Introduction
In late 2021, researchers discovered one of the most significant cyber security vulnerabilities ever seen. The vulnerability was in Log4j, an open-source Java-based logging utility. The software essentially records activities undertaken by a wide variety of computer software.
Log4Shell, as the vulnerability is known, allowed hackers to bypass computer security systems and gain access to accounts without a password. Once in the system, hackers could install malicious software or even steal sensitive data.
Get Your Free Essential Eight Cyber Security Report
Learn:
-
- The cyber security gaps costing you time and money.
- Practical steps to upgrade your security measures.
- The hidden risks of poor security protocols.
- How to bolster your cyber security and aid business growth.
While the vulnerability has been patched, a report by the Cyber Safety Review Board describes the incident as an “endemic vulnerability” that could remain in the Log4j system for more than a decade.
This is one example of the many types of cyber security vulnerabilities that can affect business systems, networks, and devices.

In this article, we’re going to look at the types of software vulnerabilities that could effect your business.
What Is a Cyber Security Vulnerability?
We consider a cyber security vulnerability to be a weakness or flaw in a computer system, network, software application, as well as a business’s processes, policies, and procedures. Hackers often exploit these weaknesses to:
- Gain unauthorised access to sensitive data
- Disrupt or disable critical systems
- Undertake other malicious activity
Cyber security vulnerabilities are exploited using various techniques, such as malware and phishing attacks. Some of the most common vulnerabilities that could impact your business are:
Let’s dive in.
Software Vulnerabilities
Software vulnerabilities are weaknesses or flaws in software that hackers can exploit to gain unauthorised access to systems, steal sensitive data, or cause other types of damage. These vulnerabilities can exist in any type of software, including operating systems, web browsers, and applications.
There are different types of software vulnerabilities, including:
Buffer Overflow
Buffer overflow cyber attacks exploit vulnerabilities in software by attempting to write more data to a buffer (a temporary data storage area) than it can hold. This can cause the buffer to overflow, overwriting and corrupting nearby data and potentially allowing an attacker to execute malicious code on the affected system.
Buffer overflows are a common type of vulnerability in software, particularly in aging or poorly designed systems.
Hackers try to exploit buffer overflows by altering the code of an application and replacing it with malicious code. By changing the program, they attempt to trigger a response that damages files or exposes sensitive business data. Using buffer overflow attacks hackers can sometimes even gain unlimited access to a computer’s resources.
SQL Injection
SQL Injection is a web security vulnerability that allows hackers to gain unauthorised access to information on a web application that is not intended to be displayed. This can include information such as:
- Intellectual property
- Customer data
- Credit card data
- Financial or administrative business information
In some cases, the hacker is able to modify or delete this data, causing constant changes to the content and behaviour of the application. SQL injection attacks can target any application that uses a SQL database, making websites common targets.
SQL injection attacks can have serious implications for a business including loss of critical business data and reputational damage.
Software vulnerabilities can be caused by a variety of factors, including coding errors, poor design, and the use of outdated or insecure software. They can also be introduced through the use of third-party libraries or components that have not been properly vetted for security.
Even with strong vetting measures in place, software vulnerabilities can still be discovered after a product has been released. To address this, many companies have implemented vulnerability disclosure programs, allowing independent researchers and others to report their products’ vulnerabilities responsibly.
Hardware Vulnerabilities
Hardware vulnerabilities differ from software vulnerabilities due to the nature of the hardware. Hardware is generally developed early in the product lifecycle, yet is still required to execute the software that will eventually run on it.
Unlike software, we usually can’t update hardware (unless via replacement), so vulnerabilities can sometimes be easier to exploit. Additionally, upon the end of its lifecycle, you need to dispose of the hardware correctly to ensure hackers don’t criminals can’t steal data still present on the hardware.
One type of hardware vulnerability is a race condition, which occurs when two or more processes are trying to access the same resource simultaneously and the system is unable to properly handle the conflicting requests. This can lead to data corruption, denial of service attacks, or even the execution of malicious code.
Hardware vulnerabilities can also be introduced through the use of insecure or outdated firmware. Firmware is a type of software that is stored on a hardware component, such as a router or a printer and is used to control the hardware’s behaviour. If the firmware is not kept up to date, it can contain vulnerabilities that hackers can exploit.
