Cyber security for small businesses has different priorities and levels of risk compared to others. As a small business, you’re less likely to be adequately protected, and, for this reason, more likely to be targeted. Depending on what industry you’re in can also affect your small business network security.
Businesses in the health industry have been the hardest hit by data breaches this year, with a total 203 reported breaches in the first two quarters. Nearly half of these breaches were caused by a malicious attack, possibly due to insufficient cyber security precautions. These numbers show that anyone can be a victim of an attack, and there is no reason to think it won’t happen to you.
What is a data breach?

A data breach is an incident involving unauthorised access of data, usually by an individual. Data breaches can be accidental and unintended, or intentionally malicious. Accidental data breaches usually come down to human error, such as sending a sensitive email to the wrong recipient. Through vigilance and employee education, you can prevent ― or at least minimise ― these incidents. A malicious data breach looks like a hacker gaining access to sensitive data for financial or personal gain. To prevent these type of incidents, cyber security measures must be implemented.
Understanding terminology and context of cyber security terms plays a critical role in protecting your business. In order to identify risks, vulnerabilities and attacks, you have to know what they look like.
What are different types of cyber attacks?
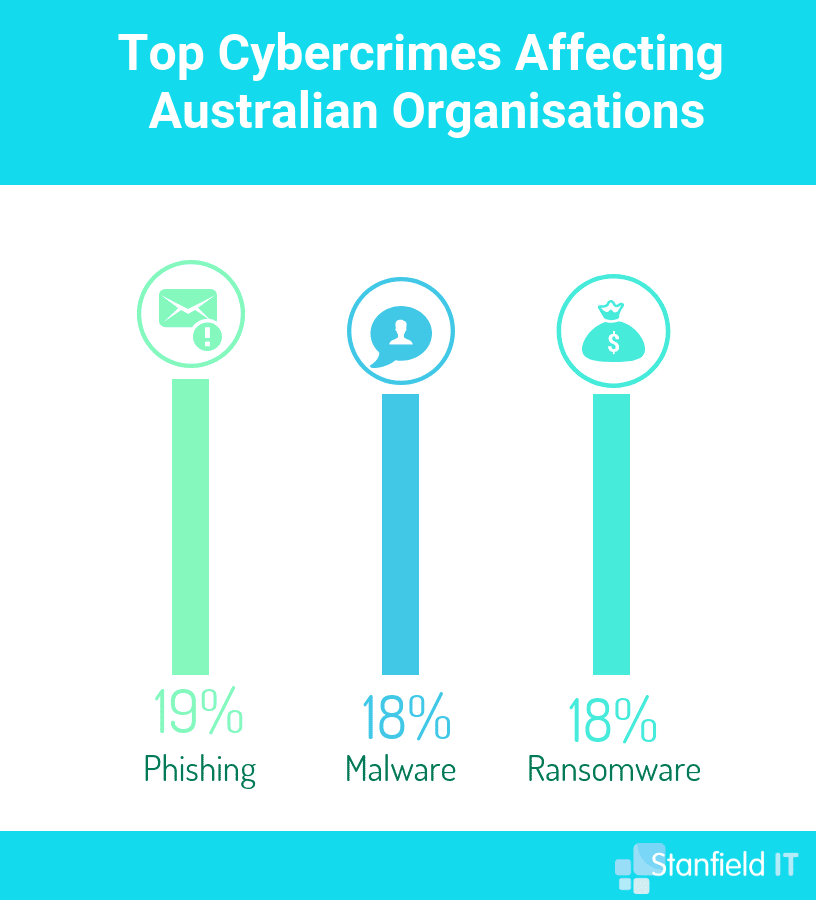
There are a variety of cyber attacks that can strike you, and being aware of them is an important factor in being able to prevent them. Some are more likely to hit small businesses, due to lower risk, and higher chance of financial gain. Ransomware is a prime example of this type of attack. Ransomware is a type of malware attack that holds your data hostage in exchange for a ransom, usually paid in cryptocurrency in order to be untraceable. As a small business, you will pay the ransom fee more often than not, being likely unprepared for this type of attack.
