Cyber attacks are becoming increasingly common in recent years.
While they might sound like scenes from a Hollywood heist film, they are very real threats that businesses face daily.
In fact, cybercrime is predicted to cost $10.5 Trillion annually by 2025.
Attacks often involve sending out thousands of phishing emails, hoping that at least one unsuspecting user will download malicious software.
Attackers rely on the likelihood that someone will eventually click on a link and fall victim to the attack.
Regardless of your position, industry, or the size of your business, the risk of a cyber attack is always present.
Some industries, such as healthcare, are targeted more frequently due to the sensitive nature of the data they hold.
For example, the 2023 IBM Cost of a Data Breach Report found that the healthcare industry consistently faces the highest breach costs, with the average cost of a data breach reaching $10.10 million in 2022.
Considering the type of sensitive data your organisation holds is crucial in understanding your vulnerability to these attacks.
What is a Cyber Attack?
In short, a cyber attack is the deliberate exploitation of a computer system or network.
Hackers use malicious code (malware) to find and exploit vulnerabilities, disrupting normal operations and compromising data.
These attacks can lead to stolen data, financial loss, and significant damage to an organisation’s reputation. Not to mention the stress caused to business leaders.
Cyber attacks can affect anyone, from individuals to large corporations, and their consequences can be severe. For more details on protecting your systems, check out our Cyber Security Guide.
Why Do Cyber Attacks Happen?
Cyber attacks are undertaken for a variety of reasons, each driven by different motives and goals.
Financial Gain
No surprises here. Financial gain is a common motive behind cyber attacks. Cybercriminals steal sensitive information such as credit card details, personal information, and banking information to sell on the dark web or use for fraudulent transactions.
Ransomware attacks, where attackers encrypt an organisation’s data and demand a ransom for its release, are primarily driven by financial motives.
Data Theft
Cyber attackers frequently target organisations to steal valuable data. This data can include:
- Personal information;
- Intellectual property; or
- Confidential business information.
High-profile data breaches illustrate the attackers’ desire to access large volumes of sensitive data.
Disruption and Destruction
Some attacks aim to disrupt operations or destroy data, causing significant downtime and financial loss. Distributed Denial-of-Service (DDoS) attacks, for instance, inundate networks with traffic, overwhelming systems, and forcing shutdowns.
Espionage
State-sponsored attacks are often launched to gather intelligence or gain a competitive edge.
These attacks typically target government agencies, defence contractors, and large corporations, infiltrating systems to steal sensitive information or monitor communications.
Political Motives
Hacktivists launch attacks to promote political agendas, protest policies, or raise awareness about social issues. They may target government websites or institutions to deface pages, leak confidential information, or disrupt services.
Revenge or Personal Vendettas
Some attacks are driven by personal grievances.
Disgruntled employees or individuals with personal vendettas may target organisations to cause harm or embarrassment, such as insider attacks where company systems are sabotaged or sensitive information is leaked out of spite.
Who Is At Risk Of A Cyber Attack? And Why?
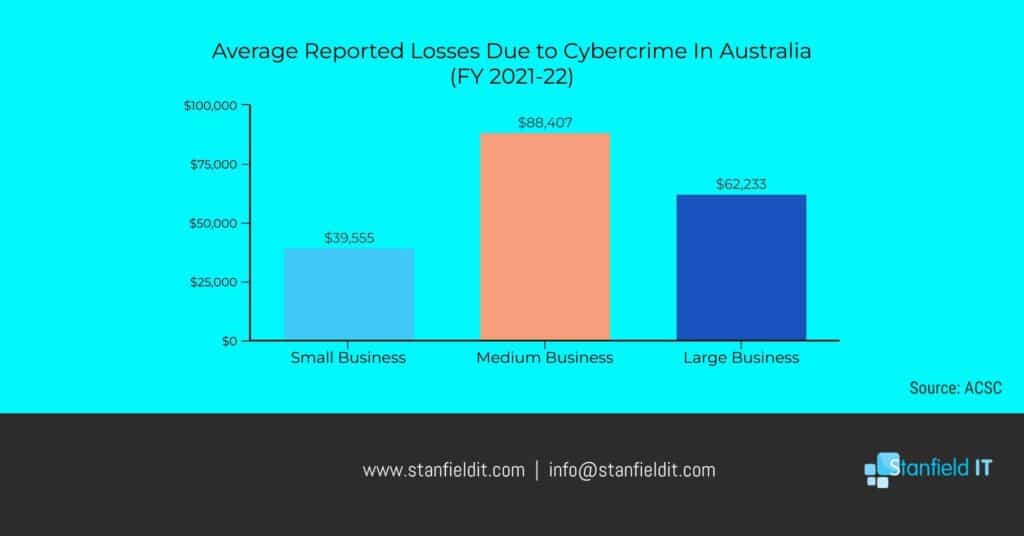
At first glance, it may seem counter-intuitive. But more than anyone else, small businesses need to be wary of cyber attacks. Small businesses present a tantalising target for attackers for a few reasons.

