Business are increasingly supplementing their operations with a network of third-party vendors.
There’s no doubt that this collaboration is vital for growth – many hands make light work. However, these partnerships often harbour vulnerabilities.
After all, a chain is only as strong as its weakest link.
And when ASIC reports that 44% of Australian organisations are not managing third-party risks, that’s a problem.

Let’s imagine a typical Australian enterprise, perhaps a start-up in Barangaroo, or a well-established firm in the heart of the CBD. Like many others, they lean on various third-party services – from cloud storage providers to customer relationship management systems. However, beneath this integration of services lies a web of digital interactions, each a potential gateway for cyber threats.
Recent incidents in Australia have illuminated these vulnerabilities, with businesses finding themselves grappling with the repercussions of cyberattacks originating from their third-party vendors.
It’s unlikely that these are isolated events but rather signs of a growing trend.
So, how can Australian businesses prevent similar issues? It’d be unrealistic to suggest that you retreat from third-party collaborations. Instead, the answer lies in minimising these cyber threats.
Understanding Third-Party Cyber Threats
What Are Third-Party Threats?
Third-party cyber threats emerge when external entities that your business collaborates with, such as vendors, suppliers, or service providers, become the weak link in the cyber security chain.
These entities often have access to a business’s internal networks or sensitive data. This makes them an attractive target for hackers.
The threats manifest in various forms, including data breaches, malware infections, or unauthorised access, all stemming from external parties.
These threats are particularly insidious because they exploit trust and access granted to third parties. For instance, a seemingly harmless software update from a vendor could introduce vulnerabilities, or hacked supplier’s systems could provide a backdoor into the more secure networks of other businesses.
This is why third-party threats can be so frustrating for businesses, it’s the action (or inaction) of others that’s put them under threat.
Recent Example of Third-Party Breaches in Australia
Latitude Financial Data Breach
The Latitude Financial data breach in 2023 is an example of third-party cyber risks.
In this incident, Latitude Financial’s security systems flagged unusual login activity from a service provider. This wasn’t an isolated incident but part of a broader pattern where the compromised credentials were used to access the systems of other linked service providers.
The breach’s impact was significant, involving the extraction of sensitive customer data. This data included personal details like driver’s licenses and Medicare information.
The way this breach unfolded highlights the complexities in managing cyber security risks involving third-party vendors.
The attack was indirect. Attackers didn’t infiltrate Latitude Financials’ systems; instead, they exploited the interconnected networks of its service providers. This method allowed them to bypass Latitude’s security measures and extract sensitive data without immediate detection.

Assessing Your Third-Party Cyber Risk
How To Evaluate Third-Party Vendors
To manage third-party cyber risks, you need to assess the cyber security posture of your vendors. This can involve several steps.
- Cyber Security Audits & Assessments: Begin with a comprehensive cyber audit of the third-party vendor. This should include reviewing their security policies, incident response plans, compliance with relevant regulations, and cyber security frameworks they adhere to.
- Security Certifications and Standards: Check if the vendor holds any cyber security certifications (like ISO 270001, SOC 2) which are indicators of their commitment to security.
- Review of Past Security Incidents: Inquire about any past cyber incidents and how they were managed. This will give you insight into their incident response capability and resilience.
- Security Practices & Protocols: Evaluate their security practices, including network security, data encryption, access controls, and employee training programs.
- Regular Updates & Patch Management: Ensure they have a robust system for regular software updates and patch management to guard against known vulnerabilities.
- Third-Party Penetration Testing: Consider requesting or reviewing the results of penetration tests conducted on the vendor’s systems to understand their vulnerabilities.
Why Are Due Diligence and Regular Assessments Important?
Due diligence is fundamental in third-party vendor relationships:
- Initial Vetting Process: Conduct thorough due diligence before onboarding a new vendor to ensure they meet your cyber security requirements. This includes reviewing their security policies, incident history, compliance records, and security infrastructure.
- Continuous Monitoring: Cyber security is dynamic; hence, continuously monitor the security posture of your vendors. This could involve regular security reports, updates on compliance status, and revisiting security audits.
- Contractual Agreements: Ensure that cyber security expectations, requirements, and responsibilities are communicated in contractual agreements with third-party vendors. This includes clauses on data handling, breach notification, and regular security audits.
- Risk Management Integration: Stay updated with compliance requirements, especially for industries that are heavily regulated. Ensure your vendors adhere to those regulations to avoid legal and financial repercussions.
- Incident Response Planning: Include third-party risks in your incident response planning. Ensure there’s a clear plan on how to respond and recover from security incidents that involve third parties.
