Healthcare data breaches in Australia are growing at a concerning rate. It’s the sector with the most reported data breaches between April 2018 and March 2019. Unfortunately, this trend is continuing. Of all reported data breaches in Australia across all sectors, healthcare has reported the most ― with 203 breaches in total. If you work in the healthcare sector, it’s important to keep abreast of trends in cyber security and data breaches in Australia. This is, however, also applicable no matter what industry you’re in. Here, we are looking into healthcare data breach trends from the first two quarters of 2019.
How many healthcare data breaches in Australia were there?
In the last quarter, (April to June 2019) there were 47 notifiable data breaches reported in Australia within the healthcare sector (of the 151 total breaches in the top five reporting sectors). For the previous quarter, (January to March 2019) there were 58 reported data breaches (of 138 total breaches in the top five reporting sectors). Again, the healthcare sector topped the list! This information has been obtained from the OAIC.
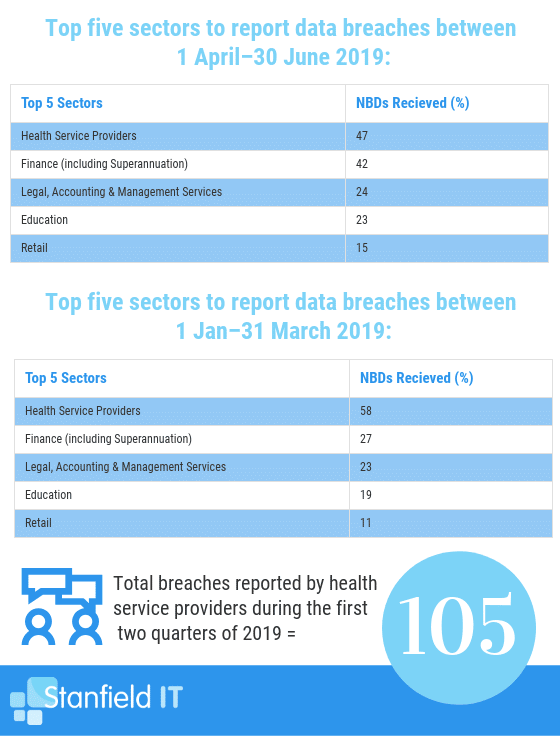
What was the source of data breaches in Australia within healthcare?
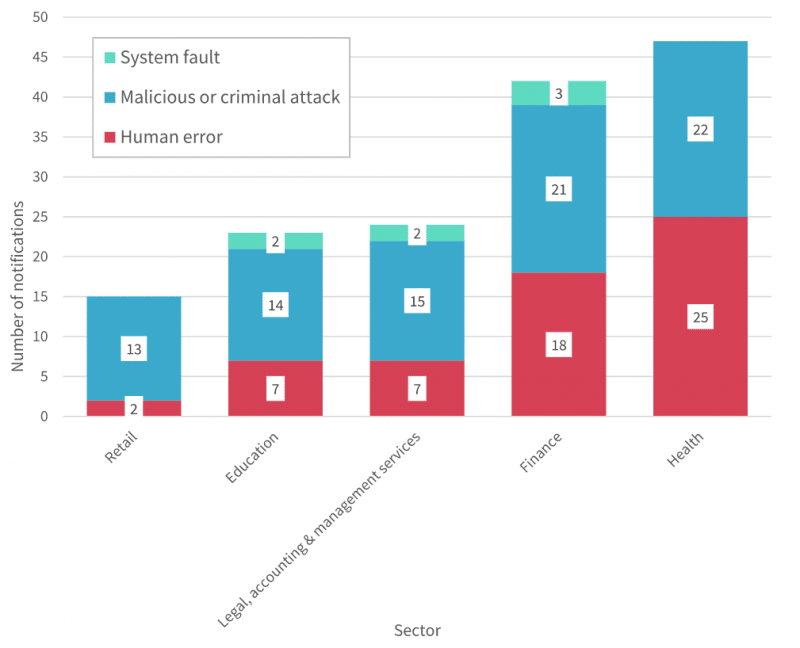
In the last quarter, 22 out of 47 breaches (47%) reported were caused by a malicious or criminal attack. The remaining 25 were caused by human error. Similarly, in the first quarter, there were 26 breaches that resulted from malicious or criminal attacks (45%). The remaining 30 were caused by human error and two resulting in system faults. With a nearly half-half split between criminal attacks and human error, the number of avoidable malicious attacks is striking. Proper staff education and implementation of cyber security measures could greatly reduce these numbers. For healthcare data security, it’s all about awareness, education, and action.
