February 2018 saw the introduction of the new Notifiable Data Breaches Scheme. Since then, healthcare cyber security has been a top priority for healthcare practices. Over the last two years, there has been a drastic rise in ransomware attacks on computer systems within the healthcare industry. This has resulted in avoidable breaches to patient healthcare information security in practices. Some attacks have brought hospitals to a standstill for days and put the confidentiality of patient information at risk. This has called for healthcare organisations to take a serious look at their cyber security and assess what measures they have in place to prevent such attacks in the future. Let’s explore why healthcare cyber security is such a growing problem in Australia and the steps you can take to minimise risks.
Why is Healthcare an easy target?
The healthcare industry have become an easy target for attacks due to the inattentiveness of the industry regarding healthcare cyber security. It’s not just hearsay. In the last quarter (with reference to statistics from April–June 2019), health service providers made up 19% off all reported data breaches — topping the list. This was followed by finance, legal, accounting and management services, education, and retail. 50% of these healthcare information security breaches resulted from malicious or criminal attacks. Healthcare is a target for cyber crimes due to the:
Number of users
The vast amount of staff that regularly use the system provides many “weak links” and entrances. Emails between the staff being easily compromised are one example of this. Insecure machines or devices on the network can also provide a way in for hackers.
Education and information
It’s only recently that education and information for healthcare employees have become commonplace. Many healthcare practices and organisations need to embrace workplace education around cyber security. Regularly educating employees of the possible risks and safe practices of cyber security is a must. Knowledge of entrance tactics and how to protect themselves while in the system could prevent attacks and help keep staff vigilant.
Constant automation
The forever changing automation and updating of computer systems within the industry has improved efficiency. However, it has caused security measures to fall behind. Keeping the cyber security measures up to date helps to prevent easy access points for hackers.
Gaps in Security
Staff mobile phones may not have any security measures, even if they’re accessing work emails, etc, on these devices. Just like in offices, all devices that staff use to access work files, data, and programs need to be protected. Using a pay-per-user subscription, like Intune, can also be a fantastic way to tighten security across all devices that access practice information. Ensuring work phones are not doubling as personal phones can also be a necessary step to take in the healthcare sector.
Easy Money
Hackers aim to exploit easy targets who are willing to pay the most amount of money. The Notifiable Data Breaches Scheme ensures that personal information held by healthcare practices fall under strict legislative rules.
The industry needs to take a preventative approach to their healthcare information security and tackle the problem from all angles. In many cases, there is no solid plan in place for the prevention or recovery from these attacks. But it’s not just the healthcare industry that needs to take cyber security more seriously. Keep on reading no matter what sector you work in, as cyber security is important in any organisation. You can also learn about the different types of security threats here: The 5 Most Common Cyber Security Threats.
Understand what the Data Breaches Scheme means for you
Privacy Act
The Notifiable Data Breaches scheme falls under the Privacy Act (Part IIIC). It applies to entities that have an obligation under APP 11 of the Privacy Act to protect the personal information they hold. Private sector healthcare providers must ‘notify individuals and the Commissioner about data breaches that are likely to cause serious harm.’ Remember that the size of the healthcare practice doesn’t matter. Even the smallest private practices are considered an APP entity and fall under the Privacy Act. They still hold health information about individuals — extremely confidential information which is at a high risk of being compromised.
Legislation
An amendment of the Privacy Act 1988, the Notifiable Data Breaches scheme ‘effectively mandates a reporting and notification process that the OAIC had previously recommended as best practice.’ As an APP entity, the health care providers must comply with the NDB scheme. Incompetence and recklessness when it comes to IT controls that result in a breach of confidentiality may incur one or more administrative sanctions for the breach of the Code. This even covers just having insufficient controls or a reckless approach to healthcare information security. There’s an expectation that organisations create a data breach response plan. A team of people within the organisation should have roles within this plan and update it as necessary.
Fines
Breaching the guidelines set in the NDBS can result in hefty fines of up to $1.8m. Breaches include not notifying the affected individual/s of the data breach, not recommending steps for the affected individual/s to take to respond to the breach and protect their data, and failing to notify the Australian Information Commissioner.
These three indicators let you know whether an incident needs to be reported to the affected individual/s and commissioner:
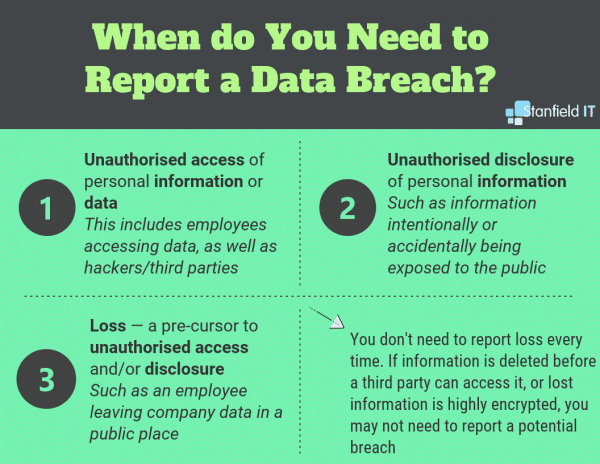
Following Industry Best Practice
RACGP
Recommendations in the Royal Australian College of General Practitioners (RACGP) can be followed to avoid and handle healthcare data breaches. These don’t just indicate the importance of healthcare information security within the organisation. They also highlight that education surrounding healthcare cyber security is an essential ingredient to practice management. Without communicating the importance of managing security risks, and the implications of breaches for both the practice and those affected, staff won’t understand the gravity of the risks of data breaches within the healthcare sector.