Small-to-medium businesses (SMBs) are less likely to have stringent security measures and appropriate incident response plans in place. Therefore, attackers find SMBs far easier to infiltrate and exploit. Additionally, they often don’t have the means to defend or recover from an attack easily, so they’ll cough up the dough after a ransomware attack just to get their data back.
The cost of a data breach is significantly more than most realise, and the financial hit is a huge one that many small businesses may not recover from. So, as they say, prevention is better than cure.
Above all, attackers are looking for two factors in a victim. Firstly, ease of access. Secondly, the potential reward. Small businesses often check that first box with minimal cyber security measures. Furthermore, depending on the type of business, the data onboard may be ultra juicy and worth quite a bit financially. So, they may sell the information to other malicious parties, or hold the data hostage for a significant ransom. Don’t make it easy for them!
What are the Most Common Types of Cyber Attacks?
Cyber attacks come in various forms, each with unique tactics and goals. Here are some of the most common types of cyber attacks to be aware of:
Phishing Attacks
- Description: Phishing involves sending fraudulent emails that appear to come from legitimate sources. These emails often contain malicious links or attachments that can steal sensitive information or install malware.
- Example: A typical phishing scam includes emails that look like they are from a bank, asking you to update account information by clicking on a provided link.
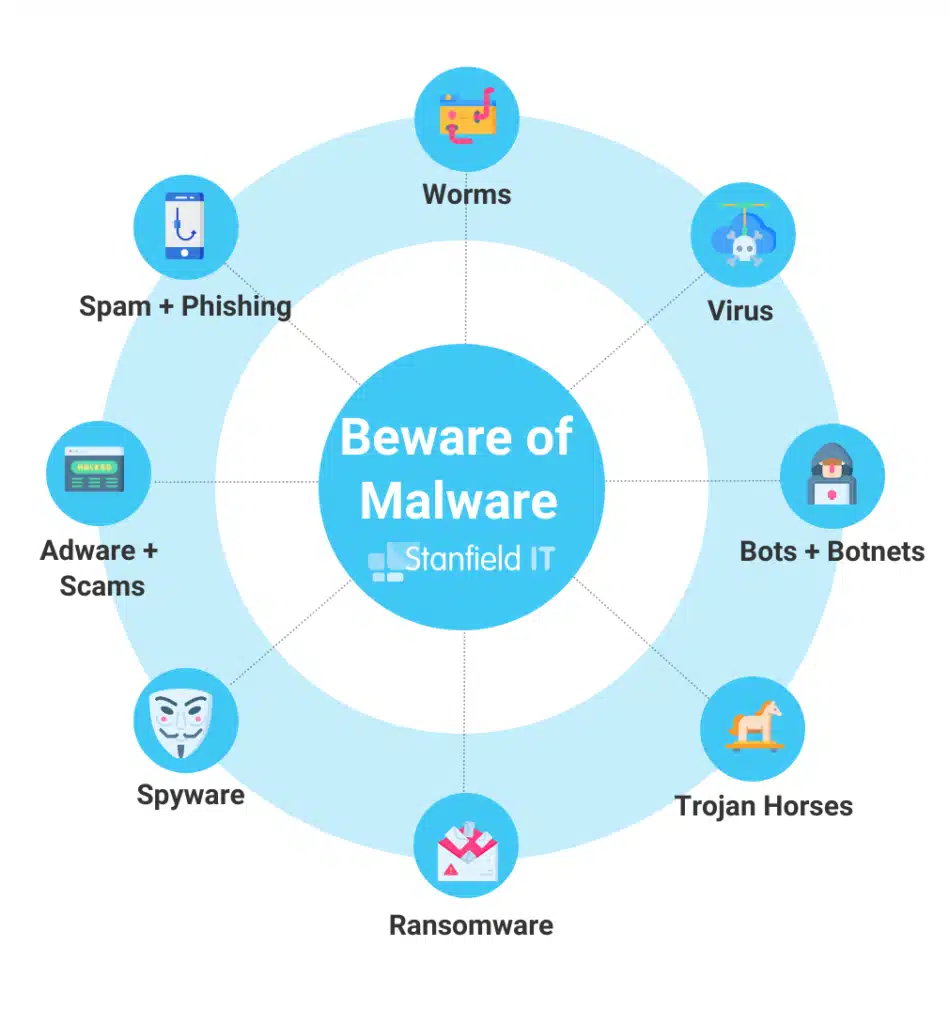
Malware Attacks
- Malware, (short for malicious software), includes viruses, worms, Trojans, and other harmful programs that can steal, encrypt, or delete sensitive data, take over computing functions, and monitor users’ computer activity. It can do a lot – and it’s effective. So, it’s no surprise that 560,000 new pieces of malware are issued by hackers every 24 hours.
Ransomware Attacks
- Description: Ransomware encrypts the victim’s files and demands a ransom to restore access. This type of attack can cause significant operational disruption and financial loss.
- Example: The WannaCry ransomware attack in 2017 affected hundreds of thousands of devices worldwide, demanding Bitcoin payments to decrypt the data.
Denial of Service (DOS) and Distributed Denial of Service (DDoS) Attacks
