In the world of finance, trust is currency. It can’t be bought. And once you get it, it can be lost instantly.
For many financial institutions, it’s a simple equation. Lose your customer’s trust and you’re done—time to shut up shop.
You end up in a situation like this:

The Australian financial sector is a vast network of banks, credit unions, and fintech companies.
It’s also the ultimate treasure trove of data – data constantly under siege from cyber threats.
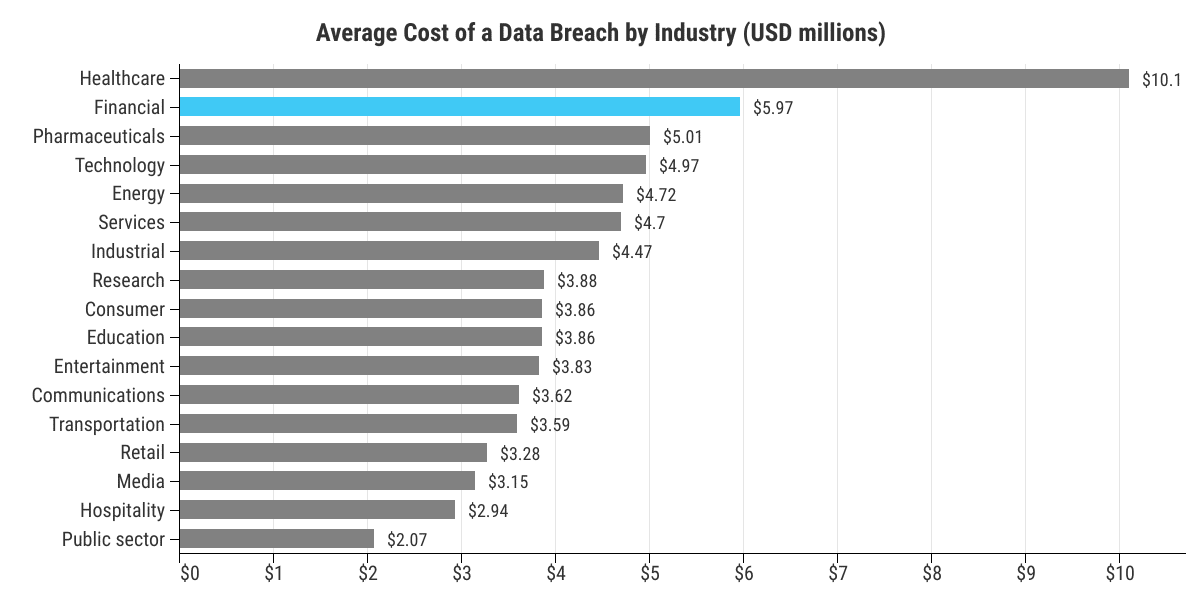
And when the global average cost of a data breach in the financial industry is a staggering $5.97 Million (USD), you understand the importance of robust cyber security measures in the sector.
In this guide, we’ll navigate the terrain of cyber security within the financial services sector. From understanding the unique threat landscape and regulatory environment to assessing your organisation’s cyber security health and exploring the key components of a strong cyber security plan, this guide aims to provide valuable insights for every financial institution looking to secure its defences.
So, whether you’re a seasoned cyber security professional looking to stay updated, or a financial executive aiming to understand your organisation’s risk exposure better, this guide has something for you.
Let’s begin.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
The Cyber Threat Landscape for Australian Financial Services
Sophisticated cyber threats are targeting the financial sector more than ever before. ANZ, one of Australia’s largest banks, has previously stated they fight off close to 10 million cyber attacks per day.
Understanding these threats is the first step towards effective cyber security. Here are a few to be aware of.
Cyber Attacks That Target The Financial Sector
Phishing
A common method cyber criminals use is sending fraudulent emails that appear to come from a legitimate source. They aim to trick the recipient into revealing sensitive information such as:
-
- Passwords
- Credit card numbers
This can lead to unauthorised access to vital systems and loss of customer trust.

Ransomware
This malware effectively holds a company’s data hostage by encrypting it and demanding a ransom to restore access. This can cause operational disruption and financial losses, especially if the ransom is paid but access is not restored.
DDoS Attacks
Distributed Denial of Service (DDoS) attacks involve overwhelming a network with traffic to cause a shutdown. For a financial institution, this can cause severe service disruption. The result? Potentially millions of dollars in lost transactions and customer goodwill.
