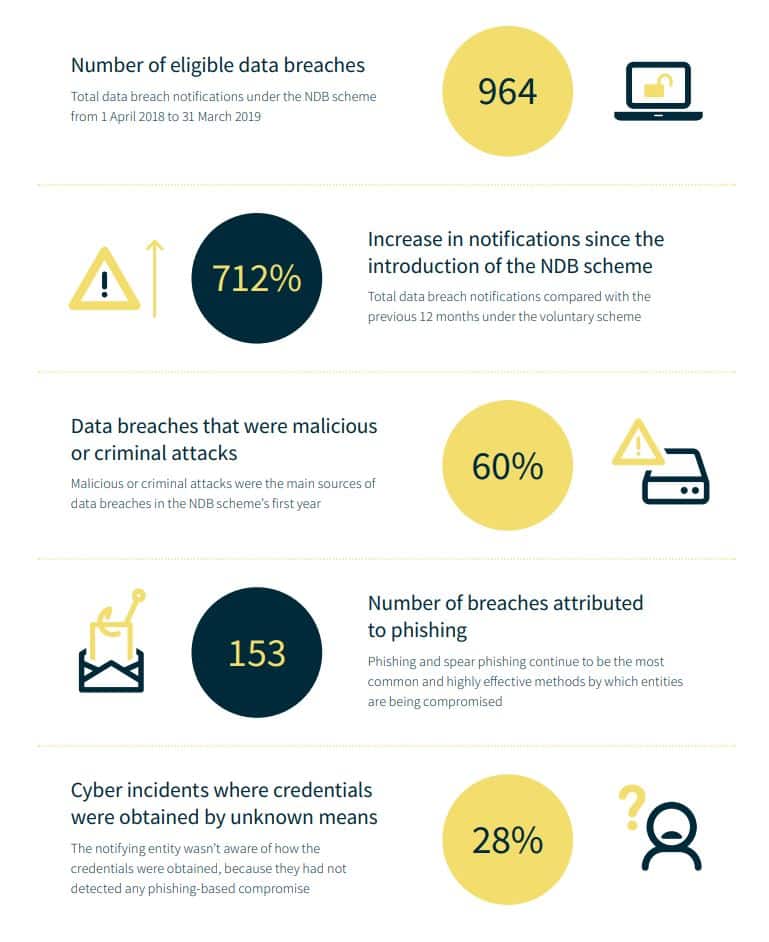
The Notifiable Data Breaches Scheme is a modern piece of governmental legislation. It forms part of the Privacy Act and has only existed for two years. It was introduced on February 22, 2018.
Governmental legislation and documents are often sprinkled with stilted and technical wording that’s a bit difficult to decipher. Don’t fret—we’ll go through it bit by bit to help you make sense of it all. By the end of this blog, you should be able to identify the the ways the Notifiable Data Breaches Scheme impacts how business’s cyber security regulations and disaster recovery plan.
What is a Data Breach?
In case you’re a new business, are looking to set up your own business, or have not reviewed information surrounding data breaches in businesses for some time, we will start with the basics: what is a data breach?
A data breach is when sensitive, private, and/or confidential information is released either intentionally or unintentionally to an untrusted environment. An intentional data breach could be something like a cyber-criminal gaining access to confidential client information through a phishing attack, or a past, disgruntled employee purposefully gaining access to your systems.
An unintentional data breach could be an employee logging into their work account on a public computer and accidentally leaving it open, or sending an email with sensitive client information to the wrong recipient.
Most data breaches won’t have an impact, but others can cause widespread business disruption.
Clients, customers, patients, and stakeholders can also be affected. The Notifiable Data Breaches Scheme is in response to these parties having the right to know if their personal information has been accessed in a data breach. It makes businesses accountable for the information they hold about the public. It also gives them steps to take in the case of a data breach. Let’s delve into this further.
Notifiable Data Breaches Scheme in a Nutshell
Prior to the Notifiable Data Breaches Scheme coming into effect, there wasn’t much protection for individuals who were trusting their information to organisations. This new scheme provides added protection and security to individuals by applying a set of rules and protocols surrounding data breaches, forcing organisations to be more transparent with clients, and more proactive with their security.
But, how do you know if your organisation falls under the scheme? Don’t worry, it’s pretty simple! ANY organisation or agency that falls under the Privacy Act 1998 will need to comply with the Notifiable Data Breaches Scheme. If you’re in healthcare, this will most certainly mean you, as all healthcare providers fall under the Act. However—this is where it may get a bit tricky—not every incident needs to be reported to the OAIC (Information Commissioner).
You MUST notify them if the data breach is likely to result in serious harm to the individual whose information has been jeopardised. The individual must be notified of the breach, too. But you can’t just drop them an email and then be on your way. It’s your responsibility as a business to provide them with recommendations as to the steps they need to take in response to this incident. You’ll also need to let them know what is likely to happen next.