- Description: DoS attacks flood a system with traffic, overwhelming it and causing it to shut down. DDoS attacks use multiple systems to launch a coordinated attack, making it harder to defend against.
- Example: Think of an attacker using a botnet to flood a website with traffic, making it unavailable to users.
Man in the Middle (MITM) Attacks
- Description: MitM attacks occur when attackers secretly intercept and relay messages between two parties who believe they are communicating directly with each other.
- Example: Attackers might intercept communication between a user and a website to steal login credentials or personal information.
SQL Injection Attacks
- Description: SQL injection involves inserting malicious SQL code into a query input to gain access, modify, or delete data in your database.
- Example: An attacker might enter malicious SQL commands into a website’s login form to bypass authentication and access the system.
Supply Chain Attacks
- Description: Supply chain attacks target less secure elements in a business’s supply network. Attackers exploit vulnerabilities in third-party vendors to gain access to a primary target’s systems and data.
- Example: A hacker might infiltrate a software vendor and insert malicious code into a widely used software update, compromising all organisations that apply the update. See the Latitude Financial information below for a real world example.
Recent Cyberattacks in Australia
Cybercriminals are targeting Australian businesses at an alarming rate. So some, this does not come as a surprise. In the Australian Government’s 2023-2030 Cyber Security Strategy, The Minister for Cyber Security said Australia was a decade behind in the fight against cyber threats.
And we’re now seeing the result of that as more of our businesses suffer from attacks.
Latitude Financial Hack
Latitude Financial Hack
Latitude Financial is an Australian financial services company that offers consumer loans and a buy-now-pay-later (BNLP) scheme. In 2023, it was the victim of a significant cyber attack after the company detected suspicious activity on its systems.
Details of the Breach
The attack began with a major vendor used by Latitude Financial, believed to be a back end infrastructure provider.
The attacker obtained the login details of a Latitude employee and stole personal information.
The impact was severe:
- Approx. 7.9 million Australian and New Zealand driver’s licence numbers were stolen.
- 53,000 passport numbers were stolen.
- Roughly 100 customers had their monthly financial statements stolen.
