The recent cyber attack on DP World Australia, a major global shipping operator, should serve as a lesson for all businesses.
In November 2023, the shipping giant was hit by a cyber attack.
The breach didn’t just disrupt their operations; it led to a data compromise, posing a serious question about data security and operational resilience.
What started as a regular day at work was suddenly disrupted by a system failure.
This isn’t the first time a major Australian organisation has been hit by a cyber attack. Yet, it still reveals an uncomfortable truth: no one is immune to cyber threats.
In this article, we’ll go over what we know about the DP World incident to understand what went wrong and how it could have been prevented.
We aim to provide actionable insights and strategies, helping businesses like yours strengthen their defences.
Hopefully, these insights will help prevent cyber incidents and ensure continuous operation even when the unexpected happens.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
Section 1: The DP World Cyber Incident
Let’s take a look at how the incident unfolded.
The attack was first detected after discovering unusual activity in their IT systems.
And the cyber intrusion was unfortunately not just a technical glitch.
Initial Impact
The initial impact was staggering. DP World’s operations were hindered, impacting about 40% of Australia’s import and export capacity.
The disruption also had a domino effect, causing delays and logistical challenges across the shipping industry.
It was a situation that highlighted just how interconnected and vulnerable modern supply chains are to cyber threats.
Data Breach Details
Amidst the operational chaos, a more insidious problem was uncovered: a data breach.
Hackers had managed to access and possibly exfiltrate sensitive information.
The extent of the data breach is not fully known, but the potential risks are clear. Such data breaches can lead to significant security and privacy concerns, especially if personal or confidential information is involved.
Response Actions
To its credit, DP World’s response to the attack was swift. To contain the breach and prevent further unauthorised access, the company disconnected its systems from the internet.
This decisive action was crucial for security. However, it further compounded the operational disruptions.
These are the tough but necessary choices business leaders have to make during a crisis. They need to strike a balance between immediate response and maintaining operations.
Section 2: Cyber Security Risks and Business Impact
Digital interconnectedness is a business norm, so you need to understand cyber security risks no matter what your role is.
These risks range from data breaches and ransomware to sophisticated phishing attacks. Each carries the potential to disrupt business operations significantly.
Understanding Cyber Security Risks
This could be an entire article in itself.
Cyber security risks encompass any potential hostile activity that seeks to unlawfully access, steal, or damage data.
These risks increase each year. Not just in frequency but also in complexity.
Businesses today face an array of threats, from internal vulnerabilities to external hacking attempts, each capable of breaching their defences.
Operational Impact of Cyber Attacks
The immediate impact of cyber attacks is most visibly seen in operational downtime.
For DP World, this interruption meant a temporary halt in port operations, leading to significant delays in the movement of goods. This showcases a direct hit on business continuity.
This disruption goes beyond the company itself, affecting the entire supply chain; including suppliers, customers, and end consumers.
Key impacts include:
- Financial Repercussions:
- Direct losses due to halted operations and, in some cases, ransom payments.
- Indirect costs such as lost sales, customer compensations, and increased insurance premiums post-incident.
- Customer Service and Experience:
- Delays and unreliability, which are common post-attack, can break contracts and erode customer trust.
- The inability to deliver services can harm reputation, leading to customer churn.
- Compliance and Legal Concerns:
- In regulated industries, attacks involving customer data can lead to legal penalties and compliance violations.
- These issues add to the financial and reputation strain on businesses.
- Internal Impact on Employees:
- Increased workload, leading to employee stress and burnout.
- Need for additional training or upskilling, particularly if the attack exploited knowledge gaps.
As you can see, the operational impact of cyber attacks is multifaceted and extends beyond the immediate interruption of services.
Section 3: Importance of Regular Security Updates
Staying updated is a necessity for safeguarding against cyber threats.
Security patches, essentially updates that fix vulnerabilities in software and systems, play a crucial role in this defence.
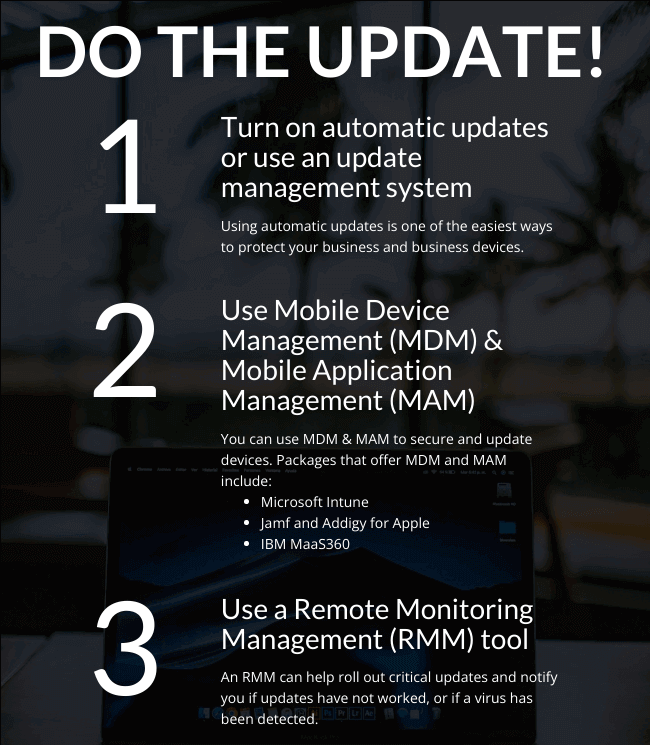
The Role of Security Patches
Security patches address vulnerabilities that hackers can exploit.