Other common types of attacks include phishing attempts, malware attacks, DDoS attacks, and watering hole attacks. Attackers will often disguise these malicious links within emails or trusted websites. One of the primary ways you can prevent these cyber attacks is to know what you’re looking for, and ensure that your employees are educated on the topic and take responsibility for cyber security as well.
Many types of attack aim to take advantage of structural weaknesses in your operating system, or software. This is usually doable when businesses don’t have their systems running on the latest updates and patches. This is an easy step to take that helps manage cyber security for small businesses.
How will I be affected by a cyber attack?
This is an excellent question. Cyber security for small businesses may seem unnecessary and excessive, because surely it’s not that big a deal, right? Nope. It’s kind of a big deal! Cyber attacks can leave your reputation in tatters and lose you clients (and therefore income). Investigating, containing and managing any attack or breach incurs a tangible financial cost to your business. As your processes are put on the back burner to handle the attack, your productivity takes a hit. We cannot overstate the very real cost of cyber attacks.
Studies show that the average cost to an Australian company in the event of a data breach is a whopping $2.51 million. Yes, let that sink in. Can your business afford to waste $2.51m on a data breach that you could have easily prevented?
Whether it’s private customer information, financial data, or sensitive intellectual property ― you’re faced with the fact that data has been compromised. You have to notify your customer base, and let’s face it, they may not be happy. So you’ll be dealing with a PR backlash, a loss of trust, and possibly a loss of business if they decide to go elsewhere. You have to spend time and money, either yourself or through an IT company, to identify and contain the breach. Then you need to protect your system moving forward by upgrading, or implementing higher security measures to prevent another similar incident.
A malicious ransomware attack could even leave your data totally compromised or destroyed. Without proper backup or business continuity plans in place, you’ve potentially lost days, weeks, months, or years worth of work.
What cyber security compliance regulations are there?
In terms of cyber security for small businesses, there are a few regulations (or cyber security frameworks) you can follow. These are templates, or guidelines, that outline protocols and policies you should implement to boost your cyber security. Depending on the nature of your business, you may find a set of cyber security guidelines designed just for you. If you’re a healthcare practice, the RACGP has a framework geared towards protecting patient information, information availability and risk assessment. CPA Australia has a set of articles and checklist that focus on the best way to protect your information.
ISO 27001 is the cyber security framework laid out by the International Organisation of Standards. This framework focuses on information security management, maintenance and risk management. ISO also advocates for an important factor of cyber security, where it should be the responsibility of everyone, and an integral part of every department. The Australian government has published several documents that also fall under this scope, from the Information Security Manual by the Australian Signals Directorate (ASD) or the Protective Security Policy Framework (PSPF). Government agencies and departments tasked with protecting highly sensitive information use these frameworks, so you have access to a great foundation of cyber security for small businesses.
How can I reduce the risk of a data breach?
There are a number of strategies you can, and should, use to mitigate the risk of data breach, whether intentional or not. Some of these come down to common sense, and some fall under a more technical umbrella.
There are a number of essential steps that especially help cyber security for small businesses. For further information on how you can mitigate the risk of a data breach, have a read of our top cyber security tips and consider performing a cyber security audit, by following a checklist or by utilising a third-party team that specialises in IT and security and have them evaluate, test and upgrade your cyber security tactics.
If you practice good password management, sensible browsing activity and keep your systems up to date, then you’re already taking good strides towards reducing risk. You will need to utilise a variety of strategies and policies within your business, however, in order to fully protect your data from being accessed.
