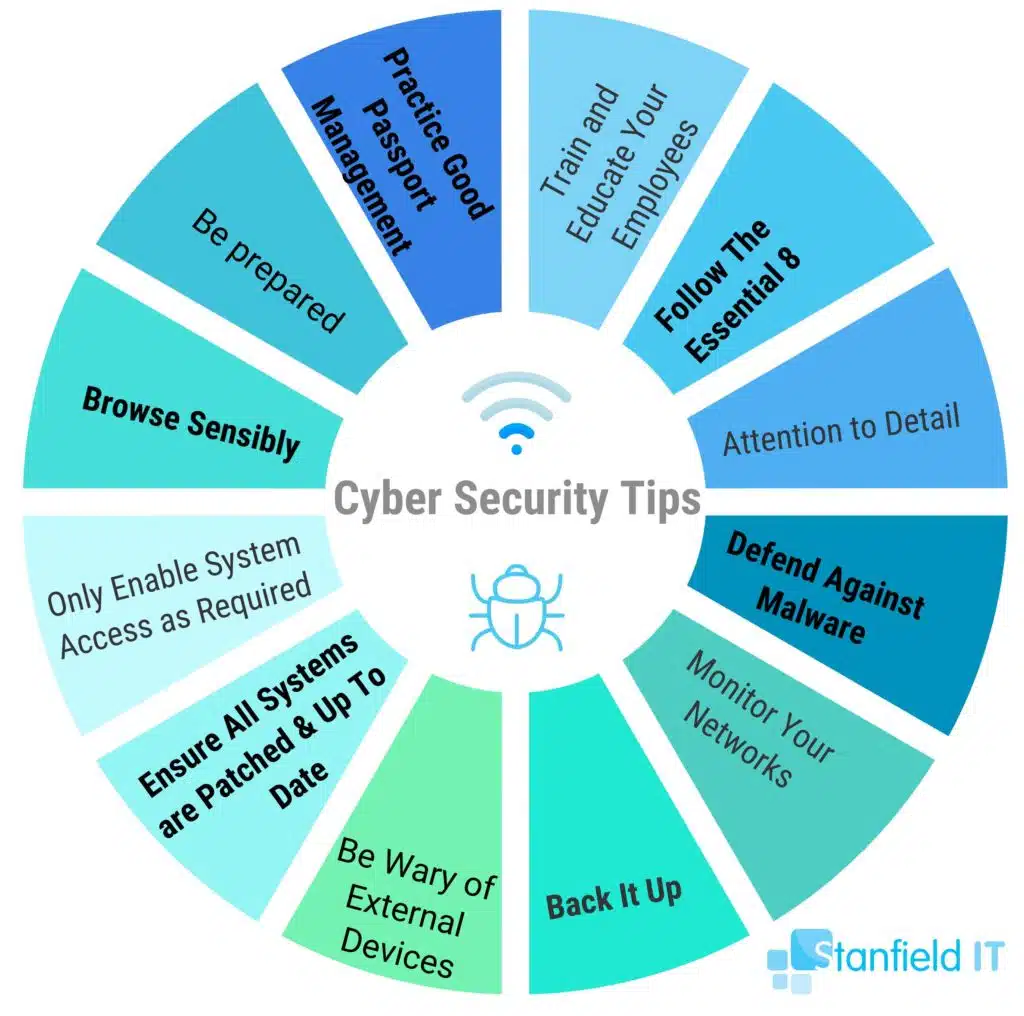
Got cyber security on your mind? So do we (and if you don’t we think you should!). To help you mitigate those cyber security woes, we’ve listed our top 12 most important cyber security tips. Enforcing these cyber security tips will set you on the right path to cyber resilience, minimising your risk of attack.
It’s important to use these steps as a starting point for locking down your cyber security. Because all businesses are exposed to different threats, you need to expand on these as you see fit. Check out our cyber security guide for more information.
Our 12 top tips will teach you the importance of regular security updates and evaluate your cyber security processes. This includes incident and recovery plans in case a breach does happen. These are the 12 cyber security tips we’re going to go through today:
Cyber Security Tip 1: Remember, It Could Happen To You!
