Let’s discuss cyber security risk and the different types of cyber security attacks. It’s one of those topics that is finally being taken more seriously across all industries. Businesses and users alike are learning to identify cyber security risks and attacks and how to avoid them. However, with the rate of cyber attacks increasing and evolving, it’s important to keep abreast of the where the greatest risks continually lay, and how to minimise them.
In particular, small-to-medium size businesses are at greater risk of cyber attack. This is primarily due to having fewer cyber security measures and policies in place. So, while the data at Google may be juicier… it’s a lot easier to break into a small local shop than trying to hit up a big bank vault, if you know what we mean.

So, as we can unfortunately see, cyber security attacks are on the rise worldwide. Without proper precautions, your customers’ most sensitive information could be at risk. It’s easy to dismiss some of the risk; it’s not like you’re hoarding secrets about national security. But many businesses are responsible for storing tax file numbers, home addresses, phone numbers, financial information, or other identifying information. It might not be national security, but it’s critically personal information for your customer base.
What is a Cyber Security Risk?
When we talk about a cyber risk, we are talking about the vulnerable points within your system. These vulnerabilities are considered entry points for potential cyber attacks. However, by managing your cyber risk, you significantly reduce your chances of falling victim to a cyber attack.
In short, ensure you have security precautions in place at your business. It provides an effective deterrent against potential invasions or attacks. Often, the presence of security tools is a deterrent in themselves. Cyber criminals are looking for a low-risk venture, so between a business that has cyber defence, and one that doesn’t? They’ll opt for the easier route.
However, security precautions aside, your cyber risk can manifest in several areas, and it’s important to understand how they can come about. Your cyber risk is increased with policies such as BYOD (Bring Your Own Device). A policy which results in employees accessing company data from their personal devices. Cyber risk is present if your staff are accessing company data or storage via public WiFi. Failing to have backups in place also presents a grave risk in the event of a disaster or ransomware attack. Cyber risk is also present in password and user managemnet throughout your network.
Cyber risk is almost always present. However, the best cyber security strategy will focus on minimising these risks before implementing cyber security tools around the joint. Your anti-malware and firewall software is a great secondary measure. They provide additional security after you’ve ensured you’re doing what you can to reduce risk inside the business.
Cyber risk means any risk of financial loss, disruption or damage to the reputation of an organisation from some sort of failure of its information technology systems.
Institute of Risk Management
The 6 Most Common Types of Cyber Security Attacks
So, before we dive in here, it’s important to understand that there are a multitude of cyber attack types and this is by no means an exhaustive list. Furthermore, the occurrence of these types of cyber security attacks does change from year to year. The last year has seen an increase in ransomware and social engineering attacks; which we will cover below. However, this doesn’t mean business shouldn’t expect another kind of cyber attack.
Malware
As you undoubtedly know, malware is more of an umbrella term that covers many types of cyber security attacks. Things like viruses, trojans, and worms, are all types of malware that could potentially infect your site or data. A malware attack is simply a case of malicious software making its uninvited way onto your system in order to wreak some havoc. It could be hidden within an application that you approved, or linked in an email that you opened.
The sneaky nature of malware means that it exists in great abundance, all over the internet. As a result, you always need to be mindful of falling subject to a malware attack. The ultimate purpose of a malware attack is to steal or corrupt your data, and ultimately, replicate itself across the internet.
Fortunately, it’s relatively simple to deter and avoid most malware attacks. Simply by exercising some restraint and awareness, you and your employees can identify and avoid most malware. The greatest weakness of malware attacks, is that more often than not, they actually require your implicit invitation. Of course, this means they try and trick you into accepting the malware.
This is why most malware is disguised in legitimate looking links or software attachments. Things that you normally wouldn’t think twice about approving or clicking. Which is exactly why you need to be wary, and learn to identify suspicious links or attachments as your first line of defence. Your secondary measure, of course, is your anti-malware software. In the case that you did accidentally approve the malware, your security tool is there to say “Hey, are you sure you meant to install dodgyvirus.exe?”
