What is Network Security?
Network security is the practice of protecting your network and its integrity from potential threats. Utilising both hardware and software solutions to manage access to the network, your business’s network security should identify threats and prevent them from accessing the system. As a result, network security doesn’t focus on managing specific devices, but rather on how those devices communicate and interact with each other.
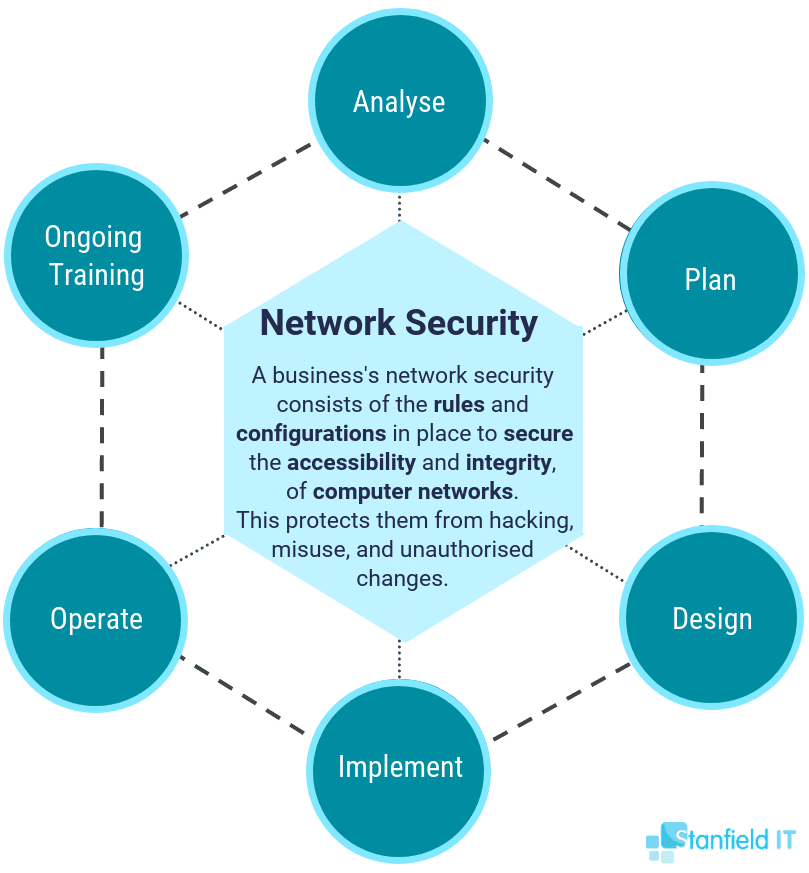
No matter how small your business is, it’s important to identify/implement the following in your small-to-medium business’s network security so that measures can be properly implemented:
Network Security Threats
Network security threats can come from both inside your business (an employee using their access to compromise the business) and outside your business (a hacker with the intent of stealing your data). These threats can also present as a result of inadequate protections being put in place, as well as human error or negligence (such as opening an unknown email and clicking on an attachment which then downloads malware to the computer).

Network Security Goals
Based on the type, size, and intricacies of your business, the particulars of your network security goals will differ from other small-to-medium businesses, even within the same industry. Make it an aim to define and list your network security goals, with attention being paid to what areas need to be better secured, and with considerations being made to any past breaches. For example, a company that had their network breached may want to increase employee password security, set up mobile device management so that compromised devices can’t join the network, and separate the main and guest network servers.
Network Security Plan
You can now come up with a network security plan that will address what was highlighted within the network security goals you set out for your company. This should include indicating specific roles any employees will play during the rollout of these procedures (e.g. HR, team leaders, and IT) and if the changes will be made in-house or will be outsourced to an external IT team.
Network Security Policy
You should now have the knowledge and frameworks in place to begin creating a network security policy for your business. This needs to outline rules for computer network access, determine how rules and regulations are enforced, and lay out the ins and outs of the basic company security procedures and network security environment.
