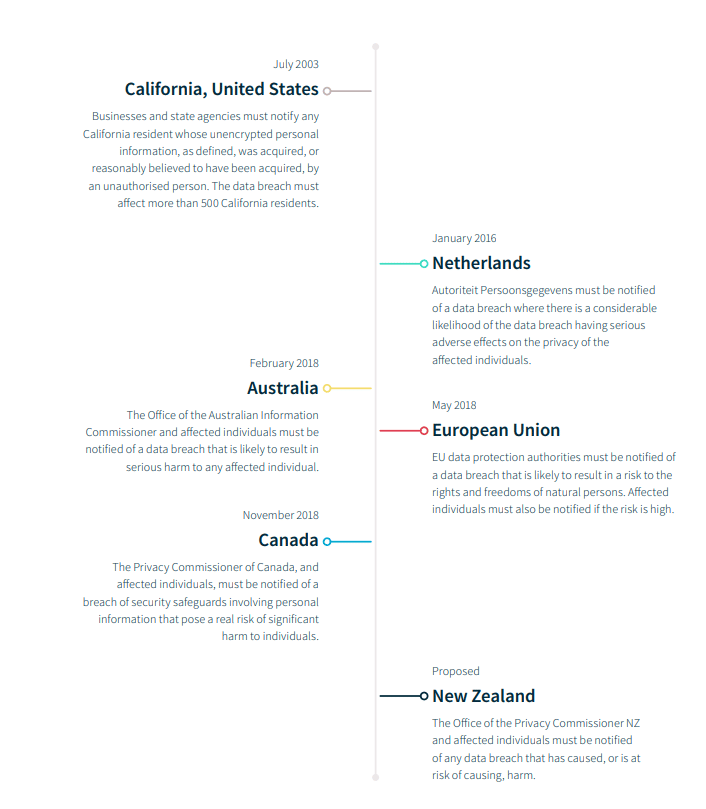
How is your business handling the new Notifiable Data Breaches Scheme? Since being introduced in 2018, it’s been a hot topic for business owners and managers alike. Considering that unreported data breaches now carries a $360,000 fine for individuals and a $1.8 million dollar fine for a company, it makes a lot of sense that it’s getting so much attention. Instead of coming at this from an over-arching legal point of view, we want to help business owners understand what this scheme means for them.
Likely in response to these impressive dollar figures, we’ve noticed the conversation around the Notifiable Data Breaches Scheme is too focused on treating the symptoms. and businesses are not paying enough attention to the cause of data leaks.
To avoid the fines, you must notify those affected by the data breach within 30 days. Sounds easy on paper, but why go through all the effort? What you really want to do is to address your underlying cyber security problems. If you don’t, then you will always be playing clean up and reporting to the Notifiable Data Breaches Scheme. It’s a risky game that will inevitably damage your reputation.
Let’s direct some attention to where it should have been all along. How can your business prevent getting caught out by the Notifiable Data Breaches Scheme in the first place? In this post, we will introduce 11 solid strategies for preventative cyber security, tailored to the Notifiable Data Breaches Scheme.
The Notifiable Data Breaches Scheme Comes Down Hard on Healthcare
The healthcare industry is gaining a reputation for the dire state of their cyber security. Considering the fall-out risks human lives and exploitable data, it makes sense that the Notifiable Data Breaches Scheme now applies to all healthcare providers.
In the NDBS’s first yearly report, the OAIC reported that 55% of healthcare data breaches were a result of human error. Furthermore, the healthcare industry again led the pack for overall data breaches with 32% more reported breaches than finance – the next most targeted industry. Why? The healthcare sector has a cybercrime bullseye on it. The sheer amount of confidential patient information practices (and other healthcare facilities) hold make them a great target for hackers who want to steal information and return it for a price.
Get On Top of The Notifiable Data Breaches Scheme With Preventative Cyber Security
The aim of this blog is to give your business a clear course of action to take that will address all Notifiable Data Breaches Scheme concerns. To this effect, we will cover reporting on data breaches and mitigating the damage to your operations. A timely response is vital, but we cannot overstate the importance of preventative cyber security, like that offered by Stanfield IT’s cyber security services.
Our 11 Strategies For the Notifiable Data Breaches Scheme (prevention + being prepared!)
1. Find Out if The Notifiable Data Breach Scheme Applies to your Business
The NDBs applies to all businesses covered under the Privacy Act 1988–this isn’t just limited to healthcare.