- An additional 6.1 million records dating back to 2005 were stolen, 94% of which were provided before 2013.
Medibank
Background
In October 2022, Medibank, one of Australia’s leading private health insurers, detected unusual activity on its network.
Initial reports suggested that the incident had been contained and no sensitive data was accessed.
However, this was quickly contradicted when hackers contacted Medibank, claiming they had stolen 200 gigabytes of customer data.
Details of the Breach
The hackers provided samples of stolen data to Medibank as proof, revealing the extent of the breach. The compromised data included:
- Names
- Addresses
- Dates of birth
- Phone numbers
- Medical claims regarding personal diagnoses and procedures
It was eventually confirmed that the attackers had accessed the personal information and health claims of approx. 9.7 million current and former Medibank customers.
For some customers, the stolen data also included:
- Medicare numbers
- Passport numbers
- Health claims data
Response and Impact
Medibank decided not to pay the ransom demanded by the hackers.
Consequently, the attackers began publishing the stolen data on the dark web, exposing sensitive information to further malicious use.
The exact method of initial access remains unclear, but it is believed that the attackers used compromised login credentials to infiltrate Medibank’s systems.
This breach serves as a stark reminder of the vulnerabilities faced by organisations handling sensitive personal and medical information and underscores the importance of robust cyber security measures to protect against such attacks.
Optus
Background
In September 2022, Optus suffered a major data breach.
Disclosed on September 22, 2022, the incident exposed the personal information of millions of customers, making it one of Australia’s most significant cyber attacks.
Details of the Breach
The attack compromised the personal data of approximately 10 million Optus customers, including:
- Names
- Dates of Birth
- Phone numbers
- Email and home addresses
- Driver’s licence, passport, and Medicare numbers
Of the affected customers, 2.1 million had at least one form of identification document number stolen, with 1.2 million being current and valid.
Response and Impact
Optus took steps to contain the breach and notify affected customers but faced criticism of its handling of the situation. The company refused to pay any ransom to the hackers.
The Australian government and regulatory agencies launched investigations into Optus’s data protection practices and Slater & Gordon filed a lawsuit representing 100,000 affected customers seeking compensation.
How to Identify an Attack
1. My Email Account Was Hacked

What Signs Do I Look For?
Here are some signs that your email account has been hacked. Look for the following:
- Your password has changed
- There’s unusual inbox activity (check sent mail, read messages, no incoming emails)
- You’ve received password reset emails from other sites
- Account access from unexpected IP address/s (your email provider usually records this information) has occurred
- Your email contacts (whether within or outside of your business) let you know that they have received strange emails from you
How Did This Happen?
Email hacks usually occur by one of the following methods of attack:
- A password hack or brute force cyber attack
- Social engineering
- Phishing email
What Do I Do Now?
- Follow Recovery Steps: 1 — 6, 7
- Follow Up Steps: 9, 20, 23
2. System Account Details Are Compromised

What Signs Do I Look For?
- Your computer speed has slowed down significantly
- Your security software has been disabled or compromised
- Software or browser add-ons appear that you don’t recognise
- Additional pop-ups are happening
- Random shutdowns and restarts are happening
- You’ve lost access to your account
How Did This Happen?
- Your email was hacked/compromised and used to access another account
- Phishing
- Password hack
- Man In The Middle attack
- Watering Hole Cyber Attack
- Unpatched Software
What Do I Do Now?
- Follow Recovery Steps: 1 — 6, 7, 8, 13, 14, 18, 21
- Follow Up Steps: 9, 20, 22, 23
3. My Online Storage Account Was Hacked

What Signs Do I Look For?
Some examples of online storage accounts include DropBox, Google Drive, OneDrive, and iCloud.
- Your site suddenly has content that shouldn’t be there
- You cannot access your account
- Files are missing/altered
- There’s unusual outbound network traffic
- You’re being notified of unexpected access locations and logins
- A large number of requests for the same object/file have been received
- Suspicious admin activity (see the previous attack)
- Excessive read operations (someone is trying to gather data)
- Contacts are receiving emails with files/links to open (make sure they don’t open them!)
How Did This Happen?
