A firewall should be part of your overall cyber security mitigation strategy. You’re not a big bank or Apple, so your business is safe from hackers. Right? Unfortunately not. Many hackers actually target small-to-medium businesses because they know SMEs are less likely to invest in cyber security.
So, how can you protect your business and client information from falling into the wrong hands? A firewall can help form part of your overall strategy, sitting as a crucial part of the data-security infrastructure in a business of any scale.

What is a firewall?
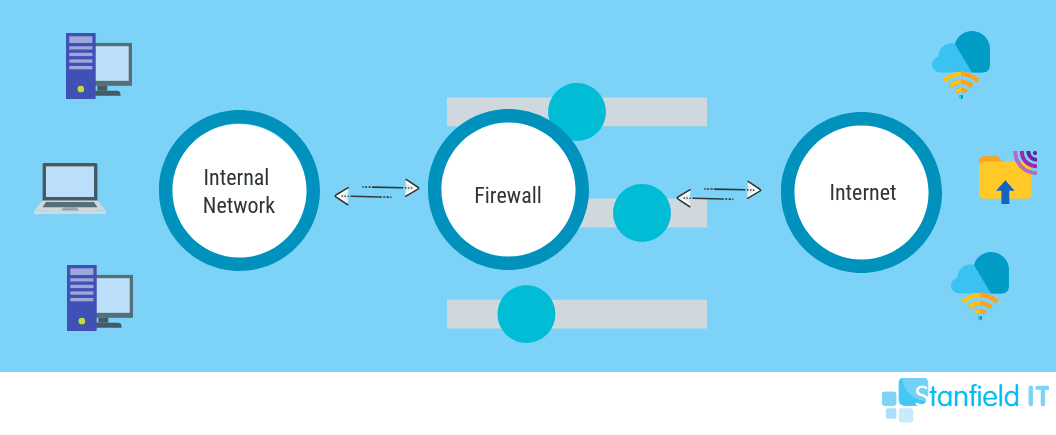
A firewall is a network security system that controls incoming and outgoing traffic on a computer or business network. This control is based on a set of policies or rules. These are configured on the firewall or via the firewall management console.
Basically, a firewall helps protect and secure the devices, applications, and data that sit behind it on the internal network. This can be at your office, between offices, or even between services you have sitting at your hosting provider or cloud provider.
Installing a firewall on your network, or in front of your cloud services, equals a better-protected network. You’re helping protect your users and data on the network from nasty online attacks and vulnerabilities. Firewalls are a key ingredient to your cybersecurity setup to reduce the risk of attack and secure sensitive data.
Early firewalls from the 80s and 90s (as well as the cheap firewalls sold today) are too basic for most modern business requirement. They only allow traffic based on a particular port, web address, or IP address. Newer and more advanced firewalls go hundreds of steps better because they use application-level scanning and machine learning.
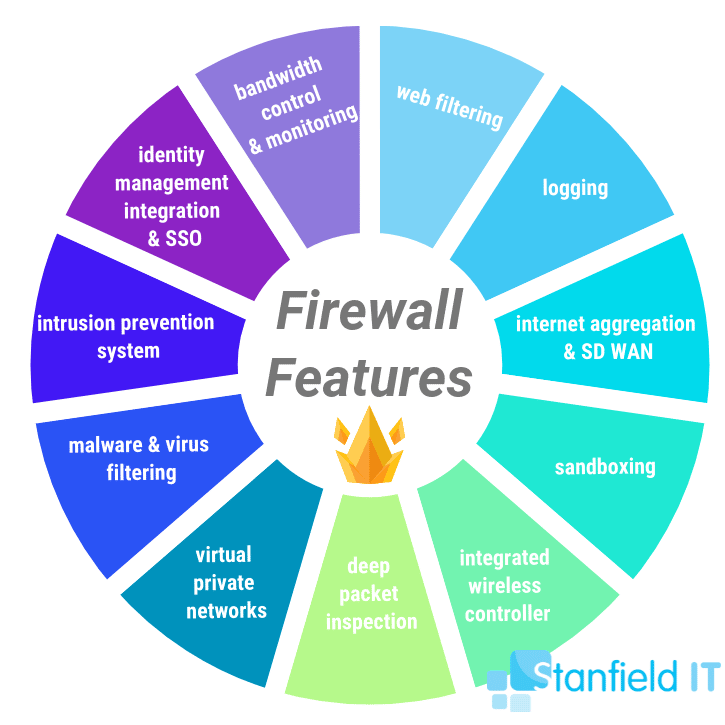
Our top 11 firewall features we can’t live without:
1: Bandwidth control and monitoring
Bandwidth control―sometimes referred to as traffic shaping―is one of the best firewall features. We don’t always have unlimited amounts of bandwidth. That means it’s vital to take control of the bandwidth we do have available. With a firewall, you can control the bandwidth available for sites, applications, and users.