Recent Attacks on Australian Financial Institutions
Unfortunately, theoretical threats aren’t just hypothetical. In recent years we’ve seen several high-profile cyber-attacks on Australian financial institutions.
The Latitude Hack – 2023
The Latitude hack is one of the most notable recent examples of an attack in the financial sector. In March 2023 an attacker accessed the login credentials of a Latitude employee.
They then stole the personal information of almost 14 million current and previous Latitude customers.
The personal information stolen included driver’s licence numbers, passport numbers, and financial statements.
Naturally, they made a ransom request, which Latitude reportedly refused to pay.
Levitas Capital – 2020

In 2020, Sydney-based hedge fund Levitas Capital experienced a devastating attack that ultimately lead to its closure.
The infiltration began when one of the company’s co-founders opened a fake Zoom invite that planted malicious software onto the Levitas network. This breach granted full access to the firm’s email systems.
Using their ill-gotten access, the attackers sent fraudulent invoices to companies with which Levitas had no previous dealings.
By the time the breach was discovered, over $8 million had already been transferred out of Levitas’ Commonwealth Bank account.
Despite efforts to halt the transactions, many of the transferred funds were not recovered.
Levitas’ largest client pulled a planned $16 million investment, and the fund closed down shortly after.
The Regulatory Environment
The Australian financial services sector operates under a complex framework of regulations. These are designed to protect customers, maintain the financial system’s integrity, and promote cyber security.
These regulations also play a critical role in protecting sensitive financial data from cyber threats.
APRA’s CPS 234
A key regulation related to cyber security in the financial sector is the Australian Prudential Regulation Authority’s (APRA) Prudential Standard CPS 234.
This standard specifically addresses information security and requires APRA-regulated entities to implement strong cyber security measures to mitigate the likelihood and negative impact of cyber security incidents.
APRA’s CPS 234 mandates financial institutions to:
-
- Clearly define the information security related roles and responsibilities within their organisation.
- Maintain an information security capability proportionate with their size and the extent of threats to their information assets.
- Implement controls to protect these assets.
Furthermore, it requires them to regularly test these controls for effectiveness, promptly notify APRA of material information security incidents, and conduct periodic reviews of their information security capability.
ASIC
In addition to APRA, the Australian Securities and Investments Commission (ASIC) also plays a significant role in shaping cyber security practices within the financial sector.
ASIC’s focus on cyber security stems from its mandate to ensure that Australia’s financial markets are fair and transparent. To this end, it provides guidelines to entities under its purview to manage and mitigate their cyber risks.
You can ASIC’s cyber resilience good practices here.
Together, APRA and ASIC establish the regulatory backdrop against which financial institutions must navigate their cybersecurity strategies.
Compliance with these standards and guidelines is not merely a matter of legal obligation. Rather, it’s a vital component of maintaining trust in the financial sector and ensuring the sector’s resilience against cyber threats.
Assessing Your Organisation’s Cyber Security Health
To strengthen your defences you need to regularly assess your cyber security health. This evaluation helps uncover potential vulnerabilities, allowing you to quickly address them.
This process consists of two essential steps: conducting a cyber security risk assessment and identifying potential vulnerabilities.
Conducting a Cyber Security Risk Assessment
A cyber security risk assessment is a structured evaluation of your organisation’s information systems and technology, procedures, and policies. It identifies the risks that your organisation faces, the likelihood of their occurrence, and their potential impact.
The assessment process begins by identifying all the assets that could be affected by cyber threats. These can include hardware, software, electronic data, and even team members and procedures.
Next, you’ll want to identify any threats to these assets. This involves identifying potential threat actors and the methods they could use to compromise your security.
Once you’ve identified threats, you need to analyse the vulnerabilities that these threats could exploit. This requires a thorough evaluation of your cyber security measures, procedures, and technologies. More on that in a bit.
The final step is to assess the potential impact of these threats. This involves considering possible damages to your business that could result in financial loss, reputational damage, and regulatory penalties.
Identifying Potential Vulnerabilities
Identifying possible vulnerabilities in your cyber security infrastructure involves a deep dive into your systems and processes. This includes evaluating hardware and software for weaknesses that a cybercriminal could exploit. It also involves assessing your team’s cyber security awareness and the procedures they follow.
