“Cyber threats are constantly evolving” – Every cyber security writer.
If you’ve read a few articles on cyber security, there’s no doubt you’ve read the above line. Probably numerous times.
But there’s a reason that line persists. It’s because the evolution of cyber threats persists.
When end users get wise to one method of attack, hackers pivot and develop new methods. Or, they simply fall back to the old reliables like the USB drop.
Yes, people are still inserting USBs from unknown sources into their devices.
Yes, this is still a bad idea.
Now that we’ve got that covered, this short post will cover four growing cyber security threats that business leaders need to pay attention to.
These include:
- TOAD
- MFA-Bypass
- QR Codes
- Generative AI
Each comes with its unique methods, but all are essentially trying to achieve the same goal: exploiting vulnerabilities within business systems and processes to gain unauthorised access, extract sensitive information, or cause disruption.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
1. Telephone Oriented Attack Delivery (TOAD)
TOAD (Telephone-Oriented Attack Delivery) is a form of phishing that involves using telephone systems to initiate cyber attacks.
It combines techniques like vishing (voice phishing) and email phishing and exploits vulnerabilities in telecommunication systems.
Scammers use TOAD to manipulate victims into disclosing sensitive information over the phone by impersonating legitimate entities like financial institutions, trusted vendors or partners, and tech support or other internal departments.
How TOAD Plays Out
A typical TOAD attack follows this process:
-
- The attacker identifies a target.
- The attacker gathers information about the target: name, job title, any relevant information to make the attempt more convincing.
- Initial contact: the attacker initiates contact via a phone call, or sends an email requesting the victim to call them. This will appear legitimate.
- During the call, the attacker builds trust with the victim. Remember, they’ve done their research and can refer to information gathered before the call to seem credible.
- Information extraction or action encouragement: the attacker may directly request sensitive information like login credentials or financial information. Alternatively, they may tell the victim to take an action like transferring funds, providing remote access, or logging into a dangerous site and unknowingly infecting themselves with malware.
- Voila, the attacker has their way in and can exploit the system. Depending on their cover, they may even persuade the victim to refrain from disclosing the conversation or use the existing information to launch further attacks.
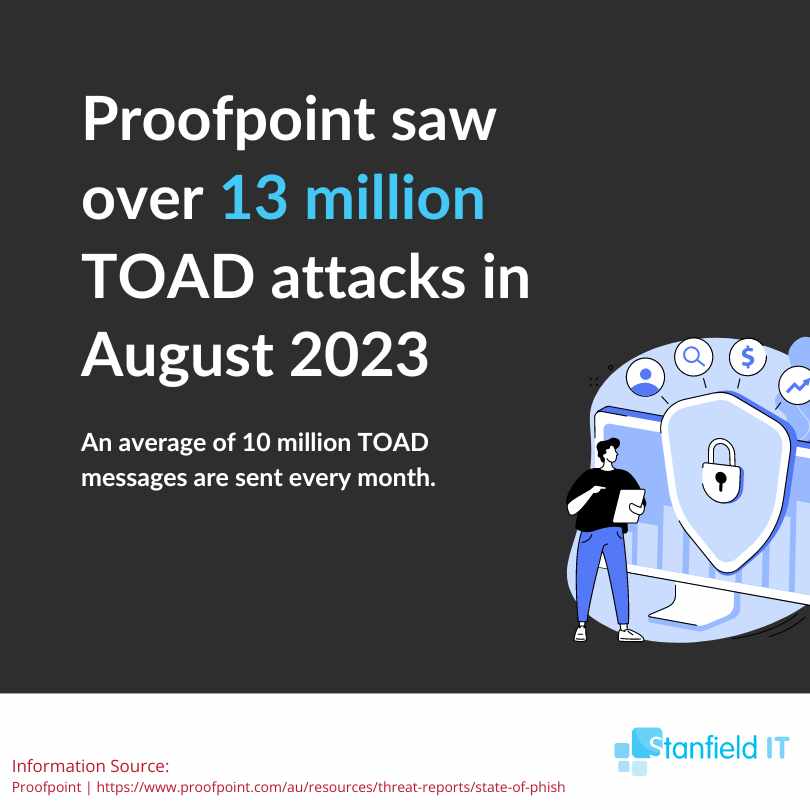
Proofpoint estimates that over 10 million TOAD messages are sent every month.