Maybe you want to give your graphics department more overall bandwidth. Or you might want to stop cloud-based file synchronization services from hammering your bandwidth. Here, popular services like OneDrive, DropBox, and Google Drive can cause serious issues. But, of course, the solution is not to stop using these amazing programs. Instead, welcome, bandwidth control!
With bandwidth control on your firewall, you can allocate a set amount of dedicated bandwidth for your VoIP phone system. You can even allow other cloud-based services, like Skype for Business or Hangouts, to have priority. This will help stop the dreaded jitter that makes any phone or video call painful.
You can control when backups happen between sites so that those backups aren’t causing problems during business hours. You can also allow backups to have a large chunk of the connection out of hours. Enforcing backup traffic to travel over cheaper links is another great feature to utilise. This will mean that more important traffic can be set to go over your higher quality links when quality really matters.
2. Web filtering
You can think of a web filter firewall as a content filtering firewall. A web filter firewall is defined as a software program that oversees the data packets that your computer sends and receives. In doing this, it filters any compromising content that has been forbidden or flagged. These rules can be set to stop access to any potentially threatening, unsecure sites. It can also be used to prevent employees from accessing certain sites that may reduce productivity (like social networking websites).
Most firewalls allow you to block access to websites. This can be done on a case-by-case basis, or your firewall can include a subscription that helps you choose categories you don’t want people to have access to. Things you may want to stop employees or guests being able to do on the work network could be: illegal activities, downloading illegal content, gambling, and many more.
The firewall vendor will continuously update their lists for you, as these types of websites will always be updating their IP addresses and domain names. Vendors like Cisco and Fortigate take the hassle out of this for you with their automatic updated lists.
Some firewall filters can easily be downloaded from the internet, but don’t be fooled. As opposed to firewalls set up by IT professionals and paid firewall subscriptions from reputable sites, these firewalls don’t provide sufficient protection. Anyone who knows their way around firewalls could easily breach them.
3. Logging
Having access to logs on a firewall gives you up-to-the-minute information about what is happening on your network. Sought after firewall features include being able to give graphs in real time and show you what vulnerabilities or attacks are happening.
Aggregating the information documented by the firewall on the source address, source port, and destination address and port, can make seeing the data collected by the firewall simple and easy to digest. This information, tracked by the firewall, can be viewed as an identifying quality of any suspicious attempt to connect.
Firewall logging is extremely useful as it allows you to see:
- if a new firewall is performing well (so you can debug, if necessary);
- if malicious activity is occuring in your network;
- any repeated unsuccessful login attempts from a particular IP address (you can then create a rule to block connections from this IP);
- and if someone is using your system as a launch pad (such as lauching attacked against your systems or networks).
4. Internet aggregation and SD WAN
Link aggregation and SD-WAN (Software-defined Wide Area Network) are great features for businesses who need multiple links to the internet. They’re also useful where you are using multiple links and would like to connect to other sites, such as branch offices or cloud services.
A link integration interface is defined as a group of physical interfaces in which you can set to work together as one logical interface. It’s used by businesses to increase the joint data throughput so that you can extend the capacity beyond that of a single physical interface. It’s also used to provide redundancy is there’s a physical link failure.
SD-WAN is a virtual WAN architecture whose purpose is to let enterprises use any combination of transport services to safely connect applications and users. This includes MPLS, LTE, and broadband internet services.
The ability to use multiple links allows you to have redundancy. It also lets you use multiple cheap links with different providers to meet your bandwidth requirements.
5. Sandboxing
Sandboxing is one of those important firewall features that end users don’t even know is there. It takes a file or executable as you’re downloading it and opens it in a completely isolated and separate “test” environment.
This replicates the end-user environment away from your production environment without putting your users at risk. A sandbox then opens the file, runs it, scans it, and looks for malware or activity that is suspicious.
If the files or URL looks safe, it will pass it onto the end-user. If the file or URL displays malicious behaviour, then a new threat has been flagged! Sandboxing is particularly effective at defending against zero-day threats (haven’t been seen before and don’t match known malware signatures). It falls into the advanced threat protection category that goes beyond what traditional inbound email filter scanners can offer.
