The Stark Reality of Australia’s Cyber Battlefield
With one cybercrime reported every six minutes and a staggering 47 million data breaches recorded in 2024, Australia’s digital landscape has become a battleground where organisations face 60% more cyberattacks than the global APAC average. This alarming reality propelled Australia to 11th place globally for cyber incidents, while ransomware attacks surged by 25% year-over-year.
As cybersecurity leaders navigate this treacherous terrain, the Australian Government’s 2023-2030 Cyber Security Strategy emerges as a beacon of hope, investing A$586.9 million in a comprehensive six cyber shields framework. However, government initiatives alone cannot shield organisations from sophisticated threat actors. In 2025, the difference between cyber resilience and catastrophic breach lies in how effectively security professionals implement strategic, layered defense mechanisms that complement national efforts while addressing unique organisational vulnerabilities and risk profiles.
Building Strategic Foundations in an Evolving Threat Environment
Organisations face unprecedented cybersecurity challenges in 2025, requiring strategic frameworks that move beyond traditional perimeter-based defenses. Australia’s six cyber shields framework provides a comprehensive blueprint for modern cybersecurity strategy development.
A robust cybersecurity strategy encompasses strategic versus tactical thinking—focusing on long-term resilience rather than reactive measures. Organisations must integrate cybersecurity with business continuity planning, ensuring operational resilience during and after cyber incidents.
Key Strategic Components for 2025:
- Zero Trust Architecture implementation across all digital touchpoints
- Assume Breach methodologies with continuous monitoring capabilities
- Threat intelligence sharing partnerships with industry and government
- Critical infrastructure protection through redundancy and hardening
- Sovereign capability development reducing third-party dependencies
- Regional collaboration fostering collective defense mechanisms
- Business continuity integration ensuring seamless operational recovery
- Risk-based governance aligning security investments with business objectives
“Zero trust operates on the principle that trust is never granted by default, regardless of location or user credentials. Every access request must be verified, authenticated, and continuously validated throughout the session lifecycle.”
The distinction between strategic and tactical approaches remains crucial. While tactical responses address immediate threats, strategic foundations establish sustainable security postures that adapt to evolving threat landscapes.
Modern organisations must embrace assume breach methodologies, recognising that prevention alone is insufficient. This paradigm shift requires robust detection, response, and recovery capabilities integrated with business operations.
Business continuity integration ensures cybersecurity strategies support organisational resilience rather than operating in isolation. This alignment creates comprehensive risk management frameworks that protect both digital assets and business operations.
Organisations implementing these strategic foundations position themselves to navigate 2025’s complex threat environment while maintaining operational excellence and competitive advantage through proactive risk management and adaptive security architectures.
Navigating Complex Threat Vectors and Strategic Implications
The cybersecurity landscape has undergone significant transformation in 2025, with threat actors demonstrating unprecedented sophistication and persistence. Recent intelligence indicates a 25% surge in ransomware attacks across Australian organisations, presenting critical strategic implications for enterprise security frameworks.
Modern ransomware operations have evolved beyond simple encryption tactics, with threat groups like AlphV (BlackCat) and Dark Angels orchestrating complex multi-stage attacks. These campaigns now incorporate double extortion methodologies, where data exfiltration has nearly doubled compared to previous attack patterns. Ransom demands have escalated dramatically, reaching tens of millions of dollars, reflecting the strategic targeting of high-value enterprises.
Business Email Compromise continues to demonstrate alarming effectiveness, bypassing multi-factor authentication in 75% of documented cases. This statistic underscores the critical need for security leaders to reassess authentication frameworks and implement zero-trust architectures that extend beyond traditional perimeter defenses.
Advanced Persistent Threats and Nation-State Actors
Advanced Persistent Threat campaigns present particularly concerning trends, with average detection times extending beyond 400 days. This extended dwell time enables threat actors to establish deep network persistence, conducting extensive reconnaissance and lateral movement operations.
Nation-state actors are increasingly targeting Australian healthcare, financial services, and government sectors through sophisticated supply chain infiltration and zero-day exploitation. These campaigns demonstrate strategic coordination, often aligning with geopolitical objectives while maintaining operational ambiguity.
The healthcare sector faces heightened vulnerability due to legacy infrastructure integration challenges, while financial institutions encounter sophisticated social engineering campaigns designed to circumvent regulatory compliance frameworks.
Security executives must prioritise threat intelligence integration across organisational defense strategies. The current threat landscape demands proactive intelligence-driven security architectures that can identify indicators of compromise before threat actors establish persistent access. Organisations should immediately evaluate their threat detection capabilities and implement comprehensive intelligence sharing protocols to enhance collective defense postures against these evolving threat vectors.
Establishing Effective Cyber Security Governance
Board-level engagement forms the cornerstone of robust cybersecurity governance, requiring executive leadership to champion security initiatives across the organisation. Modern governance structures demand that boards actively participate in cybersecurity oversight rather than delegating responsibility solely to IT departments.
