Avoiding cyber security mistakes is a must for any business, but slipping up is often easier than expected.
People do all kinds of things that put an organisation’s security at risk. Often without a second thought. These lapses, often due to human error, are a leading cause of cyber incidents.
Typically, our articles focus on what you should do. Today, however, we’re taking a more direct approach. We’ll delve into 13 critical cyber security mistakes that you and your employees must avoid. For each one, we’ll provide clear and actionable advice.
Whether you’re fine tuning your current setup or starting from scratch, this guide is aimed at helping you build a more secure and efficient IT framework for your business.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
1. Using Weak Passwords
One of the most common cyber security mistakes is the use of weak passwords. In a study by Bitwarden, 23% of Australian respondents claimed to have experienced a data breach. Yet 55% of respondents relied solely on their memories to manage their passwords.
This indicates that people are using memorable (and therefore easy to guess) passwords.
Employees often opt for simplicity over security, using basic combinations or repeating passwords across multiple accounts.
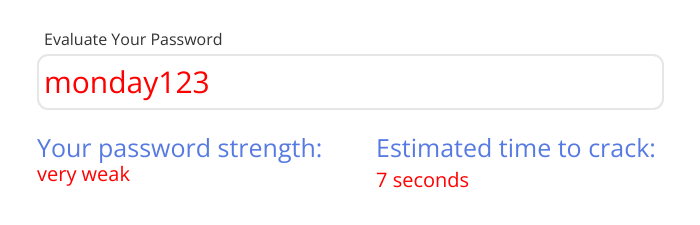
This makes it incredibly easy for cybercriminals to gain access to sensitive information.
What To Do
Encourage your team to create a strong, unique password for each account. Strong passwords have a mix of letters, numbers, and symbols, and are at least 12 characters long.
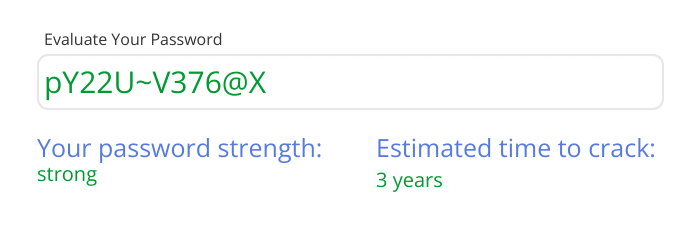
Consider using a password manager for your team (and even personally). They can generate and store passwords securely.
Good password managers include:
2. Ignoring Software Updates
Another common mistake is ignoring software updates. We get it, these updates are often viewed as a nuisance or a task for later (or never). However, this is a dangerous mindset and can leave your system vulnerable to known security exploits.
Why? Because outdated software is vulnerable software. They are called updates for a reason. By delaying or ignoring them, you’re leaving the door wide open for attackers.
What To Do
Make it a policy to regularly update all software. This includes operating systems, applications, and security tools. Set up automatic updates where possible. Alternatively, you can schedule a regular maintenance window to apply updates manually.
Educate your team on the importance of these updates. While they do often bring about new features; they’re also critical for patching security flaws and protecting data. This needs to be emphasised.
For larger organisations, consider automated management tools to streamline this process and ensure no software component is left outdated.
3. Neglecting Regular Backups
This one always surprises us. Another common oversight in many businesses is the lack of regular data backups.
Backups are your safety net in the event of data loss due to hardware failure, cyber attack, or even accidental deletion. Without regular backups, you risk losing your business data forever.
In some cases, that’s game over. Research indicates that 93% of businesses that suffer from catastrophic data loss do not survive.
What To Do
Implement a strong backup strategy that includes regular backups of all critical data. This needs to be a continuous process, not a one time event. Utilise both on-site and off-site backup solutions for redundancy.
Consider automated backup solutions that can perform backups at scheduled intervals. This means your data is routinely backed up without manual intervention.
Test your backups regularly to guarantee they can be restored successfully. This step is often neglected, but it’s crucial to know your backups are reliable. You don’t want to find out the hard way.
Finally, be sure to educate your team on the importance of backing up their work. Encourage a culture of data responsibility, where protecting company information is a shared priority.
4. Poor Email Security Practices
While email is a fundamental communication tool in any business, it’s also a common entry point for cyber threats. Poor email security practices can expose your organisation to significant risks like phishing, malware, and spam.
