Cyber threats are not only growing in number, but also in sophistication. But amidst all these changes, one vital thing remains consistent – the human factor.
The people in an organisation, their behaviour, and their decision making processes are central to the cyber security infrastructure. As a result, understanding and managing human risk has become a critical aspect of ensuring your business’s security.
Regardless of how strong your technical defences are, human error can easily open doors for cybercriminals.
In fact, research indicates that up to 85% of all cyber incidents involve a human element.
This statistic is more than just a number – it represents an emerging paradigm shift in the world of cyber security. Protecting your organisation from insider threats is no longer just about securing digital infrastructure; it’s also about empowering the people within your business.
So what can you do? Enter Human Risk Management (HRM). This is the practice of reducing your vulnerabilities and enhancing cyber security awareness among staff members. And it’s gaining traction as a critical component of a comprehensive cyber security strategy.
In this article, we’ll take a look at what human risk in cyber security entails, why it’s an essential consideration for all businesses, and how adopting effective HRM strategies can protect your organisation from cyber threats.
Human Error: The Unintended Access Point
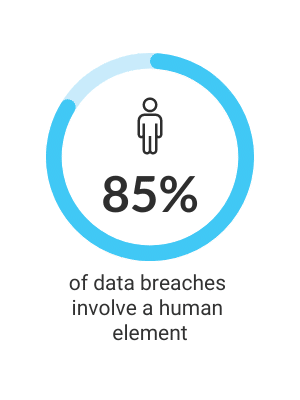
It’s a pretty alarming statistic, isn’t it?
A staggering 85% of data breaches involve a human element. It’s a truth that we can’t ignore – the vast majority of cyber threats stem from our own mistakes and oversight.
What makes up these human errors?
They can vary. For instance, it could be something simple, such as the use of weak or old passwords, or clicking on a malicious phishing link.
Alternatively, it could be something a bit more complex, such as the mishandling of security settings and configurations.
Let’s look at a few real-life case studies.
The Equifax Data Breach
In 2017, Equifax, one of the biggest credit agencies in the U.S., suffered a catastrophic breach.
The root cause? Human error.
Despite being notified by the U.S. Department of Homeland Security about a system vulnerability, the flaw went unaddressed due to oversight. This lapse allowed cyber attackers to infiltrate the system and expose the personal information of nearly 155 million people.
Ericsson Data Breach
In December 2018, a significant service outage occurred at Ericsson due to an expired digital certificate.
This human error disrupted millions of users worldwide. Outages like these can give opportunistic cybercriminals a window to bypass safeguards and launch attacks.
What Is Human Risk in Cyber Security?
Human risk refers to the potential for security breaches or incidents due to human actions, inactions, or errors.
It’s a recognition of the critical role that people play within the cyber security ecosystem.
While technology can help reduce vulnerabilities and protect systems from outside threats, it’s often less effective against human risks.
This is because they originate from within the business and are tied to human behaviour and judgement. This is what makes human risk one of the most challenging aspects of cyber security to manage.
Yet, despite its complexity, human risk is not an unsolvable problem. With the right strategies and tools, your business can significantly reduce the impact of human error. This is where human risk management comes into play. It focuses on addressing these human-related vulnerabilities through a combination of various security awareness programs, education technology, and policy enforcement.
The Evolution of Cyber Threats and the Role of Humans
Over the past few years, there’s been a distinct shift towards attacks that target human weaknesses. Let’s look at a few examples.
Phishing Attacks
Phishing attacks have become extremely sophisticated. They’ve evolved from basic, poorly-written emails to complex schemes designed to mimic trusted colleagues and businesses.
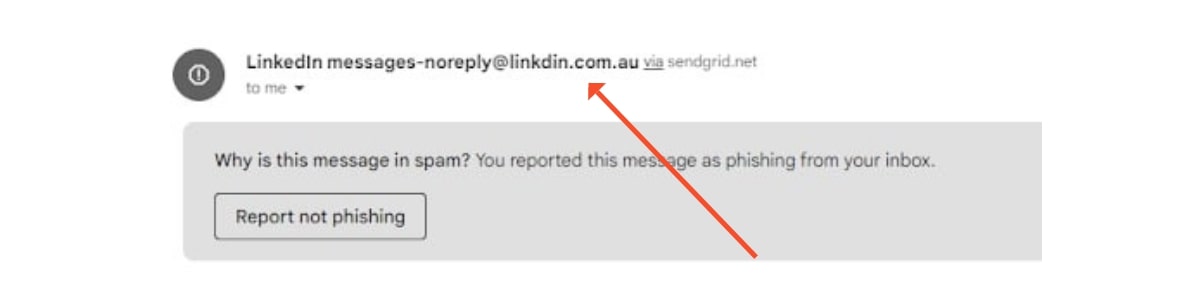
Business Email Compromise (BEC)
These are another prevalent type of attack that targets the human element.