2. MFA-Bypass Techniques
Multi-Factor Authentication (MFA) has long been viewed as one of the best methods of preventing cyber attacks.
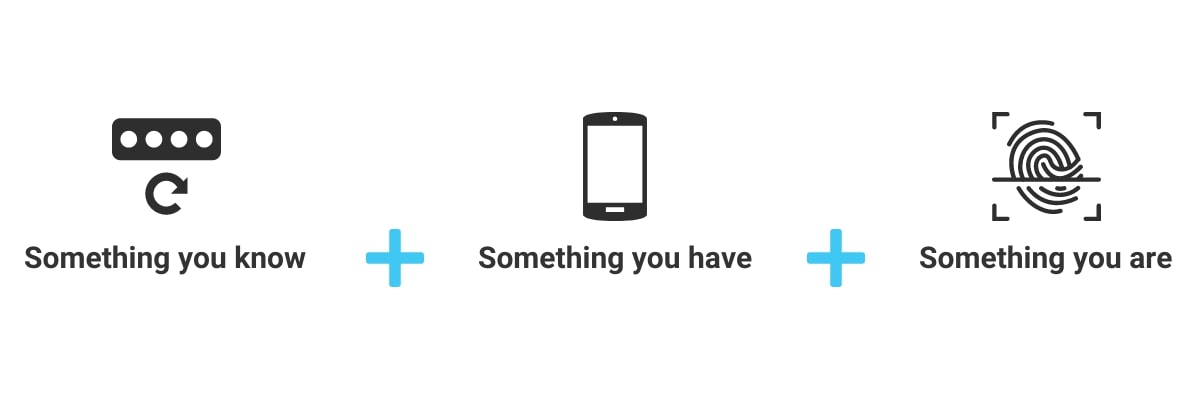
MFA is a security system that requires more than one method of verification from a category of credentials to verify a user’s identity.
Instead of asking only for a username and a password, MFA requires one or more additional factors. It’s designed to decrease the likelihood of a cyber attack.
However, while MFA does enhance your security, it’s not infallible. Attackers have developed various methods to bypass MFA, exploiting weaknesses in its implementation and user behaviour.
These advanced techniques often involve the use of proxy servers to intercept MFA tokens, enabling attackers to bypass the extra security layer offered by one-time codes and biometric verification.
Despite this, recent statistics show that 89% of security professionals believe that MFA can completely protect against account compromise.
While this underscores the general trust in what is regarded as an effective security measure, it also highlights a potential blindspot in recognising the limitations of MFA.
Don't miss out on our latest.
Join our subscribers and receive expert insights on cyber security and IT. Sign up now!
How Does MFA Bypass Occur?
MFA bypass happens through several methods, each exploiting weaknesses in MFA setup of user behaviour.
-
- Phishing Attacks: Attackers use phishing techniques to trick users into sharing their MFA codes. This can happen through fake login pages or social engineering techniques.
- SIM Swapping: The attacker convinces, bribes, or tricks a mobile carrier to switch the victim’s phone number to a SIM card they control, so they receive SMS-based MFA codes.
- Man-in-the-Middle Attacks: Here, attackers intercept communications between the user and the service. For example, using a proxy server to capture the MFA token sent during the transaction.
- Account Recovery Exploitation: Targets weaker security in the account recovery process, like using security questions or email-based reset links.
- Malware: Malware on a user’s device can capture MFA tokens or keystrokes, including one-time passwords.
- Session Highjacking: After the user authenticates via MFA, attackers can hijack the session, gaining control without needing MFA tokens.
- Push Notification Fatigue: Attackers continuously send MFA push notifications until the user accepts one, granting them access.
Example Uber Breach 2022
A real world example of MFA bypass is the 2022 Uber breach. This attack occurred after a hacker purchased stolen employee credentials from a dark web marketplace.
An initial attempt to log in was thwarted by MFA protection.