How do I know if the data breach should be reported?
The OAIC website lists the following criteria that must be met for a breach to be classed as serious and thus need reporting.
- An incident where unauthorised access or disclosure of personal information (held by an organisation or agency) has occurred. OR information has been lost by an organisation or agency and unauthorised access or disclosure is a likely outcome of this.
- This authorised access—or potential for access—is likely to cause serious harm to at least one individual. See below for examples of identifying what ‘serious harm’ means in this scenario.
- Despite remedial action, your organisation or agency hasn’t been able to mitigate the risk of serious harm occurring.
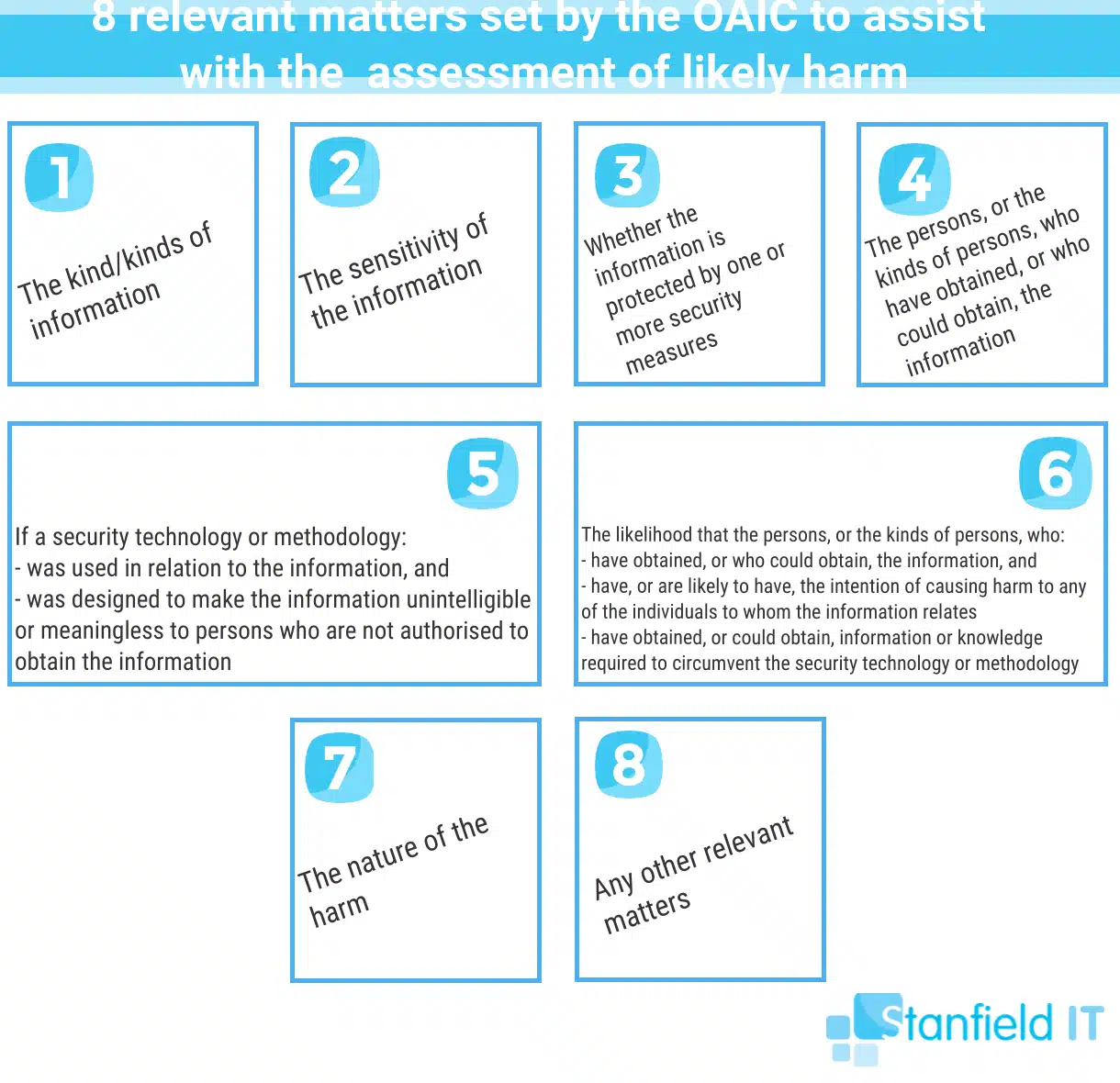
When reporting the data breach, you should include as much information as possible. This will ensure that the OAIC can respond to your notification promptly and thoroughly. It will also protect your business, as they have documented of the steps you took to contain the breach and begin remedial action.
Here you can find the Notifiable Data Breach Form.