Conducting an audit
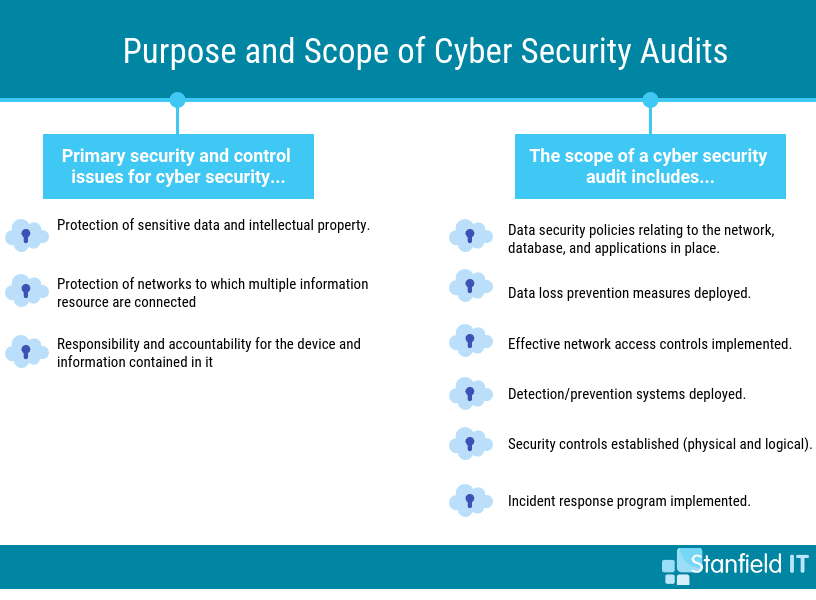
A cyber security audit provides the management and the IT team of a business a comprehensive assessment of cyber security policies and procedures. An audit also ― even more importantly ― analyses and addresses the effectiveness of these policies and procedures. It’s crucial that your measures provide the most small business network security possible.
You should also evaluate the potential risks that may compromise information security. These risks may have gone unnoticed or deemed inconsequential prior to the audit. The standards, guidelines, and procedures of cyber security for small businesses are a core focus of risk management.
Remember that cyber security audits should be conducted regularly, not sporadically. Your last audit may also not be done in the same way as the previous audit. This is because, in the days of the Cloud, information is beginning to shift location. This includes your company data, files, and resources moving from mobile to loT, to cloud. With these moves comes the necessity for new classes of controls that are suitable for these new information locations. These new classes of controls should not fall to the wayside when it comes to regular updates and auditing.
NIST guidelines
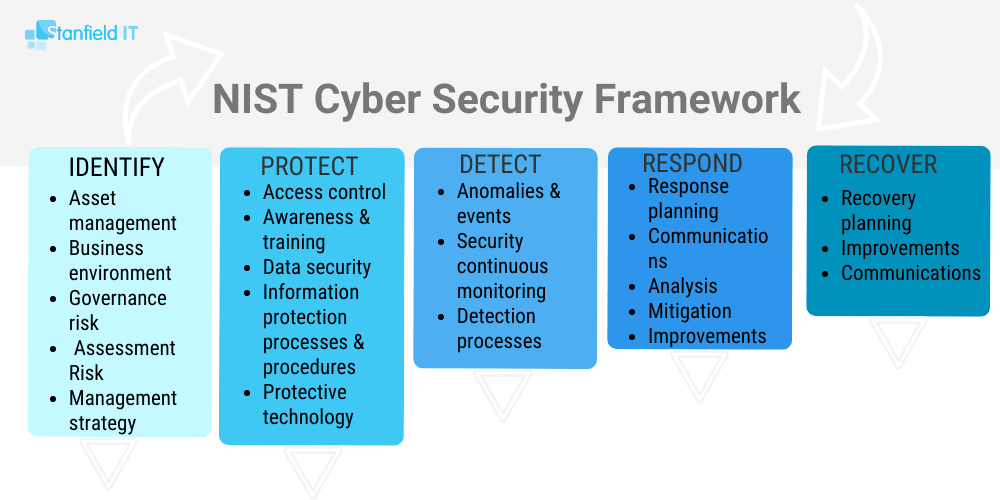
When conducting a cyber security audit, it’s beneficial for a small business to refer to a set of standards like the National Institute of Standards and Technology (NIST) guidelines. While the NIST guidelines (Special Publication 800-53 Revision 4) are geared towards ‘Security and Privacy Controls for Federal Information Systems and Organizations,’ they have useful cyber security insights that can be more broadly applied to small businesses and give you a basis for your audit strategy. It contains detailed definitions (don’t get overwhelmed; just use these as a resource!) and is prescriptive in nature. Many small-to-medium businesses have successfully implemented the NIST guidelines when developing their own personalised cyber security processes.