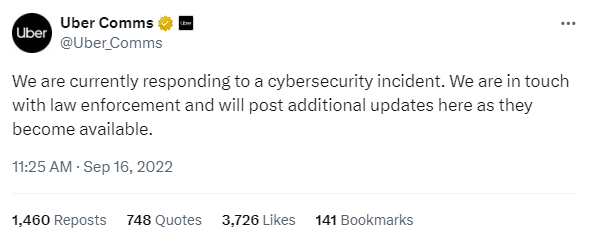
However, the attacker contacted the Uber employee via WhatsApp, impersonating Uber’s security team. They then asked the employee to approve the MFA notifications being sent to their phone.
The attacker then sent a flood of MFA requests to the employee. The employee, overwhelmed by the barrage of requests eventually approved one, unwittingly granting network access.
The attacker gained admin access to critical Uber systems, including their Privileged Access Management (PAM) solution. The hacker accessed sensitive scripts and unpatched security vulnerabilities, however there was no confirmed theft of customer data.
3. QR Code Vulnerabilities
Quick Response, or QR codes are two-dimensional barcodes that store information as a series of pixels in a square-shaped grid.
You can scan them using smartphone cameras or QR scanners to quickly access websites, data, or applications.
QR codes have become popular for various business operations including marketing to direct customers to websites, in payments for contactless transactions, and for sharing information like digital menus in restaurants.
Despite their convenience, QR codes pose a serious cyber security risk.
This is because they can be easily manipulated to direct users to malicious websites, leading to a phishing attack.
Alternatively, QR codes can initiate the download of malware onto a user’s device or trigger unauthorised transactions.
And they’re harder to detect than other phishing attacks.
For instance, if you’ve been sent a harmful link in an email, you can easily hover over the link and see where it’s going to take you.
With QR codes, it’s much harder to verify the code’s legitimacy or the safety of its embedded link before scanning.

How To Prevent QR Code Attacks
There are certain actions you can take to prevent QR code attacks:
-
- Only generate QR codes from secure sources.
- Regularly verify and update the linked content.
- Educate employees and customers.
- Use secure QR code scanners.
- Never scan a QR code to receive money.
- Don’t scan random QR codes in public, especially with company devices.
- Use software to read URLs before opening them.
4. Generative AI
Generative AI is a class of artificial intelligence that can create content such as text, images, and data models.
It operates by learning from existing data, identifying patterns and structures within this data, and then using this to generate content.
Sounds useful. And for many businesses it is.
However, the capabilities of AI bring in a new set of challenges.
As much as generative AI aids in innovation and efficiency, it offers the same powers to cyber criminals.
In early 2024 a Hong Kong firm suffered a $25 million (USD) loss to hackers using deepfake technology to impersonate the company’s chief financial officer and other staff members during a video conference.
These deepfakes were convincing enough to persuade a finance worker to transfer the substantial amount.
The attackers used previous recordings, likely from public appearances, to create AI-generated audio resulting in convincing deepfake representations.
This example highlights what is a rising trend of attackers using AI technology in their scams.
The ease with which attackers can create deepfakes is alarming, and will only proliferate as the technology develops.
So, business leaders must be vigilant and understand what they see and hear in the digital world may not be real.
And until businesses have effective and affordable AI detection technology at their disposal, vigilance is the best course of action.
Conclusion
There we have it. Four emerging cyber security threats that all business leaders should be aware of.
If you found this article helpful, please share it with anyone who wants to stay up to date with their cyber knowledge.
More Like This
Windows 10 End of Life (EOL) and What it Means
Microsoft has announced that October 14, 2025, will be the End of Life (EOL) date for Windows 10. Windows 10 EOL is set to affect all versions of Windows 10, including Home, Pro, Education, and Enterprise. Research from Lansweeper indicates that only 23.1% of...
ISO 27001 Certification in Australia: A Comprehensive Guide
Business data is like a treasure for cyber criminals. In fact, buried in almost every organisation's information assets are details worthy of holding ransom. So, how do you protect it? With ISO 27001 certification. ISO 270001 is more than just a standard industry...
Cyber Hygiene For Business: What You Need To Know
Implementing cyber hygiene practices is one of the most effective ways to protect your business from cybersecurity risks. As a business owner, the security of your company's data is paramount. With the prevalence of cyber-attacks in the modern world, it’s increasingly...