The first and most important of our cyber security tips is to never assume you won’t be a target. Smaller companies will often have the mindset that their data isn’t important enough to hack. Small-to-medium businesses are attractive victims to hackers, as they typically won’t have the same level of defences as larger companies.
If your company has money or data, it has a bullseye on it just like any other larger company. Maybe even more so, since they assume you’ll be easier to infiltrate (let’s make sure such assumptions are incorrect!). Desirable data to hackers includes:
- Passwords
- Client information
- Sensitive email threads
Just to name a few.
Thinking it’ll never happen to me makes you complacent and likely to drop your guard. Always assume you are a target and that the internet trolls are out to get you. Take the time to know and understand your assets, including where a breach is most likely to occur. For example, client data in the health industry is often a target. Raise your cyber security awareness. And, you can even perform threat-modelling exercises and put practical protection measures in place.

Cyber Security Tip 2: Practice Good Password Management
There are a few simple ways to reduce the likelihood of your someone guessing your password:
- Make it strong
- Make it random
- Include upper and lower case letters
- Use symbols
Refrain from using the same password for multiple sites and accounts, even if it’s complex. Also avoid ever sharing your password with anyone, including a family member or close friend. Consider using a password management system.
Also use two-factor authentication (2FA) wherever possible, especially on internet-facing systems. 2FA can do wonders for your business’s cyber security. Even if a hacker has a password, they won’t obtain access to an account as a second level of identification is required. Ensure your employees follow the same protocols. The IT team―internal or external―should set up the password manager and 2FA on staff desktops and any other devices they use for work, including their own device if you have a BYOD (bring your own device) policy in place. This will ensure that, even if an employee has a weak or reused password, it won’t jeopardise company data. Periodically updating your passwords, at least every six months, is also a necessary measure to take to practice good password measurement.
Cyber Security Tip 3: Practice Sensible Internet Browsing (AKA Don’t Click the Dodgy Links!)
Be aware of safe sites and links, learn to recognise phishing attempts in emails (basically, never click the link), and ensure your employees practice safe browsing, too. Simple things like don’t share your password online should be education points. Employers and employees should be suspicious of potential malware at all times, as opposed to only considering the presence of malware when there are obvious signs.
Always remember to be careful what you click. Harmful links may appear via email, in pop-ups, or as unexpected attachments. Never let your employees freely download software onto their work computer. This could lead to downloading software from untrusted sources that host malware, compromising the device without anyone realising it’s happening.

Cyber Security Tip 4: Enable System Access Only As Required
You should regularly evaluate system access and ensure staff only have access to the data or networks required for their job. Whenever there is staff turnover, remove the ex-employee’s access. Mobile application management (MAM) will ensure that previous employees will not be able to access company data and accounts on their own device(s) after they have left the business. Take a look at Intune for a great MAM and mobile device management (MDM) tool. Or read our guide on the best Intune features.
A good rule to follow is to only allow staff the minimum amount of access they need, never the maximum. Also don’t allow for blanket access across teams or departments, unless every member needs this access to do their job. Make sure that you restrict administrative privileges, just giving these to the minimum amount of people you need to. User accounts with these privileges are attractive targets for cybercrime, as they hold a high level of system access. Minimising privileges makes it more difficult for an adversary to spread or hide its existence.
Cyber Security Tip 5: Be Wary of External Devices
With a culture of BYOD becoming more prevalent, an important pick from our cybersecurity top tips is to be sure you’re screening all devices before they connect to your network. Laptops, mobiles, and USB flash drives can all carry malware and infect your system(s). Consider MDM or MAM to ensure your employees can only access company data on secure networks. This will also allow company apps and data to be remotely wiped from a device if it’s compromised.
This is relevant to company-owned devices, too. Corporate mobile devices—whether’s a laptop, mobile, or tablet—contain locally saved sensitive data and are connected to the company’s internal network through VPNs and workspace browsers. This can give the attacker a means to obtain direct access to your business if security measures aren’t in place. Think of mobile devices as an extension of the network perimeter, but easier to lose or steal.

Cyber Security Tip 6: Back It Up
Back up all your networks and systems at regular intervals, whether it’s a cloud-based or physical server. This should be standard practice anyway, but ensure your incident response plan includes it, too, in case things go awry. You should always store the backup data separate from the main server.
