As your company’s CIO, you know how often businesses are targeted by cyber criminals. Convincing members of the board that all that money is well spent on cyber security and the IT department isn’t always easy, though. Use our cyber security checklist to show all the ways that your department is working to protect your company now and in the future. Have you ever prepared a cyber security checklist to ensure you have all of your bases covered? If not, where do you start? We’re here to guide you through main points to consider.
Our Cyber Security Checklist
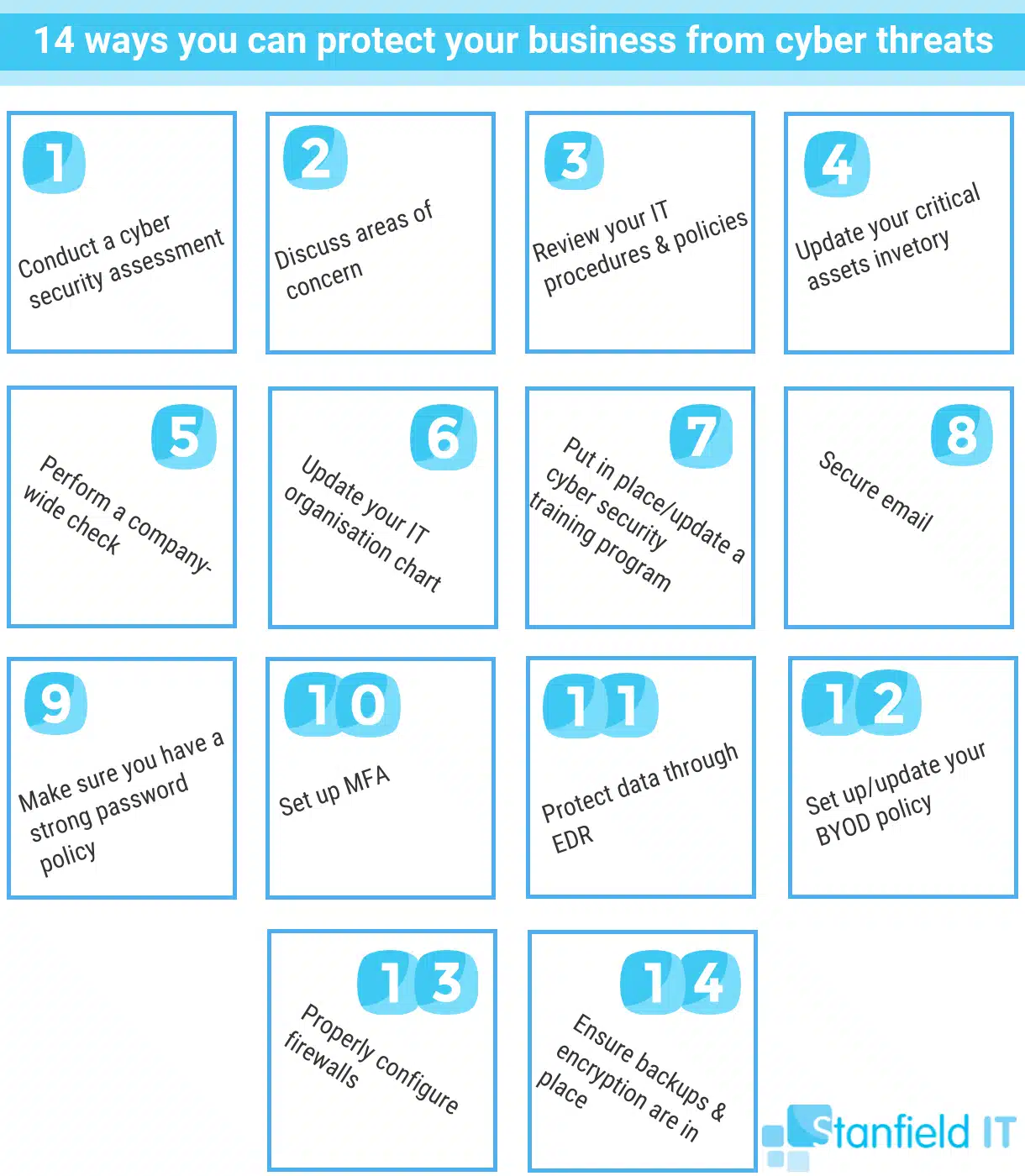
Item #1: When did you last undertake a cyber security assessment?
