Most realizations of a ransomware attack begin with a profound feeling of “oh shit”. Staff begin reporting they are unable to open or access files. When you investigate you see that file names or extensions have been changed and there are documents with ransom payment instructions. You have become the victim of a ransomware attack. The question now is, how do you deal with a ransomware attack and what do you do?
What is ransomware?
Ransomware is a type of malware that holds your data, information, or systems as hostage until a sum of money is paid. This is usually done by encrypting your data. Ransomware exploits cyber security vulnerabilities on computers, systems, and servers that are vulnerable and open to infection or have not been patched. Ransomware will encrypt any data it can gain access to and demand a payment or a sum of money be paid to regain access to the data again. A lot of the time, these demands come with a deadline; the data will never be recovered if the victim doesn’t pay on time.
Today, ransomware attacks are all too common, with perpetrators becoming more and more technologically intelligent with the times. Cybercriminals don’t discriminate between the consumers and businesses they target, with small-to-medium businesses as well as enterprises being targeted. So never get a false sense of security that your business won’t fall victim due to its size; this could be your downfall.
Ransomware attacks are all too common these days. Major companies in North America and Europe alike have fallen victim to it. Cybercriminals will attack any consumer or business, with victims coming from all industries. Initiatives like the No More Ransom project have been hugely successful. This project is nearly four years old and offers decryptions tools for 109 ransomware strains. As of July, 2019, it had prevented ransomware profits of at least 108 million dollars.
History of Ransonware
It may come as a surprise, as the world wide web was not publically available until 1991, but the first case of ransomware can be traced back to 1989! This is because the first ransomware attack was not online, but through physical mail—on a floppy disc (remember those!?) through a postage service. The contents of the disc? AIDS education software, supposedly sent by PC Cyborg Corporation. But, in reality, the purpose of the disc was to encrypt victim’s files after they had rebooted their computer a set number of times. In order to get their files decrypted, victims had to pay $189.