Sources of data breaches in the top five sectors between 1 April–30 June 2019
Sources of data breaches in the top five sectors between 1 January–31 March 2019
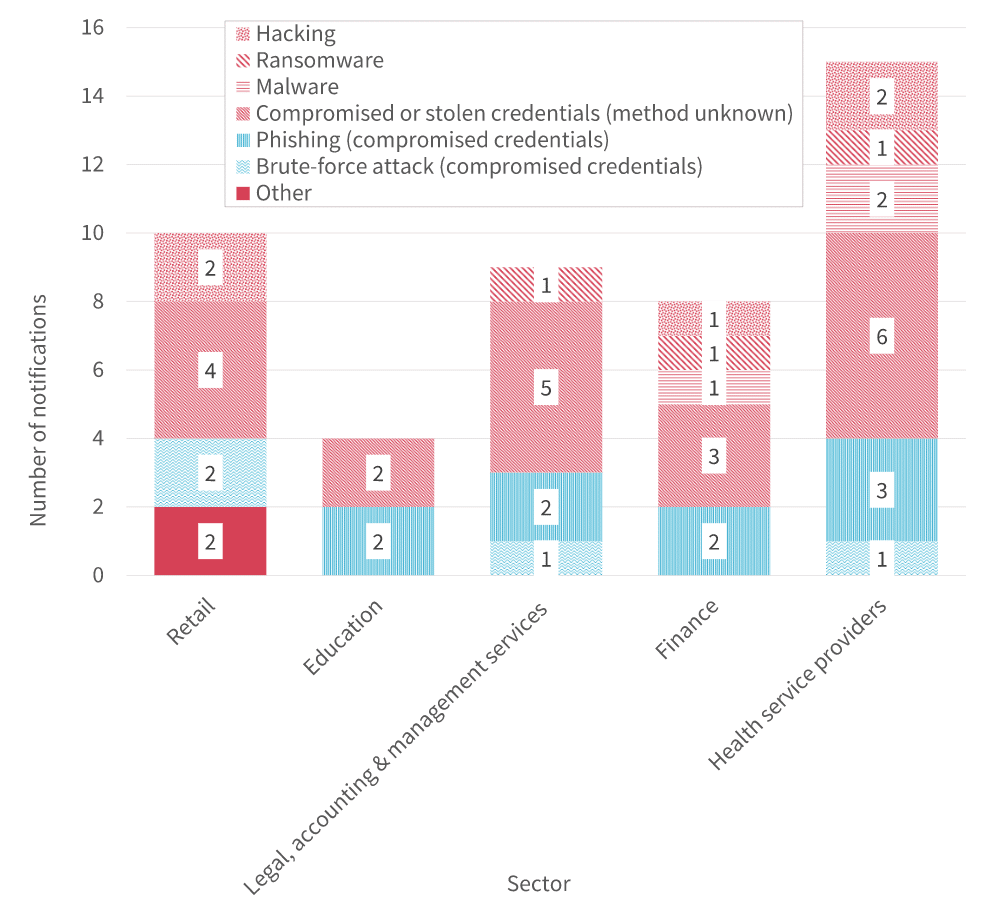
What types of malicious attacks occurred?
Malicious attacks can be broken down into one of four categories, as described below. Combining the last two quarters, 13 breaches were caused by theft of paperwork or data storage device, nine were caused by a rogue employee or insider threat, two were caused by social engineering or impersonation, and ― topping the list ― 24 were caused by a cyber incident.