In these scams, cyber criminals impersonate executives, board member or other key employees within a company, often financial roles.
Their aim is to manipulate other employees into transferring funds or exposing confidential data.
The success of BEC scams is heavily dependent on the target’s willingness to comply without question. This makes it a prime example of human vulnerability being exploited.
You can read more on these types of scams in our article here.
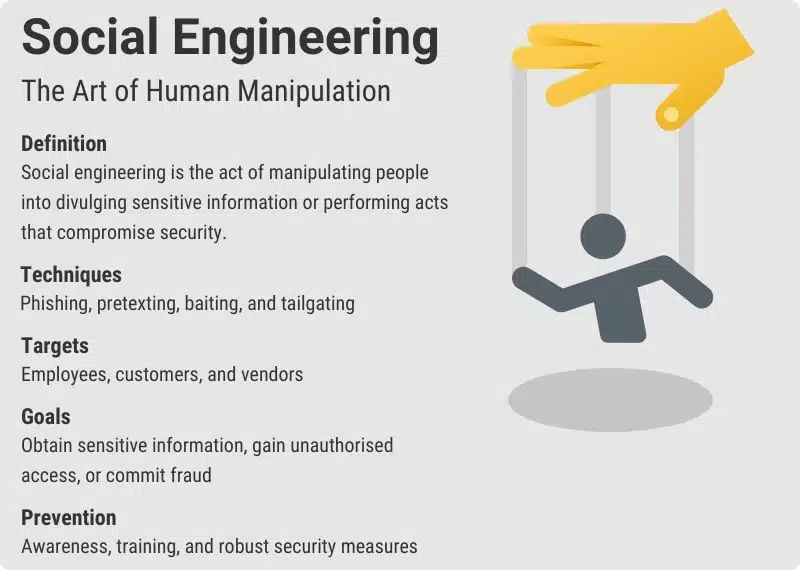
Social Engineering Attacks
Social engineering attacks involve a variety of methods, all of which are designed to manipulate people into performing actions or revealing sensitive information.
Again, these attacks prey on human traits such as trust, curiosity, or a desire to be helpful. Tactics range from impersonating trusted individuals or organisations, exploiting current events or crises, or baiting users with the promise of a reward.
Because the human factor plays a pivotal role in these threats, understanding and managing human risks is essential in developing a resilient cyber security strategy.
The Evolution of Cyber Threats and the Role of Humans
Managing human risk should be a top priority for all businesses. Here are some reasons why:
One of the biggest vulnerabilities
Studies consistently show that human error is a leading cause of cyber security incidents. Whether it’s a phishing attack or password compromise, people are often the weakest link in the security chain. By addressing human risk, you can mitigate one of the most significant sources of vulnerability in your business.
The threat landscape is evolving
Cybercriminals are increasingly targeting individuals because of the risk they pose. Social engineering attacks are becoming more common and harder to detect. As these threats evolve, it’s essential to keep your workforce updated and equipped to identify, recognise and respond to them effectively.
Regulatory compliance
Businesses are under pressure to uphold certain security standards introduced by regulations including the General Data Protection Regulation (GDPR) and the Australian Privacy Act. These regulations make protecting personal data a priority. Failure to manage human risk and security behaviour can lead to breaches that carry heavy fines and penalties.
Create a security-conscious culture
Human risk management isn’t just about reducing errors; it’s about creating a security-conscious culture. When your employees understand the role they play in cyber security they’re more likely to take ownership of their actions and contribute to your overall cyber security posture.
Protect your reputation and trust
A single cyber security incident can destroy a business’s reputation. Consumers value their data and trust businesses to protect it. Effective HRM can help preserve customer trust and protect your business’s reputation.
The Cost of Ignoring Human Risk
Neglecting the human factor can lead to some pretty severe consequences that extend beyond financial losses. Companies that overlook human risk are leaving themselves vulnerable to cyber attacks. This could have long-lasting impact on their operations, reputation, and customer trust.
- Financial Implications are the most immediate and tangible consequences of a breach. From ransom payments to fines and lost business opportunities, the aftermath of a cyber incident can create a financial burden. For smaller businesses, these costs may even lead to business closure.
- Operational Disruptions can also result from an attack. Data breaches and system infiltration can lead to downtime, during which companies may not be able to deliver their service. These disruptions can lead to loss of productivity, missed deadlines, and unhappy customers.
- Reputational Damage is another significant cost. If you’re part of a breach, you’re not just losing data, you’re also losing customer trust. This can severely harm your brand image and lead to loss of business.
So What Is Human Risk Management?
HRM is a strategic approach that turns the cyber security vulnerabilities posed by human error into strengths.
It’s a comprehensive process that acknowledges the risks associated with online human behaviour and takes proactive action to mitigate them.