Hardware vulnerabilities can also be caused by physical tampering or the use of insecure hardware components. For example, an attacker might try to insert a malicious chip into a computer’s motherboard in order to gain unauthorised access to the system. Similarly, an attacker might try to use a fake or counterfeit hardware component, such as a memory chip or network card, that contains vulnerabilities.
Human Vulnerabilities
Human cyber security vulnerabilities refer to the ways in which people can be exploited or targeted by cyber attackers. This can occur through a variety of means, such as social engineering.
Social Engineering
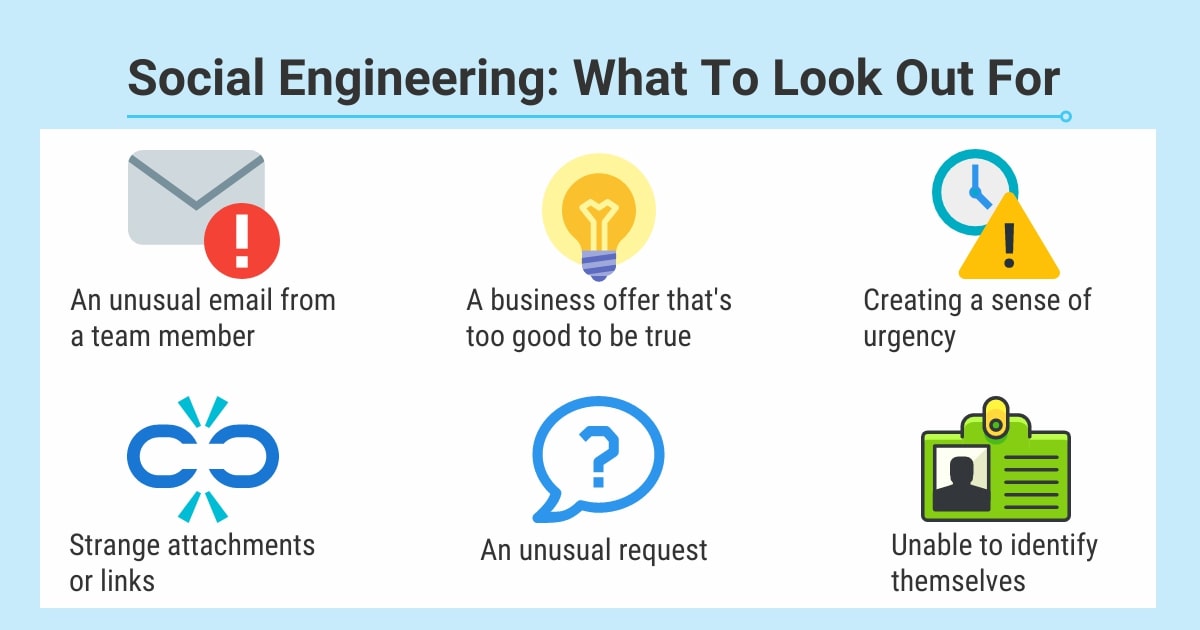
One way humans can be targeted is through social engineering tactics, which involve manipulating people into taking actions they might not normally take, such as clicking on a malicious link or providing login credentials. These tactics can take many forms, such as:
- Pretexting: Creating a false identity or scenario to obtain sensitive information. This attack is not limited to online activity
- Baiting: Offering something attractive to entice a victim to take action.
- Scareware: Using fear or urgency to pressure a victim into downloading software or sending money to receive help.
- Tailgating: An offline threat – the attacker will manipulate their way into restricted areas by posing as common workers such as delivery drivers or business representatives. Once an authorised employee opens the door, the attacker will ask them to hold it or stop it closing to gain access.
To protect against social engineering attacks, it is important for individuals to be aware of these tactics and to be sceptical of requests for sensitive information or actions that seem out of the ordinary.
Phishing
A common social engineering technique is phishing emails, designed to trick users into giving away sensitive information or downloading malware. These emails often appear to come from legitimate sources, such as banks, government agencies, or even businesses you frequently deal with. They may contain urgent requests for action or threats of negative consequences if you do not comply. To protect against phishing attacks, it is important for individuals to be aware of the potential for these types of scams and to be cautious about providing personal information or clicking on links in emails from unknown sources.
Malware
Malware is an example of what can occur when human vulnerabilities are exploited.
Malware is software that is designed to damage or disrupt computer systems, and it can be spread through a variety of means, such as infected websites, email attachments, or removable media.