Entities that have existing obligations under the Privacy Act to secure personal information must comply with the NDB scheme. This includes Australian Government agencies, businesses and not-for profit organisations that have an annual turnover of more than AU$3 million, private sector health service providers, credit reporting bodies, credit providers, entities that trade in personal information and tax file number (TFN) recipients.
https://www.oaic.gov.au/privacy/privacy-for-organisations/small-business/
Remember that The Notifiable Data Breach Scheme applies to:
- Healthcare providers
- Government agencies
- Credit reporting bodies & credit providers
- Tax file number recipients
- Agency or business that trades in personal information
Here is a more detailed list of what entities fall under the Privacy Act (all of which will thus have to comply with the notifiable data breaches scheme.)
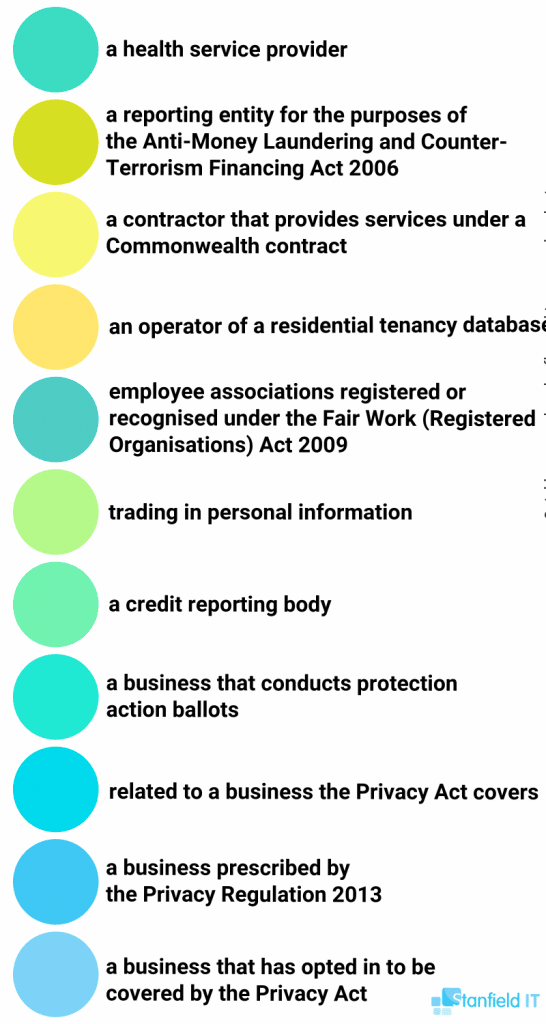
2. Understand Why The Notifiable Data Breach Scheme is Important
The sooner your business identifies that a data breach has occurred, the sooner you can mitigate the fallout and alert your customers, clients, and other stakeholders whose personal data may have been breached. These parties need to be notified ASAP, so they can take the necessary precautions (which you need to instruct them in, so you need to be across what steps an impacted person should take). For example, you may need to instruct them to change their password and place temporary holds on their bank accounts. When the dust settles, your customers and/or clients will remember how you responded to the data leak and guided them on how to handle things from their end. This will be appreciated.
Failing to notify entities fast enough that they can protect themselves can seriously impact your businesses brand and reputation. A reputation which is already in jeopardy in the wake of a data leak.