Implementing Effective Risk Management Strategies
Develop a Risk Management Framework
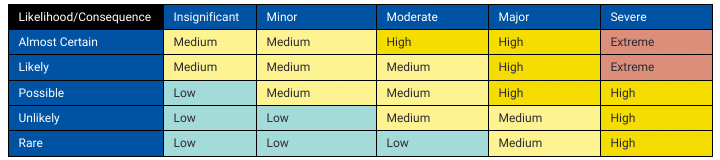
If you want a strategic approach to managing third-party cyber risks, you need to establish a framework. This framework should continuously evaluate and categorise third-party risks throughout the vendor relationship lifecycle.
It involves identifying potential risks, assessing their impact, and prioritising them based on their severity and likelihood.
Incorporating a risk matrix or scoring system can help quantify these risks, making them easier to manage and monitor.
Integrate Cyber Security Into Business Operations
Ensure cyber security is a consideration in your business processes.
This means that cyber security assessments become a standard part of vendor selection and contract renewal.
Regular reviews and updates of these processes are essential to align them with evolving cyber security landscapes and business needs.
Contractual Safeguards
Include detailed cyber security clauses in all contracts with third-party vendors.
These should cover incident response expectations, data handling guidelines, and requirements for regular security updates.
Clearly define penalties for non-compliance and ensure these align with legal standards.
Regular Vendor Engagement & Collaboration
Maintain open communication channels with vendors to share cyber security insights, threat intelligence, and best practices. Joint cyber security exercises and workshops can enhance mutual understanding and preparedness against potential threats.
Technological Solutions and Tools for Third-Party Risk Management
Now that you know why you need to manage third-party risk, let’s take a look at some of the tools you can use to help you do so.
Security Information and Event Management (SIEM) Systems
- SIEM systems are vital for real-time monitoring and analysis of security alerts across your network, including those involving third-party interactions.
- They aggregate and analyse data from various sources, helping to detect unusual activities or potential security threats quickly.
- This system effectively identifies patterns that might indicate a breach or an attempted attack.
Vendor Risk Management (VRM) Software
- VRM tools are designed to assess, monitor and manage the cyber security risks associated with third-party vendors.
- These platforms automate the evaluation of vendors’ security postures and ensure their compliance with your security standards.
- They can streamline the process of conducting due diligence, performing regular assessments, and keeping track of the security status of multiple vendors.
Cloud Access Security Brokers (CASBs)
- CASBs are essential for businesses utilising cloud services. They provide a layer of security between cloud service users and cloud service providers.
- These tools are crucial in monitoring and controlling third-party access to cloud environments, ensuring that sensitive data stored in the cloud is secure.
- CASBs can enforce security policies, prevent data breaches, and provide insights into abnormal activities within cloud services.
Network Monitoring Tools
- Network monitoring tools play a key role in tracking the traffic to and from third-party networks.
- They are instrumental in detecting network anomalies, unauthorised access attempts, and potential data breaches.
- These tools enhance visibility into the network and are essential in maintaining the integrity and security of business-critical systems.
By integrating these technologies into your cyber security strategy, you can better manage the risks associated with third-party vendors.
Future Trends in Third-Party Cyber Security
As Australian businesses look ahead to emerging trends in third-party cyber security, two key areas stand out as particularly influential.
Regulatory Compliance
The first is the heightened focus on regulatory compliance. Regulatory requirements governing data protection will continue to evolve. And businesses are finding that compliance with these regulations is becoming integral to their cyber security strategies.
This includes ensuring that third-party vendors align with standards set by the Australian Privacy Principles and the Notifiable Data Breaches scheme.
The approach to compliance is shifting from a reactive to a proactive approach, where continuous monitoring and regular updates are essential to ensure that both the business and its third-party vendors remain compliant.
Supply Chain Security
Simultaneously, there is an increasing emphasis on supply chain security. Recent cyber incidents have brought to light the vulnerabilities within supply chains, particularly those involving multiple third parties.
Businesses are now recognising the need for comprehensive due diligence and ongoing monitoring of all supply chain partners. This trend suggests a move to creating more robust and collaborative security measures that extend beyond the immediate operations of the business.
The future strategies in this area are likely to focus on in-depth assessments of third-party vendors and the establishment of joint security protocols.
Conclusion
As Australian businesses increasingly utilise third-party vendors for growth, the challenge of managing cyber security risks in these partnerships becomes crucial.
Moving forward, the focus must be on vendor assessments, embracing technological tools for monitoring, and staying aligned with evolving cyber security trends and regulations.
This strategic approach is essential for businesses to effectively safeguard their operations, building a secure and trustworthy environment that not only mitigates risks but also supports sustainable business growth.