Basically, HRM aims to convert the weakest link in cyber security – people – into a strong line of defence. There are a few strategies that go into this.
Educating employees
HRM promotes regular, tailored cyber security awareness courses and training that keeps employees informed about the latest cyber threats and best practices.
Promote behavioural change
A cornerstone of HRM is creating a strong cyber security culture within the business. It encourages employees to view cyber security as a necessity rather than an inconvenience. In doing so, it incentivises safe behaviours and promotes responsibility for cyber security at all levels.
Enforcing strong policies
Implementing and enforcing strong cyber security policies and procedures is a key part of HRM. These policies align with industry standards and regulations, ensuring compliance and enhancing security.
Leveraging technology
HRM uses sophisticated tools and solutions to bolster the human element of cyber security. This includes automated processes, detecting threats early, and providing safeguards against common use errors.
Our Approach to Human Risk Management
We understand the need to address the human risk factor in cyber security.
This is even more critical now as more people work from home, which expands the cyber security attack surface.
Recognising these challenges, we’re proud to announce that Human Risk Management will be incorporated into our service. This solution is specifically designed to assist your business in identifying, measuring, and managing human cyber risk, all while ensuring seamless integration into your existing workflows, causing minimal disruption to productivity.
Our HRM service brings several key features and benefits to your business:
- Minimise Human-Related Security Incidents: Our approach aims to reduce incidents, fines, and financial losses resulting from human error.
- Boost Resilience Against Targeted Attacks: We strengthen your business’s resilience against targeted attacks by fortifying the human component of your cyber security architecture.
- Ensure Compliance: Our HRM service aligns with leading cyber security frameworks such as ISO 27001, helping you maintain compliance.
How Does It All Come Together?
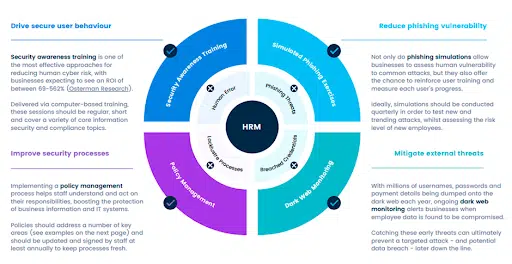
Our HRM service is designed as a well rounded package if tools and strategies that foster a cyber security aware culture in your organisation:
- Customised Security Awareness Training: Our service includes regular training modules tailored to your employee’s roles and responsibilities. These short video sessions educate staff about the latest cyber security threats and countermeasures.
- Periodic Phishing Simulations: Our service includes monitoring of the dark web for any exposed user credentials related to your business. This proactive approach allows us to alert you to potential threats before they materialise into attacks.
- Policy Management: We simplify your cyber security policy management processes by tracking employee acknowledgements, automating policy reminders, and ensuring everyone is up to date with their responsibilities.
Get Insight Into Your Human Risk Profile with Our Free Human Risk Report (HRR)
We’re excited to offer you the chance to gain a better understanding of your business’s human risk landscape with our free Human Risk Report (HRR).
This report is key to unlocking the human risk factors at play within your business. By following a few simple steps, we’ll generate a unique human risk score for your business and, most importantly, provide you with a strategic roadmap to bolster security in areas of concern.
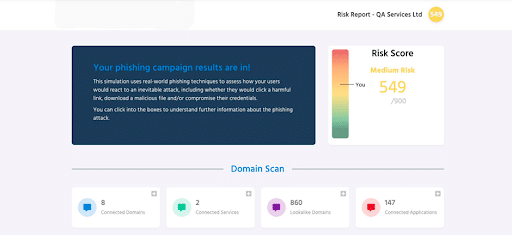
You can take a look at an example Human Risk Report here.
To start your free Human Risk Report, simply fill in the form on this page.
We’ll begin the process of your human risk scoring by identifying potential vulnerabilities and providing you with valuable insights into managing your human risk more effectively.
More Like This
Windows 10 End of Life (EOL) and What it Means
Microsoft has announced that October 14, 2025, will be the End of Life (EOL) date for Windows 10. Windows 10 EOL is set to affect all versions of Windows 10, including Home, Pro, Education, and Enterprise. Research from Lansweeper indicates that only 23.1% of...
ISO 27001 Certification in Australia: A Comprehensive Guide
Business data is like a treasure for cyber criminals. In fact, buried in almost every organisation's information assets are details worthy of holding ransom. So, how do you protect it? With ISO 27001 certification. ISO 270001 is more than just a standard industry...
Cyber Hygiene For Business: What You Need To Know
Implementing cyber hygiene practices is one of the most effective ways to protect your business from cybersecurity risks. As a business owner, the security of your company's data is paramount. With the prevalence of cyber-attacks in the modern world, it’s increasingly...