A common method to identify vulnerabilities is to conduct penetration testing, where ethical hackers attempt to breach your systems and uncover weak points. Another technique is a vulnerability scan, which uses automated software to scrutinise your systems for known vulnerabilities.
Remember, the identification of vulnerabilities is not a one-and-done task. Cyber threats evolve rapidly, so regular assessments are needed to stay ahead.
By regularly reviewing your cyber security health, you can proactively manage risks, continuously improve your cyber security environment, and ensure the ongoing trust of your customers.
Key Components of an Australian Financial Services Cyber Security Strategy
In light of recent cyber attacks, the creation of a strong cyber security strategy should be a priority for all businesses in the financial sector.
A comprehensive plan should aim to protect against attacks, detect incidents quickly, and respond effectively, minimising disruption.
Here are some key components your organisation should include in its cyber security strategy.
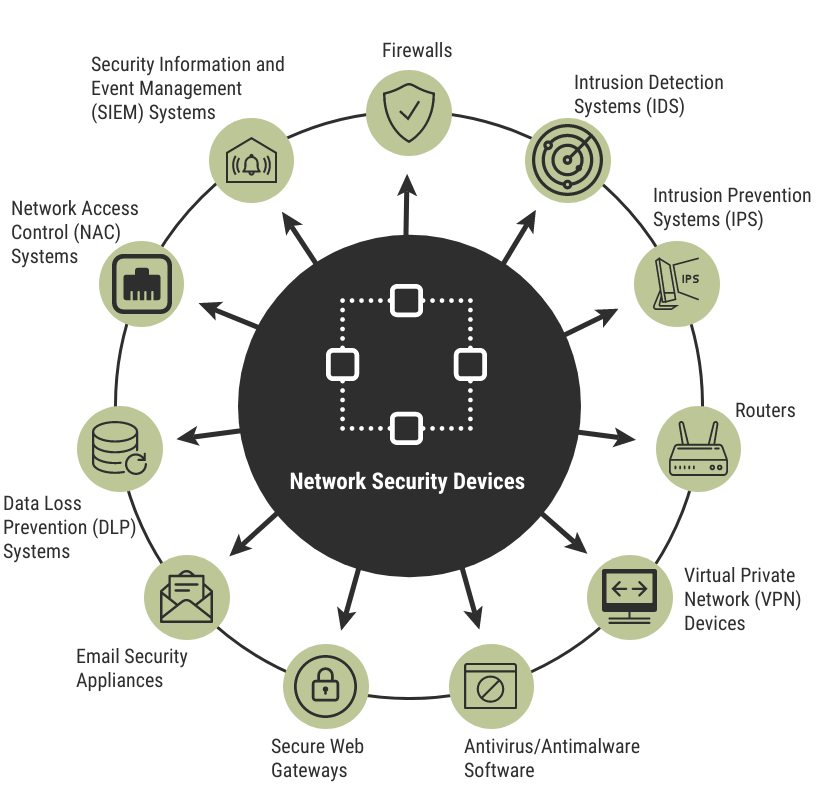
Network Security Measures
Network security is your first line of defence. Strong network security measures help protect your organisation’s interconnected systems from intrusion. These measures include:
- Firewalls to block unauthorised access.
- Intrusion detection systems (IDS) to monitor network traffic and identify suspicious activities.
- Network segmentation to isolate various parts of your network and limit the potential spread of a cyber attack.
Data Protection Strategies
Data protection strategies include encrypting sensitive data both at rest and in transit, using secure transactions to protect data from interception, and applying data loss prevention (DLP) techniques to prevent data leaks or unauthorised data transfers.
Access Controls and Authentication Processes
These processes are vital for ensuring that only authorised personnel have access to your data and systems. You can use techniques such as role-based access control (RBAC) to limit employee access to sensitive information based on their role.
Additionally, you can use multi-factor authentication (MFA) and biometric authentication methods to verify the identity of users and prevent unauthorised access.
Mobile and Remote Banking Security Measures
With the increase in mobile and remote banking, additional security measures are needed to protect these channels. Mobile device management (MDM) solutions can help secure employees’ devices, while virtual private networks (VPNs) can protect data transmitted during remote banking sessions.
Regular application updates and patching are also crucial to fix vulnerabilities in mobile banking apps.