If you feel a bit overwhelmed with completing these processes, let Stanfield IT do the heavy lifting for you, so you don’t need to life a finger when it comes to network security!
Why Is Network Security Important?
Without effective network security, you essentially have your data there for the taking. Cyber crime is on the rise, and cyber threats are getting smarter and sneakier. Even with the most basic network security, you can effectively deter a huge host of malware, viruses, and hacking attempts. Overall, network security is critical to preventing data breaches, which can take a huge toll on your business’s credibility and finances.
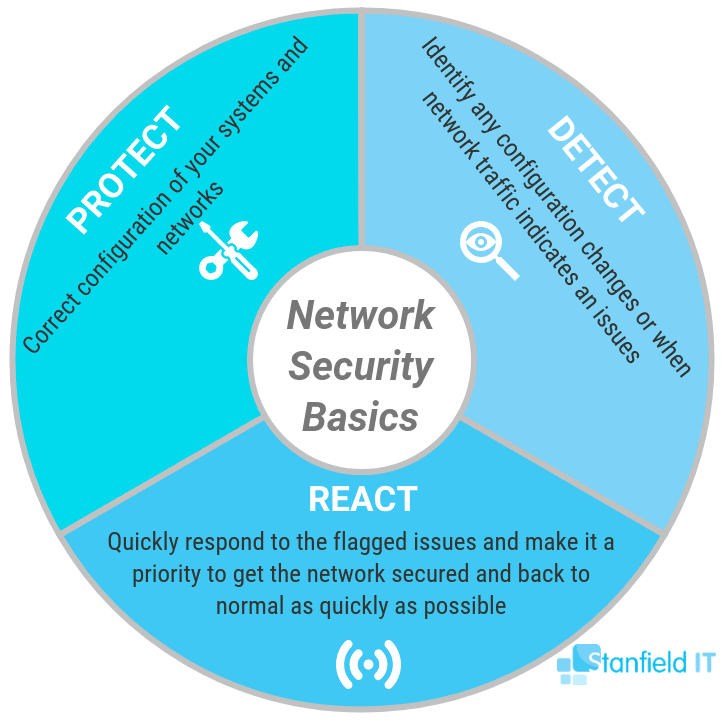
Let’s have a look at the different elements involved with network security:
1. Access Control
Allowing all users full access across the entire work network is a mistake many new businesses make. Restricting and managing network access is an essential part of network security. Remember that each user only needs access to the apps, folders, and files that they directly use to do their job.
Identify users and devices, making sure that every new user and device goes through the correct policies and procedures so that they ― and their device/s ― are recognised. Security policies should be created that cover the different types of devices that access your network. As a result, you get to enforce who has approved access and block unidentified users or devices from having unrestricted, or any, network access. You’ll often hear this process being referred to as network access control (NAC).
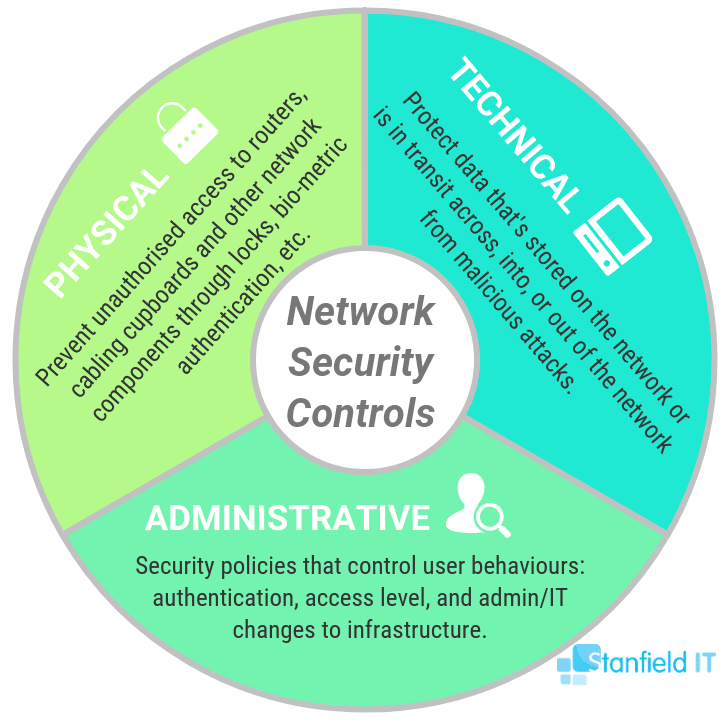
The different network security controls are as follows, with access control falling under administrative controls:
2. User Identity Management
Identity management, put simply, is the operation of controlling information about users on a computer. This includes what information authenticates the identity of the user and the information that indicates the resources and actions they have permission to access.