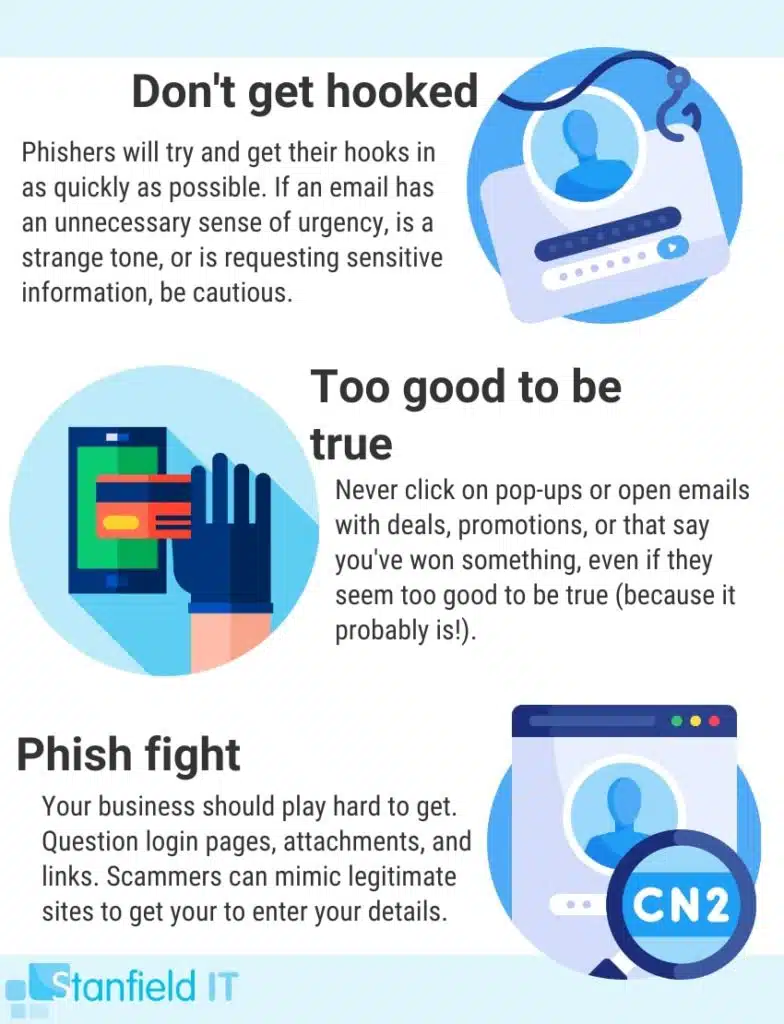
Phishing
Phishing attacks are just as prolific. They can range from the painfully obvious to the extremely clever. The general idea behind a phishing attack is an attempt to trick a user into giving away confidential information. This could be your password or credit card details. They often do this by sending emails that appear to be from a trusted source, such as your bank, or perhaps a site you use regularly. This could be anything from eBay to Amazon.
The email will usually have some variation of alarming message that requires you to immediately sign into your account to rectify. Followed by a link to the ‘trusted’ website where you then log in. Of course, the website is a dummy site that just sent your credentials to the attacker (phisherman?).
Many of these types of phishing attacks are easy to avoid when you know that your bank or other site will never legitimately ask you to submit your password or credentials in this way. So, you can almost always guarantee it’s a scam. However, the real one to watch out for is ‘spear phishing’.
Spear phishing is a targeted type of phishing attack. The attacker in this instance is not blindly sending out a thousand fake emails. These types of cyber security attacks are highly personalised and researched. The attacker has an intended victim in mind, and they’ll research everything they can. This includes everything from place of work, position, department, social media, and who they frequently interact with. This enables them to create an intimately detailed profile on this target. With all this information, these types of phishing attacks are far more successful. They are able to craft a realistic email using real information that is strictly designed to fool a specific target. Be alert and vigilant!
Ransomware
Ransomware is a type of malware, but it also deserves its own category amongst the types of cyber security attacks. Due to its prevalence, and the slight difference in its approach, it feels a little bit different to your standard download-and-corrupt virus. The name itself is a pretty big clue. Ransomware is a type of malware that works by holding your data hostage in exchange for a hefty ransom.
The rate of ransomware has skyrocketed signifcantly each year, meaning it’s an effective type of cyber security attack. Furthermore, these ransom attacks usually make their financial demands in the form of cryptocurrency, which is just about untraceable. So these attackers are getting their pay day, and then getting away with it.