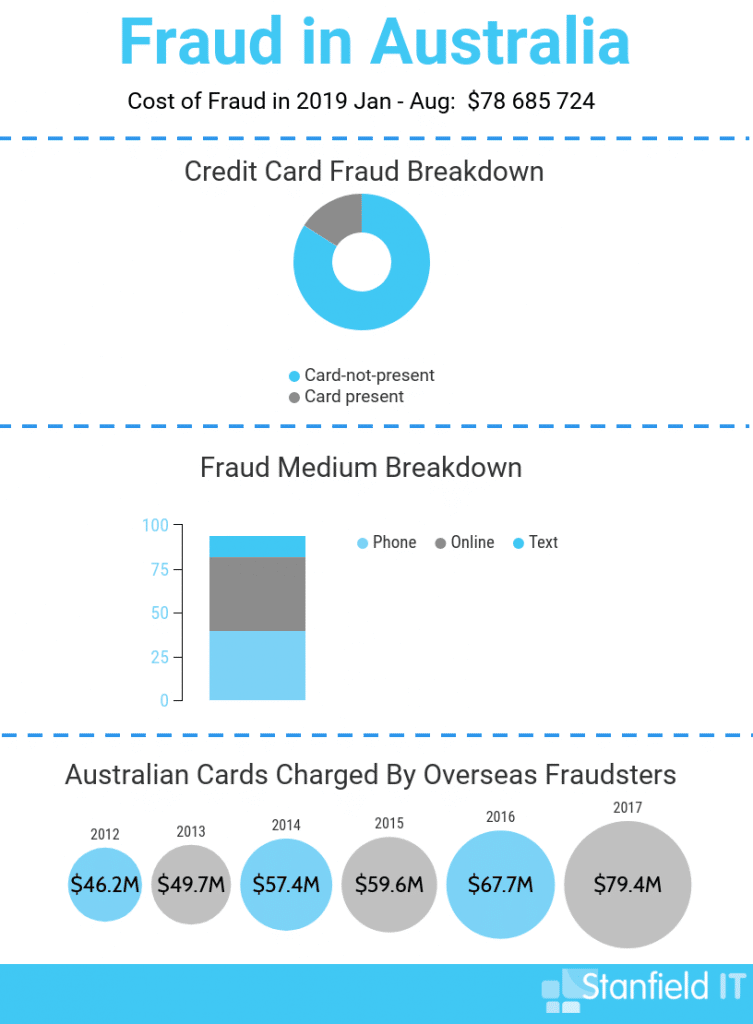
The Notifiable Data Breach scheme gives you 30 days to contact every affected entity and notify them. Failing to notify can result in fines and legal action. In a nutshell, the purpose of the Notifiable Data Breaches Scheme is to make companies accountable for data breaches.
In the OAIC’s first 12 month report – between the 1st of April 2018 and the 31st of March 2019 – there was a 712% increase in notifications following a breach. However, many breaches that fall under the scheme are still going unreported.
3. Lock Down and Restrict Employee Privileges
The OAIC reported that 35% of breaches in the first year of the Notifiable Data Breaches Scheme were caused by human error. The healthcare industry was the worst offender where human error accounted for 55% of data breaches.
It doesn’t have to be this way. There is a market overflowing with software solutions to configure access, and regain control. Restricting admin privileges is one of the ACSC’s essential 8 for cyber security. It’s great advice. Restrict who can use resources, and allocate all permissions according to an employees role in a company. You need firm business logic protecting your data assets.
For example, Microsoft Intune, is a cloud-based management solution used to implement app-level policies on corporate devices. Be it a laptop, phone, tablets or any corporate devices, it doesn’t matter. Access is enforced on the cloud making these solutions completely device agnostic. With Intune, or software like it, admins can control:
- Apps
- Password Complexity
- Geofencing (Where a user can sign in from)
- Data resources and assets
- Business policy
- MFA
- Device requirements
And much more…
Surprisingly, the source of a data breach can be as simple as an incorrectly addressed email. Most data leaks affected less than 10 people, yet companies are still wasting time and billing hours reporting these incidents to the Notifiable Data Breaches Scheme.
This is a super simple fix. With Microsoft Intune, you can set up Outlook and Office 365 to implement Data Loss Prevention. DLP will stop emails that contain sensitive information from being sent in the first place.
4. Install a Next-Generation Firewall
A next-generation firewall (NGFW) can monitor incoming and outgoing traffic to identify and block malicious applications. A NGFW is superior to a second-generation firewall. It will perform deep packet inspection to prevent threats hidden in encrypted traffic.
A traditional firewall is a good start, but can’t be depended on to filter malware. Only next-generation firewalls operate at the application level. While a traditional firewall has to close an entire port, an NGFW can block individual websites or application. Furthermore, a NGFW can be configured with Microsoft AD to prevent connections based on business logic and user identity. Combined with a better understanding of internet protocols, a NGFW can detect malware disguising itself as legitimate business operations.
Both Cisco and Fortigate offer exceptional next-generation firewalls. With this powerful software standing guard over your data, you’ve significantly reduced the risk of a data breach. In conclusion, an NGFW is a solid strategy for a business that doesn’t want to end up having to report to the Notifiable Data Breaches Scheme due to a data breach.

5. Device-Management Software to Comply With the Notifiable Data Breaches Scheme
Exactly as it sounds, device-management software manages all your devices. Businesses use this software to automate time-consuming IT tasks. For example, a common use for device management software is ensuring that all apps and the OS are up to date.
