Protecting your company data can be one of the most daunting parts of running a business. This includes personal data of employees, clients, and customers. We’re here to break down the different advice and approaches about data security, including complying with regulations, that may be coming at you from all angles. You’ll be well on your way to implementing a proper, effective IT security framework.
To help you navigate your business through the processes and protocols surrounding cyber security frameworks, we have put together this easy-to-digest guide that covers the Seven Most Common IT Security Framework Options in Australia.

What is an IT Security Framework?
An IT Security Framework is a set of guidelines or a template that outlines policies and procedures you can use in your workplace. These policies and procedures will let you establish and maintain data security strategies. When you apply a framework to your business and cyber security protocols your security perimeter will be protected and the risk of attack minimised.
There are many different organisations that can offer you a solid IT security framework for your business. Below we’ve provided an overview of outstanding templates that can be used for your own IT security framework.
Most of the listed IT security frameworks focus on a risk-management approach. Consequently, they’re easily adaptable to match your needs and can be applied to target the specific risks that threaten your IT security.
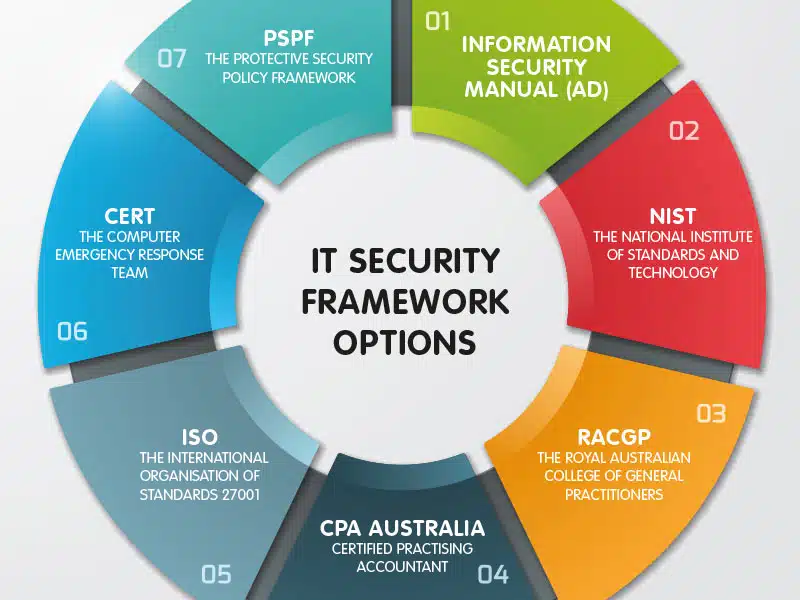
IT Security Framework Options in Australia
Australian Signals Directorate (ASD)
The ASD is an agency within the Australian government based in Canberra. It’s responsible for cyber welfare and information security, as well as foreign signals intelligence and supporting military operations. The first two apply to us. The ASD’s cyber security division is known as the Australian Cyber Security Centre (ACSC). The ACSC provides information, advice, and assistance to prevent and combat cyber security threats in public and private sectors.
Who are ASD standards aimed at?
The Australian Signals Directorate has published the Information Security Manual (ISM) for government agencies. The ISM is intended for Chief Information Security Officers (CISOs), Chief Information Officers (CIOs), cyber security professionals, and information technology managers. A variety of industries where cyber-security measures need to be implemented can use the ISM. This IT security framework focuses on minimising risks and exposure as a general rule. The ISM can be used across industries as the tactics are appropriate in broad contexts.
What cyber-security approach does ASD use?
The ASD applies a risk-based approach to cyber security that draws from the risk-management framework of the National Institute of Standards and Technology (NIST). They have published the manual across several documents. These include an outline for each standard, so you can quickly determine which one will be most relevant for your industry. Consistent updates of the manual keep it in accordance with the Intelligence Services Act 2001. It’s a fantastic resource to base your workplace information security framework on. Four key activities make up the cyber security principles within the ASD: govern, protect, detect, and respond. To effectively implement ASD standards, you should consider which guidelines are relevant to each of the systems within your organisation and apply them accordingly.
National Institute of Standards and Technology (NIST)
The National Institute of Standards and Technology is the US agency for industry standardisation and measurements. NIST has an overarching mission covering all of their sectors, including its cyber security program. This mission aims to push the US in its innovation and industrial competitiveness by researching and developing ways to enhance economic security and thus improve national quality of life.
Who is NIST standards aimed at?
The NIST framework provides voluntary guidance to organisations in the USA so that they can effectively manage and reduce their cyber security risks. This then helps to secure the country as a whole. The framework can also be universally applied, which is why they make our list. The framework acts as a ‘common language’ that people with different levels of experience in cyber security can be comprehend and implement. NIST is accountable for providing small businesses with consistent, clear, concise, and actionable resources for preventing cyber security breaches. This makes it a great framework for smaller Australian businesses to look towards when choosing a cyber security framework to follow.
