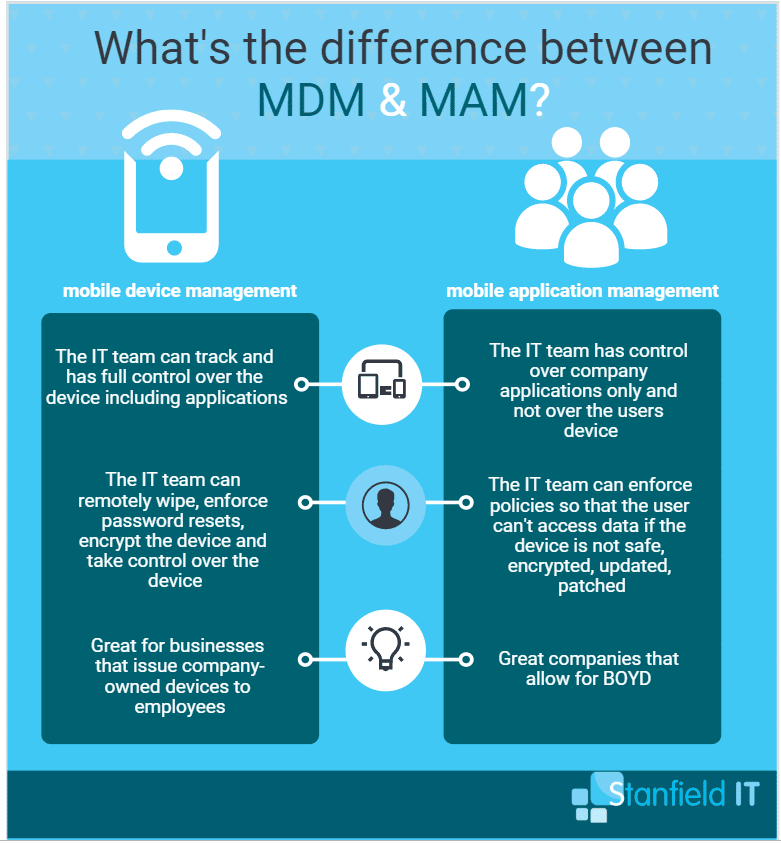
What is mobile application management?
Have you heard the term, but don’t really know what mobile application management actually means, or how it can benefit your business? We’re here to get your head around mobile application management (MAM), so you can see why it should become a part of your business’s cyber security strategy. Mobile application management is rapidly being adopted as a workplace policy thanks to the growing culture of bring your own device (BYOD). This culture has created the need for mobile application management in order to control access to internally developed and commercially available apps used on personal or company-provided devices. The aim is do this without impeding the end-user’s productivity or personal privacy.
Now, this is where MAM software comes in, where you can download required applications to employees devices and allow for any-device, any-time, any-place productivity. It gives IT administrators the ability to apply and enforce regulations, permissions, and policies on mobile apps. This means that employees can only access corporate data (that they have permissions to) from secure networks. If a device is lost or a user is no longer employed by the business, data can be remotely wiped from the device. Enterprise apps and company data can be separated from personal content on the same mobile device. This prevents your company data from getting into the wrong hands!
MAM and BOYD
Mobile application management is integrally tied with the ever-increasing popularity of BOYD in the workplace. The demand for out-of-office workspaces, like the home, hotel room, etc, means that only allowing employee’s to work from their work desktops could see a decrease in productivity. But allowing employees to log into company sites and email accounts on their personal devices via their different networks comes with its own set of security concerns.
Security breaches could arise if the employee accidentally stayed logged in on a public computer, logged in via an unsecure network, or if their personal and workplace apps share data. This is where MAM comes in. MAM allows company’s to remotely control what devices work systems can be logged into on. This means that only secure networks will be used and data sharing between apps will stay seperate. MAM lets a company’s IT team manage and secure apps. They are able to lock a user out of a corporate app or mobile email (say, if they leave the company or the device is lost), but the user’s personal accounts and data are not jeopardised. V-Soft Consulting states that:
New research indicates the average amount of devices the average person carries could reach 4.3 per person by 2020, and those devices are more powerful than ever.

Notifiable data breaches & loss prevention
Under the notifiable data breaches scheme, companies covered by the Privacy Act 1988 (such as all healthcare providers) have to notify affected parties. Additionally, for serious cases, the OAIC itself must be notified. This links in with MAM as they are both geared towards loss prevention.
The popularity of BYOD also means that MAM is more important, as there are more room for data breach opportunities. These may go unnoticed if MAM is not set up on employee’s devices. This is a huge concern as your business could be liable and face a hefty fine for not reporting a data breach. Examples of when a data breach may occur on a mobile device include:
- A device with a customer’s personal information is lost or stolen
- A device with personal information is hacked
- Personal information is mistakenly given to the wrong person via their device

Different types of mobile application management
There are two main types of mobile application management that can be used. The first is when you have the management features built directly into the app packages themselves.