If there is a cyber attack, you might have to completely wipe a device or server. This is particularly the case in ransomware attacks, which are rising. If you store backups offline and in multiple locations, infected systems won’t be able to access it. If a breach occurred, regularly perform tests to ensure that an infected system cannot access your data. Also make sure you regularly test that backups are effective and that your data restoration procedures are working.
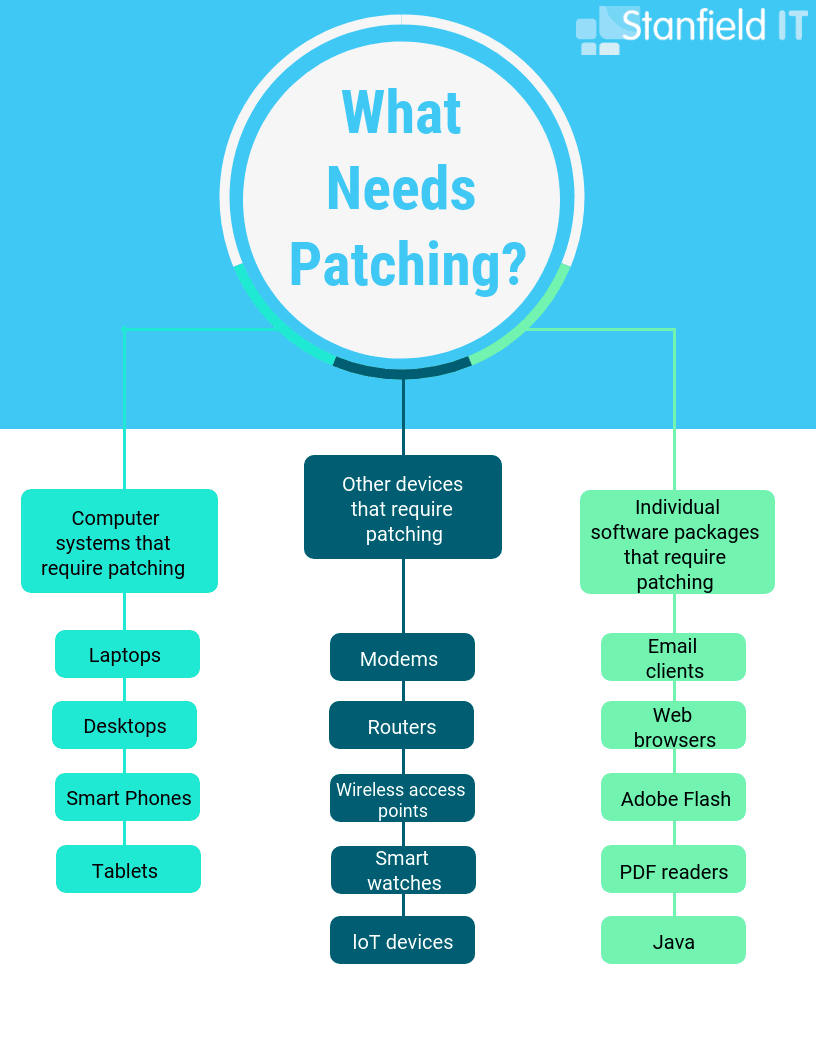
Cyber Security Tip 7: Patch and Update All Systems
Always keep your systems securely figured and updated. Device and software manufacturers release software patches to correct flaws in the software’s previous version, which includes cybersecurity vulnerabilities. Under the same premises, installing the latest software updates is equally as important and as easy to do. Leaving your system on older versions will increase the likelihood of criminal’s targeting weaknesses.
Insecurely configured environments let your system become an easy target for malicious activity, as it’s easier to obtain unauthorised access. Installing the latest patches and updates on your devices is an important habit to get into. You can do this through scheduling update checks, turning on automatic updates, and using web browsers (such as Chrome) that receive frequent, automatic security updates.
Cyber Security Tip 8: Monitor and Test your Networks
Constantly monitoring and testing your networks and devices gives you a better chance if being the first to notice any suspicious activity. If something seems out of the ordinary, it could be a sign that the system has been compromised. Understanding how the activity should normally look helps you immediately notice red flags pertaining to potential attacks. You should think about how putting a Security Operations Centre (SOC) to act as ‘virtual security guards’ can help effectively prevent, detect, and respond to a malicious attack.