What cyber-security approach does NIST use?
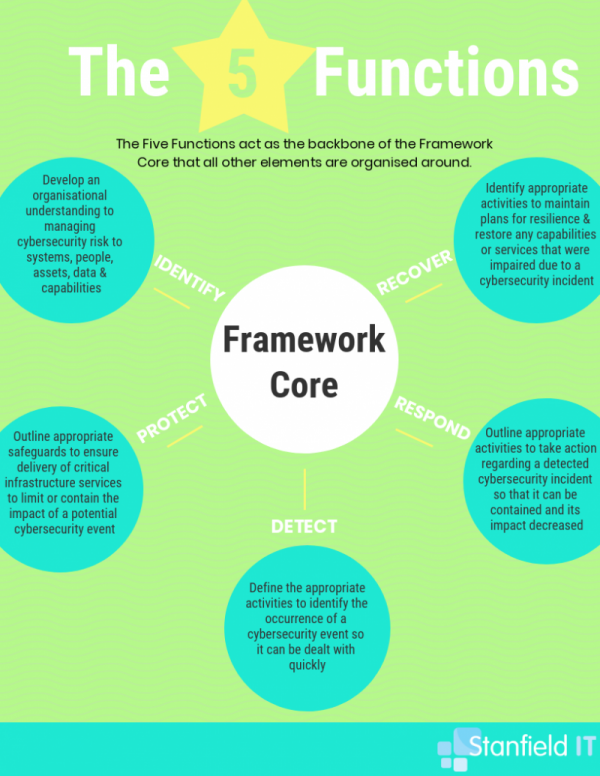
NIST’s cyber security framework adopts a practical, risk-management approach, comprised of three parts. Between them these cover industry standards, guidelines, cyber security activities, as well as the greater context for how an organisation should view cyber security risks. This framework uses five functions to explain how to deal with cyber security threats ― from prevention through to recovery. These five functions represent the five primary pillars of creating a successful cyber security strategy for your business or workplace.
The Royal Australian College of General Practitioners (RACGP)
Who are RACGP?
The RACGP is the biggest general practice organisation in Australia, representing over 40,000 urban and rural GPs. Its activities have a strategic focus that centre around collegiality; education and training for general practice; and innovation and policy for general practice.
Who are RACGP standards aimed at?
The Royal Australian College of General Practitioners has a set of standards and guidelines they’ve published as their own endorsed IT security framework. Healthcare is a high-risk industry for cyber security attacks due to the sensitivity of clinic and patient information. You can learn more about healthcare information security frameworks in our Healthcare Cyber Security blog.
What cyber-security approach does RACGP use?
Businesses handling healthcare and patient information are the target audience for RACGP cyber security standards. This set of standards doesn’t only focus on risk assessment. RACGP’s standards also go over managing availability of information with backup processes, business continuity, recovery planning, and access management.
CPA Australia
Who are CPA Australia?
CPA Australia stands as one of the largest accounting bodies in the world. As of the end of December 2018, global membership has soured to just short of 165k members. CPA Australia aims to make a globally connected world where trusted and valued business professionals enhance their communities no matter what side of the world they’re on.
CPA Australia’s intended audience are higher-ups and IT specialists in the finance sector. This includes both public organisations or smaller, privately run businesses. The information packages CPA Australia have available surrounding the topic of cyber security, however, can be implemented effectively across industries.
What cyber-security approach does CPA Australia use?
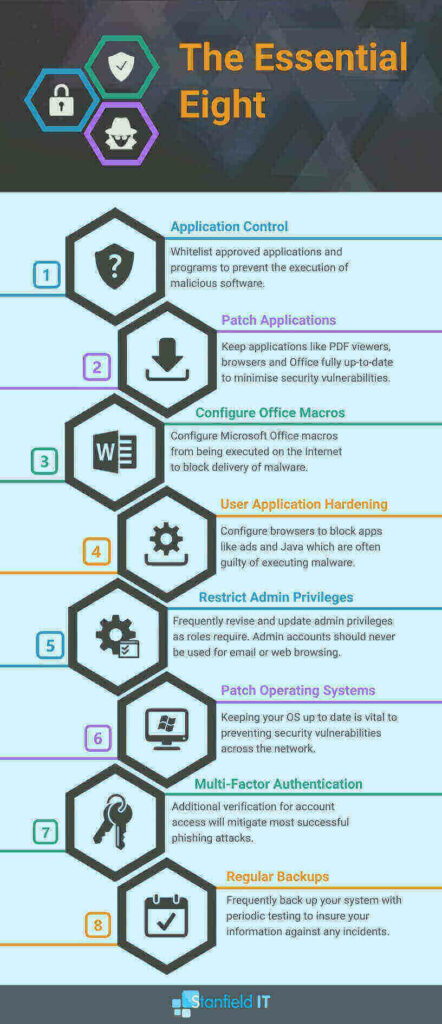
CPA has built their IT security framework around securing information and system management in order to protect their client’s sensitive information. They’ve published an array of articles, and even webinars, focusing on the best ways to secure and protect this information. Their document IT checklist covers the whole range of topics on IT system management and cyber security. This focuses on a similar approach to the ACSC’s ‘Essential Eight’ steps for security management.