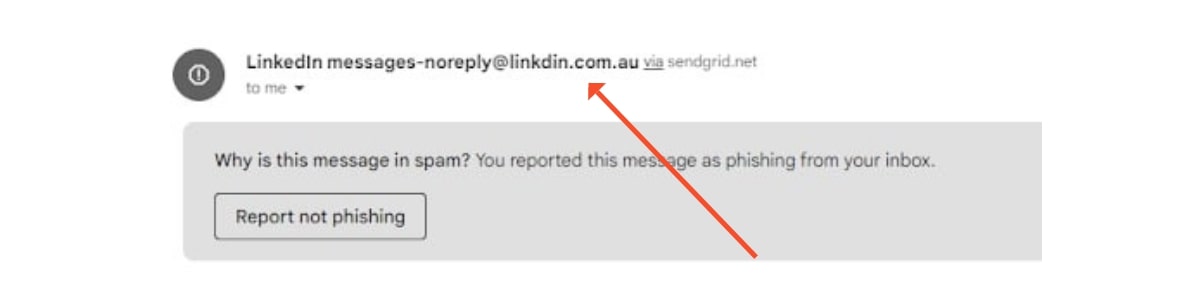
What To Do
- Implement strong email security measures. This includes using email filtering tools to catch spam and phishing attempts before they reach your inbox.
- Educate your employees on the dangers of phishing emails. Teach them how to identify and handle suspicious emails.
- Encourage cyber hygiene through the use of strong passwords and multi-factor authentication (MFA) to add an extra layer of security.
- Advise employees to remain vigilant against attachments and clicking links in emails, especially if they are from an unknown or unexpected source.
- Regularly update and patch your email software.
5. Overlooking Mobile Device Security
Just like your more traditional work devices, smartphones and tablets can be gateways to sensitive data, especially with the rise of remote work and BYOD (Bring Your Own Device) policies.
Because of these shifts in how we’re doing business, there’s a need to secure these devices.
Don't miss out on our latest.
Join our subscribers and receive expert insights on cyber security and IT. Sign up now!
What To Do
For starters, implement a comprehensive mobile device management (MDM) policy. This should cover aspects like secure access to business networks, encryption of data on devices, and the ability to remotely wipe data in case of device loss or theft.
You also want to ensure that all mobile devices connected to your business network have updated operating systems and security applications. Regular updates are just as important for mobile devices as they are for regular devices.
Again, educate your employees on securing their devices. This includes being cautious of public Wi-Fi networks and recognising the signs of a compromised device. You can also use VPNS (Virtual Private Networks) when accessing corporate data on mobile devices, especially when using public Wi-Fi networks.
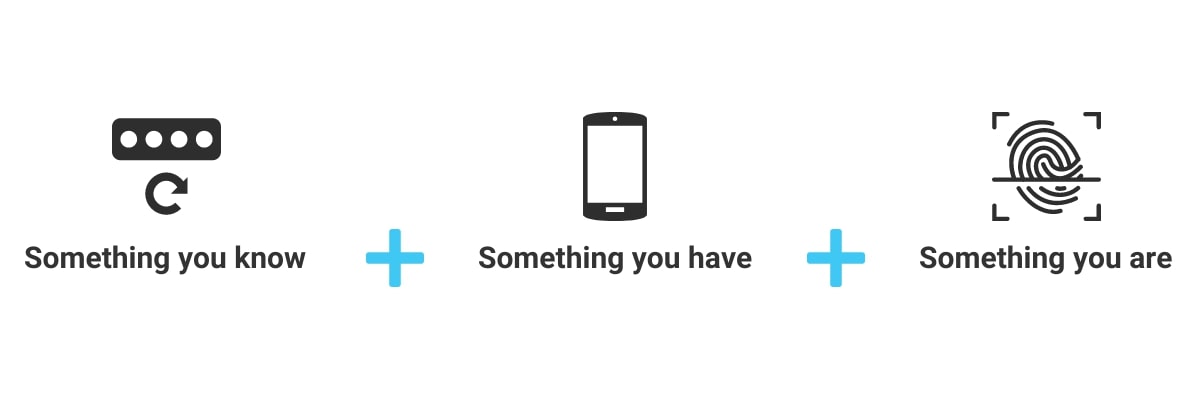
6. Not Using Multi-Factor Authentication (MFA)
It’s one of the simplest yet most effective ways to enhance your security. MFA adds an extra layer – another “factor” – to your usual login process.
