Keeping a company’s IT in working order requires reviewing it periodically. An audit of all current and planned practices keeps managers informed of all relevant business IT considerations when asking outside companies for quotes on management, support, and consultation. Asking informed questions allow companies to give answers on technology considerations that will be useful to the business.
With technology now playing a major role in the set-up and daily running of businesses, it’s important to keep abreast of fast-paced technological changes and what technologies are right for your business. Knowing how technology can grow and shape your small-to-medium business ― no matter what industry you’re in ― will have huge benefits on employee productivity, exposure to new clients and customers, and information security.
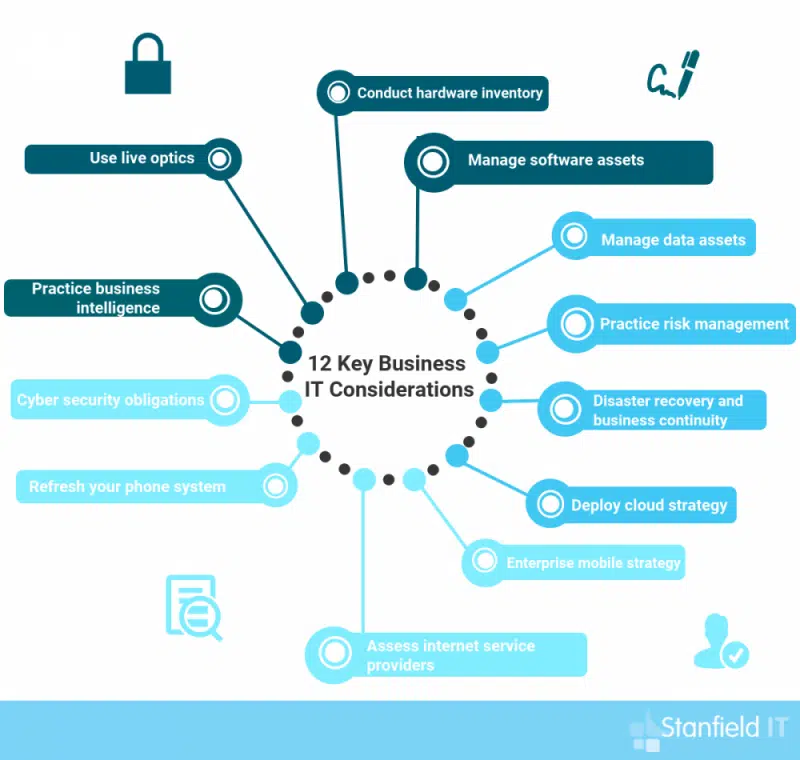
Your technology review needs to cover several key business IT considerations, with attention being paid to their current status and changing requirements. Here are the 12 key business IT considerations for your next technology review:
12 Key Business IT Considerations
1. Conduct hardware inventory
It’s necessary to replace or upgrade all hardware over time. Desktop machines, servers, printers, and networking devices have a limited useful life. An audit should determine what existing hardware needs upgrading and what new equipment will be needed. If the budget is limited, you need to prioritise hardware requirements as a part of your technology review.
If you’re moving offices or your office is undergoing an expansion, it may be the perfect time to upgrade your technology. This could save you time and money, as new systems can be installed during the relocation or upgrade, which will save time and effort doing them later.
For proper hardware inventory, a strategic approach should be taken ― always upgrade the most important hardware first and work down from there. Remember that updating your hardware is not a luxury reserved for bigger businesses. It’s a crucial part of successfully running a business of any size, with successfully security, productivity, and information management intrinsically linked to proper hardware inventory.

2. Manage software assets
Software also needs upgrading at regular intervals. Out-of-date software can have dangerous security holes. Existing licenses may include upgrades, or it may be necessary to buy them separately. The number of licenses may have to increase if the workforce is growing.
If existing software is no longer satisfactory, or if there are new kinds of work to do, new software will be necessary and should be included in your business IT considerations. Free, open-source software may serve the purpose just as well as commercial software, but it will still require support. The budget needs to cover whatever is needed to keep productivity high.
Upgrading to cloud services, productivity apps, and online accounting tools are a few things that you should consider implementing into business strategy. Apps and online services are now readily accessible and optimised for a variety of devices. This means that employees can have work-from-home opportunities or ultilise BYOD in the office.
3. Manage data assets
Data storage requirements can grow, and data may need to be managed in new ways. Storage systems need to keep up with growth, and backups need to keep it all safe. Migrating data storage to a cloud service may be more cost-effective than expanding on-premises storage, provided contractual and regulatory requirements allow it.