Define and manage user roles and their access privileges to network and sensitive data. This applies to both customer and employee identities. With one digital identity per user, you can easily manage and monitor each individual and their activity. As mentioned briefly above, users within a business often accumulate more access privileges than they need to do their job. The more access users have, the more likely a data breach is to occur.
3. Anti-Malware
Anti-malware software is another essential must-have for any business’s network security. Antivirus and anti-malware should be a part of your network security to detect and contain any viruses, worms, ransomware, spyware, or trojan horses attempting to hit your system. Deep visibility into network-level threats are indicators of great anti-malware protection.
A decent malware detection program will not just detect incoming malware, but will continually monitor and track files for anomalies. This is crucial, as you can’t rely on protection alone ― human error needs to be taken into consideration, too.
With the integration of AI and machine learning, modern anti-malware tools have become more adept at predicting and responding to new and evolving threats. These advanced technologies enable proactive and adaptive security measures, offering enhanced protection against sophisticated malware attacks that traditional methods may not detect. Implementing anti-malware solutions equipped with AI capabilities ensures a more dynamic and robust defence against a wide range of cyber threats.
4. Application Security
Application security is a broad umbrella that covers hardware, software, and processes that you choose to apply for optimal security measures. Having insecure applications is a major reason that businesses get targeted by hackers ― it can be easy to infiltrate data via an insecure app that isn’t backed by the business’s network security.
It’s crucial to take care to protect all applications and software that you use within your business. This applies to internally built programs as well as bought ones. All applications are suspect to vulnerabilities that attackers frequently exploit for unauthorised access.
In recent years, the concept of DevSecOps has gained prominence, emphasising the integration of security practices into the software development lifecycle. This approach involves embedding security measures from the initial design phase through development, testing, deployment, and maintenance, ensuring that security is a continuous, integral part of the process rather than an afterthought. Adopting a DevSecOps framework can significantly reduce the risks associated with insecure applications, enabling a more resilient and secure operational environment.
5. Hardware Security
Hardware security is another component that works to complement software security and is not to be overlooked when put beside its technological counterparts. In contrast to anti-virus applications, hardware security describes the physical hardware devices that provide vulnerability protection. Devices that provide an additional element of protection to your network include hardware firewalls and hardware security modules.
A hardware security module is a physical computing device for safeguarding computer hardware. It also provides crypto processing (via one or more crypto processor chips) and manages digital keys. This means strong authentication. Traditionally, modules come in the form of a plug-in card or external device in which you directly attach to a computer or network server.
6. AI-Based Threat Protection
Many threat detection tools now use artificial intelligence to increase their effectiveness. These AI tools have the power to predict external threats in advance and discover breaches as they occur. They also have the ability to respond to ransomware or malware attacks. These predictive and automated responses certainly have a great impact on network security.
Artificial intelligence (AI) is leading the wave of digital transformation today. Both large and small companies are actively growing their AI footprints. Higher ups are consistently comprehending more fully what AI is and how they can use it to their advantage within their business. Businesses are using AI to gain insights into the data they collect, enabling them to engage with customers and stand out from competitors.
The evolution of AI in threat detection has now embraced machine learning algorithms that can analyse patterns and learn from them, offering even more sophisticated protection. This includes identifying anomalies in network behaviour that might elude traditional security measures. The integration of machine learning enables AI systems to adapt and improve over time, enhancing their ability to detect new and evolving threats. Additionally, AI-driven threat intelligence platforms are increasingly being used to collate and analyse threat data from various sources globally, providing real-time insights and enabling more proactive cyber security measures.