This means when you or your employees log in, in addition to the standard password, an extra step is required to verify your identity.
This could be anything from a fingerprint scan to a code sent to a mobile phone.
What To Do
Start by implementing MFA on all key systems. You’ll want to target those handling sensitive data to begin with – email accounts, cloud storage, and network access points.
This extra step ensures that even if a password is compromised, the chance of an attacker gaining access is still minimal.
It’s important to select a user-friendly MFA method. This reduces friction – increasing the likelihood that your employees will use it.
Common options include receiving a code via SMS, using an authentication app, or employing a physical token.
The right choice will depend on your business needs and the type of data you are protecting.
7. Disregarding Employee Cyber Security Training
Often, the biggest cyber security mistakes come from within your organisation.
That’s right, it’s human error.

These are often innocent mistakes made by employees who are unaware of best cyber security practices.
What To Do
It’s recommended that you implement regular cyber security training for all employees. This training should cover the basics of cyber security, including:
- How to recognise phishing attempts
- Password security
- Safe internet practices
Additionally, make cyber security a training regular occurrence. There needs to be a balance here. Train your employees once per year and the message might not sink in. Train your employees too frequently and they may develop security fatigue – becoming less vigilant and more prone to oversight.
You might also consider simulated phishing exercises to test employee awareness and provide hands-on experience in identifying potential threats. Companies like usecure are great resources for these exercises, offering you insight into how your team is responding to cyber threats.
8. Ignoring Physical Security Measures
Most of the time, when we talk about cyber security mistakes we’re focusing on digital threats.
However, the physical security of IT hardware and data storage areas are equally important.
A common example is the risk of unauthorised access to physical locations (sites, offices and facilities) if these locations are unsecured.
What To Do
- Secure all access points to your IT infrastructure. This includes server rooms, data centres, and any areas where you store or process sensitive data
- Use access control measures (key cards, biometric scanners, security codes) to restrict entry to unauthorised personnel only.
- Maintain a log of who has accessed secure areas, and when. This will help investigation efforts in the case of a breach.
9. Lacking a Cyber Incident Response Plan
What happens when disaster strikes?
For many businesses, the answer is invariably “I don’t know”.
This uncertainty in the face of a cyber incident can lead to a chaotic response, prolonged recovery times, and an increase in damage to your business.
Whether it’s ransomware, a data breach, or another form of cyber threat, being unprepared is a risk no business can afford.
What To Do
No points for guessing this one. The remedy for this is to develop a specific cyber incident response plan.
- Ensure the plan addresses various types of cyber incidents and outlines clear roles and responsibilities.
- Regularly review and update your response plan to reflect new cyber threats and changes in your IT infrastructure.
- Include communication strategies in your plan. Make it clear who to notify (internal and external) and how to manage public relations after the incident.
- Collaborate with external cyber security experts if needed.
10. Granting Unneccesary User Privileges
Not every employee needs access to every system or data source in your company.
Imagine giving everyone in a hospital – from surgeons to administrative staff – access to the entire medicine cabinet.
Just as this would increase unnecessary or incorrect medication use, in your business environment, granting excessive access privileges can lead to data mishandling or breaches.