A thorough cyber security assessment of your business will reveal where you’re lacking when it comes to data security and disaster management readiness. Additionally, you’ll gain access into areas you’re preforming well in—so it’s not all bad news. Recognising gaps and establishing the steps needed to close them means you will have set out a roadmap to follow for your cybersecurity initiatives.
Item #2: When was the last time you met with your IT team to discuss new areas of concern?
We don’t just mean managers or team leaders, but everyone. You have people that are tasked with constantly learning and solving problems to your systems—utilise them. Employees have also been learning when they’re not on the job, so take advantage of this too. It doesn’t do to ignore Frank just because he’s an intern, for example. For all you know, he might be the only one to have heard about a new type of ransomware. While we understand that cyber security doesn’t always rank on the “top ten” of the daily activities within a company, having regular meetings with your team shouldn’t be overlooked.
Item #3: When did you last review your company’s IT procedures and policies?
This isn’t just the company’s compliance policy. We mean asking yourself what you’ve dedicated to protecting your company’s intellectual property and confidential property. This is your written plan to handle all issues that are related to cyber security. It ranges from how you back up and encrypt data, to how to handle a crisis situation such as a data breach. There are templates available on the web that you can use to get you started. You can then alter it to fit the needs of the company. Some of the sections to include are listed below.
Privacy Policy
The statement or legal document that discloses some or all of the ways a party gathers, uses, discloses and manages a customer’s or client’s data. This fulfils a legal requirement to protect a customer’s or client’s privacy.
Network Security Policy
An NSP outlines the rules for computer network access, determines how the policies are enforced, and lays out the basics for your company’s security environment.
Remote Access Policy
The RAP outlines the acceptable methods for people to remotely connect to the internal network. This is essential, given the increasing number of remote workers. Such employees often connect from insecure network locations, like cafés or unsecured home networks.
Acceptable Use Policy
A set of rules applied by the manager of your company’s network. These rules restrict the ways in which the network can be used.
Internet Access Policy
Applies to all internet users (employees, contract workers, temp agents, business partners, and vendors) who access the Internet through the computing or networking resources.
Email and Communications Policy
This regulates how email and other communication channels specific to the company may be used.
Bring Your Own Device Policy
BYOD governs the corporate IT department’s level of support for devices that employees bring, such as PCs, smartphones and tablets. We will delve into this further in item #12.
While you’re reviewing these policies, make sure that your company is also compliant with the Privacy Act 1988 if you collect or handle personal information.

Item #4: Do you have an up-to-date inventory of your company’s critical assets?
New content is created on a daily basis within your organisation. This means that your critical assets are constantly changing. All key people should have an up-to-date list of the most valuable assets within your company. This needs to include the security measures that are around them. Don’t skimp on the resources allotted to th. If this critical data is compromised, it could have a lasting, negative impact on your company. We aren’t just referring to your company’s reputation, but also how it operates.
Item #5 on our cyber security checklist: When was the last time a company-wide check was performed on all operating systems, software, and data centre equipment?
Programs should be updated on a weekly or bi-weekly basis as hardware regularly becomes outdated. As individual users, this isn’t so much an issue. For a company, though, systems and hardware that are out of date, or ill maintained, are akin to laying out a welcome mat to hackers. Approximately 70% of web-based attacks occur thanks to a vulnerability on the user’s computer. If you have managed IT services, like those offered by Standfield IT, your regular updates should be taken care of. This includes vetted, automated updates for your workstations, servers, and third party patching.
You won’t need to worry about your operating system, iOS, and third-party software (like Adobe, Chrome, and Java products) being out of date. If you don’t hire an external IT company, you should be performing system-wide checks and updates at the end of the working day to keep everything up to date and eliminate as many vulnerabilities as possible.
Item #6 on our cyber security checklist: When did you last update your IT department’s organisation chart?
Most people think of IT and feel that technology handles everything. Your IT employees are equally important, though. Do you know the people in your department? Do you know who has the skills to handle a data breach verses a virus? What about who has recently gained degrees in penetration testing? Staying informed of developments like this allows you to move around the hierarchy within the department so that the people who are most capable of handling challenges when they occur have the authority to do so.
Item #7 on our cyber security checklist: Is there a cyber security training program in place for new and current employees?
Have a training program in place. This is the best way to keep everyone on top of company policies. Ensure that your company is risk aware and fosters risk-prevention as company culture. In doing this, you can help reduce the number of attacks likely to occur. In the constantly changing landscape of cyber threats, it’s no use just having one-off training. Education needs to be ongoing, relevant, and easy for employee’s to remember and practice in everyday operations. Stanfield IT can do this training for you, teaching your staff about data security, email attacks, and sticking to policies and procedures.