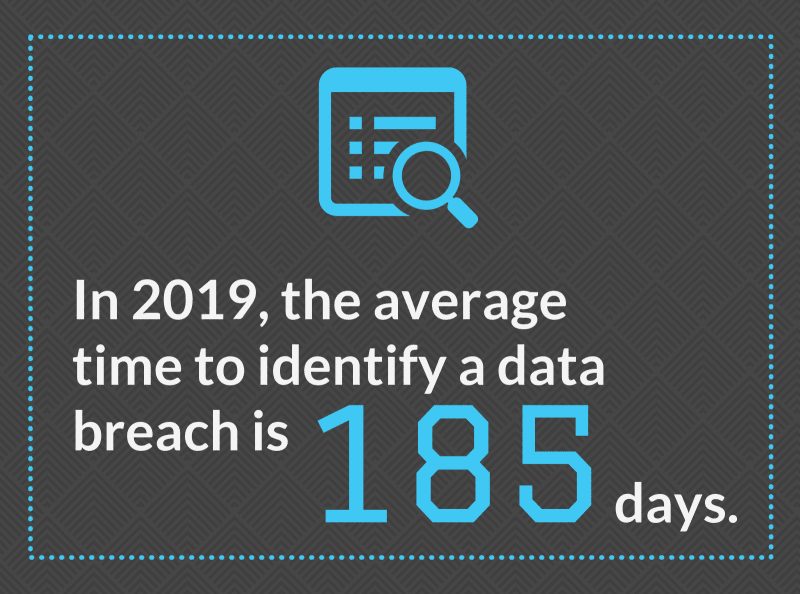
Securing business data assets means backing up regularly. These backups should be stored separate from the main server, so that they won’t be compromised in the case of a data breach. You can’t underestimate the value of your data ― no matter what size your business is, confidential business and client information is valuable to hackers. Ensuring data is as secure as possible is a key part of business IT considerations that every business owner must address.
Due to how valuable data assets are, correctly identifying and classifying your assets is a key step in your technology review. This means having a system for data inventory, where the business has a catalogue of the data that they own. Employee approvals should also be routinely managed, so that the right approvals sit with the right people.
4. Practice risk management
Security and risk management are a huge and rapidly growing concern. Ransomware and data theft can inflict serious harm on a business. Last year’s security measures won’t be adequate.
Risk assessment and protection need to operate both at the level of individual systems and the network as a whole. The weakest device can compromise the entire network. As already mentioned, keeping software updated and data backed up are important parts of the security strategy.
A risk audit needs to identify the most serious weaknesses in the network and determine what mitigation is necessary. It should assess the benefits of possible safety improvements, such as network monitoring.
Access control can greatly improve security. If systems don’t have unnecessary access privileges, they can’t do as much damage if they’re breached. If past policy has been to assume that everything inside the network can be trusted, the policy seriously needs revision during your technology review.
5. Establish disaster recovery and business continuity
Events such as floods and fires can destroy a business’s on-premises IT systems. Without a recovery plan, they’re likely to destroy the business itself. A disaster recovery plan is a necessary part of business IT considerations to survive such eventualities.
This plan requires more than just backup. It needs to consider how much downtime is acceptable, and whether it will be possible to get systems running again in that time frame. A cloud-based failover can greatly reduce the worst-case downtime scenario.
Your business’s disaster recovery plan also needs to include business’s data security. There should be a data breach response plan in place where team members know their role and the steps to take if a breach occurs. This ensures a breach will have minimal effects on the business, and panic will not ensue.
Having a disaster recovery and business continuity plan that covers physical and technological threats to business data has benefits that go beyond data security. This documentation can be made available to said stakeholders or clients upon request, ensuring they will trust in the business as much as possible.
6. Deploy cloud strategy
Cloud issues have already come up in the previous points, but a cloud strategy needs to be an item of its own in the review of business IT considerations. Many businesses are moving large parts of their IT operations to cloud services. That approach eases the need for hardware, makes it easy to increase users or usage, and requires less ongoing management.
Cloud services vary in their reliability, security, and support. It’s important to select a trustworthy provider and make sure that information will be at least as secure as it was on the premises. Knowing how to choose the right deployment model for your business can be tricky ― the easiest way of understanding cloud deployment is that it entails determining “where your data and systems will live.”
