Cyber Security in Australia underwent massive evolution in 2018, which is entirely appropriate given the rate of cyber crime growth. Throughout 2018 and 2019, Australia moved forward in addressing the rise of cybercrime.
As a country, we implemented legislation to protect individuals and their private data. In terms of cyber security, Australia has definitely stepped it up. This continues, especially as ears are perked after the stream of reports of cybercrime in businesses every year and the new awareness that it’s not just large businesses that are targeted.
We like to keep abreast of cyber security Australia focused news. So today, we’d like to provide a round-up of the top cyber security news, trends, and events for 2019 and coming into 2020. We are covering events that transpired in cyber crime, cyber security legislation, strategies, and more.
Let’s dive in.
Don’t miss out on our latest.
Join our subscribers and receive expert insights on cyber security and IT. Sign up now!
Growing Cyber Security Trends
Artificial-Intelligence-Driven Threat Detection
AI is now a tool for both malicious attackers and preventative security. With a machine’s ability to self-learn and adapt, it’s easy to see how this tool could be used for ‘good’ or ‘bad’. In response to AI-driven botnets, cyber security measures are turning to AI-driven threat detection. AI-driven prevention can keep up with the rapid rate of change and sophistication in the world of cyber attacks. We enjoyed this in-depth article on how to win with artificial intelligence.
Blockchain Data Management
You may or may not be aware, but to sum up, blockchain is the technology behind cryptocurrencies like Bitcoin. It’s a totally secure method of storing data, as each unit of data is universally verified by the participating network. Beyond its use in cryptocurrency, blockchain has true potential to provide great online security and data management. This could be anything from online voting to identity management, eliminating the risk of voter or identity fraud. These two articles by Dataversity give great insights into the era of blockchain: what its future looks like and how blockchain and artificial intelligence are driving the fourth industrial revolution.
Ransomware
Ransomware is the attack you need to worry about. Businesses are being hit with ransomware more than ever, and they’re more sophisticated and clever about hiding their insidious operations. They lock up your files and private data, then extort you for money. Usually as a significant sum of cryptocurrency for anonymity purposes. This is an interesting article from CSO Online that goes into the five biggest ransomware attacks in the last five years.
Internet of Things Vulnerabilities
The growth of the Internet of Things (IoT) has brought some new issues to light. IoT has some incredible benefits and has improved the ease and quality of life for many of us. However, there are a few security concerns that should be considered as they begin to be exploited by opportunistic attackers. We’ve all embraced Google Home, but we need to be vigilant about cyber security Australia wide. This 2018 article by InfoSec provides a helpful summary of the security vulnerabilities present in this field, which are still current. They’re also written a great article outline current IoT trends.
Greater Data Privacy Regulation
2018 saw the introduction of more privacy regulation and cyber security-related legislation, which have bled into 2019 and 2020. This tells us that governmental bodies are taking cyber security more seriously. They’re now committed to enforcing data privacy for everyone. With the introduction of the Notifiable Data Breaches Scheme, and the General Data Protection Regulation taking effect both in 2018, it’s clear there is a changing priority. This article from the Australian Financial Review takes a look at the global trend.

Best Cyber Security Strategies
Cyber Security Framework & Compliance
Above all, implementing and enforcing a cyber-security Australia-based framework for your business goes a long way towards protecting your data and private information. Frameworks cover a range of cyber-security protocols, procedures and security configurations. Stanfield IT has written an article that summarises the cyber security framework options in Australia.
Multi-Factor Authentication
Multi-factor (or two-factor) authentication is the new standard in online identity management and security. In short, it’s a simple security feature that can almost completely eliminate successful phishing attempts. It does this by remote access requiring more than just a simple password. Here is a write-up of some reasons you should consider turning to multi-factor authentication this year.
Next-Gen Firewall
Next-Gen Firewall (or NGFW) may sound like a sci-fi invention, but is a very real. Nowadays it’s quite a mainstream cyber security tool for breach prevention. NGFW utilise a combination of firewall technology, intrusion detection, SSL, and HTTP examination capabilities. It’s an essential tool for your network and cyber security Australia wide. This article covers an important aspect of NGFWs that everyone should consider.
