Cyber attacks are creating news headlines every week, so it’s essential for businesses to boost their cyber resilience. Cyber resilience is critical in the digital economy business now operate. It refers to your business’s ability to handle any cyber threats that come its way. You not only need to be able to prevent and defend against cyber-attacks but detect, manage and recover from them too.
Don’t be the next statistic; read this post to learn more about cyber resilience for business and what you can do to remain secure.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
What is Cyber Resilience?
Cyber resilience is a set of strategies, processes, and tools used to protect businesses from cyber-attacks. It involves a proactive approach to prevent, detect, and respond to cyber-attacks. By creating a secure and resilient IT infrastructure, organisations can minimise their risk of cyber-attacks and associated financial losses.
Cyber resilience is essential for businesses of all sizes and industries. With the ever-increasing sophistication of cyber-attacks, businesses must be proactive about protecting their digital assets.
Cyber resilience helps organisations build a culture of security that focuses on prevention and responding quickly and efficiently to cyber threats.
Components of cyber resilience relevant for businesses include:
-
- Cyber Security: The methods used to prevent, detect, and respond to cyber-attacks. This can include tools such as antivirus software, firewalls and employee awareness training.
- Risk Assessment: Conducting regular risk assessments to identify and evaluate potential risks posed by cyber-attacks and develop a plan to mitigate them.
- Security Management: Putting in place security policies and practices that are regularly monitored and updated. This includes protecting user accounts with strong passwords and providing staff with cyber security awareness training.
- Incident Response: Developing an incident response plan that includes procedures for assessing and addressing any security incidents. This plan should include who to contact in the event of a breach, how to contain the incident, and how to communicate with affected individuals.
- Business Continuity: Establishing a plan to ensure business operations can continue during a cyber-attack or other disruption. This includes having backup systems in place and establishing communication protocols for managing disruptions.
Protect your business from cyber attacks. Safeguard customers and end-users, and create a clear picture of your cyber security landscape.
Unfortunately, many organisations fail to implement basic cyber resilience measures, leaving them vulnerable to cyber attacks that are preventable. For example, many companies are not taking advantage of two-factor authentication, password managers, and other simple security measures which could have helped them avoid data breaches. By adopting cyber resilience measures, businesses can ensure that they are ready for any potential cyber threats.
How Cyber Resilience Benefits Businesses
1. Protection From Attack
When businesses take the necessary steps to become cyber resilient, they can help protect themselves from data breaches, malware attacks, and other malicious activities. Cyber resilience allows businesses to better detect and respond to threats in real time, reducing the risk of attackers gaining access to sensitive information. Cyber resilience also helps ensure that business’s detect and address data breaches quickly and effectively.
2. Business Continuity
Businesses need to be able to continue operating following a cyber-attack. Cyber resilience can help ensure critical services remain running during any disruption. This reduces the amount of downtime experienced, allowing businesses to stay operational.
3. Customer Confidence & Trust
Customers want to know that their data is secure and that they can trust the business they are interacting with. Cyber resilience can help build trust and confidence by ensuring the protection of customers’ data and reassuring them that their data is secure. This can ultimately lead to increased customer loyalty.
Best Practices for Cyber Resilience In Your Business
Engage Everyone

Employee engagement is an important part of any cyber resilience strategy.
It is essential that everyone in your business understand the importance of cyber resilience and their role in protecting their company’s data. Employees need to develop the knowledge and skills to identify and respond to potential threats. They also need to be able to follow best practices for data security.
Business owners should provide incentives for employees to take ownership of cyber resilience strategies. This could include making it part of their job responsibilities, offering rewards or bonuses for successful implementation of security measures, or providing feedback on their efforts. Regular reviews should also be conducted to ensure that employees follow best practices and stay informed about new industry developments.
Ultimately, employee engagement is essential for any cyber resilience strategy. By equipping employees with the knowledge and tools necessary to help protect the organisation, businesses can ensure that their data remains secure and confidential. In addition, it helps create a culture of security within the organisation that encourages everyone to take ownership of cyber resilience efforts.
Be Responsive

Cyber threats are constantly evolving, so you need to do so too. The policies and procedures
you implement today may not be applicable tomorrow. Additionally, annual review cycles may not be frequent enough to address emerging issues.
It’s clear that being responsive is essential for businesses to keep up with the rapid pace of cyber threats. Your business needs to stay ahead of the curve and respond quickly and effectively to any incident.
Responsive governance means developing a culture that encourages employees to report cyber security incidents quickly, adopting policies that provide clear guidance on how to respond in the event of a cyber attack, and having mechanisms in place to regularly monitor and update security measures.
Use Cyber Risk Management