Outdated software is a prime target for cybercriminals, as it often contains unaddressed security gaps.
Therefore, regularly updating systems is critical to close those vulnerabilities and protect against attacks.
This is a key recommendation in the ACSC’s Essential Eight.
Case Study: DP World’s Security Lapse
The DP World cyber incident highlighted the risks of neglecting software updates.
It’s believed the company had overlooked a known CitrixBleed vulnerability when it was hit by the cyber attack.
It may have been that simple. This shows that an unpatched flaw can have serious consequences for any business.
What Happens When You Don’t Update?
Failing to apply security updates can lead to severe repercussions:
- Vulnerabilities left unpatched are easy targets for cybercriminals.
- Data breaches resulting from outdated systems can cause significant financial and reputational damage.
It’s estimated that up to 60% of cyber attacks exploit known vulnerabilities that could have been patched.
Best Practices in Patch Management
Effective patch management involves:
- Regularly reviewing and applying security patches.
- Prioritising updates based on severity of vulnerabilities.
- Automating updates where possible to ensure timely application.
Challenges in Keeping Systems Updated
While updates are important, many businesses often face challenges in keeping up:
- Limited IT resources can hinder regular checks.
- Some systems may require complex or time-consuming updates.
To overcome these challenges, businesses can:
- Allocate dedicated resources for cyber security.
- Implement automated update systems to ensure consistency.
Section 4: Proactive Cyber Security Measures
With cyber threats increasing, adopting a proactive approach to cyber security has become essential for the survival and resilience of businesses.
This strategy is about staying ahead, anticipating risks, and taking preventive measures to avoid serious crises.
Understanding Proactive Cyber Security
Proactive cyber security means continuously staying ahead of potential threats, rather than reacting to them after the fact.
It’s about identifying and fixing vulnerabilities, training your staff, and implementing strong security protocols before any breach occurs.
Key Proactive Measures
Several key measures are vital for a proactive cyber security stance.
- Regular Risk Assessments: Conducting frequent evaluations of your IT infrastructure to identify and address vulnerabilities.
- Employee Training and Awareness: Regularly educating staff on cyber security best practices and potential threats.
- Robust Security Policies and Procedures: Developing and enforcing clear policies to protect data and systems.
- Advanced Cyber Security Technologies: Investing in modern technologies like AI-driven threat detection systems for real-time monitoring and response.
Learning from the DP World Incident
The DP World cyber incident demonstrates the consequence of a reactive, rather than proactive, cyber security approach.
Had there been more rigorous and regular system checks and employee training, the impact of the attack might have been mitigated or even prevented.
Building a Cyber-Resilient Culture
Creating a culture of cyber security within an organisation is critical. This involves:
- Integrating cyber security practices into daily operations.
- Encouraging open communication about cyber security issues.
- Rewarding proactive security behaviours among employees.
Regular Testing and Updating of Cyber Security Plans
Having a cyber security plan is a start, but it can’t stop there. Regular testing and updating are crucial. This could include:
- Conducting drills and simulations to test the effectiveness of response plans.
- Regularly reviewing and updating the cyber security strategy to address new and emerging threats.
Don't miss out on our latest.
Join our subscribers and receive expert insights on cyber security and IT. Sign up now!
Section 5: Business Continuity Planning (BCP) in the Cyber Age
Introduction to Business Continuity Planning (BCP)
With the complexities of modern threats, Business Continuity Planning has become a consideration of vital importance.
The unique challenges presented by digital operations demand a reevaluation of traditional BCP models.
In this section, we’ll explore how BCP has adapted to address digital risks, focusing on the integration of cyber security as a core component.
The goal is to equip businesses with the knowledge and tools to ensure continuity and agility in the face of digital disruption.
Risk Assessment
The first step in a strong BCP is conducting a thorough risk assessment with a focus on cyber risks.
This process involves identifying not just the probability of various cyber incidents but also their potential impact.