- System account was compromised
- Phishing
- Social engineering cyber attack
What do I do now?
- Follow Recovery Steps: 1 — 6, 7, 8, 9, 13, 14, 15, 16
- Follow Up Steps: 19, 20, 22, 23
4. I Received a Blackmail Email Demand

What Signs Do I Look For?
- An email stating that they have incriminating evidence on you (this may or may not be a bluff)
- An email may claim they have accessed your password through a keylogger
- They threaten to expose you to your contacts
- They make a demand for payment (most likely in Bitcoin)
How Did This Happen?
- Phishing attack
- Ransomware download
- Your account was involved in another data breach
What Do I Do Now?
- Follow Recovery Steps: 1 — 6, 7, 8, 10, 11, 19
- Follow Up Steps: 9, 20, 22, 23
5. My Social Media Has Been Hacked

What Signs Do I Look For?
- Changes to your follower count
- Friend or contact requests you didn’t make
- Duplicate accounts requesting your friends/contacts
- Posts that you did not make
- Old posts suddenly deleted
- Password has been changed
- Notification that your account was accessed from a new location/device
How Did This Happen?
- Phishing email appearing to be from Facebook/other social media website
- Sneaky social media apps
- Malicious link within Facebook/Twitter
What Do I Do Now?
- Follow Recovery Steps: 1 — 6, 7, 15
- Follow Up Steps: 20
6. Our Network Has Been Attacked

What Signs Do I Look For?
- Your files and/or server has been encrypted
- Network becomes very sluggish/slow
- Your data usage is unusually high
- Programs are continually crashing
- You received a ransomware message
- Computers are functioning without local input
How Did This Happen?
- Ransomware
- Malware attack via phishing
- Rogue software
- Physical access
- Social engineering
What Do I Do Now?
- Follow Recovery Steps: 8, 13, 14, 15, 16, 18, 19, (17 if required)
- Follow Up Steps: 9, 20, 21, 22, 23
7. There’s Been a Fraudulent Financial Transaction

What Signs Do I Look For?
- Money has been transferred to the wrong account
- Account deductions that you didn’t authorise
- Suspiciously large orders that don’t match usual order activity
- Unexpected invoices that have not been verified
- Large payments not arriving despite remuneration advice
- Advice to change address or bank details without the appropriate cross-checks
How Did This Happen?
- High ranking accounts compromised ― submitting payment requests to the accounts department. An example of this is hackers posing as the director, requesting accounts to submit a payment to X account
- Man in the Middle (posed as a financial institution)
- Invoice details were changed through a compromised system account (eg Xero, MYOB account, or accounting system login)
- Payroll/AR/AP has been hacked via phishing, social engineering, or malware
What Do I Do Now?
- Follow Recovery Steps: 1 — 6, 7, 8, 12, 13, 14, 15, 16, 19, 24
- Follow Up Steps: 9, 20, 21, 22, 23
8. We Got Infected With A Malware Cyber Attack

What Signs Do I Look For?
- Excessively slow computer processing
- Programs opening and closing automatically
- Lack of storage space
- New programs/add-ons that you did not install
- Security software disabled
- Excessive popups
- Browser keeps redirecting sites
How Did This Happen?
- Phishing
- Rogue software
- Opening or executing a malicious file (either by email or removable media)
- Insufficient firewall protection
- You allowed a program to install bundled add-ons
- Unpatched software/operating system
What Do I Do Now?
- Follow Recovery Steps: 8, 18, 13, 15, 19,
- Follow Up Steps: 9, 20, 21, 22, 23
9. I Received a Suspicious Phone Call

What Signs Do I Look For?
- You’re being offered money or a free product that you didn’t enter to win (reminder: if it seems too good to be true, it usually is)
- Any call that claims to have detected viruses or infections on your computer
- Calls that claim you owe taxes or other government payments
- If the caller deflects or refuses to answer your questions
- The caller is pushing you to make an immediate financial decision
- The caller is threatening deportation or arrest
How Did This Happen?