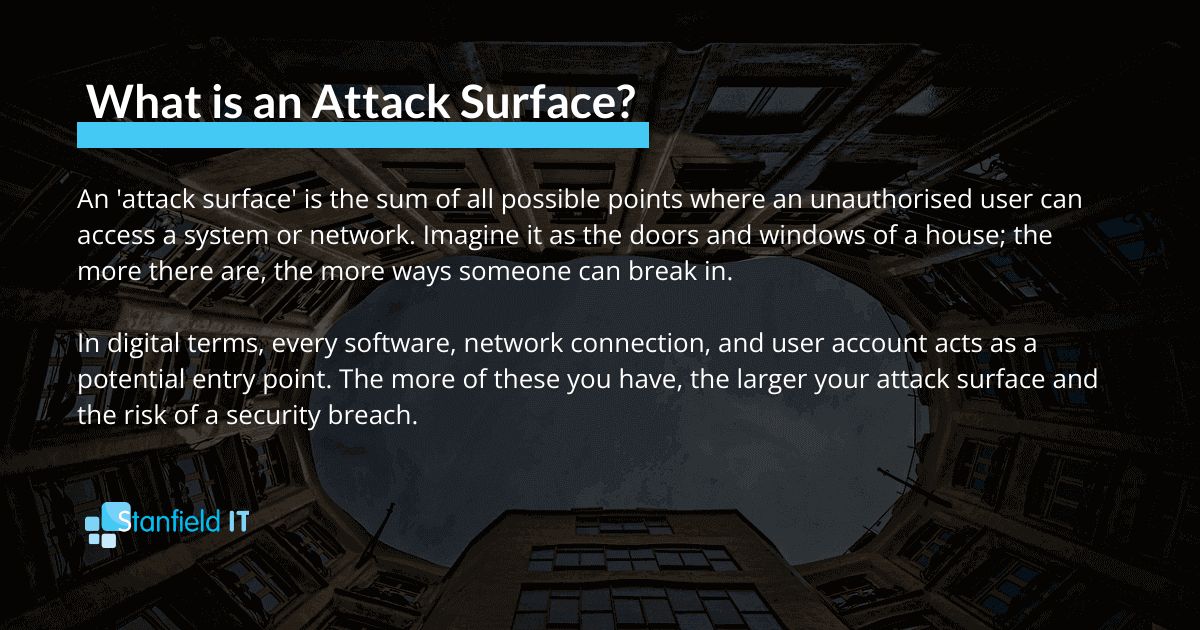
Giving everyone access is akin to leaving all doors unlocked in a building. Sure, it may seem convenient for those inside. But, it also allows potential intruders to wander freely, increasing the risk of theft or damage.
It increases your attack surface.
What To Do
Adopt the principle of least privilege (PoLP).
By doing so, you ensure that employees only have access to the information and systems essential for their specific job duties. Review and update user access rights regularly. As roles change, so too should access privileges.
Conduct periodic audits of user privileges to identify and rectify any instances of excessive access rights.
There are tools available to assist with access management. They can help monitor and control access rights, making it easier to enforce appropriate access levels. Examples include Microsoft Entra ID and Okta.
11. Not Conducting Regular Security Audits
If you’re not regularly auditing your IT systems and security measures, how do you know if you have vulnerabilities?
The truth is, without frequent, thorough checks, you don’t.
It’s like driving a car without ever taking for a service. You won’t there’s a problem until it’s too late.
Regular security audits help reveal hidden issues, ensuring your defences are up-to-date and as strong as they need to be.
What To Do
- Schedule regular audits to assess the effectiveness of your current cyber security measures.
- Use the audit findings to update and improve your security strategies.
- Consider hiring external auditors to complete this process.
- Ensure audit results are well documented and followed by actionable steps.
- Involve different departments in the audit process.
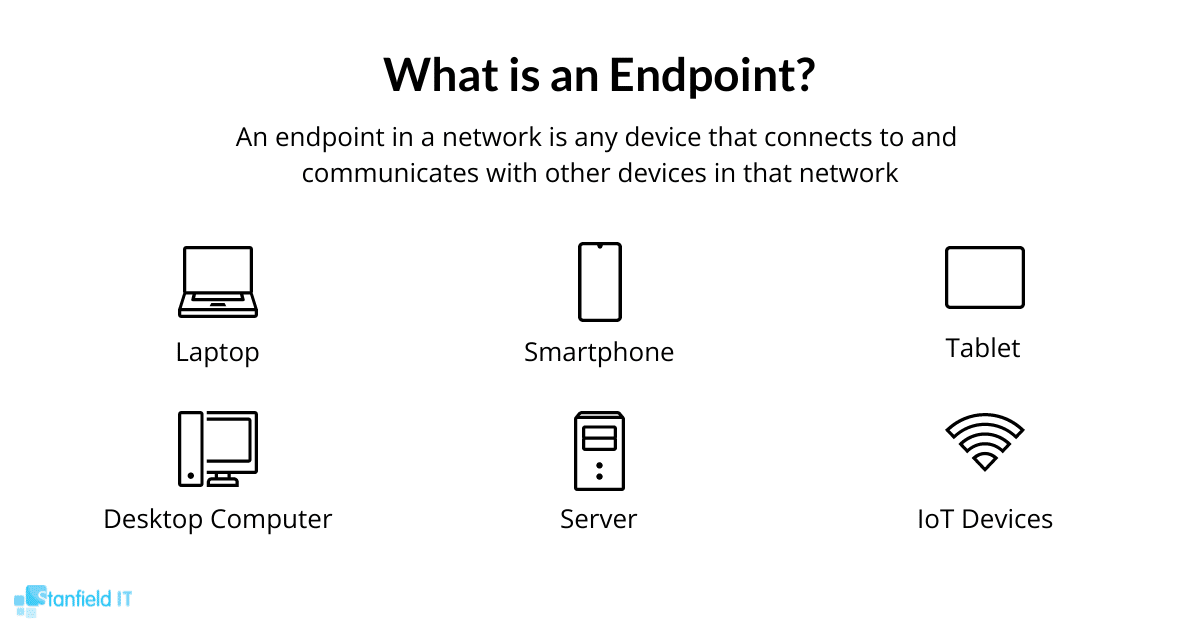
12. Endpoint Security
Every device that connects to your network, from laptops to smartphones, can be a potential entry point for threats.
Yet again, the concept of attack surface comes into play. Each additional device acts like a new door that an attacker could exploit.
We’re increasingly doing our work on the go or remotely, so it’s crucial to ensure that each of these ‘digital doors’ is well-guarded.
What To Do
- Tailor Security Measures for Each Device Type: Different devices have varying vulnerabilities. Customise security protocols for laptops, smartphones, tablets, etc. This could involve specific types of antivirus software, firewalls, or other security tools suited to each device.
- Regular Software Updates and Patch Management: Ensure all devices are regularly updated with the latest patches and software versions.
- Use Strong Authentication: Implement authentication methods for accessing devices.
- Regularly Audit Devices: Periodically audit every device connected to your network.