This risk assessment should be comprehensive, considering everything from data breaches and ransomware attacks to insider threats and system failures.
The findings of this assessment guide the development of tailored strategies to mitigate identified risks.
Business Impact Analysis
Once you’ve identified the risks, a business impact analysis (BIA) becomes critical.
This analysis looks into how cyber threats could affect different aspects of your business.
It’s about mapping the potential consequences of cyber incidents on operations, finances, customer relations, and reputation.
A well-conducted BIA helps in prioritising resources and efforts, focusing on protecting the most critical aspects of the business.
Understanding the impacts also aids in crafting communication strategies to manage stakeholder expectations during and after an incident.
Recovery Strategies
An integral part of business continuity planning is developing effective recovery strategies to ensure business operations can be resumed quickly and efficiently after a cyber incident.
These strategies should include detailed plans for:
- Restoring IT systems and data.
Maintaining critical operations during the recovery phase. - Managing communications with customers, employees, and other stakeholders.
Recovery plans should be flexible and adaptable, capable of responding to various scenarios.
Regular testing and updating of these plans are essential to ensure they remain effective.
Integrating Cyber Security Into BCP
Incorporating cyber security into BCP ensures that responses to cyber threats are not isolated incidents, but part of a comprehensive approach to maintain business continuity.
Aligning Cyber Security with Business Continuity Objectives
The alignment of cyber security efforts with overall business continuity objectives is also critical.
It involves a holistic view where cyber security is not seen in isolation but as an integral part of your business’s resilience strategy.
This alignment ensures that the measures taken to protect against cyber threats also support the broader goals of maintaining operational continuity.
It requires collaboration across various departments, ensuring that cyber security considerations are embedded in all business planning and decision-making processes.
Incident Response
A major component of integrating cyber security into BCP is the development of an incident response plan.
This plan outlines the steps for immediate and effective action in the event of a cyber breach. Key components of an incident response plan include:
- Identification of key roles and responsibilities during an incident.
- Procedures for quickly isolating and mitigating the impact of a breach.
- Steps for assessing the scope and impact of the incident.
- Protocols for internal and external communications.
Communication Plan
Equally important is a well-structured communication plan.
During a cyber incident, clear and timely communication is vital to manage the situation effectively. The communication plan should detail:
- How and when to inform internal stakeholders, including employees and management, about the incident.
- Guidelines for communicating with external parties, such as customers, suppliers, and regulatory bodies.
- The designation of a spokesperson or team to handle all external communications.
- Strategies for maintaining transparent and consistent messaging throughout the incident and recovery phase.
By including these cyber security steps in your business continuity plan, your business will be ready to respond quickly and keep your operations running smoothly in line with your overall strategy.
Testing and Updating the Business Continuity Plan
For a BCO to remain effective it must be regularly tested and updated.
This process ensures that the plan stays relevant and capable fo addressing new challenges as they arise.
The Need for Regular Testing and Revision
A BCP that was effective last year may not be today.
Regular testing and revision of the BCP is crucial in keeping pace with changes. This process involves:
- Periodically reviewing the plan to ensure it reflects the current threat environment and business operations.
- Adjusting strategies and protocols to address any new vulnerabilities or changes in the business structure.
- Ensuring that any updates in technology or processes are reflected in the BCP.
Conducting Effective BCP Drills
Effective BCP drills are essential for testing the plan’s efficacy and your team’s readiness to execute it.
These drills should simulate realistic cyber incident scenarios to assess how well the plan works in practice. Key aspects fo conducting these drills include:
- Creating scenarios that mimic potential cyber threats the business might face, such as a data breach or ransomware attack.
- Involving all relevant stakeholders in the drill, including IT, communications, and leadership teams.
- Evaluating the response during the drill to identify any gaps or weaknesses in the plan.
- Providing feedback and conducting a debrief post-drill to discuss lessons learned and areas for improvement.
Regularly testing and updating your business continuity plan will ensure your business is prepared for the challenges of tomorrow.
Leverage ‘Business Continuity in a Box’
The Australian Cyber Security Centre’s (ACSC) initiative, ‘Business Continuity in a Box’, offers valuable support, especially for small to medium-sized businesses (10-300 employees).
Developed with contributions from the United States Cybersecurity and Infrastructure Security Agency (CISA), it provides an interim solution to swiftly and securely continue critical business functions during or following a cyber incident.
The package focuses on two components: Continuity of Communications and Continuity of Applications.
This resource can be an immediate solution if your organisation does not have a recent or relevant BCP.
No, it won’t replace a comprehensive BCP. However, it can be integrated into existing plans, particularly focusing on email communications and critical applications.
Section 6: Building a Cyber-Resilient Culture
Creating a cyber security culture is about instilling a mindset where every member of the organisation prioritises and contributes to cyber security.