Unfortunately, once your system has been hit by a ransomware attack; your data becomes fully encrypted and is inaccessible without the decryption key. The attacker won’t provide said decryption key until they get paid. And in addition, it’s likely the data will be destroyed if their demands are not met.
Therefore, one of the best insurances you can have against this type of cyber security attack, is to ensure that your data is frequently backed up and stored in a safe, secure location. If you know you can easily restore all your data, the threat of losing it isn’t quite so compelling.
Distributed Denial of Service (DDoS)
Distributed denial of service, or DDoS, is a term you may have heard in relation to government agencies or large corporate websites. In 2016, there were rumours of a DDoS attack being the cause for the outage of the census website. The Australian Bureau of Statistics later confirmed that the site had been the target of several denial-of-service attacks, for which they were obviously unprepared. All in all, it was a bit of a fail.
This attack works by flooding your network with data until it becomes too congested to function. The network essentially crashes, and your service goes down. Attackers will often achieve this high volume of data by hijacking other PCs to submit all the additional traffic (hence, it’s distributed). Often enough, users aren’t even aware that their computers have been used to participate in such an attack.
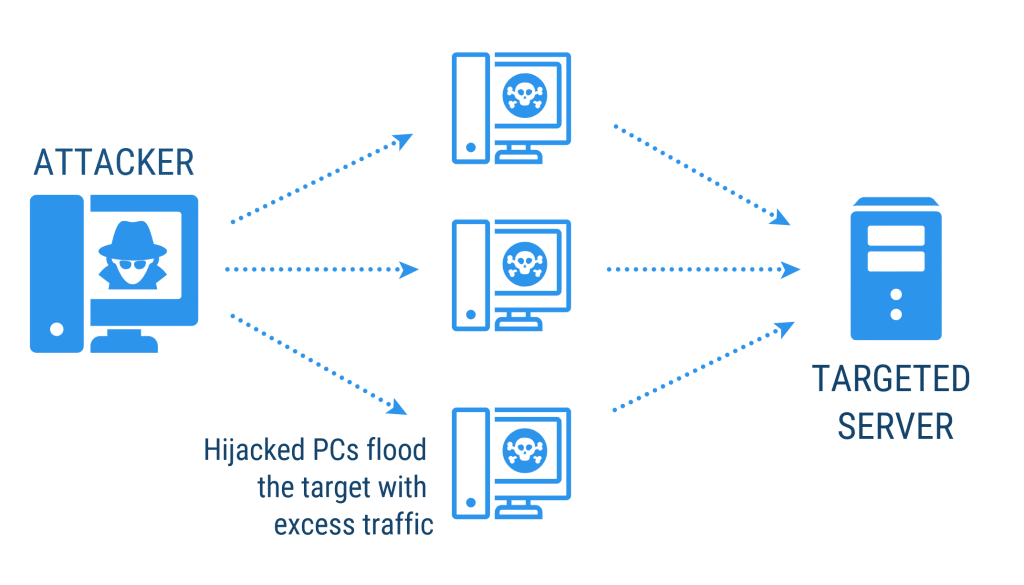
As with the example of the ABS 2016 Census, DDoS attacks primarily target government agencies, or large companies. It’s often a form of protest against policy or individuals. The end goal is different. Where phishing and ransomware are oriented towards stealing data for financial gain, the end goal of a DDoS attack lies elsewhere. The attacker doesn’t necessarily receive a direct benefit from the attack (i.e. data or credentials) but they may be doing it for the satisfaction of seeing their target fail, which makes a statement in itself.
Man-in-the-Middle Attack
The man-in-the-middle attack is one of those types of cyber security attacks that might occur without the victim being aware. It doesn’t crash your system, and it’s more effective if the victim conducts business as usual without knowledge of the insertion.
The end game of the man-in-the-middle attack is to essentially eavesdrop on an information exchange and get access to sensitive information without either party being aware. The ‘man in the middle’ impersonates the end parties to each other, so that both continue to send information across the network. The piggy in the middle gets to see everything that passes between.