The RACGP outlines that healthcare information security is not just up to the higher-ups in the practice or organisation. Every employee has the responsibility to follow information security processes and protect practice and patient information. Each practice should develop an information security governance framework. This will ensure the team can hit the ground running if there is risk of a data breach. Allocate information security roles and responsibilities to specific team members, with everyone aware of their responsibilities. This framework needs to consider the capabilities of the practice and the legal and professional requirements for the protection of information. Under the Australian Privacy Principles, AAP 11 requires that reasonable steps are taken to protect personal data from misuse, interference, loss, unauthorised access, modifications or disclosure.
Managing access to the practice’s or healthcare organisations systems and data will reduce security risks. This means allowing each staff member access to the minimum amount of data that their need to be able to do their job, as opposed to giving across-the-board access to databases. This helps to protect your practice’s or organisation’s data by limiting the risk of data being breached in the first place. Separating your clinical data and website/business data also contains the risk of data exposure across the entire system.
The Essential Eight
The Essential Eight are a list of essential mitigation strategies that help organisations improve their cyber resilience. These can be used as a baseline, where practicable, for your organisation’s healthcare cyber security strategies. The Essential Eight make it harder for adversaries to compromise systems and can save you the time, money, and effort of having to deal with a cybersecurity incident.
Before you dive into implementing The Essential Eight in your workplace, you should identify which systems require protection, what kind of breaches are most likely to become a threat and the level of protection that is required.
Application whitelisting
Use whitelist-approved and trusted programs to prevent the execution of unapproved or malicious programs. This includes all executables (.exe), DLLs, scripts (Windows Script Host, PowerShell and HTA), and installers (.msi).
Patching applications
Perform regular patching/updating of applications in your system. This includes, but is not limited to: Microsoft Office, PDF readers, Java, Flash and Web Browsers. Vulnerabilities in old versions or unpatched software are often the vector for an adversary to gain control over your system.
Office macros
Configure Microsoft Office products to block the execution of untrusted macros. Only allow macros to run from documents in a trusted location with controlled write access, or only allow digitally-signed macros (by a trusted certificate) to be used.
Harden user applications
Applications that have the ability to perform unwanted or potentially vulnerable actions must be controlled tightly. Web browsers should be configured by default to block Flash, advertising, and the Java runtime plug-ins.
Restricting administrative privilege
Restrict administrative privilege for operating systems and applications based on what the specific user needs to access. Consistently review user access, removing any access that is unnecessary. Accounts with exceptionally powerful access shouldn’t have the ability to browse the internet or access emails. These are accounts of domain and enterprise admins, etc.
Patching operating systems
Periodically patch and upgrade your operating systems to the latest versions and ensure you’re using supported versions of operating systems. This way, you’ll make sure security patches are being developed by the manufacturer as new vulnerabilities are discovered.
Multi-factor authentication
Set up multi-factor authentication (additional methods for the verification of the user’s identity). This will provide higher authentication assurance for privileged and remote user access.
Backup daily
Back up the most important, new, or amended data and configuration settings daily. This will allow your business to maintain reasonable availability in the case of a system crash or cyber healthcare information security breach. At a minimum, you should keep backups for at least three months. When you store them, do it in a place separate from your system. You should also test the restoration procedure and validate the backup integrity periodically.
Data Breach Example: My Health Record
Compile health care information in one place online, and you become a hot pot for data breaches. That’s what has happened to the Australian Government’s My Health Record online portal, which lets you and your doctors view your medical history online. In 2018, there were 42 data breaches of My Health Record System Data. This is why people were sceptical and many chose the opt-out option.
Healthcare organisations face an increased burden to maintain the privacy of the MHR data, Proofpoint Asia-Pacific and Japan vice president Tim Bentley warned, noting that today’s cybersecurity attacks “primarily target people, including doctors, nurses, and administrators, rather than infrastructure, to access data.”
Due to the rising concerns of the Australian community, the Federal Parliament passed legislation to strengthen privacy protections in My Health Records Act 2012. This means that Australians can opt out of My Health Record at any time of their lives. The new laws mean that no one can access your information for employment or insurance purposes, law enforcement/government departments can’t obtain information without your consent or a court order, and your data can’t be used for commercial or non-health-related purposes.
You can read about more Australian companies that have had their data breached this year here.

What Systems do you Have in Place for your Healthcare Cyber Security?
In the healthcare sector, cyber security at the network level is key to protecting patient and practice data. It’s shocking, but even organisations that set out to help people aren’t safe from cyber security attacks. In fact, they make a prime target. The healthcare sector’s downfall has been its neglect of healthcare information security and the absence of proper staff and user education.
Incorporate the following measures in your practice’s cyber security strategy:
- Use application-level firewalls to access systems more secure and reliable, blocking any potential threat or attack.
- Set email parameters as a simple safeguard. The number one cause of data encryption results from staff accidentally clicking harmful links. Verifying senders and blocking harmful or malicious content entering staff’s inboxes drastically reduces unwarranted entry.
- Install adblockers on staff computers and devices to stop entry through ‘malvertising’ and harmful online ads.
- Do a daily backup of your network and files and keep all systems up to date. This prevents entryways appearing in the network that may go unnoticed and provides a failsafe system if you’re ever attacked. Backing up is the best deterrent for the attackers.
- Make it a regular practice to patch your core system. This prevents holes and entryways from appearing in your system that may be exploited for entry.
While the healthcare industry is a prime target for cyber security attacks, this doesn’t mean your practice needs to succumb to these threats. Educate your employees, follow the above guidelines, and implement strong cyber security measures in the workplace. Do this and you’ll be on your way to minimalising the risk of the healthcare information security of your client’s being jeopardised.
Considering upgrading your Healthcare Cyber Security?
Speak to the experienced team at Stanfield IT on 1300 910 333