The other is where you have a device with a built-in management framework that can differentiate between enterprise apps and data, and personal apps and data. These frameworks rely on an underlying MDM enrolment.
When you have an app that’s come directly from an enterprise mobility management (EMM) vendor, they will usually have mobile application management features built into them. Developers can also use software development kits (SDKs) to incorporate MAM functionality into enterprise apps.
App-level MAM
This ‘app-level MAM’ has a few advantages. You can add whatever security or management features you require directly into the apps. Additionally, you don’t need to worry about the security of the device itself, because you’re building security directly into the app. This means that no mobile device management is required.
App-level MAM requires mobile device management for devices, so you need to enroll, manage and trust the devices, which can be tricky when considering employees using personal devices for work. Another issue to consider is that the Android platform is still somewhat fragmented. Many devices don’t support Android for Work, or all of the recent features, as opposed to Apple devices which are consistent across the board.
Device-level MAM disadvantages
Regarding ‘device level MAM’, you have more freedom in that you can apply mobile application management features to any app, regardless of what it is, or who created it. You also have consistent management features across all apps, since it’s all part of the same device framework. Overall, device level management is far simpler and more streamlined.
Mobile Application Management Tools
The following list are some vendor tools designed for mobile application management. They each have different strengths and weaknesses. Some are designed to be used as part of a software package, but some may be utilised separately. Make sure you delve deeper into them before choosing what is right for your business, or contact Stanfield IT for advice.
Microsoft Intune
Intune and mobile application management go hand in hand, and is the Stanfield IT go-to when recommending an MAM product to our clients. With Intune, you can securely manage the apps your company apps employees use, and how they use them. Microsoft have combined security with productivity when building Intune. Thier priority was for users to be able to do their work on any device, while company data and resources remain protected.
Are far as MAM is concerned, Intune is advanced in its level of managing and protecting data within applications. The suite of Intune management features allow you to publish, push, configure, monitor, and update mobile apps individually or across-the-board for all registered users.
AirWatch MAM
Airwatch is enterprise mobility software that has been created by VMware, who are industry leaders in the space of business solutions and technology. With the capability to support every endpoint and user from one management console, Airwatch is extremely popular in corporate settings.
It’s 9.7/10 rating on Finances Online is testament to its diverse functionality. It not only suits offices, but the management of kiosks and all situations of shared devices. It includes complete device management and ensures the protection of all corporate apps and data. Layered security means that this protection stays put no matter which network is being used.
Amtel
Amtel provides a combined SaaS (software as a service) solution for mobile device security, apps management, and expense control. This integrated solution is managed from a single web-based console. Setup, dashboards, and reporting for simple and secure mobile collaborations are intuitively combined.
Amtel’s SaaS enterprise is fully integrated and covers the full lifecycle of secure mobile collaboration from a single web-based console. Applications include securing devices, content and communications; taking control of apps, GPS tracking and location based control; managing procurement workflow; and mobile & telecom expense management.
Citrix Endpoint Management
Citrix Endpoint Management has fantastic MAM capabilities for an integrated workplace experience. It’s useful to note that this also includes managing endpoints and MDM. Endpoint Management lets you manage device and app policies and deliver apps to users.
Strict security protocols for identity, devices, apps, data, and networks means you can be confident your business will be protected. Citrix’s cloud environment is hosted in global data centres, which means you can expect high performance, quick response, and timely support.
MobileIron
MobileIron’s Unified Endpoint Management (UEM) is a security framework that is mobile-centric. You can build on your UEM framework with MobileIron by enabling other technologies that suit your business. These include zero-sign on (automatic validation) user and device authentication, multi-factor authentication, and mobile threat detection.
MobileIron lets you separate business and personal apps and data across user’s mobile devices. Securing access to business apps and data minimizes the risk of stolen user credentials leading to data breaches. Some of the secure productivity apps MobileIron offers include email, contacts, calendars, tasks across multi-OS devices, including Android, iOS, macOS, Windows 10, Zebra, and OSX.
Symantec Mobility
The Symantec Mobility suite was created to allow for integrated mobile management and secure productivity across businesses. Instead of relying on different products, this suite has the aim of unifying security standards across different types of devices. Mobile application management is at the forefront of the Symantec Mobility suite, whether on corporate-owned devices or BYO devices.
No matter the device, a high level of security comes as standard across a range of environments that users do their work in. Semantec Mobility isn’t designed to be seen as a gatekeeper, but as a genuine enabler of mobile business.
BlackBerry EMS
EMS, a leading technology and mobile specialists organisation, is a long-term partner of BlackBerry. Together they have created innovative new ways for on-the-go communications between employees. Their Virtual SIM is a simple, no-frills way of implementing a BYOD or CYOD (choose your own device) strategy in your company. This allows multiple numbers to be stored on a single device. Employees can switch between a work and personal number with separate bills, ownership, and liability.
EMS can let you take full advantage the BlackBerry Enterprise Server, managing and securing a range of devices through on-premises or hosted solutions. There are also extra features companies can use, like BBM Meetings, BBM Protection, BlackBerry Blend, document sharing, VPN access, SecuSUITE, and Enterprise Identity.
