When it comes to IT security, we can never really get enough. If you’ve spent any time on our site, you’ll know that IT security is one of our obsessions. With the right IT security in place, you’ll find that your business operates with more confidence, and fewer tech interruptions. You can only really protect your sensitive data when you have a comprehensive IT security strategy. From your precious IP, to your customers’ identifying information. So, the proper IT security strategy is important to give everyone a greater sense of security.
If you’ve read any of our previous articles regarding IT security, you would have seen us reference the ‘Essential Eight’. But perhaps your eyes glossed over and you didn’t dig any further. We don’t blame you, IT security is not the juiciest topic to read about. But we’ll try and keep it interesting. The ACSC defined the ‘essential eight’ to be a list of eight strategies that help mitigate cyber security incidents. These guidelines are simple enough for any business to implement, and comprehensive enough that they will effectively reduce your risk of a data breach or cyber attack.

Implementing The Essential Eight:
Let’s review the ‘essential eight’ in terms of what each rule is, and what it means for your IT security. When you have all these strategies in place, they work together to a) prevent unexpected malware delivery and execution, b) reduce the extent and potential damage of cyber incidents, and c) recover your data and protect system availability.
Before you begin rolling out these strategies, however, you should probably determine the following: which of your systems need protection (i.e. where do your vulnerabilities lie). Identify where attacks or data breaches are likely to originate from (e.g. accidental data breaches, malicious insiders, corporate espionage). And lastly, what level of protection do these vulnerabilities require you to implement? The ‘essential eight’ each have different tiers of security you can implement depending your needs.

Use Application Whitelisting
Instead of going through and blacklisting all strange, new, or potentially malicious programs from executing on your system: create a whitelist instead. You can manage a list of approved and trusted programs far more easily than the inverse, as it’s a much smaller number. Ultimately, you’re saving yourself from the hassle of constantly trying to approve or determine which programs should be allowed to operate.
This rule explicitly prevents all non-approved applications from executing within your system.
This can be done in a few ways. You can whitelist applications on the local level using the Security Policy Editor. This approach is strictly local however, so it has to be configured on each device. Without centralised management, you can see how this becomes complex or ineffective when you’re dealing with multiple devices.
Therefore, a more recommended approach is to use Windows Active Directory, or Azure AD. Both of these approaches mean you have a centralised management approach and can enforce policy changes remotely to all devices. This is far easier and more effective.
Patch Applications
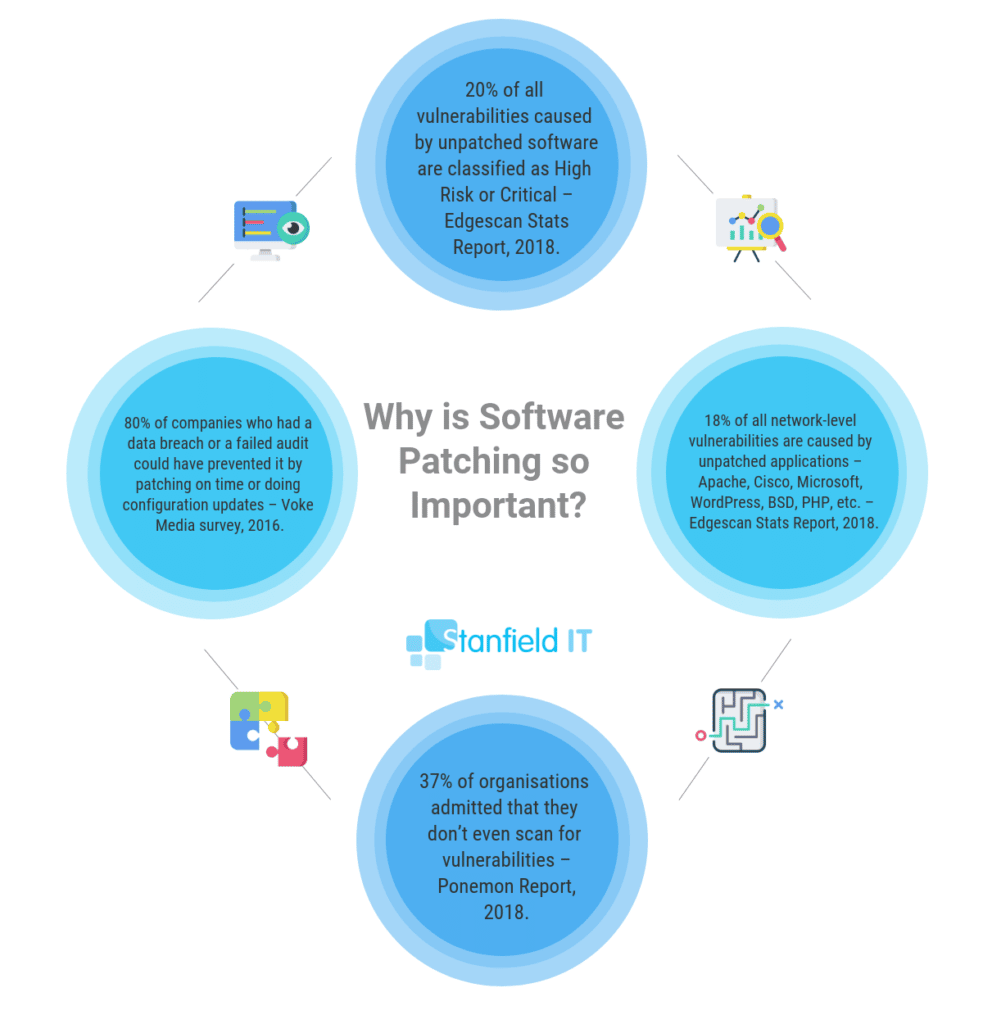
Ensure that all your software, tools and applications on your system are keeping up with the latest patches and updates. Software manufacturers release these patches regularly in order to address security vulnerabilities within the program. When we talk about applications, we mean everything from your Microsoft Office programs, to your PDF viewers and web browsers.