Assigning cyber security responsibility
While we always stress that every employee of a company is responsible for consistently implementing cyber security measures in their day-to-day online tasks, it’s crucial for a business to have someone responsible for cyber security. This can either be an internal team or employee or an external party ― an outsourced IT company, for example. Whom an organisation chooses to take control of their cyber security depends on the type of company it is, the company culture, and the size of the company.
On-site cyber security
Many small businesses will have their IT team/employee responsible for conducting cyber security audits, implementing data protection best practice, and responding to and controlling threats. Cyber security definitely shouldn’t just be down to one department. However, there does need to be a consistent point of call when it comes to cyber security procedure. There should also be a team of people in place in case a breach does happen. One person alone will not be able to handle this themselves and expecting them to could risk the breach not being contained in a timely manner. Such a team is called a ‘Data Breach Response Team,’ and you can see an example of some of the roles below. These roles may overlap in businesses with a smaller staff base.

Off-site cyber security
You don’t need to have your cyber security strategies conducted in house, though! Many people think that hiring an external party to handle cyber security is just for bigger businesses with bigger budgets. However, many small businesses are now outsourcing IT services from professionals in the field. This is because it saves the business a lot of time that can be spent building up their small business. It also means that business owners have the peace of mind that everything is taken care of, and that, if a breach does occur, the business is far less likely to see financial impacts and even shutdown. A local, expert IT team, like that at Stanfield IT, will have the knowledge and experience to enhance small business network security. Every small business is different and there isn’t a one-size-fits-all solution.
“With affordable and scalable outsourcing options available through today’s managed service providers, security certainly doesn’t have to break the bank to be effective and even smaller businesses can ensure they’re doing these types of basics. Couple that with the idea that security should be viewed as a ubiquitous function of the organisation, and you’ve got a great foundation.”
Tim Brown, VP of Security at SolarWinds MSP
Focus on protecting sensitive data
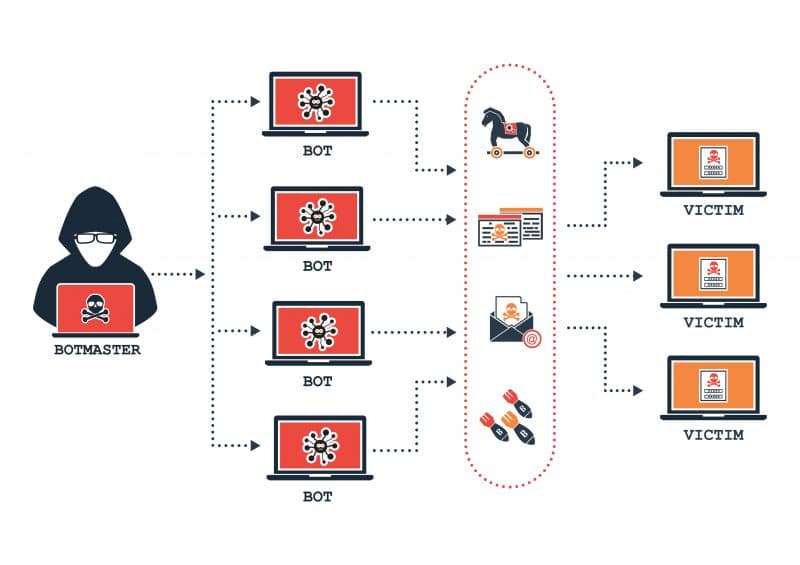
As mentioned, cyber security is not just up to the IT team or offsite team responsible for managing cyber security for small businesses. This means that employees need to be across the signs of malware, ransomware, phishing, Botnet/DDos attacks, and other malicious attacks. As well as due to a lack of vigilance (such as clicking a suspicious pop-up), data breaches can occur from software and hardware not being kept updated and properly protected. This could cause an application to provide a hacker access to the data it’s designed to protect. Now you can see why audits are so important!