Effective governance begins with establishing clear organisational structures that define roles, responsibilities, and reporting relationships. The CISO plays a pivotal role in coordinating implementation of zero trust architecture and ensuring leadership commitment at all levels.
| Governance Role | Primary Responsibilities | Meeting Frequency |
|---|---|---|
| Board of Directors | Strategic oversight, risk appetite setting | Quarterly |
| Cybersecurity Committee | Policy review, incident response oversight | Monthly |
| C-Suite Executive Sponsor | Resource allocation, strategic alignment | Bi-weekly |
| CISO | Operational coordination, risk reporting | Weekly |
| Risk Management Team | Vulnerability assessment, compliance monitoring | Continuous |
C-suite responsibilities extend beyond traditional IT governance to encompass enterprise risk management integration. Executives must ensure adequate resource allocation for vulnerability scanning, penetration testing, and control validation activities. They must also champion user access reviews and establish clear accountability frameworks.
Strategic Decision-Making Implementation Framework:
- Establish dedicated cybersecurity oversight committees with board representation
- Integrate cybersecurity metrics into enterprise risk dashboards
- Define clear escalation procedures for security incidents
- Implement quarterly CISO reporting to board leadership
- Conduct regular governance effectiveness assessments
- Align cybersecurity investments with business objectives
Organisations must embed cybersecurity governance into their business continuity planning processes, ensuring that security considerations influence strategic decision-making. This integrated approach enables proactive risk management and demonstrates due diligence to stakeholders, regulators, and customers while maintaining competitive advantage in an increasingly threat-laden digital landscape.
Implementing Defense-in-Depth and Zero Trust Principles
Organisations must adopt a comprehensive defense-in-depth strategy combined with zero trust principles to address evolving cyber threats. Defense-in-depth creates multiple security layers, ensuring that if one control fails, others remain operational. This approach integrates with zero trust architecture, which eliminates implicit trust assumptions and continuously validates every transaction.
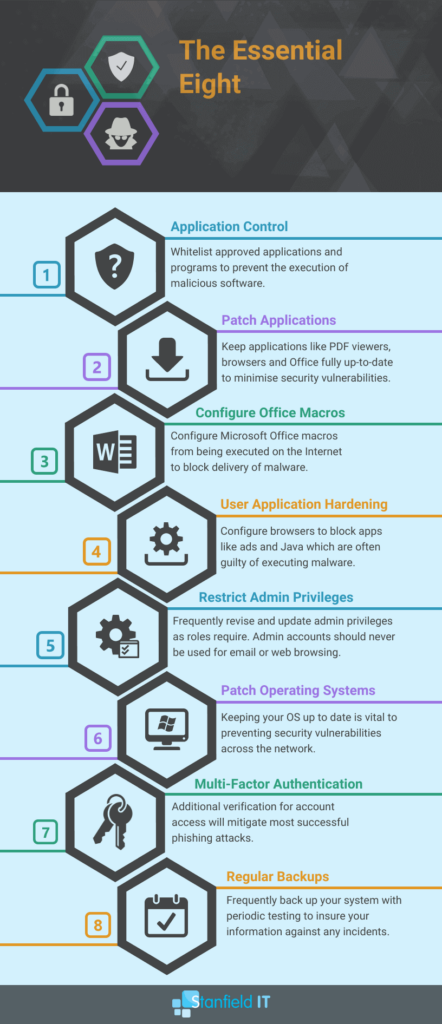
The Essential Eight Maturity Model provides a foundation for implementing these principles through systematic application of patching protocols, application control mechanisms, and robust backup strategies. However, successful implementation requires careful technology selection based on strategic criteria:
- Interoperability with existing security infrastructure and business applications
- Scalability to accommodate organisational growth and evolving threat landscapes
- Performance impact assessment to maintain operational efficiency
- Cost-effectiveness analysis including total ownership expenses
- Vendor reliability and long-term support capabilities
- Compliance alignment with regulatory requirements and industry standards
Identity Management and Access Control
Privileged Access Management (PAM) serves as the cornerstone of zero trust implementation. Organisations must implement multi-factor authentication, continuous monitoring, and micro-segmentation to control access to critical assets. PAM solutions provide granular control over administrative accounts, reducing the attack surface and enabling comprehensive audit trails.
The transformation extends beyond technology deployment. As cybersecurity expert Dr. Chase Cunningham notes, “Zero trust isn’t just a technology shift—it’s a fundamental change in how organisations think about security perimeters and trust relationships.”
Successful implementation demands organisational commitment to cultural change. Employees must understand that continuous verification protects both corporate assets and their roles. Leadership must champion the initiative, providing resources for training and technology adoption.
Identity and Access Management systems must evolve to support dynamic policy enforcement, risk-based authentication, and seamless user experiences. This comprehensive approach ensures that organisations maintain security posture while enabling business agility in an increasingly complex threat environment.
Creating Sustainable Cyber Resilience Capabilities
Cyber resilience represents a fundamental shift from traditional security approaches that prioritise prevention to strategies emphasising rapid recovery capabilities. While conventional security focuses on building impenetrable defenses, resilience acknowledges that breaches will occur and prioritises minimising business disruption through swift restoration of critical operations.