- You submitted information somewhere that sold your information to a third-party
- For example, you entered a raffle or sweepstakes, or signed a petition
- You recently signed up for a service or website
- Social media ― your profile may be too public, and scammers used public information against you
What Do I Do Now?
- Follow Recovery Steps: 1, 6, 11, 25, 13
- Follow Up Steps: 20, 23
Cyber Attack Recovery Steps
1. If you still have access to the account, immediately change your password to something more secure
A tip for creating a secure (yet memorable) password, is to create a phrase or selection of random words together. Something like Grass Silver Calculator Seven is a random combination of words that is simple enough to remember but difficult to guess. Google has a great guide for creating a strong password.
Here a few tips:
- Make it unique – Use a different password for each of your important accounts.
- Make it long – A password should be at least 12 characters.
- Don’t include personal info – This includes birth dates, street addresses, or the name of your child or pet.
2. Update your recovery contact information
Often we rely on recovery information to get back in to our accounts.
Recovery contact information usually includes a different email or phone number linked to the account you’re trying to access. They can help you reset your password when:
- You have forgotten your password
- You think someone else is using your account
- You’ve been locked out of your account after a cyber attack
However, if an unwanted individual gains access to your account, your recovery options might be at risk too. So, make sure you update them as well as your main account.
And remember to keep these recovery options up to date and secure, you never know when you might need them.
3. Advise your email contacts so they know to question suspicious emails
If you have been hacked then you need to alert your email contacts so that they can identify suspicious activity.
Just a tip ― it’s best to do this in another medium other than email so they aren’t mixed up with the suspicious emails. Contact your contacts by phone, or even put out a social media post.
However, if you have to alert some contacts via email, see below for a template:
To our contacts,
We have recently been made aware that (insert your business’s name) has been targeted by criminal activity.
We became aware of this on (insert incident date). A malicious actor may try to/may have emailed our contacts impersonating our business and staff. These emails may be in relation to invoices, requests for large transfers, or to changing banking details for payments. The following accounts were compromised (insert hacked/impersonated email address).
If you receive an email from (your business name) that matches this description, please ignore the email’s contents and send it to us for investigation. Please also check with your bank whether any payments have been made to fake invoices or fraudulent bank details.
Please remain vigilant, the malicious actor may continue to impersonate our employees, including email signature, names and email addresses. If you are suspicious of any email you receive from (your business’s name), please contact us via a phone number you know is correct for confirmation.
Regards,
Your business’s name
4. Change your security question/s
After a cyber attack it’s important to change your security questions too. It may be unclear how the attacker hacked your account, so all possibilities are on the table. This includes by guessing the answer to your security questions. Malicious actors can do simple research to find out the answer to common security questions like ‘What high school did you attend?’. Information like this could be on your Facebook or LinkedIn account.
- Change Your Security Questions for Apple
- Tips for Creating a Good Security Question
5. Configure your email settings
In some cases, hackers will change your email settings to forward a copy of each email your receive to themselves. They do this so that they can scour your emails for any sensitive details that might help them log into other accounts. Check your email settings to make sure that no unwanted email addresses were added, and change if necessary.
6. Update any other accounts with the same password
We recommend that you use a different password for every account you have. This is because once an account is compromised, any account that has the same login details can also now be easily accessed.
Use the site Have I Been Pwned to see if your password has been compromised, or look here for any compromised email addresses.
