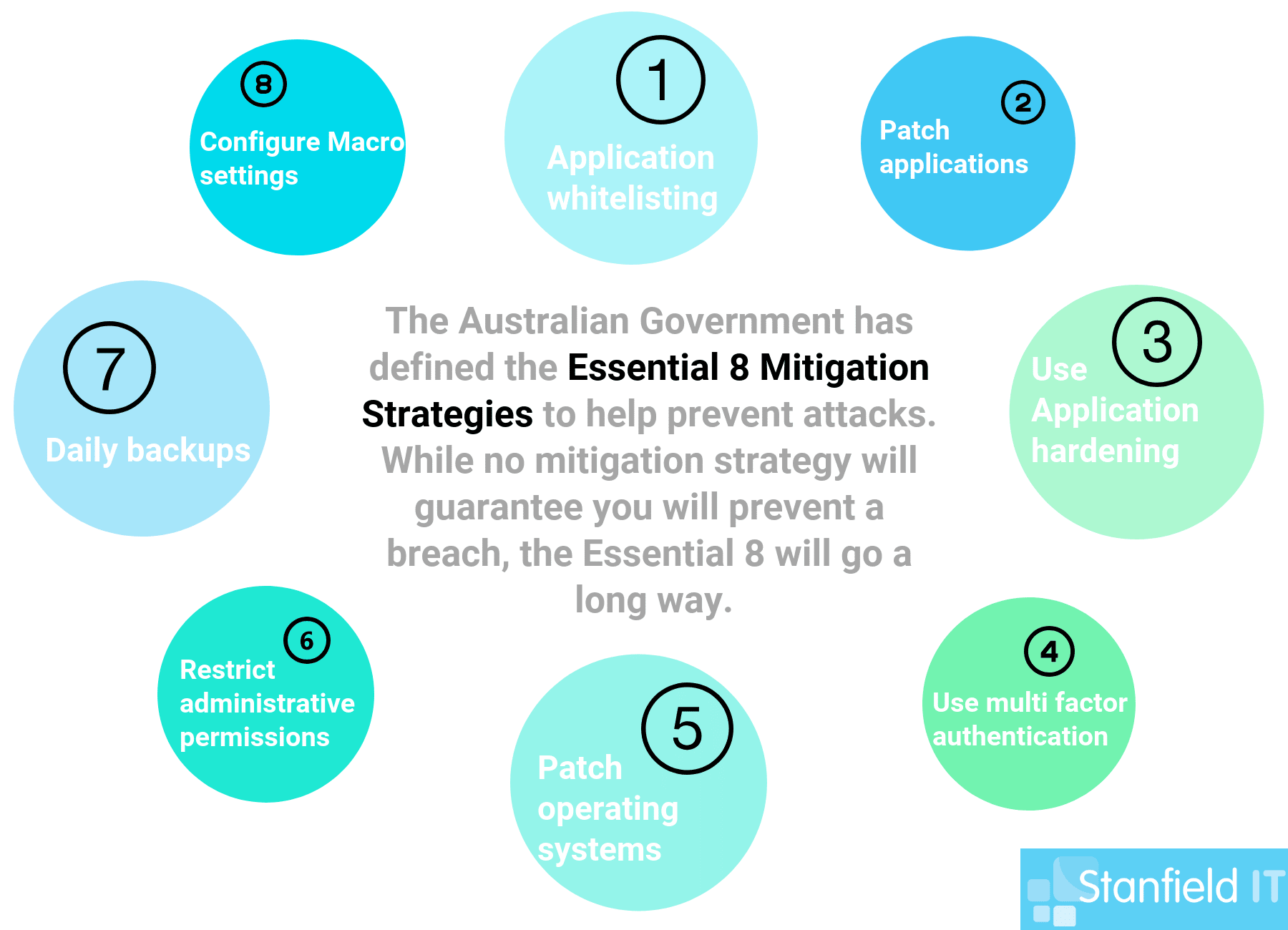
1. Implement Multi-Factor Authentication
Implement a multi-factor authentication system across all systems that can offer it. Seems like overkill? It’s really not. Just requiring a password to access accounts means you’re just one security measure away from your information being compromised.
We’ve discussed two-factor authentication previously, and it essentially comes down to the fact that:
Adding multi factor authentication is a simple additional layer of security that drastically reduces the chance for malicious opportunists to access your data.
Let’s look at some system examples that people should focus on and be at the top of your list when it come to MFA. These are:
- Internet banking
- Email platforms G Suite and Office 365
- Accounting and payroll packages
- ERP (enterprise resource planning) and CRM (customer relationship management)
- Any system storing confidential information, like servers or cloud-based storage solutions
If any of these are compromised, your business will severely suffer. To get the ball rolling on this, log in to each system and set up any default MFA processes.
If you are looking for a central way to manage it, look at Okta. They have a range of identity management solutions including single sign-on and multi-factor authentication. For your personal devices, consider Authy.