Ivanti AppSense
AppSense has been a top provider of management solutions for secure user environments for the past twenty years. The follow the mantra of enabling workers to be more productive and complete a more effective job. How? By having access to no more or no less than what they need to get the job done!
Since launching MobileNow, Appsense has been able to offer businesses the functionality of a cloud-based, hosted mobile device and application-management service. These capabilities can be deployed either as an integrated suite, or independently to work with you company’s existing lecacy software. The MAM features of Ivanti AppSense’s MobileNow service includes application security controls; deep and broad inter-application controls and data encryption; real-time online or offline policy enforcement; and a pre-populated enterprise application store.
Cortado MAM
Cortado MAM lets businesses easily and securely provide employees with the right apps for effective mobile application management. With a focus on native management capabilities of mobile systems, Cortado is known for the timeliness and ease of deploying an app to an employee’s device. Cortado MAM allows employees varying degrees of freedom. This is dependant on which apps are considered a security threat/don’t comply with corporate guidelines.
Employers can block these apps by blacklisting them. That way, employees won’t even be able to manually install them. Cortado saves businesses precious time by allowing companies to automatically set up email accounts on mobile devices. Their secure ‘business container’ allows for designated work apps to exchange data with each other and not apps external of the container. This means that no business data can end up in a user’s personal apps.

In summary: why your company needs mobile application management
Still wondering why your company would benefit from mobile device management? The below points are some key takeaways for why MAM will be a great company asset for you. We have seen these benefits across the businesses of our clients.
- Increased flexibility for employees, allowing them to work remotely or on-the-go.
- Reduced burden on IT, as organisations can send out mobile apps and updates to all devices periodically. This means that IT doesn’t have to physically handle all devices.
- Maintains privacy for business and users, as the company is merely controlling access and restrictions to company-related data. Users don’t need to worry that the company is monitoring all of their activity.
- Internal business apps can be deployed through an enterprise app store, equalling effificent rollouts. This means they avoid the tedious process of applying for approval to publish through the Apple App or Google Play stores.
- Improved end-user experience. Employees are able to respond promptly and interact with customers at any time, without being restricted to a workplace environment.
- Software delivery ― often through an enterprise app store ― and software license management.
In conclusion
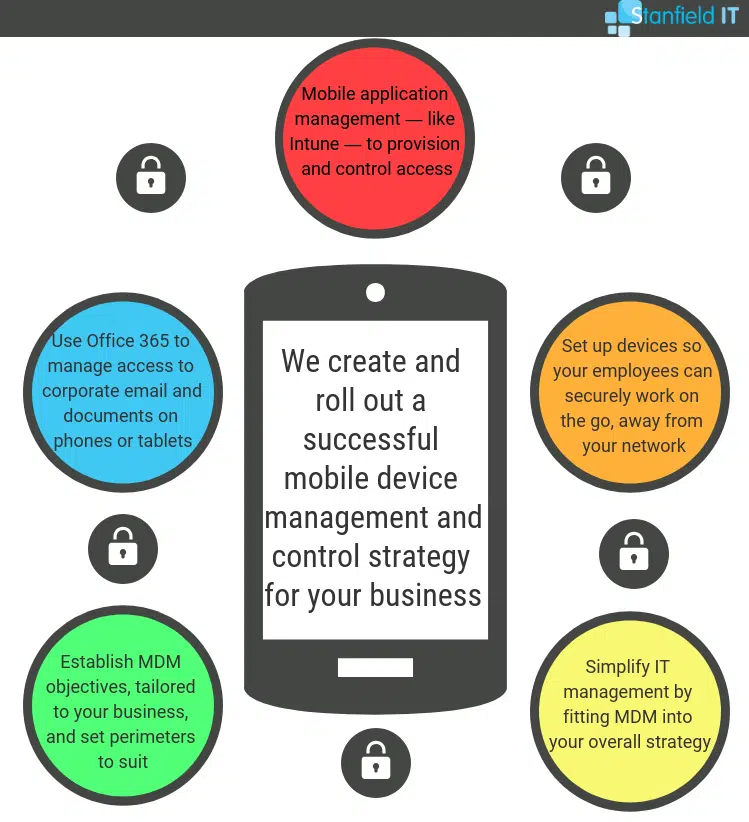
Mobile device management is an important part of cyber security services. It’s an increasing factor for businesses as many employees are opting to access work emails and files on their mobile phones and laptops. MDM is one of Stanfield IT’s specialties. We set up and maintain Intune subscriptions for many small-to-medium businesses. They can then enjoy unified endpoint management of both corporate and BYO devices.
Employees securely accessing business apps on their both BYO and company mobile devices will let you see increased productivity and centralised controlled. Software and updates will be deployed across the board and updates can be set up to automatically install on registered devices. If you’d like to incorporate a mobile application management system into your business, and need someone to help you roll it out and provide support, have a chat with our brilliant team at Stanfield IT.