7. Email Security
Email portals represent a significant risk of breaches, standing as the number one way a business’s data is jeopardised. Many attackers target emails for phishing attempts and malware links. They compile personal information to present convincing emails that deceive recipients.
Email security, often via an email security application, is crucial for blocking incoming attacks and managing outgoing messages. The sophistication of phishing attacks has increased, with tactics such as Business Email Compromise (BEC) becoming more prevalent. These attacks often involve impersonating executives or trusted partners to request sensitive information or financial transactions
Employee training is also critical here, as a computer cannot be infected if the recipient of a virus doesn’t open the compromised link or pop-up. Regular training and awareness programs are essential to keep employees informed about the latest phishing techniques and best practices for identifying and reporting suspicious emails. This human layer of security complements technical measures, forming a comprehensive defence against email-based threats.
8. Network Security Firewalls
Firewalls are a critical part of network security for any organisation. They provide a hard barrier between your internal trusted network, and untrustworthy external networks, like the Internet. You define the rules that determine what traffic is allowed and what will be blocked by the firewall.
A standard security tool for the majority of companies, you probably have traditional firewalls in place in your business. In today’s forever-shifting threat landscape, however, next-generation firewalls (NGFWs) need to be considered for proper protection. NGFWs are a major step forward as they offer ‘Deep-packet inspection’ that goes beyond port/protocol inspection and blocking. They add application-level inspection, intrusion prevention, and bring intelligence from outside the firewall.
These advanced firewalls are capable of detailed inspection of the contents of your traffic, enabling them to detect and block sophisticated cyber threats. They also integrate seamlessly with other security systems, providing a more holistic and adaptive approach to network security. Features like application awareness and control, advanced threat protection, and automated responses to identified threats, are part of what makes NGFWs essential in a modern cyber security strategy. Their ability to provide real-time, context-aware security makes them a vital component in defending against the increasingly complex and targeted cyber attacks we see today.
9. Intrusion Detection and Prevention
Intrusion detection software monitors your network for suspicious or malicious activity by scanning network traffic. The software flags this activity, usually sending the results directly to an admin or admins. It might also be collected within a security information and event management (SIEM) system.
An intrusion prevention system (IPS) blocks any incoming attacks before they can be executed. They often use AI to anticipate and identify threat patterns. An IPS continuously monitors your network, looking for potentially malicious activity and capturing information about these incidences.
10. Mobile Device Security
Don’t forget to include mobile devices and apps, which cybercriminals are increasingly targeting, when considering network security. There are a plethora of mobile device management and mobile application management programs available now. You can even use the built in mobile device management for Office 365. With these you can manage devices and keep them secure.
Every year, more and more businesses are supporting corporate applications on personal mobile devices. Of course, the devices that have network access needs to be controlled and monitored. Connections also need to be configured in order for network traffic to remain private. Mobile device management or mobile application management systems and procedures need to be implemented.
11. Wireless Security
Wireless network security needs to be more strict and specialised than that of wired networks. This is due to the fact that wireless networks are less secure by nature. Without strong, effective security measures, installing a wireless LAN can be like putting ethernet ports everywhere for people to access your network without even knowing who they are.
To prevent your network from being exploited, you need to take advantage of specialised products that protect wireless networks and measures that can be taken to ensure you aren’t at risk of attack. This includes strong encryption, secure WPA passwords (different for the guest network, if applicable), checking for rogue WIFI access points, hiding the network name, using firewalls, enabling MAC authentication, and using a VPN.
12. Cloud Security
With more services taking place within the Cloud, it’s crucial to use cloud security. This is not the same as security solutions delivered by cloud. It refers to protecting the cloud itself in order to safely run applications, process transactions and store data.
High-profile hacking cases in the past few years have made business owners nervous about storing their data in the Cloud. In nearly every case, however, it’s the way that the Cloud is being used that causes issues, not the Cloud itself.