You should also conduct penetration tests and vulnerability assessments. They’ll detect any infrastructure weaknesses that could result in system vulnerabilities. If you have SOC in place, use these results to determine your detection and response capabilities.
Cyber Security Tip 9: Use Technology and Education to Defend Against Malware
Preventative measures are, of course, the best way to stop a cyberattack from happening altogether. They can save your company a lot of time and money! Aim for your business to have defences that make it harder for a malware attack to infiltrate your system. Measures should also be in place so that you can easily isolate a breach. This means if one computer gets infected the malware is blocked from spreading.
There are a range of precautions that can be taken―email security, firewalls, and ad- and script-blockers can block malicious senders and attachments. A firewall is a software- or hardware-based application that will prevent malicious attacks from various types of malware, such as hackers, worms, ransomware, and viruses that try to steal information. A crucial way of defending against malware is to educate and train your employees on cyber security. In doing so, you’re proactively preventing the initial downloading and execution of ransomware, malware, and phishing links. Additionally, in our cyber security services, we offer staff training so that you are confident in your own cyber security knowledge and the preventative measures to take.
Cyber Security Tip 10: Follow The Essential Eight
ACSC’s Essential Eight strategies are recommended by the Attorney General’s Department. Implementing the strategies relevant to your company is a great step to mitigate cyber threats. Other frameworks and strategies are also effective, which we delve into in our blog covering The 7 Most Common IT Security Framework Options in Australia.
Of these, The Essential Eight are the most practical starting point for businesses to improve their cyber resilience. They comprise of eight mitigation strategies that act as a baseline of protection against cybersecurity threats. These eight strategies cover: application whitelisting, patching applications, configuring macro settings, user application hardening, restricting administrative privileges, patching operating systems, multi-factor authentication, and daily backups. The Essential Eight are designed so that they’re customisable to your business’s risk profile and the adversaries that are of the most threat to your business.

Cyber Security Tip 11: Train and Educate Your Employees
The weakest part of any business’s cyber security solution are humans. It doesn’t matter how costly or effective your defensive technology is. If one person lets their guard down or is careless, it can have terrible repercussions. Unfortunately, it just takes one click of an unfamiliar link or attachment for a cyber attack to begin on one employee’s computer and, potentially, your whole network. There are measures you can take to lesson the risk your own employees pose to your business’s cyber security: education and awareness.
Engaging cyber security experts to conduct workplace training on how to prevent and recognise a breach makes all the difference. Even if it seems like common sense, it important to go over what to look out for when it comes to malware, ransomware, botnets, phishing, and data breaches.
Cyber Security Tip 12: Be prepared and Have an Incident Response Plan Ready
No matter how many precautions you’ve put in place to try to mitigate a cyber security attack from successfully infiltrating your business, you can never be fully safe from threats—they’re always evolving and morphing. Consequently, you should have an incident response plan in place so that, if an event takes place, you have the means to hastily stop, contain, and control the incident.
Your incident response plan will usually be created by your IT team and incident response team. These are the people responsible for taking charge following a cyber-security breach. This team of people will be been given particular roles that will come into effect during an incident―they will be able to carry out the incident response plan quickly and effectively. You can find out more about incident response plan’s in our Definitive Cyber Security Guide for Small-to-Medium Businesses.
As well as roles and responsibilities for incident response team members, an incident response plan can also include: a business continuity plan, tools/technology/resources that should be in place, network/data recover processes, and internal/external communications that should take place.
What’s Next?
You should frequently evaluate your networks and look for ways to improve system security, whether it’s through employee education, changing and upgrading passwords, patching software, updating incident response plans, or installing antivirus software. These cyber security top tips don’t cover everything, and there are a myriad of ways to protect your business that mostly don’t require an in depth knowledge of cyber security technicalities or scouring the deep web for a hacker to penetrate your firewall.
Anyone with the most basic computer knowledge can learn the fundamental steps to keep their network and data secure from outside attacks, and in the long run save yourself the financial drain and headache that follows from any breaches. If you’re still not sure about how to tackle your cyber security, check out our Cyber Security Guide for small to medium businesses or contact us directly. Good luck!

