Healthcare organisations are constantly under threat from ransomware.
And as our medical institutions become increasingly reliant on technology, the threat of ransomware only grows.
Unfortunately, when it comes to healthcare, this creates the potential not just for a breach of data, but to endanger lives.
Sophos’ “The State of Ransomware in 2023” whitepaper serves as a stark reminder for all healthcare professionals: this threat is real – and it’s escalating.
Using data from a survey of 3,000 IT and cyber security leaders across the globe, the report diagnoses the prevalent risks and symptoms of ransomware infiltrations within the industry.
In this article, we’ll unpack Sophos’ critical findings, turning data into actionable insights for you.
We aim to provide a ‘prescription for prevention’ that could help shield our vital healthcare organisations from the ransomware epidemic.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
Key Findings From Sophos Whitepaper on Ransomware in Healthcare
Data from Sophos’ whitepaper paints a concerning picture or cyber security in the healthcare sector. Here are the key findings that every healthcare IT professional should be aware of:
- Incidence Rate: The report indicates that a significant portion of healthcare organisations have been hit by ransomware in the past year. This highlights how common the threat is.
- Financial Impact: The financial repercussions extend beyond just ransom demands. They also affect operational budgets and resource allocation within affected organisations.
- Operational Downtime: Many healthcare providers faced substantial downtime due to ransomware attacks. This leads to critical delays in patient care and access to essential services.
- Data Recovery: The whitepaper highlights a surprising statistic about the amount of data healthcare organisations could recover post-attack. This raises questions about current backup and disaster recovery strategies.
- Cyber Security Investment: In response to the growing threat, there’s been an increased investment in cyber security measures.
- Ransom Negotiations: An analysis of how often healthcare organisations opt to negotiate and pay ransoms, and the implications of doing so.
- Preparedness and Response: Despite increased awareness, the survey reveals gaps in preparedness and response planning. This signals an urgent need for more robust incident response protocols.
These findings make one thing clear; those in the industry need to do more to enhance their defences.
Ransomware Incidents in 2023
In 2023, we’ve seen healthcare continue to be ambushed by ransomware incidents. Here’s what healthcare organisations face:
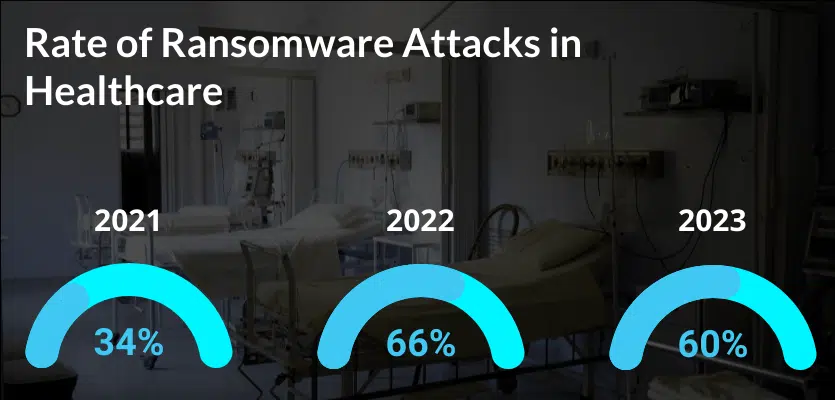
- Prevalence: 60% of healthcare organisations reported experiencing at least one ransomware attack, indicating a substantial risk of exposure in the sector.
- Severity of Attacks: The percentage of organisations that took more than a month to recover has increased to 28%. This is up from 28% the previous year, highlighting an increased severity of incidents.
- Response and Recovery: Recovery speed varied, with 47% of healthcare organisations recovering within one week. This is a decrease from 54% the previous year. Those who relied on backups for recovery fared better than those who paid the ransom.
- Cyber Security Readiness: The incidents underscored the different levels of preparedness across the sector, prompting many to recognise the need for improved cyber security defences and incident response strategies.
This section underlines the reality that no healthcare organisation is immune to ransomware. The industry must continuously work to better protect sensitive data and critical infrastructure.
Common Attack Vectors
The Sophos report shed light on how ransomware makes its way into healthcare systems.
Understanding how ransomware gets in is critical for healthcare IT teams to defend their business effectively. Here are the typical pathways through which ransomware has entered organisations.
Phishing Emails
Often the starting point for ransomware. Phishing emails remain a significant threat, with attackers using sophisticated social engineering techniques to deceive recipients into downloading malicious attachments or divulging sensitive information.
Unpatched Vulnerabilities
Attackers often target software flaws that haven’t been fixed. Keeping up with software patches is a key part of the Essential Eight strategies for cyber security, helping to block these common entry points for ransomware.
Inadequate Endpoint Protection
With many healthcare devices connected to the network, insufficient endpoint protection provides a gateway for ransomware to infiltrate and spread across an organisation’s infrastructure.
Insider Threats
Whether they are intentional or accidental actions by insiders can lead to ransomware incidents. This highlights the need for strong access controls and user training.
Insecure Third-Party Services
Healthcare organisations often work with numerous vendors. Because of this, healthcare organisations often become a conduit for attacks. This emphasises the need for stringent vendor risk management.
Each of these vectors represents a potential weakness. They also represent opportunities for improvement.
By focusing on these areas, healthcare organisations can significantly enhance their cyber security posture and resilience against ransomware attacks.
Ransom Payments Versus Data Recovery
Healthcare organisations must make a critical decision when faced with a ransomware attack.
Do they pay the ransom or attempt to recover the data through backups?
The Sophos whitepaper offers insight into the outcomes and considerations of each approach.
Should You Pay the Ransom?
Some organisations choose to pay the ransom as a quick path to regaining access to their data.