Cyber risk management is the process of identifying, assessing, and managing the potential risks of a cyber security attack on your business. This process involves understanding the threats that can come from both internal and external sources and taking steps to protect against them.
By having a clear understanding of the potential risks posed by cyber threats, you can create policies and procedures to help protect your business and its assets. This includes network security, data security, access control, user authentication, and more. Additionally, it includes ensuring that the systems in place are regularly updated with the latest security patches and that employee awareness and training are at an appropriate level.
In addition to being proactive about preventing attacks, cyber risk management also helps businesses respond effectively when a threat does occur. This includes having plans in place to identify, assess, and contain any incident, as well as minimise the impact of a cyberattack. It also involves implementing strategies to ensure that any lost data or confidential information is quickly recovered and that all affected systems are brought back online safely.
By taking steps to build an effective cyber risk management strategy, businesses can better prepare for any potential attack. It’s important to recognise that even the most secure systems can still be vulnerable to attack, so developing a comprehensive cyber resilience plan is essential to reducing the impact of a breach. Cyber risk management is an important part of a comprehensive cyber resilience strategy that can help businesses mitigate their risk and protect themselves from potential threats.
Promote Awareness and Training

Cyber awareness and training are critical components to cyber resilience in business.
Cyber awareness training helps employees understand the risks of cyber threats and how to protect themselves and their company from potential data breaches or other malicious activities.
To effectively prevent cyber attacks, employees must be made aware of:
-
- The types of threats that exist.
- The techniques criminals use to gain access to sensitive information.
- The steps they can take to protect themselves.
Your business might also consider investing in cyber security awareness software, which can provide employees with real-time notifications of any suspicious activity. It can also provide employees with tailored advice on responding to threats. This type of software can quickly identify high-risk activities, such as when an employee clicks on a malicious link or tries to access a restricted network area.
By investing in cyber awareness and training initiatives, organisations can reduce the chances of their employees falling victim to cyber threats. This helps create a safer work environment for everyone and can help businesses save money by reducing the risk of costly data breaches. It also ensures that employees have the necessary skills and knowledge needed to detect, respond, and recover from potential cyber-attacks.
By taking proactive steps to increase cybersecurity awareness among employees, businesses can create a stronger cyber-resilient environment. Regularly scheduled awareness training is a great way for businesses to ensure their employees are kept up to date.
Use Protective Measures and Controls

The protective measures and controls in place for your business can greatly impact your cyber resilience.
For a start, your business should implement, or make it a priority to implement the ACSC’s ‘essential eight’.
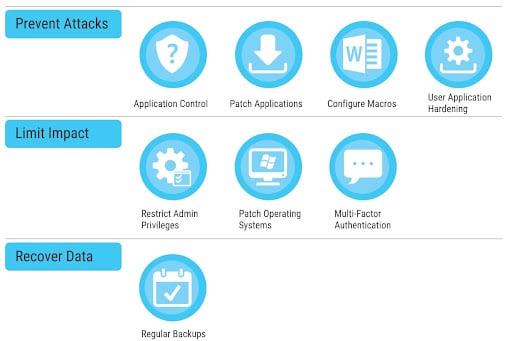
These are:
- Application control
- Patch applications
- Configure MS Office macro settings
- User application hardening
- Restrict administrative privileges
- Patch operating systems
- Multi-factor authentication
- Regular backups
When sending sensitive data over the internet, it’s important to use encryption technology to protect it from unauthorised access. Businesses should also use secure protocols such as Secure Socket Layer (SSL) or Transport Layer Security (TLS). Additionally, businesses should use Virtual Private Networks (VPNs) when accessing confidential information from outside networks.
Other cyber security controls include antivirus software, firewalls, usernames and passwords.
Incident Detection and Response

Incident detection is the process of proactively monitoring and analysing events and logs from multiple sources. This includes network, system, and application logs, as well as user access records. By analysing these logs, security professionals can identify unusual or suspicious activity that could indicate an attack or breach.
Once a threat has been identified, the next step is to investigate the incident and determine its impact on the organisation. This may include gathering evidence, conducting forensic analysis, and interviewing potential witnesses. The investigation should be comprehensive, and all relevant data should be collected and analysed.
The last step is to respond to the incident. The response should be tailored to the specific incident and should include measures such as patching vulnerable systems, restoring lost data, or implementing additional security controls. It’s also important to communicate the incident internally, as well as to any external stakeholders or customers who may have been affected.
Overall, incident detection and response are critical for ensuring that organisations remain resilient against cyber threats. By proactively monitoring their systems, investigating any potential threats, and responding quickly, organisations can protect themselves against damage or disruption. Incident detection and response are key components of a robust cyber resilience strategy.
Business Continuity

Business continuity is an essential component of cyber resilience because it ensures that an organisation can continue to operate in the event of a cyber incident.
By having a business continuity plan in place, organisations can minimise the damage caused by a cyber incident and ensure that they can quickly return to normal operations.
Your business should use a business continuity plan to identify the critical systems and processes essential to the organisation. This includes everything from IT systems and networks to financial systems and customer service. Once these critical systems have been identified, the organisation can then develop a plan for how to maintain or restore them in the event of a cyber incident.
Conclusion
Cyber resilience is an essential step for any business to take in order to protect its data and operations. By having a secure and resilient system, businesses can be prepared for potential threats and recover quickly from cyber-attacks.
The benefits of cyber resilience are significant. And businesses can have peace of mind knowing that they are protected. As the digital world continues to evolve, the need for cyber resilience will become even more crucial.
We are dedicated to helping businesses build cyber resilience by providing security solutions tailored to meet their needs. We understand the importance of being secure and resilient in a rapidly changing digital landscape. Visit our cyber security services page to learn more about how we can help your business stay resilient.