Item #8 on our cyber security checklist: Have you secured your email?
It’s estimated that 90% of data breaches begin with phishing attacks. Most of these are delivered to potential victims via email links. With hackers behind phishing attacks getting more intelligent with their construction of realistic-looking emails, potentially disastrous emails are getting harder and harder to detect. Once detected, half of organisations reported that it takes a day (or longer!) to remove phishing emails from endpoints. This is often the result of a lack of trained IT professionals in the office. This is why engaging IT managed services can be such a great step to take for small-to-medium businesses.
Item #9 on our cyber security checklist: Do you have a strong password policy?
If you have a weak password, you’re practically doing the hacker’s work for them! You need to have a password policy for your business that includes MFA (see below), ensures passwords are at least 8 characters in length, and requires passwords to be changed on a regular basis, such as tri-annually. A password management program, such as LastPass, is also a great way to ensure security without the hassle of employee’s forgetting their different passwords. You should also consider denying or limiting USB file storage access, set user screen timeouts, and limit user access. The latter means employees should only have access to resources they need to complete their job.
Item #10 on our cyber security checklist: Have you set up multi-factor authentication?
Multi-factor authentication (MFA) or two-factor authentication (2FA) mitigate your business becoming another number in the 81% of hacking-related breaches that occur as a result of stolen or weak passwords. You shouldn’t be picky with what you use MFA for in your business. Utilise this technology whereever you’re able to, including on your network, email, banking sites, social media, as well as any other services your business uses. With MFA, you are allowed an extra level of protection for your business data, even if your password gets stolen.
Item #11 on our cyber security checklist: Is your data protected through advanced endpoint detection and response?
Endpoint detection and response (EDR) continually monitors and responds to cyber security threats. The end game is to mitigate threats and breaches. Essentially, it protects your corporate network when it’s being accessed from remote devices. This refers to mobile devices like laptops, mobiles, and other wireless devices. The software, which is constantly monitored, is installed on the end-user device, while the data is stored on a centralised database. In the case where a threat is detected, a prompt is immediately issued to the end-user. A list of actions that can take to prevent the threat from developing into a data breach will appear for you to follow.
With EDR, your internal or external security team can collect, record, and store endpoint data. This means your business has exceptional threat visibility. Think of EDR as being like an advanced surveillance system. Today, the latest EDR technologies will protect against file-less and script-based threats. This technology can even prevent a ransomware attack!
Item #12 on our cyber security checklist: Have you set out a current or future BYOD policy?
Cyber criminals LOVE trying to avoid your business’s security by attempting to steal data or access your network through your employee’s mobile devices (like their smartphone or tablet). Unfortunately, SMBs often overlook BYOD policies, thinking they aren’t a large enough business to be targeted. You should make sure you have a BYOD policy in place, with mobile device management or mobile application management being at the forefront. Employees should not be able to access company data on public wireless networks, store company data on devices with little or no security, or be able to access company data on devices where remote wipe cannot be done in the case of the device being lost or stolen.
Item #13 on our cyber security checklist: How’s your firewall situation looking?
A critical part of the security infrastructure of businesses of any size, the proper configuration of your firewalls should not be overlooked. If this isn’t done, your firewalls could let hackers into your internal network, giving them the means to bypass your filters. Your firewalls should also leverage the latest tools, whether you’re implementing them in software form, hardware form, or a combination of the two.
Item #14 on our cyber security checklist: Do you have backups and encryption in place?
Let’s talk backups and encryption. These are the two items that NEED to feature on your cyber security checklist. Where you can, you should consider encrypting your files. This includes those at rest (data on your hard drives), in motion (data on cloud services or email, etc). This is especially crucial for mobile devices, which are more likely to physically get stolen. Backups are a vital (not optional!) part of the cyber security security of your business.
Backups protect your computer from accidental (an employee erasing files they don’t mean to, for example) and intentional (like having to wipe devices that have been affected by ransomware) data loss. Your backup data must be stored on a server that is completely separate from your main server/s. Failing to do this means the same viruses could infect your backup data, too. Backups on the Cloud are also important, as is testing your backups often.
At the end of the day, remind your fellow board members that security doesn’t just matter to the IT department.
We hope you found this cyber security checklist useful if you did please comment below. If you would like to learn more about how to secure your company against attacks and improve your defences, please contact us today.
Need help with a your Cyber Security?
Speak to the experienced team at Stanfield IT on 1300 910 333