Sandboxing is an added layer of protection so that, if an email contains unknown URL links, files types, or suspicious senders but still makes it through the email filter, tests will be conducted prior to it reaching the network or mail server.
6. Integrated wireless controller
Using a firewall with an integrated wireless controller is a fantastic way to save money and bring all of your policies and control into one place or platform.
You can easily set up different SSIDs and policies, taking full control over your environment. The model of firewall you choose will impact how many wireless access points you can use. Low entry-level models will allow 2-10 access points, while larger high-end models will allow hundreds.
You can even set up all of your sites using the same policies. This lets your users roam between sites without needing to connect or enter in passwords at each site.
7. Deep Packet Inspection
Deep packet inspection (DPI) is a great feature we just can’t live without anymore. This technology is an advanced way of examining and managing network traffic where the firewall takes a close look at the packet that is being passed through.
As it examines the content of packets passing through a given checkpoint, it can look for hidden viruses and malicious activity, making real-time decisions based on rules assigned by the enterprise, ISP, or network manager. The firewall can then decide what to do with the packet. It can block the sender or drop the packet. Technological advancements have enabled DPI to perform deeper and deeper inspections in real-time on huge volumes of traffic. This is why it’s a favourite of our firewall features.
The really great thing about DPI is that if the firewall determines it’s a new source threat it will send a note back to the vendor. This will then be reviewed and other firewalls around the world will be updated. The result? Different networks working together to keep one another safe.
8. Virtual Private Networks
Virtual private networks (VPNs) are networks that are built using public wires (usually the internet) to connect remote users or regional offices to a company’s private, internal network. VPNs are great for users connecting back to a site or the office. They can also be used to connect two sites together.
You want to make sure that your device, whether it uses another network/firewall or if it’s an end user computer, is secure and safe. With a VPN, you can allow users to access applications and data securely from remote locations. Best of all, you aren’t opening up public facing ports or applications. A VPN ensures privacy and security through an encrypted tunnel that transmits the data between the remote user and company network.
The three main protocols used with VPN tunnels (generally incompatible with each other) are:
- IPSec – A set of protocols developed by IETF to support secure exchange of packets.
- PPTP – Point-to-point Tunneling Protocol technology used for creating VPNs.
- L2TP – Layer Two Tunneling Protocol (an extension of PPP protocol) that enables ISPs to operate VPNs.

9. Malware and virus filtering
Next generation firewalls are always filtering for malware, new and old, and are your perimeter defense mechanisms. This includes scanning for viruses, compromised websites, files containing viruses, bot nets trying to hack you, man-in-the-middle attacks―you name it! They can even scan encrypted traffic, such as SSL and TLS connections, to make sure they are safe and trusted.
Some more advanced firewalls can communicate to all of your endpoints, quickly flagging any compromised systems through active monitoring. Instantly, the firewall will block or limit network access to these devices until the issue is rectified. Firewall features include being able to remotely monitor and adjust their settings so that employees can focus on their work instead of being interuppted by network security implications.
10. Intrusion prevention system
An intrusion prevention systems (IPS) is the latest advancements from intrusion detection systems (IDS). IPS continually monitors your network, capturing information about possible malicious attacks. These events are then reported to the system administrator(s), who take preventative steps like closing access points and configuring firewalls to prevent future attacks.
These capabilitities mean that IPS goes one better than IDS by monitoring the network traffic using policies. As well as looking for external suspicious activity, they can also identify issues with corporate security policies. This means that employees and network guests are deterred from breaching the rules of these policies. If they don’t follow the rules, the firewall will detect suspicious activity on the network, block the traffic, and provide a report.
11. Identity management integration and Single Sign On
Single Sign On (SSO) is a feature of identity and access management that means users can authenticate their identity safely and security via multiple applications and websites by logging in a single time. The application or website they’re signing into requires verification from a trusted third party to ensure positive identification and no security breaches.
One of the greatest features is that firewalls allow you to integrate with single sign-on platforms, either directly or via a RADIUS (Remote Authentication Dial-In User Service) server. A RADIUS server is a networking protocol that features centralised authentication, authorisation, and accounting management for users who connect and use a network service.
If you have an environment where cyber security is paramount and you are controlling your users by department, function, or even site, then integrating their access into group management and SSO cuts down the administrative overhead.

A firewall can never guarantee the safety of your data, but it does offer a far greater chance of keeping it safe. If you can’t afford to lose your data, or suffer a breach of confidential data, then a firewall will help form part of your overall cyber security mitigation strategy.
Have a question about firewalls or anything else? Our friendly team is here to help.