- Use Endpoint Detection and Response (EDR) Solutions: Implement EDR solutions for real-time monitoring and response to threats at the device level. Good EDR tools include Cisco Secure Endpoint, Crowdstrike Falcon Insight, and Microsoft Defender for Endpoint.
13. Entering Sensitive Information into AI Tools
Out of all the behaviours that could result in a data breach, this one is probably top of mind. The careless input of sensitive information into AI platforms or tools is a serious cyber security mistake.
Research from LayerX revealed that 6% of users shared sensitive information in ChatGPT.

While that may seem like a small percentage, it’s significant given the rapid proliferation of AI platforms and tools.
As these technologies become more integrated into daily business operations, the risk of inadvertently exposing sensitive data can increase dramatically.
What To Do
- Establish Clear Guidelines: Develop an AI Policy specifying what types of information employees should never enter into AI tools. This includes confidential business data, personally identifiable information, and any sensitive company secrets.
- Educate Your Employees: Raise awareness about the risks of AI platforms.
- Choose Secure AI Tools: Opt for AI platforms that are known for strong security measures.
- Monitor & Enforce Compliance: Keep an eye on how AI tools are being used in your organisation and enforce your data security policies strictly.
Conclusion
You don’t need qualifications in cyber security to protect your business.
A basic understanding of common IT and cyber security errors can significantly improve your organisation’s defences.
Stay vigilant, educate your team, and regularly update your practices to keep your business safe.
More Like This
How Risky Behaviour and MFA Myths are Undermining Cyber Security
The number of cyber incidents caused by human error varies depending on which report you read. But they all have one thing in common. It’s high. A study by IBM estimates that human error is the driving factor in 95% of cyber security breaches. But how can that be?...
Latitude Hack: How To Stop It Happening To Your Business (Updated 2024)
Another day, and another Australian business has suffered a data breach. The Latitude Financial cyber attack hack has once again put the spotlight on the importance of cyber security for businesses. The recent attack also highlights the prominence of cybercrime in...
The Top 22 Cyber Security Audit Checklist Strategies in 2024
Imagine this: your business is thriving, taking advantage of all the opportunities in our increasingly connected world. You're reaching new customers, streamlining processes, and innovating like never before. But wait, what's that lurking in the shadows? Cyber...