Defining Cyber-Resilient Culture
A cyber-resilient culture is one where cyber security is ingrained in every aspect of the business.
It’s a culture that recognises the importance of proactive defence and collective responsibility in protecting digital assets. Such a culture is critical in minimising risks and ensuring quick recovery in the event of a breach.
Leadership and Cyber Resilience
Good leadership is critical in shaping a cyber-resilient culture.
It starts from the top, with leaders setting a tone by prioritising cyber security in their agenda and decision-making.
Leaders should actively promote cyber security awareness and demonstrate its value through their actions and investments.
Employee Engagement and Training
Employees are often the first line of defence against cyber threats.
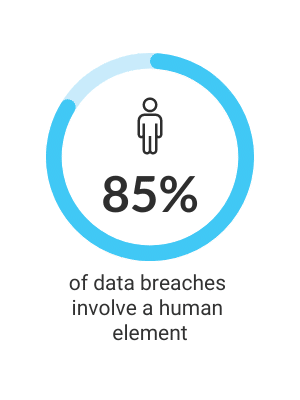
For this reason, regular training and awareness programs are essential to keep them informed and vigilant.
Engaging employees through interactive sessions, simulations, and continuous learning opportunities can foster a more security-conscious workforce.
Integrating Cyber Security in Business Processes
Embedding cyber security into the fabric of business processes is key. This integration can be achieved by:
- Making cyber security a standard part of business decision-making.
- Implementing clear policies and procedures that reinforce secure practices.
- Leveraging technology to automate and support cyber security measures.
Continuous Improvement and Adaptation
Cyber security is an ongoing process.
As a business, you need to continually assess and improve your cyber security strategy and adapt to new threats and changing landscapes.
This requires keeping up-to-date about the latest cyber security trends and threats and being ready to evolve and adapt as necessary.
Section 7: Broader Implications and Questions
The DP World cyber incident, along with similar breaches in companies like Boeing and Allen & Overy, underscores the critical reality for businesses of all sizes: cyber security is a pervasive challenge that requires both global awareness and local action.
Direct Business Implications of Global Cyber Security Trends
Understanding the Threat Landscape
Recognising that large-scale vulnerabilities like CitrixBleed can impact businesses worldwide, companies should keep informed about global cyber security trends.
This knowledge helps in assessing their vulnerabilities and preparing accordingly.
Learning from Big Players
Watching how major organisations respond to cyber attacks can provide valuable lessons for smaller businesses.
Strategies employed by these organisations, such as rapid response protocols and communication strategies, can be adapted to fit the scale and scope of smaller enterprises.
Cyber Security as a Practical Business Concern
Risk Management
Every business, regardless of size, should incorporate cyber security into its risk management strategy.
This includes regular risk assessments and creating contingency plans for potential cyber-attacks.
Employee Training and Awareness
Cyber security is a company-wide concern. Regular employee training on cyber security best practices is essential to make your first line of defence stronger.
Navigating Cyber Security in a Connected World
Collaborative Defence
Small and medium-sized businesses can benefit from collaborative efforts, such as industry-specific cyber security groups, sharing threat intelligence, and pooling resources for better defence mechanisms.
The ACSC has helpful cyber security resources for smaller businesses here.
Compliance and Legal Responsibilities
Staying compliant with local and international data protection laws is crucial.
Businesses should keep abreast of legal requirements to avoid penalties and maintain customer trust.
Questions for Every Business
In light of these recent considerations, businesses should reflect on:
- How well-prepared are we to handle a security breach?
- Do we have a clear understanding of our legal and ethical responsibilities in the event of a data breach?
- How can we better collaborate within our industry and with cyber security experts to enhance our defences?
Conclusion
The DP World cyber incident highlights the critical need for comprehensive cyber security across all businesses.
It’s a clear call to action for enjoying vigilance, regular updates, and company-wide awareness.
As businesses, we all need to evolve our strategies for combating cyber threats.
Some of our latest
Windows 10 End of Life (EOL) and What it Means
Microsoft has announced that October 14, 2025, will be the End of Life (EOL) date for Windows 10. Windows 10 EOL is set to affect all versions of Windows 10, including Home, Pro, Education, and Enterprise. Research from Lansweeper indicates that only 23.1% of...
ISO 27001 Certification in Australia: A Comprehensive Guide
Business data is like a treasure for cyber criminals. In fact, buried in almost every organisation's information assets are details worthy of holding ransom. So, how do you protect it? With ISO 27001 certification. ISO 270001 is more than just a standard industry...
Cyber Hygiene For Business: What You Need To Know
Implementing cyber hygiene practices is one of the most effective ways to protect your business from cybersecurity risks. As a business owner, the security of your company's data is paramount. With the prevalence of cyber-attacks in the modern world, it’s increasingly...