Incident Response and Disaster Recovery Planning
Despite all precautions, cyber incidents can still occur. An incident response plan lays out the steps to take when an incident does occur. This enables a coordinated response to minimise the impact on your business.
Meanwhile, a disaster recovery plan details how your organisation will recover and restore critical functions in the aftermath of an incident.
A strong cyber security strategy incorporates all these elements and more based on the needs of your business.
The Importance of Employee Training
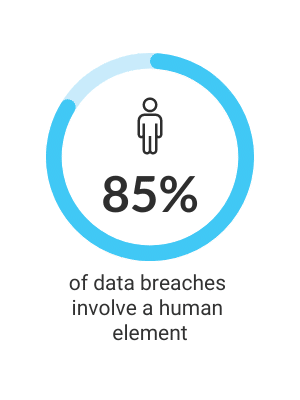
While tools and protocols are important, human error remains one of the most significant risks to cyber security.
Incidents like phishing scams, accidental data sharing, and unauthorised data access often occur due to a lack of understanding or awareness about cyber security risks. Refer to the Latitude and Levitas examples above.
Human Error – A Significant Risk in Financial Services
Human error can have severe consequences. Employees may accidentally click on a malicious link, use weak passwords, or fail to follow proper procedures when handling sensitive data.
These mistakes can provide an easy entry point for hackers, leading to data breaches or system compromises. Therefore, addressing human error is crucial.
Implementing Effective Cyber Security Training
Cyber security training should be a recurring event. Here are some key steps for implementing effective cyber security training:
1. Make It Regular
Conduct regular training sessions to keep employees updated on the latest cyber security threats and best practices. This could include recognising phishing attempts, using strong, unique passwords, and safely handling sensitive data.
2. Tailor Your Training
Different departments within your organisation may handle data differently and face unique risks. Tailor your training sessions to address these specific needs and scenarios.
3. Do Practical Exercises
Practical exercises can help reinforce training and help your team understand how to apply their knowledge to real-world situations. This could include simulated phishing attempts to test employees’ abilities to identify and report suspicious emails.
4. Encourage Reporting
You want to foster an environment where employees feel comfortable reporting potential security threats without worrying about getting in trouble. Quick reporting can often prevent minor incidents from escalating into major security breaches.
5. Continuous Learning and Improvement
Cyber threats constantly evolve, so you and your employees need to as well. Regularly review and update your training program to address new threats and incorporate lessons learned from previous incidents.
How We Can Help
Maintaining an in-house cyber security team can be a daunting task. This is where working with cyber security professionals can prove beneficial.
We offer a range of services designed to help organisations protect themselves from cyber threats. These include 24/7 monitoring and management of security devices and systems, intrusion detection, security audits, vulnerability assessments, and incident response.
By partnering with us, you gain access to a team of experts dedicated to protecting your organisation from cyber threats. We understand the latest technologies and threats and offer a level of expertise that is difficult to replicate in-house.
What You’ll Get With Us
We understand the unique needs and challenges of your organisation and the wider financial services sector. Work with Stanfield IT, and you’ll get:
-
- Expertise and Experience: We’ve got a proven track record in financial services and a deep understanding of the regulatory environment.
- Range of Services: We offer a wide range of services that can cover all aspects of you cyber security needs.
- Response Time: In the event of a cyber incident, every second counts. You can count on us to respond quickly.
- Communication and Reporting: We’ll give you regular, easy-to-understand updates on your security posture and any threats or incidents.
We can work with you to create a robust, customised cyber security strategy that fits your organisation’s needs. We always aim to create partnerships based on mutual trust and a shared commitment to protecting your business, customers, and the sensitive data you hold.
Conclusion
If your business operates in the financial services sector, robust cyber security is a non-negotiable.
However, despite the complexity, you’re not in this alone. At Stanfield IT, we’re here to help guide you through the challenges of cyber security; ensuring your data, reputation, and future are secure.
Don’t wait until a cyber attack happens. Be proactive and take the necessary steps today.
Contact us to learn more about how we can assist in fortifying your cyber security defences and making cyber security a core part of your business strategy. Your security is our priority.

Chat with Angus
Secure your financial institution and take control of your technological infrastructure with our industry-leading cyber security services and support. Reach out to us today to schedule a consultation and take the first stride towards reinforcing your security.