Organisations must establish clear Recovery Time Objectives (RTOs) and conduct comprehensive Business Impact Analysis (BIA) to quantify acceptable downtime thresholds. Traditional security measures often fail to address the reality that sophisticated attackers will eventually breach perimeter defenses. Resilient organisations instead invest in adaptive response capabilities that enable them to detect, contain, and recover from incidents while maintaining essential business functions.
Zero Trust Architecture forms the foundation of resilient cybersecurity, requiring continuous verification of users, devices, and applications regardless of their location within the network. This approach eliminates implicit trust assumptions that characterise traditional perimeter-based security models.
Workforce Development and Culture
Strategic awareness programs must transcend basic compliance training to foster genuine behavior change. Australia’s national cyber security strategy exemplifies this approach, emphasising cultural transformation alongside technical capabilities. Organisations should implement role-based training that connects cybersecurity responsibilities to specific job functions, making security personally relevant to each employee.
A leading Australian financial institution successfully transformed its security culture by implementing gamified awareness programs and embedding security champions throughout business units. This approach reduced security incidents by 40% within 18 months while improving employee engagement scores.
When considering outsourcing versus insourcing decisions, organisations must evaluate their capacity to develop internal expertise against external provider capabilities. Insourcing enables greater control over cultural integration and knowledge retention, while outsourcing provides access to specialised skills and threat intelligence. Many organisations adopt hybrid models, maintaining core capabilities internally while leveraging external expertise for specialised functions like threat hunting and incident response.
Sustainable cyber resilience requires balancing technological solutions with human-centered approaches that build organisational capacity for adaptation and recovery.
Strategic Implementation and Maturity Progression
Organisations must align cybersecurity initiatives with Australia’s three-horizon strategy framework to achieve sustainable security maturity by 2030. The first horizon focuses on immediate defensive capabilities and quick wins through vulnerability management and incident response optimisation. Second horizon initiatives target transformative security architecture improvements, while the third horizon emphasises emerging threat preparedness and innovation integration.
Effective phased deployment requires robust KPI frameworks measuring security posture improvements, threat detection efficiency, and business continuity metrics. ROI calculation methodologies should encompass risk reduction quantification, operational cost savings, and compliance adherence benefits. Organisations can establish baseline security metrics and track progression through maturity models, ensuring measurable value delivery at each implementation phase.
Quick wins include automated patch management, enhanced monitoring capabilities, and streamlined incident response workflows. These initiatives provide immediate security improvements while building organisational confidence for larger strategic investments.

Future Trends and Strategy Adaptation
Emerging technologies demand strategic adaptation as artificial intelligence, quantum computing, and IoT expansion reshape the threat landscape. AI-driven security tools offer enhanced threat detection capabilities, while quantum computing presents both opportunities for advanced encryption and risks from quantum-resistant cryptography requirements.
Automation investment priorities generate significant debate among security professionals. Proponents argue that automated threat response reduces incident response times and human error risks. However, critics emphasise that over-automation may create single points of failure and reduce security team expertise development. Organisations must balance automation benefits with maintaining human oversight capabilities.
Orchestration platforms enable coordinated security tool management, improving operational efficiency while maintaining strategic flexibility. Investment decisions should consider existing infrastructure compatibility and staff training requirements.
Continuous strategy review mechanisms ensure organisational resilience against evolving threats. Regular assessment cycles, threat intelligence integration, and strategic plan updates enable proactive security posture adjustments. Organisations that embrace adaptive planning methodologies maintain competitive advantages while protecting critical assets against sophisticated adversaries.
Taking Action: Strategic Imperatives for Tomorrow’s Cyber Resilience
Australia’s cybersecurity landscape demands decisive leadership and immediate action. The six cyber shields framework provides organisations with a robust foundation, but implementation requires strategic commitment from cybersecurity executives who understand that threats evolve faster than traditional defenses.
Zero trust architecture isn’t just a technical transformation—it’s a fundamental shift in organisational thinking. Cybersecurity leaders must champion this transition while establishing governance structures that enable rapid adaptation to emerging threats. The Australian Cyber Security Strategy 2023-2030 emphasises collaborative defense, making inter-organisational partnerships essential for comprehensive protection.
Immediate next steps for cybersecurity professionals:
- Conduct comprehensive zero trust readiness assessments across all organisational layers
- Establish executive-level cyber resilience committees with clear accountability metrics
- Implement continuous threat intelligence sharing protocols with industry peers
- Develop adaptive incident response frameworks that evolve with threat landscapes
The time for reactive cybersecurity approaches has passed. Today’s threat actors leverage sophisticated techniques that require equally sophisticated defenses. Organisations that delay strategic implementation risk becoming tomorrow’s breach headlines.
Cybersecurity executives must lead this transformation, ensuring their organisations don’t just survive cyber threats—they thrive despite them. The framework exists; the strategy is clear. What remains is decisive action.
Building Your Cyber Security Strategy
Take the first step towards comprehensive cybersecurity strategy. Contact us today to schedule a cyber security assessment and learn how our tailored solutions can safeguard your business.
Don’t wait for a breach to realise the importance of security.