A cyber incident refers to hacking, phishing, ransomware, compromised or stolen credentials, or a brute-force attack. Each of these methods was used at least once ― in case you were thinking that ransomware seemed far-fetched. If you’re interested in breaking this down even further, refer to the chart below. It breaks down what types of cybersecurity breaches have affected the healthcare sector in the last two quarters of 2019.
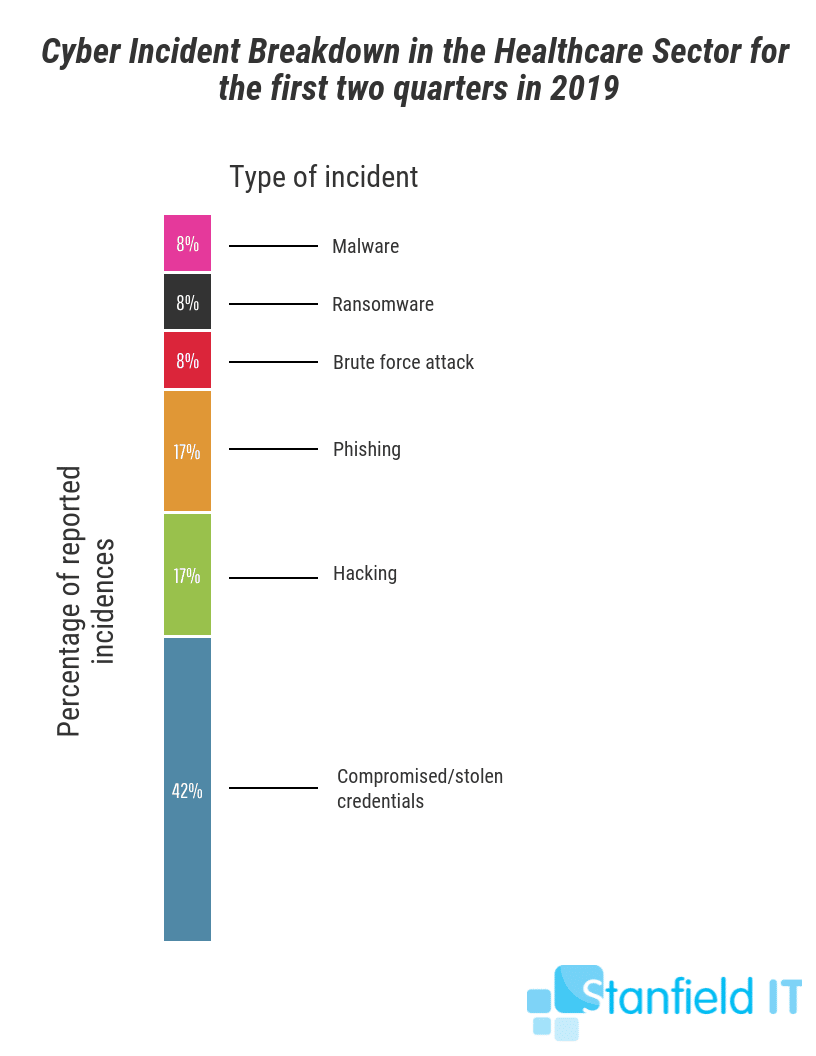
Human error breaches mostly boiled down to communication mix ups via mail, email, or unauthorised verbal disclosure. It may seem tedious to constantly verify identities when dealing with medical information, but the frequency of these breaches justifies the need.
What do these figures show?
These statistics highlight the calling for regular employee training surrounding issues in cyber security. This education means employees will be able to avoid becoming a target or easy victim for hackers. Technological solutions also need to be delivered within workplaces. These will help employees implement what they’ve learnt as they’ll have up-to-date software and cyber-security tools at their fingertips. Training also needs to centre around workplace processes that can lesson human error in the healthcare sector. The data shows that personal information being sent to the wrong recipient was the most common human error breach. This was via email, mail, or other forms of communication.
