Data security is consistently topical because business data is incredibly valuable. If you have something that valuable, it’s more or less inevitable that someone will try to steal it, unfortunately. Every day, businesses are hacked and valuable data is stolen. Small-to-medium businesses in particular are a very frequent target of these attacks and data theft.
However, it may surprise you to know that the biggest threat to your data security isn’t actually wily hackers and their malware.
90% of data breaches are caused by human touch.
As we all know, data is central to our business process. It empowers our decision making, improves customer experiences, and turbo-charges our productivity. In our experience, data security is not hard. In fact, much of data security is just common sense. Often, managers and executives simply overlook the importance of data security.

Firstly, What is Data Security?
Let’s keep it simple. Data security is any technique that prevents unauthorised access or loss of data. Organisations around the globe are continuing to increase their stores of digital assets and resources. As a result, data security has emerged as an essential undertaking to protect all things digital within a company.
In practice, data security includes techniques like enforcing authorisation and access control, better data storage, encrypting files and backing them up offline, implementing policies to better manage employees, and so on.
Data security is an extensive topic the encompasses many techniques. For that reason, the best implementation is an across the board improvement. This means you essentially cover all your bases, and improve the overall data security and data management of the organisation.
Here, we have taken the time to cover ten easy steps that will put you on the path towards securing your data today.
10 Data Security Measures For Your Business

1. Data Security Software
Software and data security go hand in hand. Think of data security as a tower defence game and your files are the helpless villages. In this metaphor, the hackers are the waves of enemies. With each new wave your enemies learn about new exploits and find new vulnerabilities in your defences.
The only way to keep the advancing waves of viruses and hackers at bay is by continually upgrading your fortifications. Businesses can’t constantly focus on manually patching bugs and updating systems, so we rely on tools and software as a data security measure.
Let us save you some time.
The type of software you need is called enterprise management software or device management software.
There are many offerings on the market to choose from. There’s Bitdefender: a local data security company based in Australia. Or premium international offerings such as Microsoft Intune, Cisco’s Meraki and IBM MaaS360, to just name a few. More often than not, companies package this software as a complete solution that provides all the functionality and administrative power needed to secure an entire enterprise.

2. Application Whitelisting
Application whitelisting is the practice of indexing approved applications. Your endpoint management software is responsible for this index. Then when an employee attempts to download an unapproved application, the software automatically prohibits this action. It’s possible to add custom business logic to the process too. For example, create a popup that says “This application isn’t approved. Go see an IT admin for permission to download it”.
That’s the how. Here’s the why. Malicious programs will pretend to be legitimate applications. Hackers can upload viruses to well-designed websites or position their malware as apps on the Playstore.
In 2018, Forbes reported that half-a-million Android users downloaded a virus from Google Play disguised as a racing game.
Lifewire
Once they are downloaded and executed, theses programs can change system configurations, delete important files, send data to hackers, and encrypt your data so you can’t read it.
Since disguising malicious programs is such a common attack vector, application whitelisting is considered an essential component in modern cyber security. So essential, that the Australian Government included it in their 8 recommended cyber security practices.