However, this is a risky option – not one to take lightly.
For instance, there’s a possibility that attackers may not provide the decryption key, so you won’t get your data back.
Additionally, paying the ransom incentivises criminals to continue ransomware activities and may make businesses a target in the future. Once they know you’ll pay they’re more likely to target you again.
A common consensus from governments worldwide is that organisations should not pay ransoms. However, this only works if everyone does it. As long as there is a viable market in ransomware – it will continue.
Recovering from Backups
The preferred and recommended approach is to restore systems from backups.
This strategy avoids funding criminal activities and encourages better preparedness.
Yet, the effectiveness of this method hinges on the organisation having recent and uncorrupted backups, coupled with an efficient recovery process.
Impact on Operations
Regardless of the choice made, both options come with significant operational impacts.
Paying the ransom may lead to quicker recovery but a high financial and ethical cost.
On the the hand, data recovery efforts are often time-consuming and may not fully restore all the lost data.
Don't miss out on our latest.
Join our subscribers and receive expert insights on cyber security and IT. Sign up now!
Preventative Strategies & Best Practices
The nature of ransomware attacks in the healthcare sector calls for more than just a reactive stance.
To effectively safeguard the life-saving services they provide, healthcare organisations must proactively improve their defences.
In this section, we’ll cover the preventative strategies and best practices that can lead to greater cyber resilience.
By embracing these practices, healthcare entities can reduce their vulnerability to ransomware attacks, ensuring continuity of care and protection of sensitive patient data.
Regular Employee Training
Your staff are the frontline of your cyber defences. Because of this, regular employee training is crucial.
This training should focus on raising awareness about the various forms of cyber threats, particularly phishing, which is a common entry point for ransomware.
Employees should be taught how to identify suspicious emails, links, and attachments. And how to respond when they do identify them.
Interactive sessions, simulations, and regular updates about the latest cyber threats can help keep this fresh.
In the end, the aim is to create a workforce capable of identifying and eliminating potential threats before they escalate.
A Word on Cyber Security Fatigue
Cyber security fatigue is a growing concern. It occurs when employees become overwhelmed by the constant vigilance required to maintain security protocols. This can lead to complacency and risky behaviours.
It’s important to address fatigue. Healthcare organisations should aim for a balanced approach in training, ensuring it’s engaging and not overly burdensome.
The following can help reduce this fatigue:
- Introducing varied and engaging training methods to prevent monotony in routine security practices.
- Using gamification to make learning more interactive and enjoyable.
- Recognising and rewarding employee efforts in maintaining security measures.
By recognising and addressing cyber security fatigue, healthcare organisations can maintain a higher level of vigilance among their employees.
Robust Backup Systems
A robust backup system is a major part of ransomware resilience, especially for healthcare organisations.
Ensure all critical data is regularly backed up, and that these backups are secure and easily recoverable.
This involves not only backing up data frequently but also ensuring that you store backups in a secure, offsite location or the cloud.
You’ll also want to regularly test these backups to guarantee that you can restore them quickly in an emergency.
By implementing a backup strategy, you reduce the risk of data loss and aid in data recovery following an incident.
Up-to-Date Security Protocols
Unsurprisingly, up-to-date security protocols are a critical defence against ransomware.
This includes regularly updating and patching software, operating systems, and security tools to protect against known vulnerabilities.
Healthcare organisations should implement a rigorous patch management program to ensure updates are made on time.
Additionally, they should conduct regular security assessments and audits to identify and address potential weaknesses in their network.
Incident Response Planning
Effective incident response planning can minimise the impact of a ransomware attack.
Healthcare organisations should develop a comprehensive incident response plan that outlines specific procedures to follow in the event of an attack.
This plan should include identifying key team members, defining communication protocols, and establishing steps for containment, eradication, and recovery.
Regular drills and simulations can ensure that the response team is prepared and can act quickly and effectively.
An effective incident response plan not only helps in managing the crisis but also in restoring operations. This in turn can reduce the potential harm to patient care and data security.
Vendor Risk Management
Third-party services are often intertwined with healthcare operations. Because of this, vendor risk management is crucial.
This involves conducting thorough security assessments of all your vendors and ensuring they adhere to strict cyber security standards.
Healthcare organisations should have clear contracts outlining the security expectations and responsibilities of each party.
Regular monitoring and auditing of vendor practices are essential to ensure ongoing compliance. By rigorously managing vendor risks, healthcare providers can close off a common avenue for ransomware attacks.
Conclusion
The landscape of ransomware in healthcare is a challenging but navigable terrain.
By understanding the threats outlined in the Sophos 2023 whitepaper and implementing the above strategies, healthcare organisations can improve their defences.
There is a collective responsibility to protect healthcare organisations, patient data, and the uninterrupted provision of critical healthcare services.
Some of our latest
Windows 10 End of Life (EOL) and What it Means
Microsoft has announced that October 14, 2025, will be the End of Life (EOL) date for Windows 10. Windows 10 EOL is set to affect all versions of Windows 10, including Home, Pro, Education, and Enterprise. Research from Lansweeper indicates that only 23.1% of...
ISO 27001 Certification in Australia: A Comprehensive Guide
Business data is like a treasure for cyber criminals. In fact, buried in almost every organisation's information assets are details worthy of holding ransom. So, how do you protect it? With ISO 27001 certification. ISO 270001 is more than just a standard industry...
Cyber Hygiene For Business: What You Need To Know
Implementing cyber hygiene practices is one of the most effective ways to protect your business from cybersecurity risks. As a business owner, the security of your company's data is paramount. With the prevalence of cyber-attacks in the modern world, it’s increasingly...