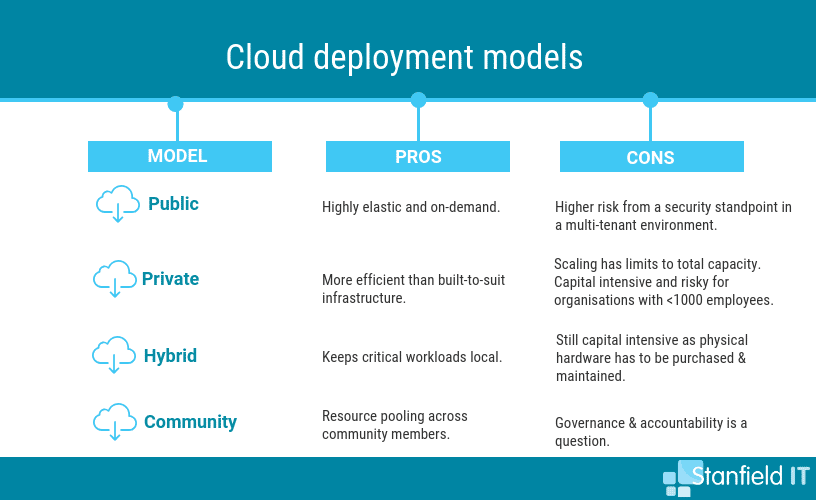
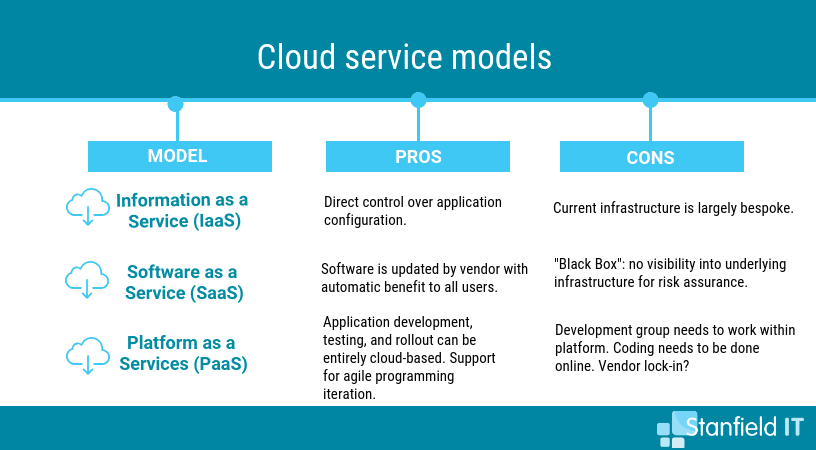
As well as choosing the right cloud deployment model, you need to consider the correct type of cloud service ― think of this as how you want your cloud deployment to be managed. To help you get your head around cloud deployment and service models, Stanfield IT can assess your business structure and goals and then tailor and execute an appropriate cloud strategy.
7. Enterprise mobile strategy
Mobile strategy incorporates mobile devices into your business’s overarching corporate strategy. It’s easy to forget about phones and tablets as part of the IT infrastructure, but they play a growing part in most businesses. Before you implement a mobile strategy, you should look at your business as a whole and establish what your company objectives are.
Your business’s mobile strategy will require its own software strategy and risk assessment. You’ll also need to consider what your desired outcomes are for introducing mobile apps for team use in your business. With these things done correctly, there’s a huge opportunity to leverage mobile technologies to increase employee productivity.
Many companies wrestle with whether to allow a BYOD policy and what restrictions to place on user-owned devices. Neglecting this area can seriously compromise network security. Think about how mobile initiatives can assist your business in mapping and attaining corporate objectives.
8. Assess internet service providers
For teams and individuals to work effectively together in and out of the office they need to be connected. If you’re finding that your service is lacking, you should shop around and consider the benefits of changing to a provider the meets your business’s needs. The team at Stanfield IT can help with this, assessing your business strategy, internet use, and if you’re getting the best service possible for the least investment.
If you do choose to pick a provider on your own, ensure that they offer the required bandwidth so that your employee’s can be efficient with their work without you taking on unnecessary costs.
Remember that the most important factor is service reliability. This includes both how reliable the internet service itself is and how responsive the providers are when issues arrive and they’re contacted.
9. Refresh your phone system
If you’re expanding your office or moving to an entirely new location, it could be the perfect time to look at upgrading your phone system to suit the demands of your business expansion. Voice over IP (VoIP) providers now offer continuous communication services and cloud-based phone service for a level of flexibility that’s unachievable from a standard phone system.
Even if you aren’t moving locations or dramatically expanding your business, you phone system may need an overhaul. If you have instances where your phone goes down, you’d know how this can stump productivity and make your business appear unreliable, so you’re probably more likely to change providers. However, even if your phone seems fine, there are a few things that you should be demanding from business phone services.
These include mobility (a phone system that can travel with you); better call quality (if you’re using a pure IP system you may need to speak to your IT provider if you’re experiencing poor call quality); and automatic routing (smart technology that can negotiate a basic set of timing instructions that can route your calls properly).
