Cyber security challenges every business to uphold only the best data management strategies and security protocols. These strategies will ensure you protect your sensitive information, and customer satisfaction. At a glance, it may not seem like it, but cyber security plays a key role in your customer satisfaction.
Research shows that in the wake of a severe security breach, small-to-medium size businesses experience at least 8 hours of system downtime (Cisco 2018 SMB Cyber Security Report). Furthermore, 39% of businesses reported that more than half of their systems were affected. In a small business, you’re far more likely to have interconnected core systems with less separation between critical systems. Take a moment to think about that. Could your business survive if more than half your system went down for over 8 hours? Our best guess is probably not.

The 5 Cyber Security Challenges Facing Businesses Today
Unfortunately, cyber attacks are consistently on the rise. Furthermore, the overall cost of data breaches has increased (from an average of $141 per record, to $148). So, it’s clear that many businesses need to address a few things in order to protect themselves and their customers. As a result, we’ve identified the five major cyber security challenges that small-to-medium organisations need to focus on. We believe that overcoming these challenges will help your business succeed in these attack-infested waters of modern business.

Challenge #1: Identify and Contain Breach As Quickly As Possible
This sounds like an obvious rule of thumb for any business, but it’s not nearly as simple as it sounds. The average time to identify a breach in 2019 was 185 days! That’s half a year. Then after that, the average time to contain a breach is around 75 days. These numbers are much higher than you might expect. But often data breaches go unnoticed for months. This comes down to one main reason: businesses are not alerted to the breach at the time of the attack.
Unless you’re aware of the attack at the time that its happening, how could you possibly know your data has been compromised? Imagine that one day while you were out at work someone broke into your home. They made a copy of your passport and then left unnoticed, leaving no evidence of their presence. How could you possibly know that something was amiss? Unless you knew for certain that someone had been in your home? It’s a similar concept. This is why data breaches take so long to identify. As a result, compromised data could be used in a damaging way well before the affected party even realises.
The challenge in making sure your business isn’t one of these statistics lies in your cyber security management. Implement active network monitoring, data loss prevention, and next-gen firewall with anti-malware. These tools are all designed to alert you to any suspicious activity and attempted breaches.

Challenge #2: Reduce The Opportunity For Attack
What’s better than identifying a data breach or attack as soon as possible? Avoiding the attack altogether, obviously. So, this is your next challenge as a small-to-medium business: identify and minimise risks, so there is far less opportunity for cyber attack. Most cyber attacks rely on exploiting system vulnerabilities, and looking for the ‘path of least resistance’. This is why small-to-medium businesses are common target of cyber attacks; they are far less likely to have the cyber security measures of a big enterprise (despite the enterprise probably having juicier data).
So, it becomes about reducing those opportunities. We do this by patching system vulnerabilities and implementing cyber security policies that make it nearly impossible for attacks to be carried out. Implement strategies like the ASD’s ‘Essential Eight’. Implement multi-factor authentication, and utilise a mobile device management tool. Ensure that you have data encryption on every level. Cyber security is a process of protecting your data and ultimately, your livelihood. We’ve compiled a sensible list of cyber security strategies that will drastically reduce vulnerabilities and opportunities for attack.
Be mindful that data management forms a large part of this aspect of cyber security, which is not always something that is given a lot of thought. Have a look at some tried and true data management strategies we advise:


Challenge #3: Creating a Culture of Awareness
Why is this a challenge? It’s a challenge because a) it is so common and all too easy for businesses and employees to undervalue the importance of cyber security and b) even if you’re on board with it, it’s going to be hard to get everyone else engaged with the same level of vigilance. It feels like a much less personal stake for employees. For many employees, they’ve been in the workforce for anywhere from 10-40 years, so you can imagine that cyber security simply isn’t a habit or something they consider on a daily basis.
When you work in IT, or other modern and/or technology-based industries, it’s easy to fall into a bubble where you live and breathe cyber security issues. It can be really difficult to convey that importance to employees who’ve spent 80% of their career without giving it a second thought. So, this is your next challenge. Why is it important? Employee education is one of the top cost-reducing factors when it comes to the overall cost of a data breach. With unified understanding from the managerial level down, you minimise the risk and chance of attack.
Creating a culture of awareness means constantly and consistently highlighting cyber security within the workplace from day one. It’s not enough to run a one-off seminar on the importance of password protection. Some suggestions that may help get the ball rolling: incentivise your staff to identify cyber security risks and reward them for executing excellent cyber security awareness, regularly review security news and vulnerabilities together as a team, or run cyber drills where your staff have to identify or experience a simulated cyber attack or phishing attempt.