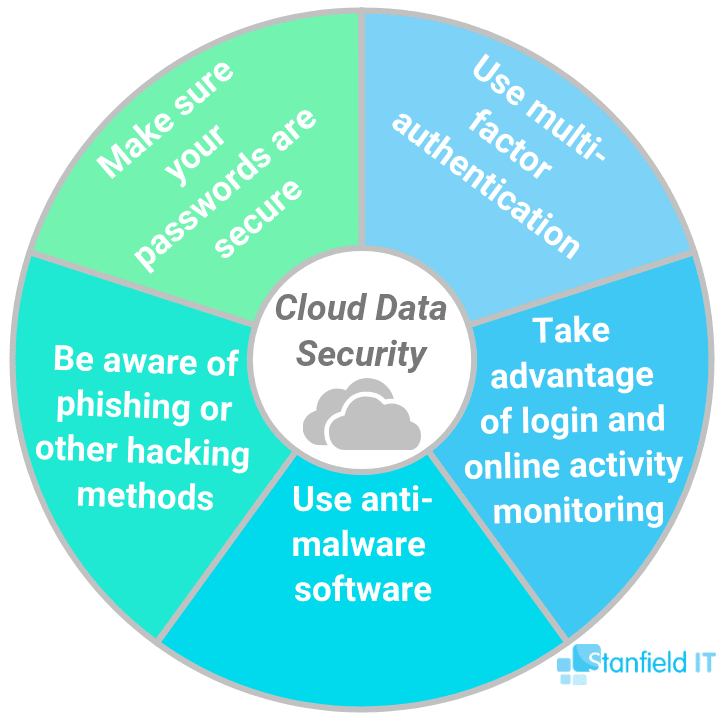
Here are five key ways to secure your cloud data:
13. Virtual Private Networks (VPNs)
A VPN encrypts the connection from an endpoint to a network. Most often, this occurs over the Internet. Usually, a remote-access VPN uses IPsec or Secure Sockets Layer to authenticate device and network communications.
VPNs are a pretty well-established network security tool at this point. Your online activity is easily visible to anyone when it’s not protected. Enter the VPN. It works by encrypting your data and routing your connection through a private server. Consequently, your activity and your privacy is protected online.
14. Network Segmentation
It’s easy to see how your network security is difficult to manage when everything is jumbled up together. Network segmentation divvies up your network traffic into different classifications. This makes it much easier to enforce different security policies based on endpoint identity.
These classifications should be based on endpoint identity, as opposed to IP addresses. Access rights can be assigned based on role, location, and more. This ensures that correct access at the right level is assigned to the correct people and suspicious devices are flagged and contained so that the compromising situation is remedied.
15. SIEM software
Security information and event management (SIEM) is a software solution that aggregates and analyses activity from many different resources across your entire IT infrastructure. SIEM collects security data from network devices, servers, domain controllers, and more.
SIEM products pull together the information that your IT team needs to identify and respond to threats. These products come in various forms, including physical and virtual appliances and server software.
16. Behavioural analytics
Behaviour analytics in cybersecurity is roughly defined as using software tools to detect patterns of data transmissions in a network that are out of the norm. The theory is that the analytics tool would detect the anomaly and alert IT managers, who would stop the unusual behaviour or cyberattacks.
Enterprises use behaviour analytics to detect intrusions that evade preventive technologies such as firewalls, intrusion-prevention systems, and antivirus software. Those conventional tools match fingerprints or signatures identified in prior attacks, while behaviour analytics tools study and report anomalies that are judged against a baseline of normal behaviour.
17. Data Loss Prevention (DLP)
Data loss prevention (DLP) is a strategy used by businesses in their network security policy to ensure that users don’t send sensitive information outside the corporate network. DLP is also used to refer to software products that help a network administrator control what data end users can transfer, replicate, etc.
Humans will always be a business’s weakest security link. Technologies and processes to ensure that employees don’t deliberately or inadvertently send sensitive data outside the network need to be enforced.