Many cyber attacks and malware rely on security vulnerabilities in these applications in order to access your system. You’ll ensure your security vulnerabilities are minimised by running the latest version of your applications.
Your software will generally prompt you regarding all security patches and updates. So, your first approach is to perform all patching and updates manually.
In terms of a centralised solution, there are a couple of options. Windows Server Update Services (WSUS) will help you manage all your Microsoft-related updates (only if you have Windows Server OS). For third-party application patching and updates, you can utilise a tool called Ninite Pro which will keep all included applications automatically updated. Or, you can use a remote monitoring and management (RMM) tool such as ConnectWise Automate or ManageEngine Patch Manager.
Configure Macros
No, we’re not talking about your ratio of carbs to protein. Macros are basically bits of embedded code within Microsoft Office documents. Macros automate procedures related to document creation and editing, in order to make work easier. Unfortunately though, macros have historically been used to deliver and execute malicious code. As a result, they present a major security vulnerability.
This rule advises you to block all macros from the Internet (essentially any unknown or untrusted source), and only permit macros from trusted locations (i.e. they have a digitally signed trusted certificates, or you have personally vetted the source).
Locally, you have the option to configure or disable macros through the Trust Center, but again, this option is not ideal when you have more than a handful of devices to work with. You quickly run into the problem of having to keep track of which devices have been updated and configured.
For a centralised option, Microsoft Intune has a function that enables you to create rules that prevent macro threats; so they’re unable to create or execute content, amongst other rules. If you’re running your system on Mac OS, don’t worry. Intune is also supported on Mac OS.
Application Hardening
On one hand, you’ve got your whitelist of applications that are allowed to operate freely within your system. You’re keeping those applications up to date to minimise security vulnerabilities now as well. But how do you make these applications even more secure? You restrict extraneous functions that have the potential to deliver malware.
Configure your web browsers to block extensions like Flash, Java or ads, and disable all unnecessary functions within Microsoft Office and PDF viewers (e.g. object linking and embedding or OLE).
We’ve established that it’s better to steer clear of manual and individual configurations, as a matter of efficiency. Luckily, Microsoft has a great tool included on Windows Enterprise called AppLocker. AppLocker allows you to create and deploy application-specific policies and configurations across your whole network of devices.
If your business is running on Mac devices, the MacOS Server comes with Profile Manager, which gives you the ability to configure settings and distribute policies across devices. A third-party option would be a mobile device management tool such as Jamf, which specialises in Mac systems.