Furthermore, device-management software can implement conditional access that will keep data safe. The software will consider contextual factors like an IP address, behaviour, or device location before it decides if a login event is high-risk.
Then, based on the level of risk, the software can request a user complete MFA, or further authenticate before accessing an endpoint.
Device management software can also enforce device compliance policies. These could require that a computer is up to date before it connects to a network, or that an iPhone isn’t jail-broken. A chain is only as strong as the weakest link, and a network is only as secure as an unpatched operating system.
We have already covered Microsoft Intune, but there is a multitude of device management options on the market. If you want to learn more, look into Cisco’ Meraki, IBM’s MaaS360 and VMware’s Airwatch.

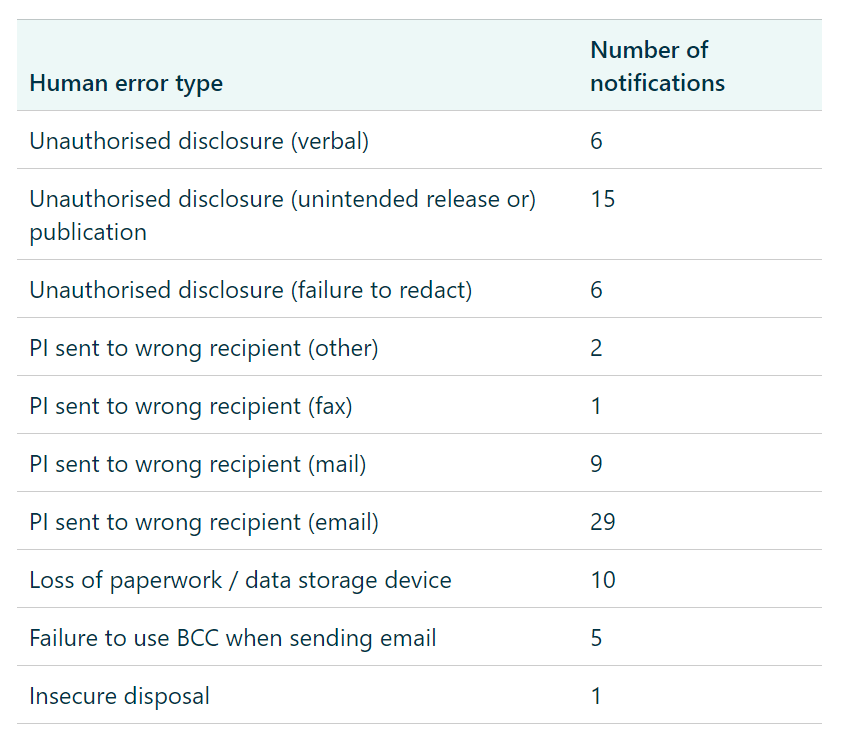
6. Mobile Device Management for Locking Down Phones & Laptops
Mobile device management is software that manages all the mobile devices in an organisation.
In case you have been living under a rock, people take their personal laptops and other mobile devices to work with them. It’s called BYOD culture, and while it’s the hip new trend for businesses to support, there are cyber security implications that must first be addressed.
It’s inevitable, one of your employees is going to pirate Game of Thrones and they are going to get malware.
To protect your business against this eventuality, MDM software can sandbox business data on a device. Most MDM Sand-boxing is done at an application level. It’s like a partition that digitally separates personal data from business data.
That isn’t all MDM software can do. With the press of a button, you can wipe the device of a disgruntled employee or enforce lock-out screens when the software detects suspicious behaviour. MDM can require that a user set complex passwords, prohibit jail-breaking, and disable a phone’s functionality when the device is in a certain area.
Get your devices under control to comply with the Notifiable Data Breaches Scheme.
7. Follow Industry Standards To Comply With the Notifiable Data Breaches Scheme
You don’t have to reinvent the wheel to comply with the Notifiable Data Breaches Scheme.
The healthcare industry has a wealth of well-thought-out industry standards to draw from. The RACGP standards are more than adequate for structuring a business continuity plan or preventing data breaches from occurring in the first place.
Are you in healthcare? Bookmark this PDF. It has whole sections of valuable information dedicated to preventative cyber security and best practices for backing up data. A common problem in the healthcare industry is ransomware. One of the many problems with ransomware is that it encrypts data so the practice can’t read it.
Food for thought, if your list of customers is inaccessible, and you need to notify mentioned customers about a data breach within 30 days, how exactly are you going to comply with the notifiable data breaches scheme?