Over the years, attackers have gotten more creative. Payments have become near-impossible to trace, assisting hackers in staying anonymous. This has been further achieved through hackers avoiding payments via normal currencies, but, instead through things like Bitcoin and Apple gift cards. Bitcoin—along with the birth of other cryptocurrencies like Ethereum, Litecoin, and Ripple—saw digital attacks skyrocket.

How Ransomware Works
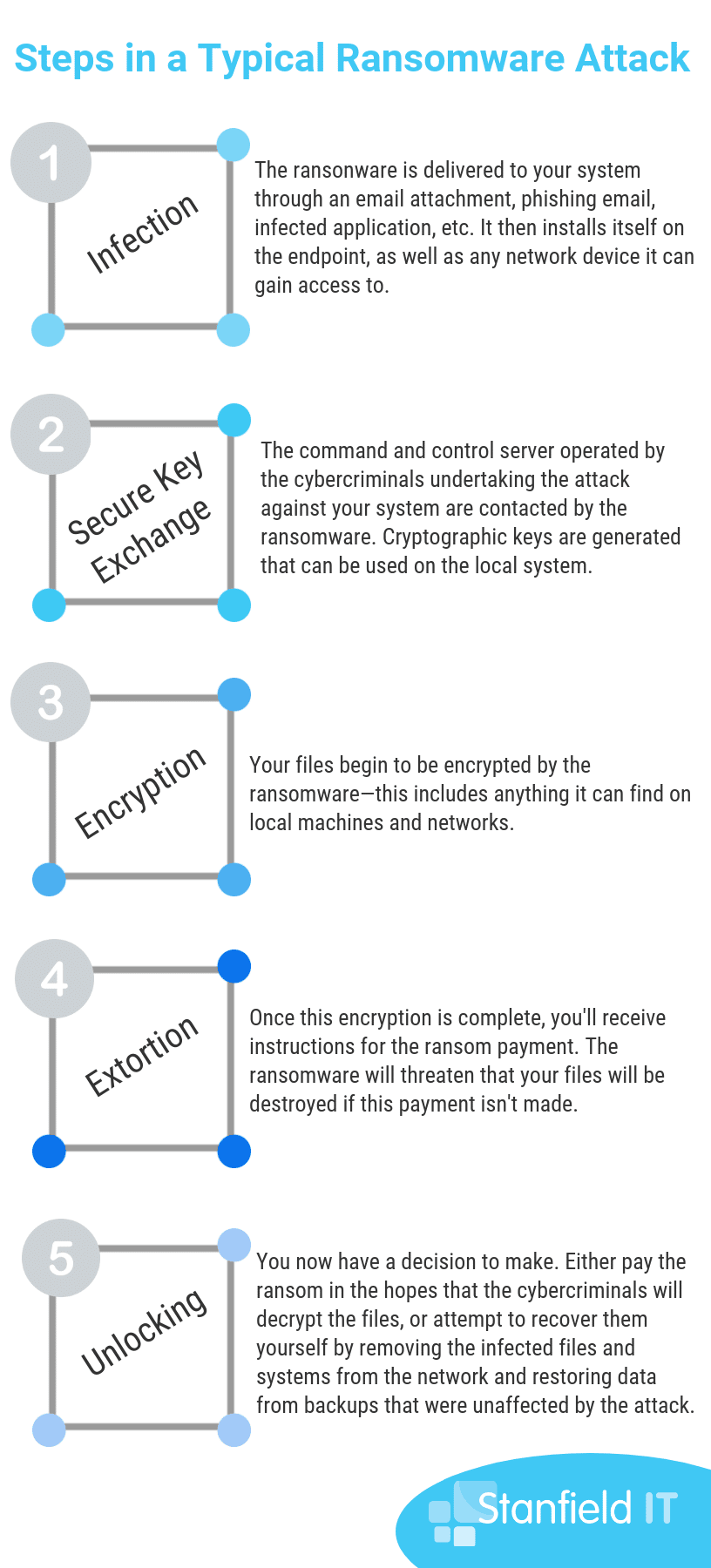
As we mentioned, ransomware is designed by hackers to extort money from victims by holding their data ransom. The most popular methods of ransomware used by hackers are encryptors and screen lockers, but we go into others in the graphic below. Common to both encryptors and screen lockers, victims are often made aware of the attack through a lock screen. They’re instructed to purchase a cryptocurrency, such as Bitcoin, to pay the ransom. Once payment has gone through, the victim will get a decryption key so that can attempt to recover their files. There are reports of varying degrees of success with files getting decrypted after the ransom is paid—sometimes, victims never even receive a decryption key. Sometimes, attackers install malware on the computer even after payment is received and the data is released.
Who is targeted?
In the past, ransomware attackers have focused their exploits on personal computers. However, users within businesses are increasingly become victim to the attacks. This is largely due to the fact that businesses will pay more to get their data back and unlock critical systems. Attacks can have a more prominent effect on businesses over individuals, as daily operations can be halted, money lost, and reputation damaged. Attacks within businesses usually begin with an employee receiving a malicious email, which poses as being from a credible source. The unsuspecting user then opens the attachment or clicks on a compromised URL to kick-start the ransomware attack.
The next thing you can expect to happen is that a ransomware agent is installed on the computer or device and key files on the employee’s PC are encrypted, as are online shared files. Once completed, a message is displayed on the infected device that explains what has happened and the steps to undertake to pay the attacker. Although we know they’re not always true to their word, the ransomware instructs that the victim will receive a code to retrieve their data if they pay the ransom.
So what do you do if you get a ransomware attack?
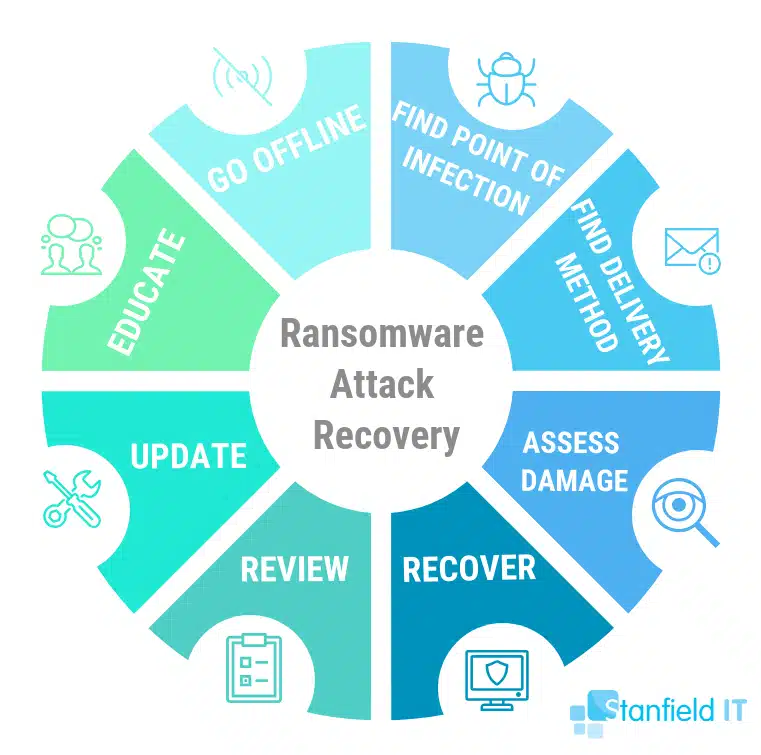
1. Go offline
The best advice in this situation is to go offline immediately. Take all your systems offline, unplug network cables, turn off the WiFi. If you are lucky and have been alerted to the attack early then the ransomware software may still be in the early stages of its attack and may not yet have had a chance to spread across the network.