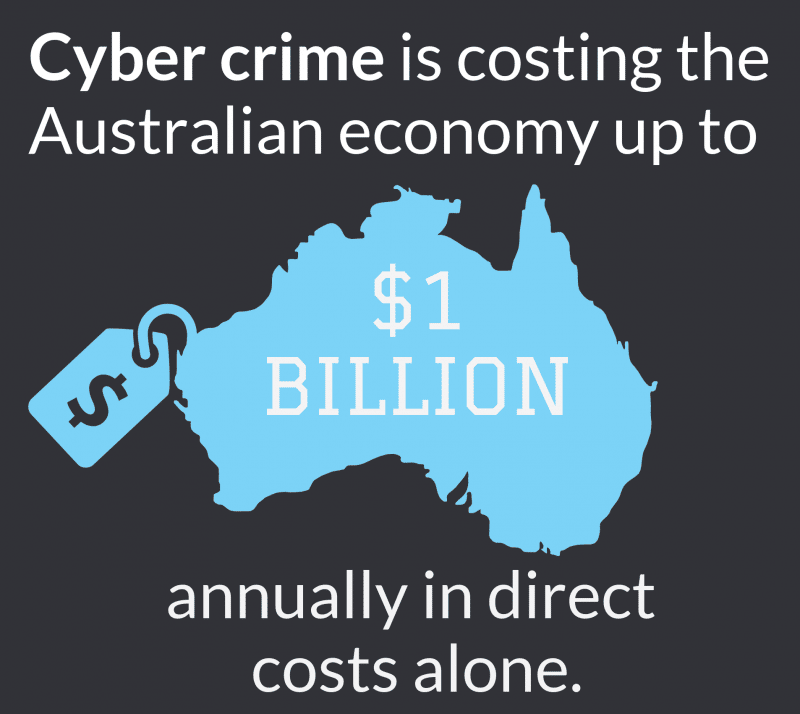
10. Cyber security obligations
Realise your cyber security obligations as a business owner and embrace holistic, end-to-end, rules-based solutions. Hiring IT professionals to do a technology review and investigate the best cyber security options for your business is a great way to handle information security.
To make sure your data is secure, your team also needs to be trained and fully across what they should do in the case of an attack. They also need to understand the preventative measures that need to be taken in order to prevent an attack in the first place. Up-to-date education and training around cyber security should be made the norm in your workplace, so that every employee can see how they play a part in keeping company data safe.
11. Practice business intelligence
Historically, business intelligence (BI) was reserved for larger companies. Today, though, software as a service (SaaS) has pushed smaller businesses to use BI tools, too. This means that successful small-to-medium businesses are tracking, storing, processing, and analysing data. The result is more informed decision making when assessing what expenses to cut, where the best growth opportunities lie, and how overall performance can be improved. This is made even easier and cost-effective with platforms like Microsoft SharePoint.
Smarter decision making is also means engaging with the key stake holders in the business, finding out where the business is going, what changes are coming, what needs to be provided to support that. Keeping up to date on what new technology is coming to a head and what other businesses in your industry are doing means you won’t fall behind. You should conduct vendor, partnership, and relationship reviews so that you can be confident that you’re liasing with people you can trust and who will carry you forward with technology.
12. Use live optics
Live Optics is a fantastic business asset for analysing your network and hardware at all times, not just during your technology review. It’s used to collect, visualise, and share data concerning your business’s IT environment and individuals’ and teams’ workloads. Dell EMC Live Optics™ is fantastic free software that is industry standard.
With Live Optics, you can impartially document server and storage configuration and performance, plus observe data file characteristics. You should see your company’s performance as a fingerprint ― unique to all others. That’s why it’s so important to safely analyse, record, and communicate this performance to grasp the workings of your business.
The types of optics you can gather information on include:
- Virtualisation & Host Optics ― platform for IT professionals to record and communicate their achieved benchmarks, current workloads, or support concerns with employers and employees to promote quick decisions with less risk.
- File Optics ― allows rapid characterisation of unstructured data and offers visual insights into data growth drivers in your organisation.
- SAN Optics ― can be used to conduct storage area network health assessments.
- Storage Optics ― vendor-specific hardware profiling for storage arrays or data protection software/hardware. This includes both configuration and in-depth performance insight.
Reviewing all Business IT considerations
A detailed review of all of these areas will provide a good basis for future IT plans. Neglecting any of them can leave a business operating with inadequate hardware and software or expose it to a serious breach. It takes some time to conduct a proper review, but it’s time worth spending. Contact us at Stanfield IT to learn how we can help you to cover all your IT issues.