Another way to conform to the Notifiable Data Breaches Scheme is to follow standards set in the ISO/IEC 27001. This internationally recognised framework has become the de facto standards for information security.
The ISO/IEC is unique in that it’s a risk-based approach. There is no one perfect solution that everyone should copy regardless of industry. Instead, the standard addresses risks and propose ways to reduce them.
8. Acceptable Usage Policies To Hold Employees Accountable
An organisation can enter into an agreement with an employee called an Acceptable Usage Policy. The gist of it is you can use the business’s network, provided it’s within the bounds of acceptable use stipulated in the acceptable usage policy document.
This bit of housekeeping can protect you from the commissioner, who under the Notifiable Data Breaches Scheme has the authority to investigate your business after an unreported breach.
It’s good practice to include a clause that requires employees report on data breaches. The 30-day timer for the Notifiable Data Breaches Scheme begins once someone in the organisation knows about the breach. If later it comes to light, that an employee knew about but failed to report on a breach then an Acceptable Usage Policy can help shift the blame to where it belongs.

9. Multi-factor Authentication Stops Hackers in Their Tracks
Receiving a secondary SMS code blocked 100 percent of automated attacks, 96 percent of bulk phishing attacks, and 76 percent of direct, targeted attacks – thenextweb
Multi-factor Authentication is the bane of a hacker’s existence.
To understand why put yourself in a hacker’s malicious shoes. You are up to no good. You have captured a corporate account and you are about to deploy your malware. In order to start your exploit, all you need to do is log in. Not to worry, you phished the email and password last week. Now that you’ve got that It will only take a couple of seconds to…
Oh no! The dreaded popup “a secret code has been sent to your mobile device. Please confirm the code” On the other side of the world, a confused employee receives a secret code and realises that someone is trying to access their account. Disaster averted. Passwords can be changed and no one needs to report a leak to the Notifiable Data Breaches scheme.
Every additional factor of authentication adds another layer to your defence. Protecting your data with 2-FA or 3-FA, makes it much much harder for a hacker to break through your authentication.
Passwords and usernames are the backbone of the modern internet and other networks. Unfortunately, employees are always going to set their password to “password” or add 00 to the name of their dog.
Hackers can socially engineer or guess passwords. Furthermore, if they can’t guess the password, they can recover it by answering a dead simple recovery question. Anyone with Facebook can work out where you went to school, or have a crack at your childhood best friend.
Because of the inherent weaknesses of passwords, MFA is now the industry standard.
10. Application White Listing To Combat Malware
Avoiding malware is hard. When there is malware disguised as racing games lurking in the Google Play store it is no longer just a matter of being careful.
To combat malicious applications we recommend application white listing software. Put simply, it maintains an index of approved applications. Applications left off the list are blocked, and they can’t be installed on a company device. Application white listing is one of the OAIC’s essential 8 for better cyber security.
Application white listing configures what applications can be installed. To control application privileges, you need application management. It will enforce what data apps can and cannot send once they are installed.
The technology has come a long way and now admins can limit application functionality within certain areas. A real-world example might be preventing employees from accessing certain apps outside the office, or disable the camera while in the workplace.
11. Train Your Staff For Organisation-Wide Cyber Security Improvements
It is unfortunate, but the general population has only the most basic operational understanding of how computers and the Internet work.
Hackers, on the other hand, are some of the most competent IT people on the planet. In another life, they would be working for Facebook or Microsoft.
This is who is trying to gain access to your network. Luckily, a little bit of education goes a long way. An investment in teaching employees the difference between good and bad cyber security will pay for itself 10 fold.
Employees don’t need to know Macros to know that they should never enable it. The risks of taking a photo of and sending personal data might not be immediately obvious to all your employees.
Too often, employees lack a basic understanding of cyber security threats and how their actions and behaviours can impact an organisation. In other cases, employees do not follow established protocols or the policies and procedures established by the organisation are too complicated or unwieldy. – Security roundtable

Don’t Get Caught Out by The Notifiable Data Breaches Scheme.
There is no such thing as perfect cyber security. All you can ever do is evaluate the risks and try to improve on what you’ve got. However, that is more than enough. You must implement these strategies and continue to learn about cyber security. It will improve the practices within your organisation and ensure you aren’t caught out by the notifiable data breaches scheme, or any scheme, for that matter, that the government has planned down the track.