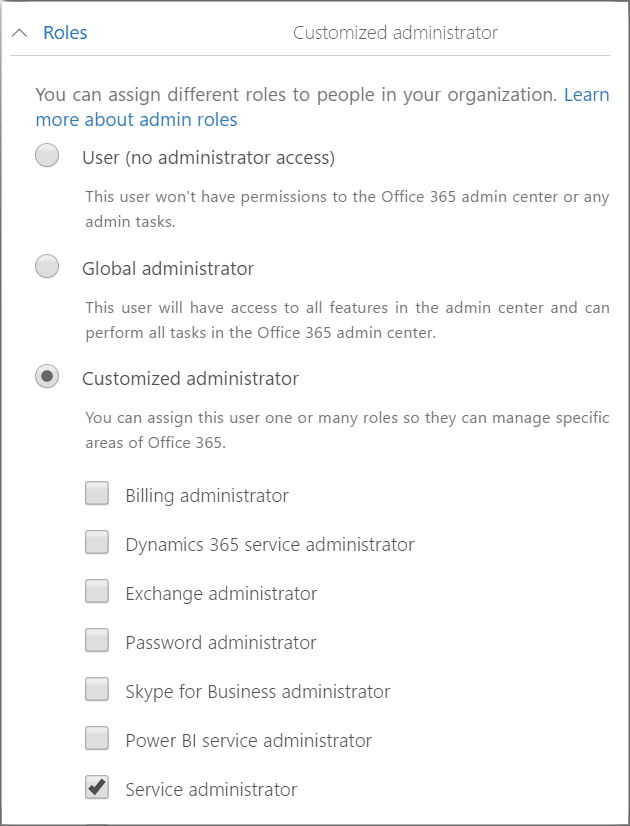
Restrict Administrative Privileges
This might seem counter-intuitive. After all, isn’t the point of admin accounts that they have more access and privileges? Well, yes. And no. You must configure administrative accounts so that they can only access what the user requires. Ultimately, there’s no need for one user to have full privileges and access to everything like they’re some kind of cyber overlord.
Consequently, this important rule recommends you regularly revise who has access to admin privileges, and most importantly, ensure that admin accounts do not have web or email access. Because administrative accounts have access to so much, a malware attack has the capacity to do far more damage if it infiltrates in this way.
In order to configure and restrict administrative privileges centrally, Azure AD has your back. Follow the steps in this process in order to group and control admin privileges as required.
Similarly, for Macs, you will find that Profile Manager has the settings you need to configure and control accounts across the network.
Patch Operating Systems
So, this rule follows the exact same logic as patching your applications. Operating system updates often contain important security patches and address potential security vulnerabilities. This also applies to using pirated or outdated operating systems. If your OS is so old that the manufacturer doesn’t support it, then you need to upgrade because you have a serious vulnerability.
This rule is important on its own as these security vulnerabilities within operating system code can be used to compromise an entire system, not necessarily just one local computer.
We mentioned WSUS earlier, this is your tool to approve and deploy OS updates. WSUS enables you to remotely update all devices with the latest OS updates and security patches. MacOS Server has everything you need to perform the same functionality.
Set up Multi-factor Authentication
This is another IT security strategy you’ve likely heard about, whether here or elsewhere. Multi-factor authentication is now something of a security standard now, across many platforms and tools. This is great! Such a simple strategy, but has the power to mitigate so many potential angles of attack. Enable your MFA wherever possible.
Multi-factor authentication essentially verifies users before granting access to accounts or data. It does an excellent job of preventing phishing attacks or password hacking from being successful.
Multi-factor authentication is not a feature you can implement through a third-party application. By its very nature, it has to be a built-in function of the platform or tool you’re using. Where possible, enable multi-factor authentication settings on every single tool you use. Most especially to your collaboration platform (G Suite, or Office 365), your accounting tools (Xero, MYOB), financial and online banking tools, your CRM (such as Salesforce) or your ERP (e.g. SAP).
Other Key IT Security Defenses to Consider:
Enable Daily Backups
What’s your strategy for recovering your corrupted or lost data in the event of a cyber incident? Daily backups. This is your strategy now. Backups ensure you retain all new or changed data, and even software and configuration settings. Likewise, store your backups in a location disconnected from your main network, retained for a set period of time, and tested periodically.
Above all, system backups ensure that critical data and information can still be accessed after something like a ransomware attack, that relies on holding your data hostage in exchange for financial compensation. If your data is safely secured elsewhere, your would-be blackmailer has no leverage.
Your best bet with backup solutions is to utilise a tool that provides both an on-premise backup and cloud-based backup storage. Employ a self-managed tool like StorageCraft or Acronis for the best of both worlds. Therefore, with self-managed tools you need to ensure that you’re configuring your settings appropriately in terms of frequency (anywhere from daily to weekly), retention period (around three months), and testing (one or two times per year).