3. Restrict Admin Privileges
By restricting admin privileges, you can control who has the power to make potentially system-breaking changes to your network. Seems like a power that should be restricted, right?
IT systems are complicated and take years of dedicated study to properly understand. It seems careless to simply hand over such complete access to employees who may not even understand the fundamentals of data security. When applications run with administrative privileges, they can make significant changes to their configuration and operation, bypass critical security settings and access sensitive information.
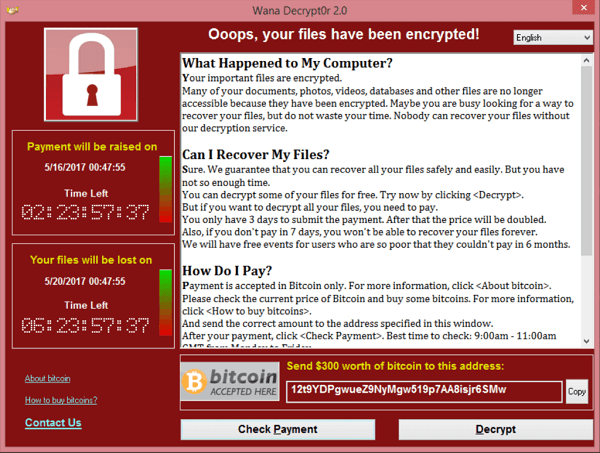
A recent example of unrestricted privileges causing worldwide catastrophe was the wannaCry hacks in 2017. Maybe Australia has better data security than Europe and the US. We were affected, but it wasn’t as bad.
In the UK, their NHS was left floundering after an easily preventable exploit shut down their entire network. If they had only restricted users and prevented them from enabling macros, the whole ordeal could have been avoided.
If you’re a smaller business, or if the restrictions only apply to a few employees, you can opt to restrict admin privileges locally. On a larger scale, it is best to restrict privileges with a directory service like active directory and put control in the capable hands of a domain administrator.

4. Mobile Device Management
Who doesn’t take their laptop or phone to work? The pros of BYOD far outweigh the cons. However, when approaching BYOD from a cyber security standpoint, we are almost always talking about the cons. That’s because external devices coming into the workplace and connecting to internal servers and the clouds are a data security risk.
As a result of the uptake in BYOD, mobile device management software has become a must for general cyber security and data security. There is a whole host of tools designed to rein these devices back under admin control. MDM and its spin-offs: mobile application management, and enterprise mobility mangement. Endpoint management, application management, access management and a whole array of other functionality. In short, mobile device management software applies business logic to the myriad of devices we now use at work.

5. Backups
Even a high school student knows that if you don’t want to lose data you need to back it up. However, there are degrees of backing up, and some types of backups are more resilient than others. The safest way to store data is encrypted and offline. Although you’ll need to weigh up the trade-off of security vs practicality.
For example, burying a hard drive in the parking lot is incredibly secure. However, it’s very difficult to update. Parking lot data also isn’t available when you need it. An image-based backup is a better enterprise backup solution. An image-based backup copies your entire hard drive and stores it in a single file called an image.
If you take your hard drive out of your computer and plug it into another computer, it will boot up with your operating system, your files and everything else. It’s indistinguishable from your file-system.
That’s the idea behind an image-based backup. Now imagine, instead of copying one computer we copied all the computers in your system and every single file that made your system your system. If your data is corrupted, or you’re attacked by ransomware you can reset everything to exactly how it was before the attack.

6. Multi-Factor Authentication
MFA is a simple, yet incredibly effective defence against hackers. Usually, when we think of multi-factor authentication, we think of two-factor authentication since it’s basically industry standard at this point. However, there are actually three factors of authentification.
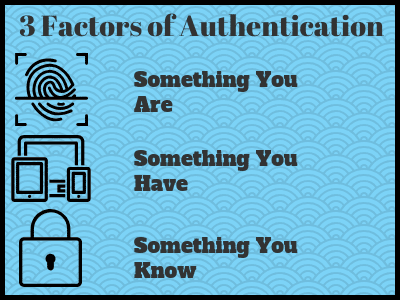
Normally, when we log in to an account we use something we know to authenticate ourselves. A username/password combination. However, keyloggers, data leaks and brute force attacks can reveal our passwords. An emerging common practice is asking users to further authenticate by logging into an email account and clicking a link or entering a code on your phone. You own the phone or the email account. The final factor of authentification includes thumb and face scanners.
Multi-factor authentification protects data security by making a hacker’s job much harder. Guessing that an employee set their password to “password” is one thing. But stealing a phone or compromising an email account is another.
MFA can also leverage contextual information such as the device that’s logging in, where it’s logging in from, when you last logged in, and then request additional information based on this.
There are endless MFA solutions on the market. LastPass, and Duo are some immediate examples. If you are using GSuite apps, Microsoft365, or really any modern enterprise software then go into your settings and enable 2-FA. Registering for services by linking a Google account is another quick and easy way to protect new accounts with 2-FA.