18. Web security
Implement a web security solution to control employee’s web use, block web-based threats, and deny access to malicious websites. This will protect your web gateway on site or in the Cloud. Web security is also used to refer to the measures you take to protect your business’s website.
Your website or web application’s security is heavily influenced by its level of protection tools. Some of the major vulnerabilities for web-based services ― the most common ways in which a website or web application becomes hacked ― are SQL injection, password breach, cross-site scripting, data breach, remote file inclusion, and code injection.
19. DDoS attack security measures
A distributed denial-of-service (DDoS) attack is where multiple compromised computer systems attack a target, resulting in the denial of service for its users. The target could be a server, website, or other network resource. Make sure that you keep programs and software up to date. This will ensure that any bugs or issues are flagged and fixed as they arise.
Conduct careful planning and enforce security measures in order to prevent a DDoS attack. The first thing to note is DDoS attacks can happen to anyone ― thinking it won’t happen to your small or relatively unknown business will just work against you and make your business more vulnerable. There are several measures that you can use to protect your business from a DDoS attack, which include: having a plan, allocating roles, and installing protection tools like firewalls, network monitoring software, anti-virus and anti-malware programs, as well as threat monitoring systems.
20. Endpoint Security
In network security, endpoint security is the protection of the business network when it’s accessed via remote devices. Such devices include laptops, mobiles, and iPad’s. Every time a new device connects to the network, a potential entry point for security threats is established.
In the days of BYOD in the workplace, as well as employees trying to use public networks to access work files (like in the library or airport), it has never been more crucial to think about how endpoint security plays a part in your overall network security strategy.
21. Zero Trust Architecture
Zero Trust is a security strategy cantered on the belief that organisation’s should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems, before granting access.
This approach is increasingly relevant given today’s cyber threats and the shift toward remote working.
Implementing Zero Trust involves a shift in network security philosophy. Traditionally, network security has focused on strong perimeter defence to keep threats out. However, once inside the network, users and devices often had considerable access. Zero Trust eliminates this implicit trust, requiring continuous verification of each user and device, whether they are inside or outside of the network perimeter.
Key components of zero trust architecture include:
- Strict User Authentication: Verifying the identity of all users before granting access to network resources.
- Micro segmentation: Breaking up security perimeters into small zones to maintain separate access for separate parts of the network.
- Least Privilege Access: Limiting user access rights to only what is strictly necessary for their role.
- Multi-Factor Authentication (MFA): Requiring multiple methods of verification.
- Regular Monitoring and Validation: Continuously monitoring network activity and validating security configurations.
Adopting Zero Trust can be complex, involving significant changes in network architecture and policy. However, its benefits in reducing the risk of data breaches and cyberattacks make it a compelling approach for modern network security.
22. Cyber Security Insurance
Cyber security insurance is a product that businesses can use to protect themselves from the financial risks associated with digital threats and data breaches. These days, it’s an essential consideration for businesses of all sizes.
Cyber security insurance policies typically cover a range of incident types, including data breaches, network damage, and business interruption caused by cyberattacks. This can help lower the financial impact of incidents such as ransomware attacks, data theft, and other forms of cybercrime.
Key aspects of cyber insurance include:
- Risk Assessment: Many insurers provide risk assessment services to identify vulnerabilities and improve security practices.
- Cost Coverage: Policies may cover costs related to legal defence, customer notification, data recovery, and even ransom payments in some cases.
- Support Services: Insurers often offer support services during and after a cyber incident, such as legal advice, public relations, and cyber security expertise.
It’s important to note that cyber security insurance does not replace the need for robust security measures. Think of it more as a safety net, providing financial support and resources in the event of a security breach.

Combining these essential elements, we create a formidable defence against cyber threats, ensuring your network is resilient against infiltration and attacks.
Navigating the complexities of network security requires continuous vigilance and expertise. Reach out to a Stanfield IT security specialist to strengthen your defences and conduct a thorough cyber security audit. Together, we can build a secure and robust network environment tailored to your business’s needs.