In addition to the threats mentioned above, there are many other forms of human cyber security vulnerability, such as weak passwords, unsecured Wi-Fi networks, and failure to use two-factor authentication. To protect against these and other threats, it is important for individuals to be aware of the potential for cyber attacks and to take steps to protect themselves and their personal information.
Now that we know what kind of cyber security vulnerabilities are out there, let’s take a look at what you can do to protect your business from them.
What Can You Do?
Cyber security can be confronting, there are plenty of threats out there that could do harm to your business. Luckily, there are a number of ways you can protect your business. All it takes is a little time, effort, and investment.
Let’s go through some of the steps you can take.
1. Educate Employees About Cyber Security
People are often the biggest cyber security risk, so it’s important to provide employees with cyber security training on how to identify and prevent cyber threats, such as phishing attacks and malware infections.

2. Regularly Update Software and Devices
By regularly updating software and devices, you are ensuring that the latest known vulnerabilities are being addressed.
3. Use Strong Passwords
Strong and unique passwords or passphrases are one of the first steps in a robust cyber security landscape.
4. Use Firewalls and Antivirus Software
Firewalls help to protect against unauthorised access to a network, while antivirus software can detect and remove malware.
5. Regularly Back Up Business Data
Create regular backups of important business data to protect against data loss in the event of a cyber attack.
6. Implement Access Control
Use access controls to limit employee access to sensitive business data and systems to reduce the risk of unauthorised access.
7. Use Secure Networks
Avoid using unsecured networks. If you have no choice but to use an unsecured network such as public Wi-Fi, ensure you use up-to-date anti-virus, a trusted VPN, up-to-date software, and strong passwords.
8. Use Multi-Factor Authentication
Enable Multi-Factor Authentication to protect against unauthorised access to systems and data.
9. Use Security Protocols
Security protocols such as HTTPS can help to protect against data interception and tampering.
10. Conduct Regular Security Assessments
Regularly assess the security of systems and networks to identify and address any vulnerabilities. One common way to do this is by performing vulnerability scanning.
Vulnerability Scanning
Vulnerability scanning is a process of identifying, assessing, and prioritizing vulnerabilities that exist within a business’s IT infrastructure.
To identify vulnerabilities, businesses typically use specialised software or tools that scan their systems and networks for known vulnerabilities. These tools work by comparing the configurations and software versions on the business’s systems against a database of known vulnerabilities. When a vulnerability is identified, the tool will provide information about the vulnerability, including its severity, potential impact, and potential fixes.
After vulnerabilities have been identified and assessed, they are prioritised for remediation based on their severity and potential impact. This process involves identifying the most effective means of fixing vulnerabilities, which may include patching or upgrading software, configuring network security controls, or implementing additional security measures.
It’s recommended that you conduct vulnerability scans on a regular basis to identify and fix vulnerabilities as they arise. In addition to routine scans, you should also conduct a vulnerability scan in the wake of a cyber security incident, or if there has been a change in your IT environment. For example, it’s a good idea to conduct a vulnerability assessment after deploying a new software application.
Vulnerability scanning is an important part of a business’s overall cyber security strategy. By identifying and addressing vulnerabilities in a timely manner, businesses can reduce the risk of a security breach or cyber attack, and protect their systems, data, and reputation. In addition to conducting regular vulnerability scans, businesses should also have a robust incident response and remediation process in place to quickly address any security issues that may arise.
Vulnerability scanning can be a complex and time-consuming process, particularly if your business has a large and complex IT infrastructure. To ensure the effectiveness of your vulnerability scanning efforts, you may want to use a vulnerability assessment tool, such as Tenable’s Nessus.
Nessus can identify software flaws, missing patches, malware and misconfigurations within your operating system, devices or applications. Nessus is constantly updating with the latest threats so your system is protected from new attacks. Nessus comes with some built-in templates depending on what your focus is — from configuration audits to patch management. You can create custom reports including specific vulnerability types, vulnerabilities by host or plugin, and customise by team or client, who you can email after every scan.
Conclusion
Every business has its own unique cyber security vulnerabilities. To keep your business safe, we recommend that at the very least you implement the steps listed above.
If you’d like help protecting your business, check out our cyber security services. You’ll learn how we keep businesses cyber-safe using our 100% Australian-based service team.