2. Restrict Administrative Privileges
Administrative accounts should be restricted to operating systems functions and relevant applications (that are required for work purposes). With administrative accounts restricted from internet access and emails, they are secure against phishing attempts and malware links.
If someone gets their hands on an administrative account, they could wreak an enormous amount of damage and access all the sensitive information.
You can make changes to your admin privileges, whether you’re running Windows or Mac OS. Here are some resources on how to get started yourself:
- Change Admin Roles in Windows 10
- Add or Remove Admin in Mac OS X
- Why Less Admin Privileges Are More Secure
3. Patch All Operating Systems
This means Windows, MacOS, iOS, Android and, yes, even Linux need to be patched. Don’t forget all devices on the network or cloud as well. Operating systems are written with the best of intentions, but unintended vulnerabilities in the code may not be discovered for some time after release.
Vulnerabilities are often discovered when an opportunistic villain exploits said vulnerability and everyone has to scramble to patch the OS. In other words, patch your system as these updates roll out―this will save you a lot of pain.
Read more about updates for Windows and Mac here:
4. Whitelist Your Trusted Applications
A whitelist of your approved applications ensures that no new or malicious software can execute or install. Any software that comes from outside of your ‘whitelist’ could be infected with malware, or be otherwise unsafe. Just like you give your house keys to trusted family members who are welcome to access your house, you lock it against any unwanted intruders.
Read more about implementing application control via these links:

5. Patch All Whitelisted Software
For the same reason we encourage you to update your operating systems, we advise you to keep your whitelisted applications up to date as well. These friendlies can turn foe if a vulnerability is found and exploited by malicious parties. Keep them up to date, and prevent a breach.
6. Application Hardening
Basically strip out unnecessary software and add-ons on your system computers and mobile devices to make applications more secure. Configure your web browsers to block ads and Flash (or uninstall it completely).
Applications like Flash and Java have a ridiculously bad history with security problems, so we advise you get rid of them completely if you have no need of them.
7. Configure Microsoft Office Macro Settings
This step probably seems a little out of place, but it’s an essential one. Microsoft Office macros can be used to deliver and execute malware on systems. So, we block Office from executing macros from the Internet and permit macros from trusted sources (or those with a digitally signed trusted certificate).
Learn how to configure, disable, and manage Macro setting here:
8. Daily Backups
If you have an incident where your data is compromised, corrupted or destroyed, you want to be able to access that information relatively quickly. Schedule daily, or frequent backups of new, important or critical data. You should test them on a regular basis and consider a retention period of at least three months so you can go back in time to recover lost files. Store multiple copies of your back up in different locations.
Read the specifics on backing up on Windows and Mac:

9. Use a Password Manager
The downside of having multiple passwords that fit the requirement of being long, complex and random is that it becomes incredibly difficult to remember them all. Enter: the password manager! A password manager stores your passwords securely by encrypting them and offers the ability to share them safely. When you want to disable their access, you can do so without needing to change the password. At Stanfield IT, we use the LastPass password manager. Some other suggested password managers you can use are:
10. Use a Next-Gen Firewall
A next-gen firewall is part of the third generation of firewall technology, meaning it combines a traditional firewall with more sophisticated functionalities for detecting and preventing intrusion. They generally include anti-malware and anti-virus that are continually upgraded as new threats are discovered.
Get started with next-gen firewall technology here:
11. Restrict Access to Data
Regularly evaluate your system and ensure that your staff only have access to the data and networks that they actually require to perform their job. The less people you have exposed to sensitive data, the less likely that such data is going to be compromised (either intentionally or accidentally).
Learn more about the specifics surrounding permissions on Windows and Mac here:
12. Use AI Anti-Malware
These malware detection programs use clever algorithms to immediately detect and contain any malware, often detecting intrusions before they take effect. There is some debate on whether it’s really AI, or just advanced machine learning, but the end result is the same — an anti-malware program that handles threats before you’re even aware of them. Just avoid the one called Skynet. Suggested tools to consider:
13. Conduct a Vulnerability Scan
Performing a vulnerability scan of your entire infrastructure will help to highlight any security weaknesses in your system. You can do it yourself as an individual using an entry-level scanner tool, or employ an IT expert who can use a more sophisticated enterprise-level product. Start here:
14. Cyber Security Audit
A cyber security audit should give you a clear idea of your problem areas and what issues you need to deal with regarding your information security. There are audit questionnaires you can use yourself to get an idea of where you stand. Or you can opt to take your business to an IT company that specialises in cyber security and ask them to take your security to the next level. Review our cyber security audit tips here:
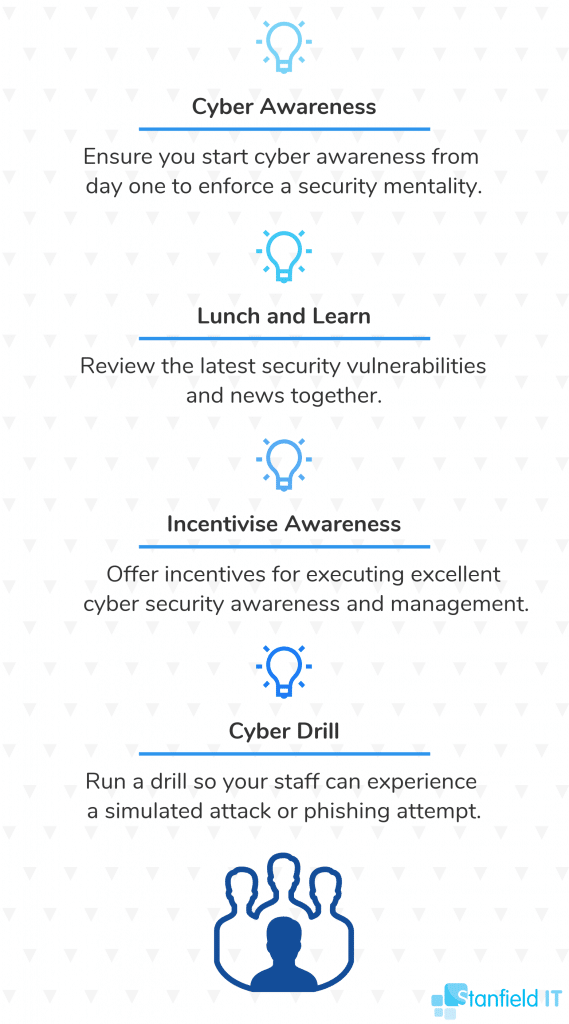
15. Educate Your Team
This is one strategy that doesn’t require any big spending, and we will always advocate for this. Ensure that your team understands the risks and gravity of information security — they will be your biggest defenders if they’re alert and aware. Teach your team to identify cyber risk so they make safe online choices. Suggestions to engage your team:
16. Implement a Framework
An IT security framework is a template of information security protocols you can implement on your system to minimise risk of incident and compromise. There are multiple frameworks to choose from, depending on your type of business and security needs — these can be confusingly technical, so don’t be afraid to reach out to an IT consultant for help. Review our list of frameworks linked above, or get started with these:
17. Mobile Device Management
Implement a mobile device management solution within your business. There are numerous MDM tools you can use, and many have their pros and cons — but ultimately they work to secure your company data, and your employee’s personal information.
A good MDM tool allows you to provide your staff with access to business apps and data on mobile devices without requiring individual device enrolment. Look at the endpoint management capabilities of the systems you already have, such as in G Suite or Office 365. If you need more refined control look at bold on products such as Microsoft Intune.
18. Mobile Application Management
Similar to, but not to be confused with mobile device management, MAM is a management tool that has evolved to suit a culture of BYOD (bring your own device) in the workplace. Instead of managing an entire device, mobile application management is about managing and controlling required apps on a personal device, where you control the permissions and security. Like with mobile device management, see Intune for more granular MAM.
19. Encrypt All Devices
All your devices should be encrypted — this means computers, mobile devices, hard drives and storage. Encrypting the devices means that your data is incomprehensible without a key. Basically, if someone gets access to your laptop or mobile, they can easily access files and data without encryption. If encrypted, your files are still protected in such an instance. See specific information on device encryption here:
- Device Encryption for Windows
- Data Encryption for Mac OS
- Encrypt your Android device
- Encrypt iPhone backups