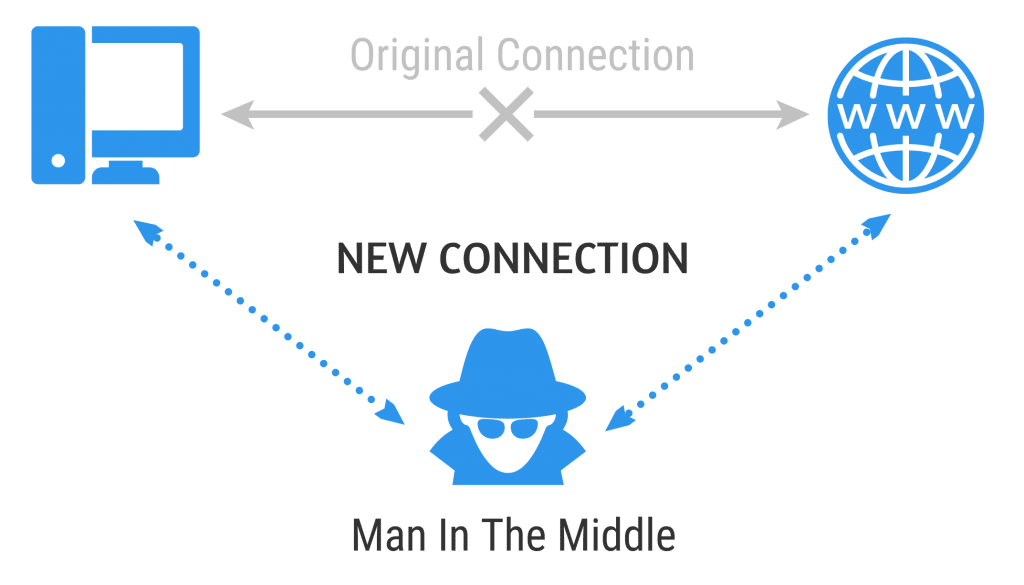
This type of attack is often achieved by session hijacking or IP spoofing. In the instance of session hijacking, the attacker captures the session token and then uses it to pose as the user. Meanwhile the server continues to believe it’s communicating with the client.
A solid way to prevent or reduce the risk of MitM attacks is to use encrypted access points (which prevents random users from joining your network), using VPNs (which encrypts your communications), and always check that the sites you are using are HTTPS (meaning the site is verified with a security certificate).
Social Engineering
Lastly, social engineering is technically a type of infiltration method that predates cyber security attacks. It’s about exploiting human psychology, rather than using technical methods to get access. Watch any Hollywood heist movie, and at least one character will rely heavily on social engineering to get access to the bank/vault/casino/lab/insert secure location here.
They’ll disguise themselves with a janitor or maintenance uniform, and act like they belong. This air of confidence and appearance lends credence to their belonging and they can often enter unchallenged. It’s playing on the human’s natural inclination to trust what we see. Upon closer inspection, the illusion breaks down, but the damage at this point is done.
When you apply this philosophy to online data, you can see how it may be an effective type of cyber security attack. This is especially prevalent amongst invididuals who are less tech-savvy and haven’t learned to mistrust the majority of online encounters. Phishing attacks fall under the category of social engineering attacks, as they work on the premise that the victim trusts the email source, and seeks to take advantage of that trust.
A great approach to avoiding social engineering attempts is to be suspicious of all online encounters. This especially applies to situations that seem out of the ordinary, or possibly too good to be true (no, sorry, you didn’t win the lottery despite not entering).
How to Prevent These Types of Cyber Security Attacks
Overall, the key to preventing these common types of cyber security attacks is to minimise your exposure and ultimately, your risk. We discussed cyber risk briefly above. Your cyber risk management should be an integral part of your cyber security strategy. In short, your cyber security strategy should be a three-pronged approach. We recommend that it focus on minimising risk (as we discussed), data management, and of course, your endpoint security (anti-malware, firewalls, etc).
In short, when you focus on all three aspects of your strategy, including backups and data recovery, you become remarkably resilient to all types of cyber security attacks. Your IT partner can assist you to build this strategy, as well as ensure that you have the right anti-malware and security endpoints in place.

Stanfield IT has an excellent track record (see: obsession) for cyber security management. Further, we will happily assist you with recovering from cyber attacks, as well as help you develop an appropriate cyber security strategy. With the right partner by your side, your business can be protected from cyber security attacks, and ensure your customers feel confident with your service.