Devices that access data need to be secure. In the age of BYOD, having a proper mobile management system in place is of utmost importance. This means that company data that is accessed on employee’s personal devices can be removed via remotely wiping company apps in the case of a lost or compromised device. Accessing company data and apps via an insecure network can also be a doorway for hackers. Through mobile management, the networks that can be used to access these apps and data can be controlled.
Educate your team and users
Human error still remains a top reason for data breaches, even in small businesses. No matter how much you invest in your businesses data security, if you don’t train and educate your employees on their role in minimising risk you will be an easier target for hackers than a company that hasn’t invested as much in software, but have thoroughly trained their employees.
In Australia, one in three data breaches are the result of human error. These figures are taken from the Notifiable Data Breaches Scheme 12-month Insights Report. There seems to be a way of thinking that an attack won’t happen within a small company, and people only care about security once they themselves have been attacked. You need to work to mitigate this attitude within your company through comprehensive employee education. This should cover how to recognise and report a breach and, importantly, how to avoid becoming a victim altogether.
In the fast-paced work environments of today, people often click emails and links without a second thought. Employees need to be educated on the potential phishing, ransomware, and malware threats that can come with one simple click and to always be vigilant if something doesn’t look right, if an email seems to good to be true, and to never give out company information unless you can verify the identity of the recipient. The cyber security services at Stanfield It extend to one-off or ongoing training of your employees within your small business around cyber security.

Implement the Essential 8 Checklist
There are a number of essential steps that especially help cyber security for small businesses. The Australian Signals Directorate (ASD) has published this list ‘the essential eight’. These are cyber security protocols that any and every small business should implement as a foundation for cyber security protection.
The Essential 8 is always one of our first ports of call when it comes to recommending cyber security strategies to small businesses. The Essential 8 make up strategies you can use in businesses of all sizes to mitigate cyber security incidents. It’s a prioritised list, but you can use the points that apply the most to your business and what adversaries you need to increase your protection against. The Essential 8 is designed to be used as a baseline. It is useful even for new small businesses that want to forge a strong cyber security system from the outset.

How do I know what to focus on?
You can take a cyber security questionnaire in order to determine where your weaknesses may lie. We’ve created one for such an occasion, but these are easy enough to find. The questionnaire will help you to identify vulnerabilities and what you need to focus on. You can (and probably should) hire some experts to assist you with this process. However, doing the questionnaire beforehand will allow you to provide an outline of what you need and give you essential knowledge, too.
Understanding the whole context of your business process takes a critical role here. It may seem obvious, but actually identify where sensitive information enters the system, for example. What programs, or applications are processing the sensitive information? This should include all mobile devices, laptops, external hard drives and PCs that interact with said data. Is your network hardware secure too? Data storage, servers, and routers should be secure. If not, how can you improve this? Do you have any cyber security policies already in place; fundamentals like firewalls, encryption, and VPNs which all interact to protect your system.
Once you learn more about cyber security for small businesses, you start to get a feel for where to start. You will need to evaluate your system at regular intervals, to identify any changes or vulnerabilities that may have developed. You should roll out system patches and software updates promptly every time, as they often repair coding vulnerabilities.

Summary
Being a small business doesn’t mean you can disregard cyber security, in fact, it’s the opposite. Your livelihood depends on protecting your reputation and your data. Therefore, it’s essential to have solid cyber security measures in place. However, this doesn’t mean you need to blow out your budget by building state-of-the-art network solutions for your business (though it might be nice!).
You can utilise many off-the-shelf solutions to protect your business. These include G Suite for storing all your data, or the Cisco security suite. Hire an external IT company for managed services covering cyber security, networks and includes monitoring. Get started right in your own office though, by keeping your staff trained and aware, and keeping your systems updated.
Cyber security is a big deal, but it doesn’t need to be a big deal, if you follow some IT common sense!
Contact Stanfield IT today for your small business network security assessment.