Remove Old Accounts
It may come as a surprise, but idle, unused accounts from previous employees are an easy in for hackers. Luckily, there’s an easy fix—just delete them! This is a simple way to tighten your IT security. Old accounts may not just come to exist through staff turnover, but may be a result of system migration as your business transitions to new platforms or software over the years.
This can result in many accounts for the same employee coming into existence, and it’s the responsibility of management to make sure unnecessary accounts are deleted. Having an off-boarding procedure in place, as well as business guidelines for regular admin and housekeeping, can make removing old accounts a part of the day-to-day of your IT security procedures and tighten information security.
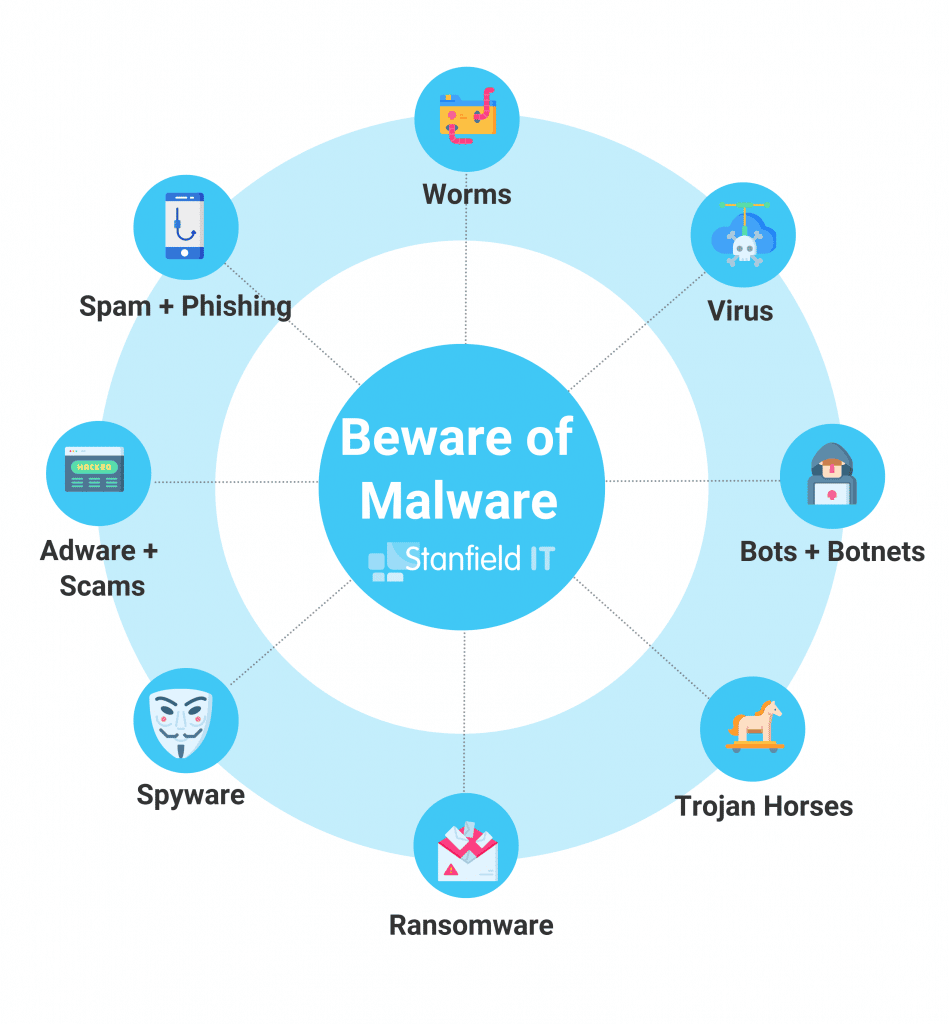
Use Anti-virus and Anti-malware Protection
Small businesses have a big, red bullseye on them when it comes to hackers. They often don’t have the advanced anti-virus protection of larger businesses and enterprises, plus security measures may be more relaxed as they don’t think their assets are worth targeting. Wrong! In 2019 in Australia, 78% of small businesses were the targets of a cyber attack.
One way to ready your own small business for such a circumstance is to implement antivirus and antimalware protection into your IT security. Ensure that you’re on top of updates, so that you know you’ve using the most relevant, advanced software version – if you don’t do this, it may be an easy way for hackers to breach your security. Use spam filters so that the majority of spam emails don’t make it to your inbox, and the inboxes of your employees. Email security is often not high on a small business’s IT security agendas, but 90% of cyber attacks are actually carried out via email.