2. Find the ransomware attack point of infection
You need to find which user or device was originally infected so you can eliminate the threat. Until you can be sure that the source of infection has been found and cleaned there is too much risk to bring any systems back online, some forms of malware may remain dormant and attack again after you recover or restore systems. You may need to disable the user’s access or wipe their devices to ensure the threat is stopped.
Remember that there might be more than one device that has been infected. This is because the ransomware could have penetrated your business through more than one computer. Or, in some cases, the may be laying dormant in other systems. Therefore, all connected and networked computers must be treated with suspician, applying measures to ensure all systems are not infected.
3. Find the infection delivery method
Once you know who got infected, you need to find out how. Find out from the staff member if they received any suspicious emails and opened links or attachments from them. Most ransomware is delivered through email so the chances are that other staff in your organization also received the same email. If you can identify it then alert all other staff about it so nobody else makes the same mistake.
Identifying the ransomware will assist you with understanding the type of ransomware you have, how it spreads, the types of files that are encrypted, and your options for removal and disinfection. Knowing the ransomware that infected your business will ensure that you’re able to properly report it to authorities, the recommended course if action.
4. Assess the ransomware attack damage
Once things have calmed down you will need to assess the damage and find out exactly what has been infected. Search across all shared and local storage for encrypted files and folders as this will help you plan for recovery. If possible find out what type of ransomware you have been attacked with.
It’s up for debate whether you can be successful in completely removing a ransomware infection, especially if it’s a new infection that a decryptor has not been developed for yet. The only way to be completely sure that the ransomware has been removed from a system is to fully wipe your connected storage devices and reinstall everything from scratch. This is why it’s so important that your business has a seperate, back up system.
5. Recovery from a ransomware attack
Although the chance is very slim, you may have been attacked with an older form of ransomware for which the encryption has been broken. If you have no backups this may be your only chance of recovery. Great if you have backups now is the time to go to your last good backups and begin the recovery process by restoring the data. If you have entire systems that have been encrypted or infected it may be worthwhile to rebuild them or restore the entire system from backup as well.
Make sure that you know as much as you can about what ransomware you were infected with. This includes figuring out the date of infection. Remember, as stated, the infection can happen unbenounced, sitting dormant in your system for a certain period of time. Identifying the particular type of malware that attacked your system makes you better equipped to understand how malware functions and the best way for your business to move forward.
6. Review security and procedures
Once recovered from a ransomware attack it is the best time to review your security and find out exactly what happened and how. Look at who got attacked and how far the infection spread. Ransomware attacks from the system or user who was infected, so everything they can access, so too can the ransomware. Is there anything they should not have been able to access? Also consider changing passwords and updating accounts. Some ransomware can also steal data.
Use a tool like Bitdefender to help protect your computer and prevent ransomware specific infections.
7. Get your systems and mitigation strategies up to date
In most cases up to date systems and cyber security prevention tools will prevent a ransomware attack. When a vulnerability is found the vendor such as Microsoft or Apple will have updated their software very quickly. Make sure in future you keep up to date.
You need to make sure that you also have a backup solution in place for your business’s files and data. Remember, though, that local backups can also be encrypted by ransomware. Unfortunately, if you have a backup solution that’s local and connected to a computer that comes under attack by ransomware, chances are that these backups will be encrypted, too.
8. Educate your team
Finally, use the opportunity to educate yourself and staff about what happened, how it happened and what they need to look out for in the future to prevent another such occurrence. Make sure that it doesn’t just stop at this–your employees should be constantly kept in the loop regarding the latest phishing scams, especially those that they might find in your work email inboxes posing as legitimate companies.
Prevention is Better Than Cure

Ransomware is (and most likely will continue to be) a major threat to businesses in all sectors, with healthcare being particularly targeted. Continually evolving their strategies to circumnavigate business’s defenses, cyber criminals have intelligent attack methods that hone in on areas that offer the highest payback for the least effort. Of course, equipping your employees with the knowledge and tools to avoid being a ransomware victim is always better than having to do the clean up. We delve into this more in The Definitive Guide to Cyber Security for Small to Medium Businesses. Or, feel free to contact the experienced team at Stanfield IT today on 1300 910 333 to secure your business.