VLANs
A VLAN is a virtual LAN (Local Area Network) that allows you to group devices together despite being in different physical LANs. This can help with managing data security, optimising traffic and organising network areas. Above all, VLANs give you greater control over which devices can access one another, and therefore greater security. This article is a great breakdown.
Essential Eight
The ACSC’s policy for cyber security in Australia is a simple list of eight steps everyone can (and should) take. If followed, these steps will immediately reduce your cyber risk and increase your network’s cyber security. There is no hyper-technical tricks here, just common sense protocols for cyber safety. We will always advocate for the Essential Eight.
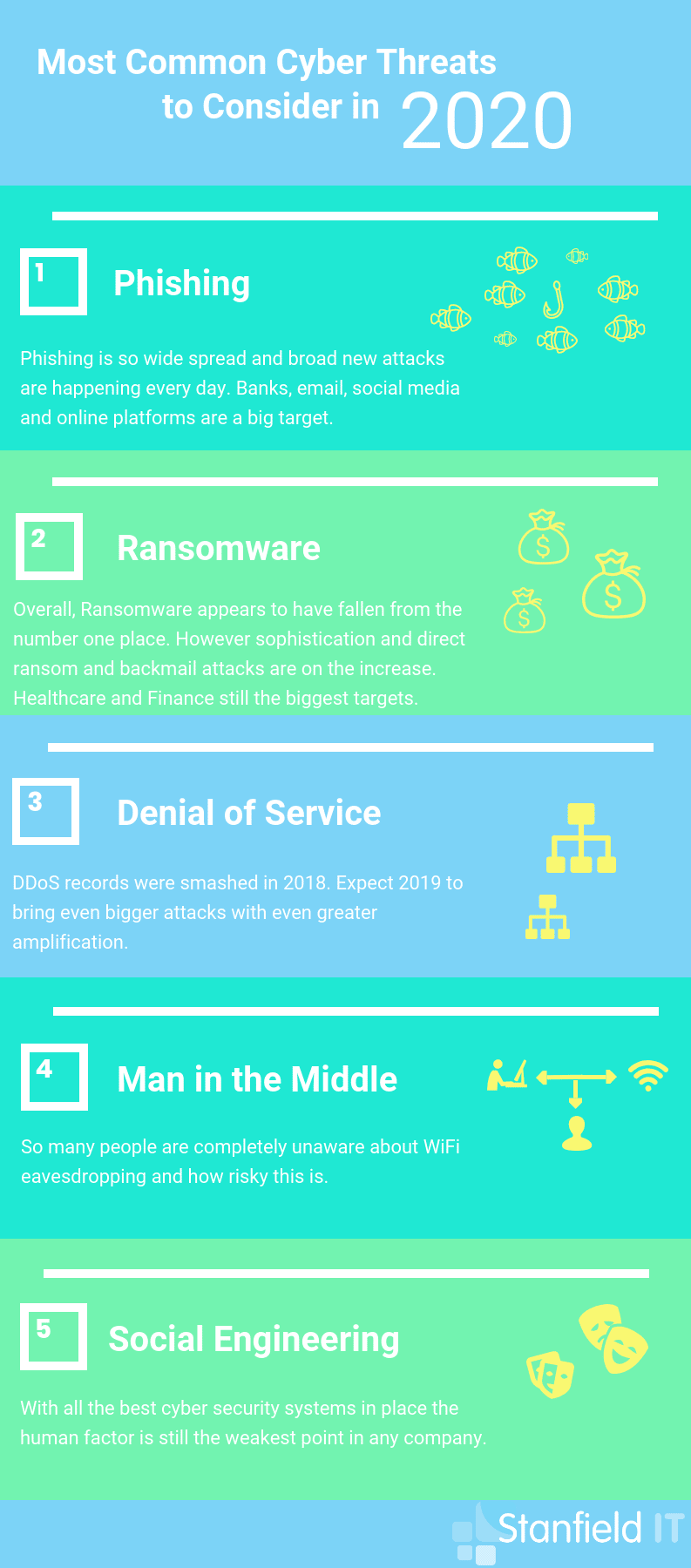
Most Common Cyber Threats
Phishing
Phishing is such a widespread and successful cyber attack as it relies on human error, unfortunately. They are counting on you to make a mistake and let them in. Ultimately, no security tool can prevent you from straight up giving your credentials away. But we can be alert, aware, and use sensible online practice to prevent successful phishing. SecureList provides quarterly statistical data around phishing and other cyber security threats. We recommend the IT threat evolution reports from Q2 and Q3, 2019, and the spam and phishing report from Q2, 2019.