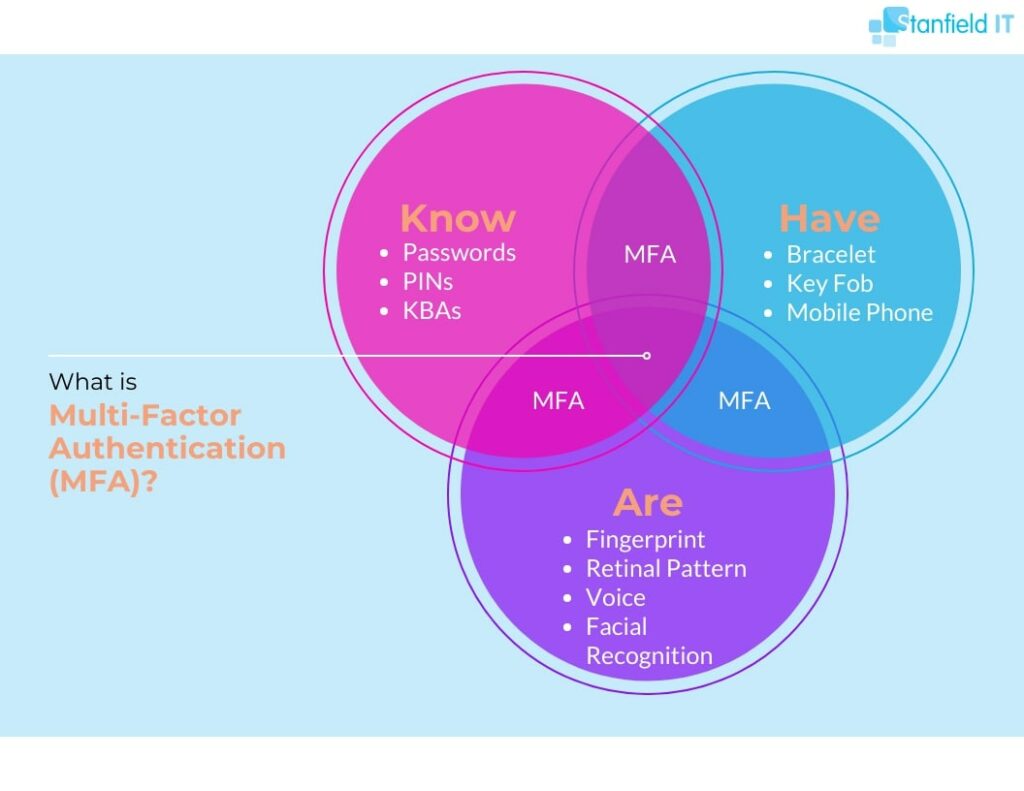
7. Enable Multi-Factor Authentication (MFA)
If you’re not already using it, MFA will help reduce of the risk of account compromise in the future. It does this by requesting something you know (e.g. a password), something you have (e.g. a mobile phone), and something you are (e.g. fingerprint).
8. Perform a security scan for malware
Malware is software specifically designed to gain unauthorised access to a system. If you don’t have a tool to scan for malware, here are some great anti-malware programs you can use:
9. If you haven’t already, implement the ‘Essential Eight’ as laid out by the ACSC
The Essential Eight is easy to remember and an effective list of strategies you can use to reduce your risk of attack. We’ve given an overview of these steps here in an easy-to-read format. These are a must-do, regardless of if you have had a cyber attack.
10. Do not engage the blackmailer
If you’re a victim of a ransomware cyber attack, then it can be tempting to just pay the attacker. After all, once you’ve paid everything will return to normal, right? Not exactly.
Our advice (and advice from the ACSC) is to never pay the ransom. It might seem like the quickest and easiest solution, but there are some serious second and third order consequences of paying a ransom.
- Paying the ransom will not guarantee the restoration of all your data. Research suggests that only 8% of companies who pay a ransom manage to recover all their data. Often hackers cannot decrypt their own files even after receiving the ransom.
- If you pay the ransom, you are incentivising hackers to continue deploying ransomware attacks.
You can read this article for some great steps to take when confronted with cyber blackmail.
11. Contact the ACSC for support
The ACSC (Australian Cyber Security Centre) is the Australian resource and body for reporting any cyber attacks you may experience. The ACSC will evaluate your crime report and can direct your case to relevant law enforcement.
12. Call your financial institution and freeze the account/s
Alert your bank/financial institution that you suspect sensitive information has been stolen or accessed. If you’ve noticed that suspicious activity has occurred, you can have your account cancelled or suspended. Alternatively, you can submit a request for a 90-day alert. This will allow you to continue to use your financial account, but the account will be monitored for any suspicious transactions.
If a customer or client has lost money due to the cyber attack, encourage them to report it to their financial institution.