Notifiable Data Breaches Scheme Essentials
The official wording is: If an organisation falls under the authority of the new Notifiable Data Breaches Scheme, they are now obligated to notify both the Australian Information Commissioner, as well as the individuals whose personal information has been involved in a data breach that is likely to result in serious harm.
So, if your organisation suffered a serious data breach, you cannot just quietly make it all go away. You must inform the OAIC and the affected individuals. This all sounds pretty fair, right? However, there have been many cases where companies did just the opposite. That is, they tried to sweep a data breach under the rug, leaving individuals exposed and unaware.
When notifying the OAIC and individuals, the affected organisation must include the following information.
- The identity and contact details of the organisation.
- A description of the data breach.
- The kinds of information concerned.
- Recommendations about the steps that an individual can take in response to the data breach.
With regards to notifying individuals, the organisation has a choice to either notify all individuals, notify only those at risk of serious harm, or, alternatively, simply publish their statement on the company website and publicise it. Such a statement could also include an apology, and further explanation of the actions being taken to resolve the breach.
Notifiable Data Breaches Scheme Terms
The term ‘serious harm’ can seem a little vague and subjective. So, here are some concrete examples of what can constitute ‘serious harm’ under the auspices of the Notifiable Data Breaches Scheme:
- Physical harm.
- Financial/economic harm.
- Emotional harm (e.g. embarrassment, humiliation).
- Psychological harm (e.g. marginalisation, bullying).
- Reputation harm.
So, realistically, most instances of a data breach would fall under this jurisdiction. It’s not only applicable if passwords or financial information was stolen, even just an exposed name can cause reputation harm or embarrassment (consider the Ashley Madison case).
Who falls under the authority of the Notifiable Data Breaches Scheme? A quick way to determine if you are subject to the Notifiable Data Breaches scheme is to ask yourself the following questions.
Are you:
- An Australian government agency?
- A business or not-for-profit organisation with an annual turnover of at least $3m?
- A credit-reporting body?
- A health service provider?
- A TFN recipient?
If you said yes to any of these, then Notifiable Data Breaches Scheme applies to you! If you’re still not sure, you can review this in more detail at OAIC.
Notifiable Data Breaches Scheme Timeline
If you are subjected to a data breach, and you fall under the great Notifiable Data Breaches Scheme umbrella, then you have a maximum of 30 days to assess and investigate in order to determine if it constitutes an ‘eligible breach’. As yourself: is it likely to cause serious harm to the affected individuals?
If you’ve determined it to be eligible, then you follow through with notifying the OAIC and the affected individuals. You can also post it directly to your website.
All in all, it’s pretty a straightforward process, just wrapped up in bureaucratic terminology designed to put you to sleep. The OAIC has all the information you need on how to notify them and what to include. So, if you feel this is something relevant for you right now, jump over to the OAIC website for more details.

Preventing a breach in the first place
Getting your head around the correct way to report is one thing, but wouldn’t never having to lodge a report at all be the best outcome for your business?
There are a number of steps that your business can take in order to prevent a data breach from occurring. These can also be applied if a data breach has already occurred in order to lessen its effects.
Preventative steps to take
- Of course, our first point here is to get yourself and other team leaders across the Notifiable Data Breach Scheme. You should be able to describe what an eligible data breach means, as well as what your reporting obligations are should a breach occur.
- Make sure your staff have up-to-date, ongoing, cyber security training. This will be your best defence against the leading cause of data breaches—human error! The training your staff should undertake should include how to identify likely cyber security threats, like a phishing attack.
- Change your passwords regularly, ensure they are strong (upper and lowercase used, symbols used, 8 characters or over, etc), and utilise two-factor authentication. A password management system (we use LastPass) is also a great way to ensure secure, unique passwords that employees have to change a certain amount of times per year.
- Ensure that employees are given minimum access to files. That is, they should just have permissions to what they need to get their job done. Also make sure that only staff members who require access to clients’ personal and financial information have access to this.
- For businesses using cloud computing—which is a lot of us these days—ensure that your cloud provider has sufficient security measures.
- Get a response plan ready that you can share with those in your business. This plan should go over how to identify data breaches and how to report such breaches of the OAIC.
- Make sure your security software—such as firewalls—are up to date and working effectively. Install security software and/or ensure that any software already in place is up to date and effective.
For more details on steps to take, check out our cyber security checklist.
In conclusion
All in all, it’s a pretty straight forward process, just wrapped up in bureaucratic terminology designed to put you to sleep. The OAIC has all the information you need on how to notify them, and what to include, so if you feel this is something relevant for you right now, jump over to the OAIC website for more detail.
For a full guide to Cyber Security check out The Definitive Cyber Security Guide for Small to Medium Businesses
Get in touch with the Stanfield IT team if you need assistance implementing any of the essential preventative measures for your cyber security.