To address the threat of cyber security and pattern of human-error data breaches within the healthcare sector, the Office of the Australian Information Commissioner (OAIC) has worked with health sector stakeholders. They’ve offered professional advice and guidance on data breach prevention strategies. The OAIC will now report every six months on notifications received under the NDB scheme. This was in direct response to the rise of data breaches in the healthcare industry we are seeing in Australia today.
Healthcare data breach case studies
My Health Record System
In January 2019 there was public news about the rise in data breaches in the My Health Record System. 42 incidents in total were reported over the previous year. None of these, however, were purposeful or malicious attacks that constituted concern in the realm of cyber security. Instead, the majority of the incidents were the result of Medicare fraud.
However, due to the enormous scale of the My Health Record System that in turn makes it prone to cyber attacks, new legislation has been introduced surrounding the opt in and out period. In November 2018, the Federal Parliament passed legislation that strengthens the privacy protections of the My Health Records Act 2012. This was passed without debate or division.
This new legislation was a great step towards the Australian public being able to take more control of their privacy ― individuals now have the option of opting in or out at any time. This means that, if you have a My Health Record, you can permanently delete it whenever you’d like. While there may not have been any malicious cyber security breaches that spurred this decision, it is still partly in result of the true threat cyber security risks pose to the healthcare industry.

HealthEngine
Our second case study looks back to June, 2018, when HealthEngine revealed a data breach in their system. This breach may have caused patient feedback information to be accessed. This was never confirmed, though. In total, 59,600 pieces of patient feedback was potentially viewed. Of these, 75 contained potential identifying information about the site user. In order to deal with this potential large-scale data breach, HealthEngine notified the individual’s who were potentially affected. They also notified the Office of the Australian Information Commissioner.
This data breach was not the result of a malicious attack, instead, it was the result of an error in the website. This error exposed the webpage’s code to the public. Although it was not caused by a cyber-security breach, it reveals the huge scope of the how many people can potentially be affected. This is especially true when it’s a whole online database of healthcare information.
CEO Dr Marcus Tan said in a statement:
“HealthEngine has worked around the clock to investigate how the information was improperly obtained, what patients might have been affected, and the steps required to further address the matter. We have removed all published patient feedback from our site while we review the HealthEngine Practice Recognition System, to ensure that hidden feedback information can no longer be accessed in this way.”

How can you protect your business or workplace?
Start by looking into the top guidelines that have been built for IT security. This is a great way to expand your knowledge on actually implementing the changes into the workplace that you need to make. There are two, in particular, that are focussed on the healthcare sector:
The Royal Australian College of General Practitioners (RACGP)
The RACGP represents over 40,000 general practitioners. It is strategically focussed, with its activities centreing around GP education and training ― this includes practice policy. The RACGP has a set of standards and guidelines they’ve published as their own endorsed IT security framework. This set of standards focuses on risk assessment, managing availability of information with backup processes, business continuity, recovery planning, and access management.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA is not Australian legislation, but that of the United States. However, it can be used as a guide for Australian practices and other healthcare organisations when implementing data privacy and security provisions. With a greater number of healthcare data breaches trending in the USA, too, the Act has come into greater prominence. In the USA, there have been many notable attacks, including ransomware, in health insurers and providers.

If you’re a health service provider, and feeling the heat from the likelihood of these attacks, it’s important to follow the cyber security tips we’ve outlined here. Being a healthcare provider means you’re responsible for extremely critical and confidential information. It’s time to take essential steps to protect your data, your business, employees, and clients.
Immediate steps you can take to prevent healthcare data breaches:
- Perform cyber security audits, and update cyber security protocol
- Implement cyber security guidelines and framework as advised by RACGP
- Be proactive about employee education and awareness
- Back up your data regularly, and have an incident response plan in place so you’re able to recover lost data without fuss
- Follow the ‘essential eight’ tips endorsed by the Australian Cyber Security Centre (ADSC)
If you’re unsure where to begin with regards to securing your data, and protecting your networks, these steps are a great place to begin. If these steps still have you feeling lost, Stanfield IT is well-versed in providing advice and implementing cyber security plans for healthcare providers, so just call or email our team for a chat. Check out our cyber security guide for small to medium businesses here.