Ransomware
As mentioned earlier, ransomware attacks are becoming far more sophisticated these days. Prevention is your best bet rather than trying to deal with the fall out and aftermath of an attack. Statistics vary on whether ransomware is on the rise or decline. Most importantly, though, it remains a popular method of attack amongst cyber criminals looking for a pay day. Just because you’re a small business doesn’t mean you’re safe from ransomware attacks. In fact, Business News Australia goes over how SMEs in AU and NZ were hit the hardest by ransomware attacks.
Denial of Service
This malicious attack occurs when the attacker floods a system network or resources to the point that it can no longer function or respond to service requests. A DDoS (distributed denial of service) is the same type of attack, but instead utilises a large host of other machines controlled remotely by the attacker to provide more attack power. This article reviews DDoS attacks in 2018 and growing trends.
Man in the Middle
This type of attack is pretty self-explanatory. But despite its simple name, the attack itself is clever and can be totally devastating. A hacker can intercept a connection and then insert themselves into the exchange so that both parties now unknowingly reveal sensitive data to this malicious third-party. We found this site to be very informative and comprehensive on the nature of MITM attacks.
Social Engineering
This occurs when the attacker manipulates you (the victim) into believing a message, link or attachment has come from a trusted source and then infect your system to steal confidential data. It’s easy to avoid messages and emails from unfamiliar contacts. But they’ve become clever, and will entice you to open something that looks like it’s from your sister or friend or co-worker. Here is an interesting experiment on social engineering and how successful it really is.
Data Breaches
2018
- Svitzer Australia revealed up to 60,000 emails were leaked over the course of nearly a year. This was the first data breach publicised under the new Notifiable Data Breaches Scheme. Svitzer is not a huge organisation. With around 1000 employees, this case shows you don’t need to be a big ball-busting corporate machine to be affected by a data breach.
- Teas.com.au is a small business run by Salina Hainzl, and nearly lost her business entirely due to a virus. In addition, her site was hacked six times! Salina has since restricted her cyber security and improved her site security to safe-keep her business.
- Family Planning NSW suffered compromised databases, with approximately 8000 affected people. The government department was hit by a ransomware attack, and details of patients and inquirers were subject to the attack.
- HealthEngine is another health industry related business that was affected by a data breach. Cyber attack is not to blame for this breach however, with the company blaming the breach on a website error. The “error” caused normally hidden data to be exposed in the website’s code. Multiple instances of revealed information contained identifying information about a site user.
- GoGet is the car-share service around Australia. Someone had accessed the fleet booking system and attempted to use vehicles without permission or payment. In doing so, the individual had also attained access to personal data of other GoGet members.
2019
- DPS are introducing/introduced cyber attack simulations that parliamentarians and their staff will be subject to. This has been sparked by the state-sponsored cyber attacks against Parliament House in early 2019. The aim is to heighten cyber security awareness.
- NAB had a data breach in July 2019 that affected 11,500 (80% of these were contacted within two business days of the incident). The data breach was a result of human error, which is actually the leading cause of data breaches, and additional staff training has now been put in place. In this breach personal identifying information (like drivers license details, government identity numbers, dates of birth, and contact details).
- My Heath Record saw a large number of data breaches in In 2018 and 2019 and, although these were well in decline last year, in excess of 2.5 million Australians have opted out of the online system. ‘After falling from 64 to 57 between 2016-17 and 2017-18, the number of formal complaints climbed to 304 in 2018-19,’ the article by Justin Hendry of IT News reads.