13. Communicate with your team and keep them updated
Effective communication can stop a bad situation from getting worse. It’s important that you:
- Ensure you have open communication channels with your team
- Be honest with your team about where things stand
- Keep them informed so they know to be on high alert
- Schedule a meeting to inform them in person, as mass emails can often go unread
14. Notify the OAIC if you need to comply with the NDBS after a cyber attack
If your business is covered by the Privacy Act 1988 then you are required to notify the OAIC of a data breach that is likely to result in serious harm to individual’s whose personal information is at risk. For more, you can read our guide on the Notifiable Data Breaches Scheme (NDBS).
15. Notify any affected users
In addition to notifying the OAIC, you are required to notify any individuals who may be harmed by the data breach due to their personal information being compromised. The OAIC has a guide on how to go about notifying affected users of a data breach.
16. Follow your Business Continuity Plan
A business continuity plan is a easy-to-follow documented plan on how your business can prepare for and recover from a cyber attack. If you don’t have a business continuity plan, you need to make one now.
A business continuity plan should contain all critical business information needed to ensure your business can quickly get back up and running following an incident. This includes contingencies for business processes, assets, human resources and business partners. In short, a plan for every aspect of your business that could be affected.
To cover everything a business continuity plan should include is out of scope for this article. But at the very least, you want to include:
- A risk management plan
- An incident response plan
- A recovery plan
- A testing, evaluation and update schedule
Click here for a business continuity plan template.
17. Restore from a backup
Data backups ensure you have a copy of systems ready to be restored immediately. It’s important to schedule regular backups for your system and keep them stored safely. Not just because of potential cyber attacks either, it’s not unheard of for simple acts of human error to result in significant loss of business data.
Here’s a guide to backup for Windows. Alternatively, you can talk to your IT managed service provider about ongoing backups for your network.
18. Isolate the infected site (disconnect endpoints and server from rest of the network)
You don’t need to shut down your entire network. In fact, that could do more harm than good. Quickly isolate infected devices to limit the impact of the attack. Your security protection software should have a guide for doing this (e.g. Symantec ATP). From there, your incident response team can analyse the attack and identify if any damage occurred.
19. Call IT security professionals for specialised assistance
If you don’t have a managed services provider then you should find a reputable team to assist you with your issue. Then, look at implementing IT managed services for your business to prevent the issue in future.
20. Refresh your cyber security training for yourself and your team
You’ll want to brush up on your cyber security training while the attack is fresh in your team’s mind. Most IT service teams will offer this as a service to your business. Cyber security training will give you and your team the knowledge needed to stay safe online. If large scale cyber security training isn’t within your budgetary capabilities, there are some helpful online resources you can use to build your cyber security knowledge.
21. Review monitoring systems to identify and understand how the threat entered
The following network monitoring tools can help with this:
22. Document the process from identification, to containment and recovery
Creating cyber security documentation of an incident is a great way to provide valuable learning for future events. You can also use documentation to improve your Business Continuity Plan. Take note of:
- How the threat entered
- How it was managed
- What can improve
Cyber security documentation is often neglected, however it can contain valuable information that helps limit the impact of future attacks.
23. Consider employing an IT company to perform network monitoring and manage your cyber security
There are plenty of reasons why your business needs a managed service provider. Perhaps most importantly, managed IT services are one of the most cost effective ways to protect your business from a cyber attack. Employing a cyber security professional full-time doesn’t come cheap. Often it makes sense to outsource your cyber security management instead.
24. Report the Cyber Security Incident to ACSC
Reporting to the ACSC helps them identify greater patters of cyber attacks and in the development of new policies. You can submit a report here.
25. Report the scam to ACCC
Finally, you can report scams to the Australian Competition and Consumer Commission (ACCC). Reporting to the ACCC means they can advise Australian businesses about new scams to watch out for, creating a stronger cyber security resilience in the population. You can submit a report here.
Conclusion
Hopefully you never need these tips. A cyber attack is a stressful event, no matter what size your business is. However, by reading these tips you’re in a much stronger position to identify and respond to a cyber attack.
If you’re concerned your business is under threat, click here. Simply fill out the form and you’ll get a free 30-minute consultation.
Lastly, try our free online cyber security assessment to receive expert recommendations on how you can make your business more secure.