Leverage threat intelligence
With human error making up one in three data breaches in Australia, the ultimate form of IT security is knowledge. This doesn’t just mean your managers, but across all teams and players in your business. Knowing where risks lie, how to detect threats (such as a phishing email), who to report threats to in the business, and the worst-case scenario if the threat went undetected, is the best way to safeguard your business. After all, knowledge is power!
You should also have a response team in place who can act quickly if a data breach does occur. Want some guidance when it comes to staff training and education around IT security? Stanfield IT can help! Contact us today to learn about training options for your employees, run by us.
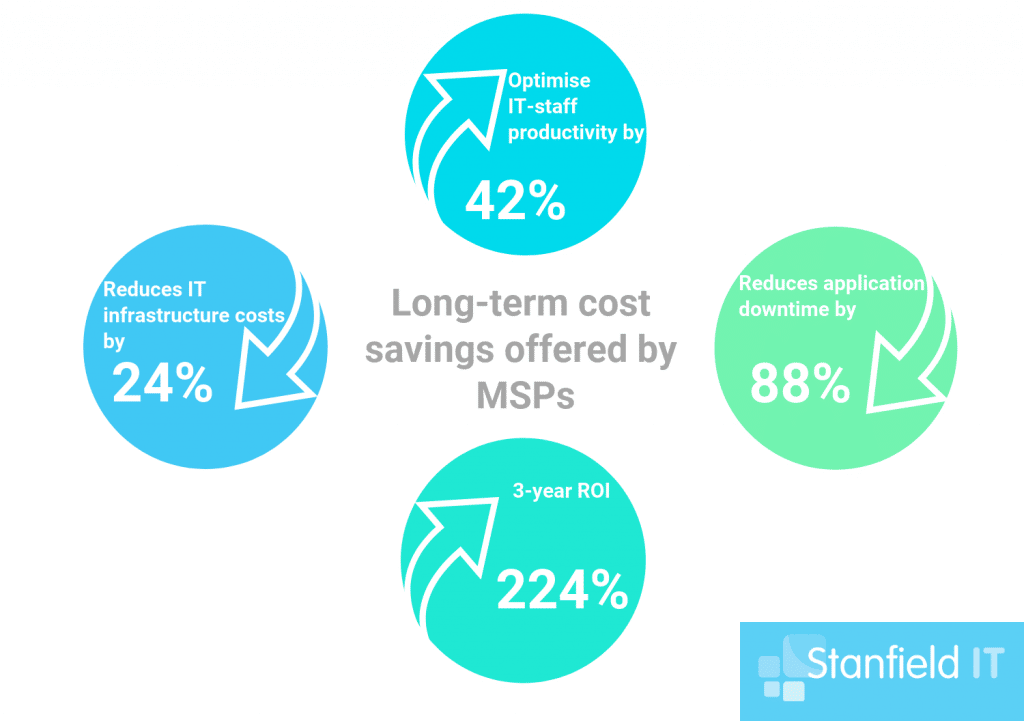
Consider Managed Services
If you feel a bit overwhelmed, or just want the ultimate in cyber security, consider managed IT security services. Managed services are designed so that you have a whole expert IT team at your disposal, no matter how small your business is. You can save big, as it’s a fixed cost, and also get the peace of mind that you have access to around-the-clock IT assistance.
With managed services, your business will have the flexibility to address the constantly evolving IT threats and regulatory requirements. Managed services allow you to incorporate robust IT security programs into your business infrastructure, with still keeping the decision making up to you so you don’t need to worry about your policies management strategies being swept from underneath you. Find out more here about Stanfield IT managed services.
Putting Everything Into Practice
So, hopefully you now have a pretty clear idea of what each of these strategies mean and how they actually help to protect your system from potential cyber attack or data breach. If not, give us a call and let’s talk about it some more.
Admittedly, this is a big task. Putting all of these into practice and taking the time to research and understand all the appropriate tools and solutions is time-consuming and can be overwhelming. In short, put it in the too-hard basket. This is where managed IT services are your friend. Above all, your IT security is simply too important to let slide.
On the other hand, when you’ve got your hands full just trying to manage your business, and you don’t have the internal resources to handle it, what do you do? It’s time to start researching someone to handle your IT security for you.
To sum up, for the sake of your business, it’s best if you are able to understand and implement these security strategies yourself. However, if not, then chat to someone like us and see how we can help you get on track.