- Westpac‘s (yes, yet another bank!) PAYID real-time payments platform was victim to a cyber attack in mid 2019 that affected both Westpac customers and customers from other banks. 90,000 users had their bank account details and personal data leaked. This prompted a statement from computer security experts who warned that the pilfered data could be used for fraud.
- LandMark White, an independent property valuation and consulting firm in Sydney, was victim to a huge data breach when of contractor of the firm purposefully uploaded valuations of 275,000 individuals to the dark web. This cost LandMark White an estimated $8M. The perpetrator, Stephen Grant, was arrested under the suspicion that he gained unauthorised access to the firm’s database to get these documents.
2020
- P&N Bank in Western Australia was hit by a data breach in January this year. It’s WA’s largest member-owned bank, and the customers who has personal information exposed have been notified. Luckily, the data accessed was all in the ‘non-sensitive’ category (no credit card details or customer passwords were leaked) as the core banking system was not jeopardised.
Cyber Security News from 2018 to 2020
2018
- The biggest cyber security news for 2018 starts with the Notifiable Data Breaches Scheme coming into effect in February. Lifehacker provided an excellent round-up on the legislation to break through the governmental jargon. However, there remains some debate over whether the new regulations are successful. The numbers of reported breaches are vastly below what one would expect based on cybercrime and data breach statistics.
- The next big privacy regulation to roll out was the General Data Protection Regulation (GDPR) which came into effect in May 2018. This is a regulation focused on data protection and privacy for individuals within the EU. The OAIC provides an outline on the regulation and how it may affect Australian businesses.
- The AA Bill (Assistance and Access) stirred a lot of controversy at the end of last year. It was rushed through the House, with many individuals concerned that there are repercussions being overlooked by politicians who don’t fully understand the cyber security Australia focused environment. Any backdoor designed for law enforcement and intelligence to access could equally be accessed by hackers and provides a built-in vulnerability. Here is a great overview of the bill and what it entails for Australians.
- MSP Global Hack has affected a number of managed services providers within Australia, in which data was stolen from customers. The full extent of which MSPs have been affected is not known at this point, but it seems that there has been a significant blow to privacy here.
- Australia released its first Cyber Incident Management Arrangements in December 2018. The intent of these guidelines is to reduce the severity and impact of a national cyber incident, but there is question over whether the guidelines are enough to protect Australia from a national cyber attack. Have a read of some of the criticisms here.
2019
- In January 2019, Google copped a $57M fine from French regulators. They alleged that the multi-billion dollar search giant was not being transparent regarding how personal information was being collected. They also claimed that Google was failing to properly obtain consent for personalised advertisements. On the back of this, a few months later Ireland’s Data Protection Commission voiced plans into an examination of whether Google’s Ad exchange marketplace violated GDPR when handling user data.
- Companies are aiming to synthesis the collection and analysis of data and automate responses to common issues using SOAR (Security Orchestration, Automation and Response) tools. The acquisition spree kicked off in March 2019 when Palo Alto Networks brought Demisto for $560M in order to automate customer’s security options through leveraging artificial intelligence and machine learning.
- In November, 2019, a peak financial regulator warned Australian banks to expect a tougher approach to security in response to their poor cyber hygiene. Within the four months following the new regulation where they have to disclose any data breaches, Australian banks saw a total of 36 data breaches. This also follows a Melbourne woman in a major fraud syndicate being charged for stealing the identities of thousands of customers of superannuation funds.
- Let’s end with some good news! As reported towards the close of 2019, Australia’s online fraud bill is being forced down by the marked shift to mobile-based online and tap purchases, as opposed to entering credit card or debit card details. The latest payment fraud statistics (from the 2018 to 2019 financial year) showed a 5% drop from $479M to $455M. This may not sound like much of a drop, but it’s just the second time this figure has declined since reports started being kept.
In Conclusion
Want more? We recommend taking a look at Positive Technologies Cybersecurity breakdown from 2019 to 2020, which you can view online and download as a PDF.
If you are struggling trying to work out where to start with your cyber security give the team at Stanfield IT a call and we can help walk you through the process.