7. Training Your Staff
As we mentioned earlier, 90% of data security breaches involve a human touch. This is true across all workplaces and all industries. We can expect that all industries suffer from staff who are poorly trained in IT. However, recently the spotlight came to rest on healthcare. We instinctively trust healthcare to safeguard our sensitive and personal data. Unfortunately, healthcare practices are the most highly targeted out of any industry and it’s become clear that many workers in the industry don’t know what data security is.
Incorrectly addressed emails cause more data leaks than hackers and malware. Cases of unauthorised access, opening an infected email attachment, and bringing malware to work on USBs are far more common than sneaky hackers tippy-typing their way into your personal data.
If you can’t train them, restrict them. But, we do recommend training them.
There are many flavours of access management and data loss prevention software that we can use to restrict employees. Intune and Microsoft Teams, for example, can be configured to omit personal data – credit cards, passwords, phone numbers, or anything else an organisation deems appropriate, from messages and emails.
If employees want to send this data, they need to encrypt it, but if you don’t train your employees why this is important, well there is nothing stopping them circumnavigating these systems by taking a photo and texting it on their phone.

8. Implement Antivirus Software
When you try to open an application or install a program, your anti-virus software will scan the application before they actually launch. However, it’s effectiveness is directly tied to how up-to-date it is. Therefore, it’s important that you keep your antivirus software up to date. Each update provides the software tool with the latest virus and malware. The tool compares your application against this list. No updates, no list, it doesn’t stop the virus from executing.
Naturally then, if your anti-virus is a few months or years behind on updates, then it doesn’t know about the most recent viruses and is unable to detect them. Another related suggestion to look into is AI-driven antivirus software.
It isn’t as sci-fi as it first sounds. Companies like Cylance, Microsoft and IBM are pioneering a new breed of antivirus software that can predict variations of current malware before they occur!
AI-driven antivirus is also proving invaluable in combating fileless malware. Traditional antivirus struggles to recognise fileless malware because antivirus looks for specific “file” signatures when it scans a computer.

9. Next-Generation Firewall
Next-generation firewalls perform deep packet inspection to remove suspicious traffic without disputing regular business traffic.
A traditional firewall can block and restrict traffic. However, in order to do that it needs to shut off a port, or be pre-configured to stop messages from a specific site or program.
Next-generation firewalls, on the other hand, have application-level awareness. Since malware is essentially a malicious application, this means a NGFW can fight threats in real-time and without IT staff intervention.
Fortigate provides a NGFW that uses AI to monitor incoming traffic and can even identify threats in encrypted traffic. The Cisco Firepower was the first and is still a proficient Next-Generation Firewall.

10. Business Continuity Plan
Pre-planning for catastrophe just might be what saves your business from ruin. When it all goes wrong, it’s critical that you are able to act swiftly. Your plan of action should address steps taken to recover data, potentially notifying customers of a breach, and lock down what you can to stop the spread of damage.
A business continuity plan isn’t just about recouping money and protecting the bottom line. Though it certainly doesn’t hurt. Customers will pay attention to how you respond. Ideally, you don’t want to give them anything to criticise. The longer an attacker has access, files are missing, or you are waiting for systems to come back online the bigger the problem is. That’s why a business continuity plan can literally save your business.
Final Thoughts on Data Security
The best data security measure you can take is to keep learning, improving and to remain vigilant. If you aren’t in IT, the big words can be off-putting but behind the scary terminology are some very straightforward concepts. Keep your protection software up to date, make life difficult for hackers, back up your data and make a plan in case it all goes horribly wrong.
Your commitment to reading articles like this one and learning more about data security will definitely pay off. It’s like we keep saying, 90% of data security breaches involve a human touch. Don’t be one of those humans. We are contending with widespread computer illiteracy. Be a part of the solution, not the problem. Of course, you can always contact Stanfield IT. We will gladly point you in the right direction towards better data security.