20. Enforce Strong Passwords
Passwords are the key to your accounts, so why make it easy for others to guess or hack? Create a policy of strong passwords in your work place and enforce it. Ensure your staff create complex, random passwords to boost security and change them periodically. Tips for creating strong passwords:
- Use passphrases made up of at least four words that you can remember
- Don’t include any personal information or meaningful dates
- Review password etiquette from the government’s Stay Smart Online initiative
21. Email Security
We advise you to enable and enforce email security measures such as SPF (Sender Policy Framework), DKIM (Domain Keys Identified Mail), and DMARC (Domain Message Authentication Reporting and Conformance). These measures protect you by verifying email senders and recipients to prevent any malicious emails coming in or out. See below for more information:
- Set up SPF in Office 365
- SPF for G Suite
- How to use DKIM in Office 365
- DKIM for G Suite
- Using DMARC in Office 365
- DMARC for G Suite
22. VLANs
A VLAN is a group of devices that appear to be on the same local network despite their physical distribution. Hence the name “virtual local area network”. This drastically improves the security of such a network. VLANs also allow you to virtually segment devices or departments on different networks to improve security — you may have heard it referred to as ‘network segmentation’. As long as you have a VLAN-capable switch, you can do this:
23. ICT Policy
Ensuring that your company has an up-to-date ICT usage policy, and that it’s being enforced gives your team a good set of boundaries to work within that protect your business and your data. Have a look at some examples of ICT policies to help you kick start or amend your own policy.

24. Financial Transaction Protocols
Make sure that your company has a clearly defined set of policies and processes for transferring money and handling payments to reduce any risk of financial fraud or breach. Here are some useful resources:
25. Physically Protect Equipment
Seems simple enough, but it’s also important to physically protect and restrict access to your critical equipment as much as you need to restrict virtual access. Data can be accessed or compromised through physical access too! Some tips for creating a physically secure environment:
- If you have a dedicated server room, ensure it’s locked whenever not in use, and clear policy about who has access to the key or code.
- Set up surveillance in the event of unauthorised access
- Use rack mount servers as they are easier to secure.
- Any portable or vulnerable devices should be locked away.
- Shred or destroy unwanted printed documents that may contain sensitive information.
26. Scanning Email and Web Content
Set up automatic and dynamic scanning for email and web content with sandboxing to protect your system. Sandboxing isolates programs so they aren’t able to spread any potential issues to the rest of the network.
27. Web Content Filtering
Use your firewall to set up web content filtering. The filter works by identifying the origin or content of a web page based on rules you have defined. This can help you avoid visiting malicious pages. Content Filtering will significantly improve your security by blocking access to malicious or risky websites, utilise your policy-based controls and prevents malware download. Examples of Web Filtering tools:
28. Control Removable Storage
Control removable storage media and connected devices, which can easily carry or transmit malware to an unsuspecting or unprepared computer. Don’t allow anyone to just bring in their thumb drives willy-nilly! You can even disable drives so employees aren’t able to put information on removable media.
29. Setup TLS Encryption
More techno-babble, sorry. Apply TLS encryption to your email servers for added protection. TLS stands for Transport Layer Security, and is basically a cryptographic protocol that encrypts communication to make it secure!
30. Disable Local Admin Passwords
Ensure that you disable local admin passwords across all computers and servers — this ensures that administrative functions cannot be accessed anywhere and reduces the risk of compromise.

31. Penetration Testing
This is a step you probably want to engage after you’ve done your vulnerability scans and cyber security auditing. Penetration testing is a next level step to test how secure your system really is, what weaknesses and entry points there are. Make sure to only use an organisation that has been certified by CREST Australia (Council of Registered Ethical Security Testers).
32. Block Access to Unnecessary Cloud Services
Common sense tells us to reduce or remove access to any applications, processes or services that we don’t need. We saw this with application hardening and whitelisting. Cloud services fall under this rule too.
33. Business Continuity Plan