Challenge #4: Avoiding Loss of Functionality
One of the more difficult cyber security challenges lies in maintaining business functionality in the event of an attack or breach. As we discussed above, a severe attack can bring everything grinding to a painfully expensive halt. Your business could suffer from excessive system downtime, or data loss. You need to minimise this downtime and loss of functionality within your business. In order to avoid this critical loss of functionality, there are a few strategies you can implement.
Firstly, every business should have an up-to-date business continuity plan. A solid business continuity plan will provide you with a set of steps to take following a cyber incident to get you back on your feet as soon as possible. Secondly, backups and disaster recovery are your friend. Ensure that you have regular backups scheduled for your system (either to a local, or cloud-based server). Backups should always be tested! It’s no good to you if you try to restore from backup, only to find the last month worth of data isn’t there.
Lastly, and this is not an accessible option for every business, but redundant infrastructure is also going to be your lifesaver here. In the event of a serious cyber attack that puts your whole system out of action; a redundant server exists to take over in the immediate aftermath of said failure.

Challenge #5: Complying With Cyber Security Legislation
The last challenge on our list is one that many businesses don’t think about. Cyber security legislation is slowly coming into effect around the world. This signifies a cultural shift in the way cyber security is understood and reflects new social norms in the cyber security world. However, too many businesses are not taking note of the changes and are possibly unaware that they may be in violation of these cyber security regulations.
In 2019, we are looking at two primary regulations that have come into effect. Based in the EU, you have the General Data Protection Regulation and here in Australia, we have the Notifiable Data Breaches Scheme. Despite being far from the EU, if your business handles any information for customers or business partners in the EU; you’ll be on the hook. And it’s almost guaranteed that your business falls within the requirements for compliance of the NDBS and the Privacy Act. Unless your business has a cool $420,000 lying around to spare in fines; it’s important to ensure you’re complying with the Australian regulations (even if it’s just to protect your wallet).
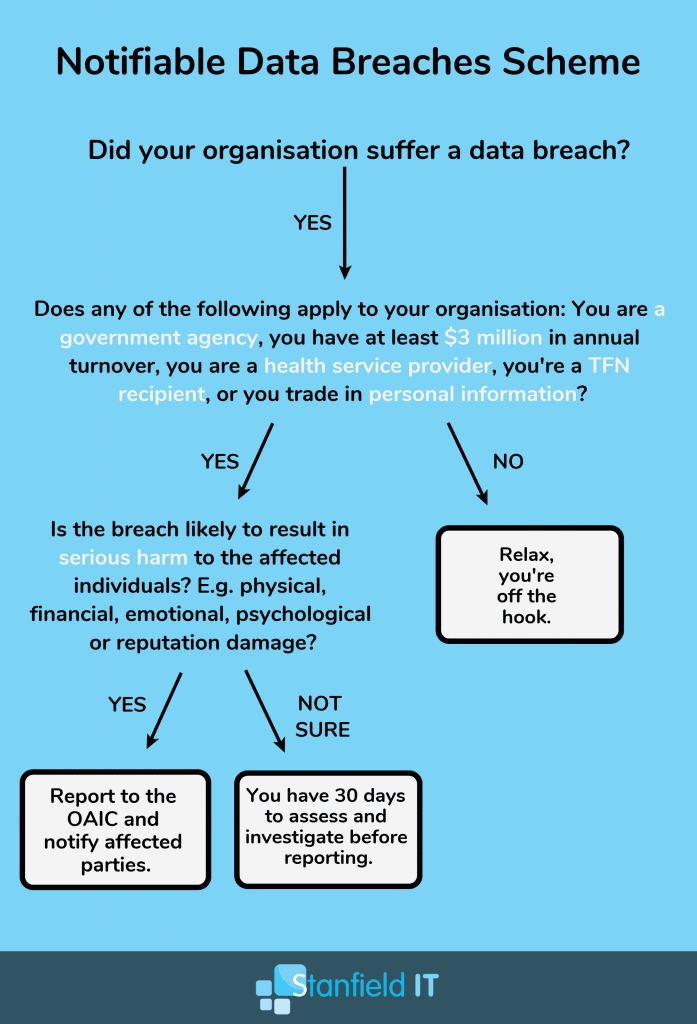
Getting Started!
So, where’s your business at in terms of meeting these cyber security challenges? Are you up for the task? We recommend a couple of things to get you started. Firstly, do you have a contextual understanding of the flow of data within your business? We have a simple flowchart that breaks down the process for you here. Secondly, where’s your cyber security at? Perform a basic internal review of your cyber security as well.
With these two main learning tasks completed, you’re now much more equipped to actually meet and overcome these cyber security challenges. With the correct cyber security procedures and protocols in place, you’re already ahead of the curve. A comprehensive cyber security strategy would enable you to identify breaches quickly, and would absolutely reduce the opportunity for attack. You would be all over it in terms of creating and encouraging a cyber secure awareness in the workplace, and have appropriate contingencies in place to avoid loss of functionality.
However, if you need someone to help get you started, or simply don’t have the time and need to outsource this process; then it’s time to look into employing an IT managed services team. Contact our amazing team at Stanfield IT and we’ll happily talk you through the ways your business can benefit from just such IT services.