The Essential Eight are crucial mitigation strategies that, if followed, can greatly assist organisations with their cyber security resilience. Organisations use them as a baseline for cyber security strategies to make a breach less likely to happen in the first place. You can find out more about The Essential Eight via our Healthcare Cyber Security Blog.
International Organization for Standardization (ISO)
Who are ISO?
ISO is a global not-for-profit organisation based in Geneva, Switzerland. It develops and publishes a huge range of standards. This includes those for information technology, which cyber security falls under. ISO has 162 members, each representing the country they’re from. Standing as the largest developer and publisher of standards in the world, ISO acts as a medium for discussion and eventual agreement between individual standards developers. ISO has the goal of positive collaboration and standardisation. Developers can share research and findings with their global associates, meaning advancements can be implemented worldwide.
Who are ISO standards aimed at?
As you would suspect from the global-standardisation goals of ISO, their cyber security frameworks don’t discriminate between industry types, sizes, and locations. While nothing can be one-size-fits-all when it comes to cyber security strategies, ISO have created accessible, user-friendly standards to follow when securing your company information and data from attack.
What cyber-security approach does ISO use?
ISO has an established IT security framework titled ISO 27001 that covers all aspects of information security frameworks from establishing a management system through to implementation, maintenance, and improvement. It emphasises the need for integrating cyber security management across the board of your business, not just within the IT department.
Computer Emergency Response Team Australia (CERT Australia)
Who are CERT Australia?
CERT Australia is colloquially called ‘the CERT,’ so we’re sticking with that nickname here. The CERT is Australia’s national computer emergency response team, based in Canberra and Brisbane. If a cyber security issues is affecting a major Australian business, the CERT is who they turn to. It’s also part of the Australian Cyber Security Centre, which works closely alongside the Australian Security Intelligence Organisation (ASIO), the Australian Federal Police (AFP), the Australian Crime Commission (ACC) and the Australian Signals Directorate (ASD). The CERT also has a close relationship with international counterparts, making it informed and well connected when it comes to cyber security on a global scale.
Who are CERT Australia standards aimed at?
The CERT’s standards are aimed at large-scale businesses, organisations, and not-for-profits in Australia. They give critical advice and support to owners and operators of Australia’s critical infrastructure and systems. These include: banking and finance, communications, energy, resources, transport, and water. A data breach in these wide-scale, valuable industries could have extremely damaging effects to Australia’s economy, citizens, defence, and security. The CERT stands as a critical part of large-scale cyber security control in Australia.
What cyber-security approach does CERT Australia use?
The CERT provides advice, guidelines, and support for mitigating and managing cyber incidents. Their IT security framework includes a remote-access protocol that you can implement into your own IT security framework; a guide to developing an incident response plan; and a document on the top control systems tips.

The Protective Security Policy Framework (PSPF)
What is the PSPF?
The PSPF articulates government security policy so that entities of the Australian Government can protect their people’s information and assets ― whether in Australia or abroad. It provides guidance to these entities so that the policy can be effectively implemented across security governance, personnel security, physical security, and information security framework divisions.
Who are PSPF standards aimed at?
The Protective Security Policy Framework is designed to protect assets and information. Their IT security framework focuses mostly on security protocols and information-security management. The Australian government developed these protocols for governmental agencies, but they offer the tools and guidelines that can be used by a private organisation.
What cyber-security approach does PSPF use?
PSPF standards aim to create a positive culture around security and are distributed with a security-risk-management approach. They consist of five fundamental principles that apply across all areas of security that can be used universally. They also include four outcomes, which outline the desired end-state government results the government aims to achieve. Lastly, there are 16 core requirements articulating what entities must do to achieve these desired outcomes. These make up a standardised approach to delivering security measures across government. The PSPF also provides guidance on how these requirements should be delivered.

Your IT security framework is the moat and fortress safeguarding your information, networks, and business from cyber attack. These frameworks provide you with everything you need to be compliant with cyber security standards. All the information you need to apply the standards are at your fingertips, so you’re not left grasping to figure out what you need to do. Whether you choose to implement one of these as your own IT security frameworks or choose to mix and match protocols and policies to make your own personalised IT security framework is up to you, but either way you are making the choice to protect your business in the best way possible.
To work out the best IT Security Framework for your business or to find out more chat with the team at Stanfield IT.