Having a business continuity plan in place means that in the event of a disaster (of any sort), your team is adequately prepared and knows what actions to take without hesitation. Keep a physical copy of the plan in a secure location.
34. Server Snapshots
Use virtualisation technology to create snapshots of your servers. Virtualisation technology works by creating a virtual version of a device (such as your server) for maximising your resources and safer information management. Some resources for virtualisation:
35. Regularly Evaluate Permissions
Make sure to conduct regular evaluations of who has permission to different systems in your network. This includes systems that have been opened with APIs. Due to staff turnover or evolving roles, permissions should be periodically updated and reviewed.
36. Avoid Public WiFi
If your team works remotely, or on the go, make sure that they don’t resort to using public WiFi. Public WiFi is inherently insecure, and puts your information at risk. Instead, provide them with portable connectivity they can use on the go.
37. Guest WiFi
Set up a WiFi specifically for guests that is separate from the one you use for work. The guest WiFi should have no access to your internal networks, so this way your guests have internet access but not access to your data.
38. Use Your Email Security Features
Your email platform will come with built-in security features, and we advise you to take full advantage of them! Email is such an easy, common target for cyber criminals since every other account you hold on the internet can pretty much be reset through your email. If they have access to your email, they can easily access other systems, or send malicious content to your contacts who won’t realise you’ve been hacked.
39. Industry Guidelines
Be sure you review any industry-specific guidelines as they frequently will have good tips and rules you can follow within your data management to keep things safe and reduce the risk of breaches. Review the industry-specific guidelines below:
40. Cyber Security Monitoring
With a cyber security monitoring system implemented, you’ll be able to consistently monitor critical systems and data. With this you’ll be able to know straight away if there’s any suspicious activity or data breach.
41. Incident Response Plan
An incident response plan gives your team a set of steps to follow to manage and mitigate any data breaches or other incidents. Tailor the response plan for data breaches and information security. If you’ve got a framework implemented, then it should also provide an incident response plan for you to follow. If not, then get that framework happening!
42. Keep Abreast Of Vulnerabilities
Subscribe to receive updates on any newly discovered vulnerabilities. Keeping yourself informed on threats, is a way to seriously reduce your risk. If you’re aware of the new threat, you’ll be on the ball to get it fixed as soon as a patch is released. Keep informed with the following links:
43. VPN
Using a VPN is a simple but thoroughly reliable security measure. It protects your network from being exposed to the network, or other unsafe networks by encrypting your information and providing a secure network of communication. You can set up a VPN software on Windows or your Mac OS. Alternatively, you can use your existing security solution such as FortiGate.

44. Use An Expert
At the end of the day, you can read all the tips, and watch all the tutorials — but there is no substitute for having an expert on hand. You pay an expert for their knowledge and expertise that they’ve accumulated through real experience. Find them, use them. Things to look for in a cyber security team:
- Do they have relevant experience? Review examples of their work if possible.
- Their first priority should be a cyber security audit/risk assessment — not just selling you a one-size-fits-all software solution.
- Will they communicate and be transparent with you?
- Can they provide training for your staff?
- Are they able to provide a tailored plan for your business?
45. Hardware Security
In contrast to anti-virus applications, hardware security describes physical hardware devices that provide vulnerability protection. Examples include hardware firewalls and hardware security modules. These devices provide an additional element of protection to your network.
46. Identity Management

Identity management is all about defining and managing the roles and privileges of your individual users on the network. How do you define who can access what? Have you separated customer identities from employee identities. Each individual should have one identity — this way you can monitor activity and immediately identify who performed what action.
47. Understand and Assess Risk
So much of the steps listed above come down to one thing: risk management. Once you understand information security and the risks that threaten it, you ironically reduce that risk. Being on the ball means you recognise threats and know how to prevent them.
48. Protect Your WiFi
This one is so obvious that its easy to miss. Protect your WiFi by ensuring it’s secure, encrypted and hidden so that your network is not waving a big ol’ flag to any passing hackers. Change the router password, use WPA2 encryption and keep the firmware up to date.
49. Secure your CMS
Whatever Content Management System (CMS) you’re using, there are likely ways to improve its security. So many CMS attacks happen through front-end login. Remove front-end login for anyone who needs to access your CMS (back-end access instead), change default admin accounts, and be wary of plugins.
50. Always Assume There is A Vulnerability
It’s never safe to assume you are 100% protected. That leads to complacence. Complacence leads to weaknesses. Which leads to the dark side, etc etc. Information security is about the journey, not the destination. You should be constantly evaluating, revising and updating your policies, software and permissions. Assume someone is always looking for that one tiny loophole in the system.
To Conclude…
Whew, that was a big list. If you made it all this way, you must have been really keen for some information security tips. Our team is even better to be perfectly honest, so it’s okay if you’re feeling bewildered about all the information coming at you. If you’re a bit concerned about the information security within your organisation, then please don’t hesitate to get in touch with our amazing team at Stanfield IT. This is what we do, and we’ll get you where you need to be.
Have a look at our case study here to see how we’ve assisted our clients in exactly this area.
